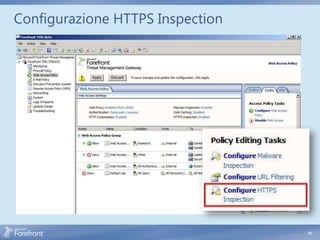
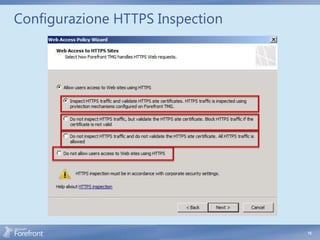
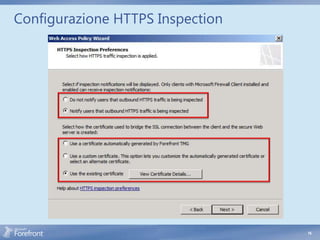
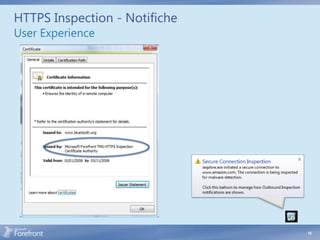
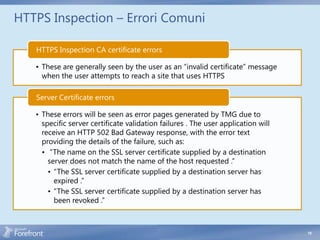
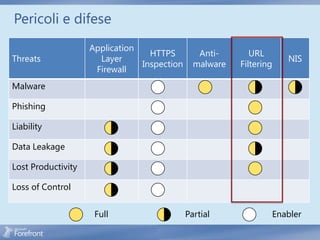
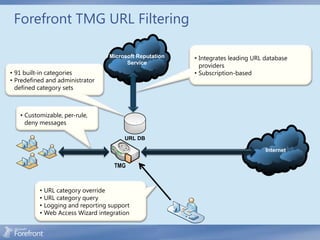
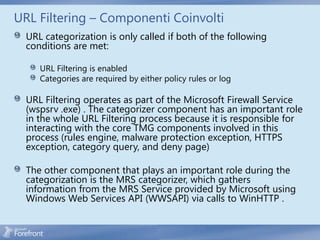
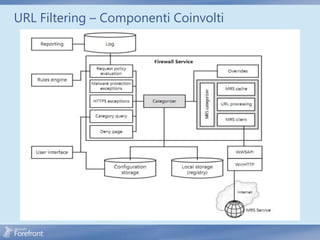
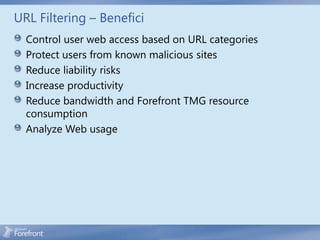
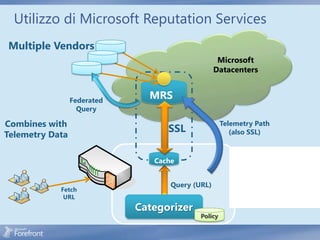
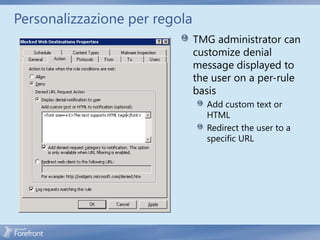
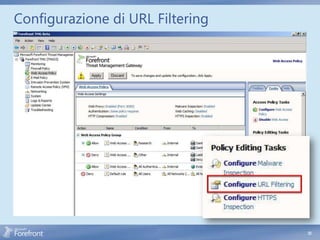
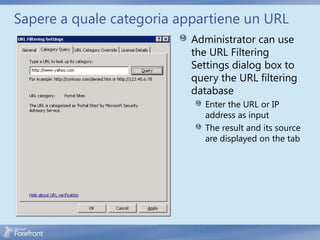
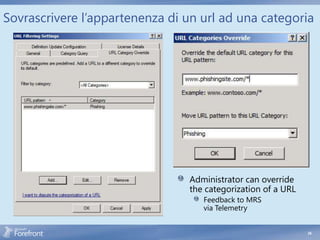
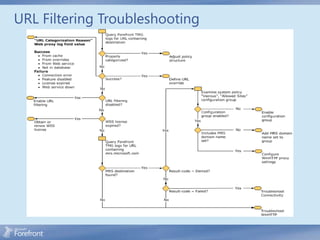
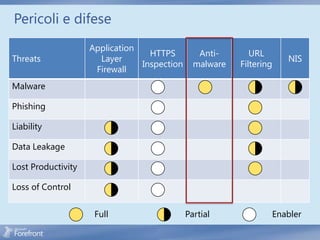
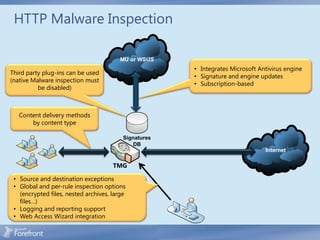
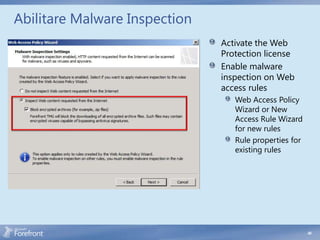
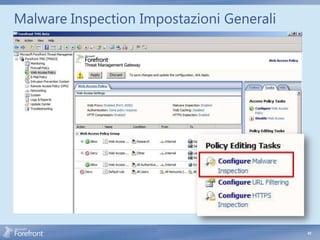
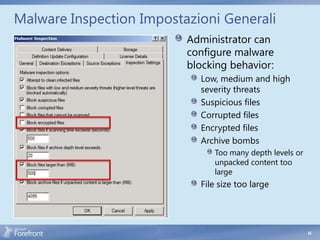
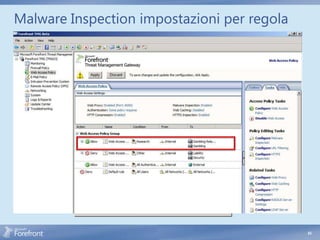
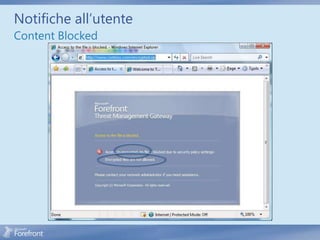
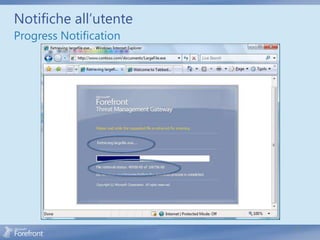
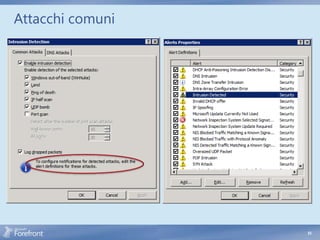
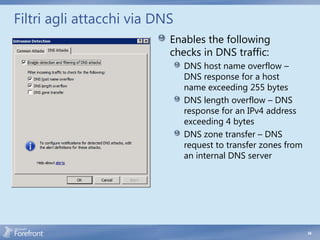
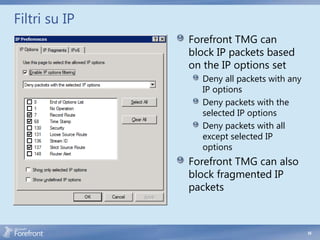
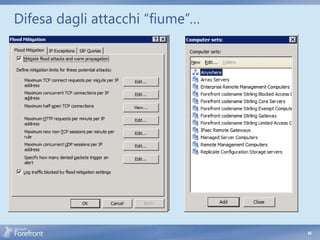
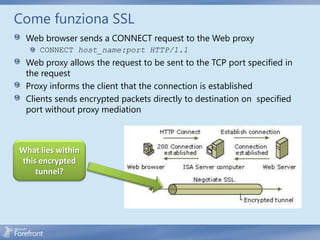
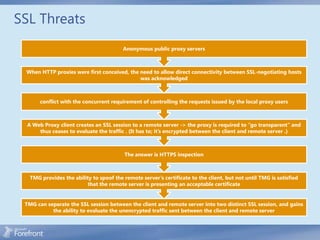
