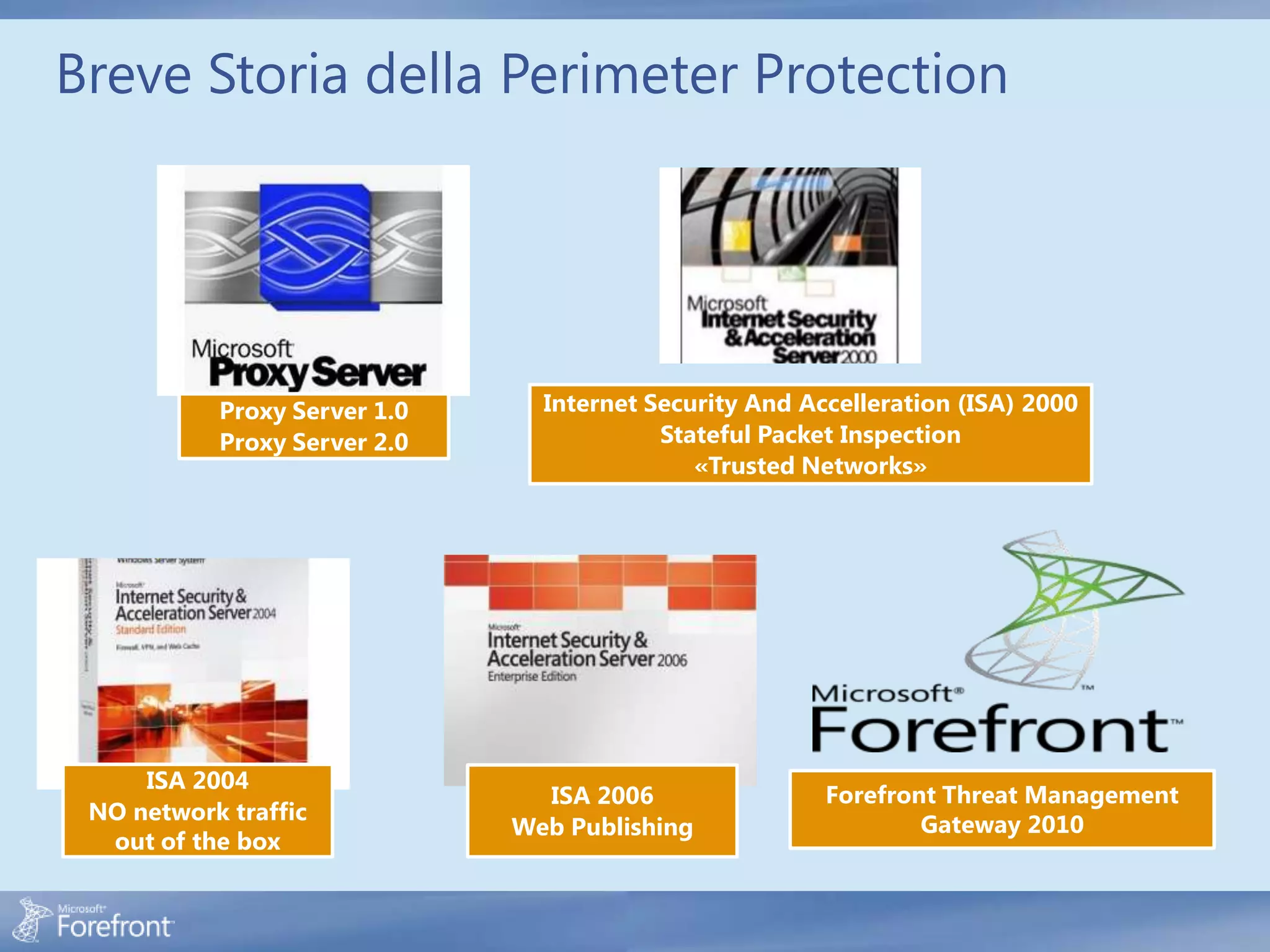