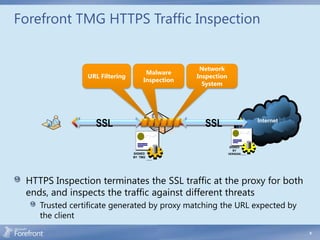
The document discusses secure web gateway technologies including HTTPS inspection. It describes how HTTPS inspection works by terminating the SSL connection at the proxy to allow inspection of encrypted traffic. It also covers potential threats of HTTPS inspection, best practices for configuration, and common errors.



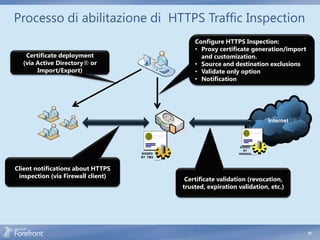


![HTTPS Inspection - Operazioni
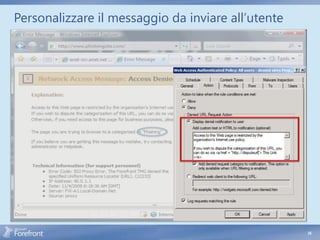
Enable HTTPS inspection
Generate trusted root certificate
Install trusted root certificate
on clients
contoso.com
https://contoso.com https://contoso.com
SIGNED
SIGNED BY
BY TMG VERISIGN Contoso.com
Contoso.com
1. Intercept HTTPS traffic
2. Validate contoso.com server certificate
3. Generate contoso.com server proxy certificate on TMG
4. Copy data from the original server certificate to the proxy certificate
5. Sign the new certificate with TMG trusted root certificate
6. [TMG manages a certificate cache to avoid redundant duplications]
7. Pretend to be contoso.com for client
8. Bridge HTTPS traffic between client and server
13](https://image.slidesharecdn.com/2-securewebgateway-120625162108-phpapp02/85/2-secure-web-gateway-13-320.jpg)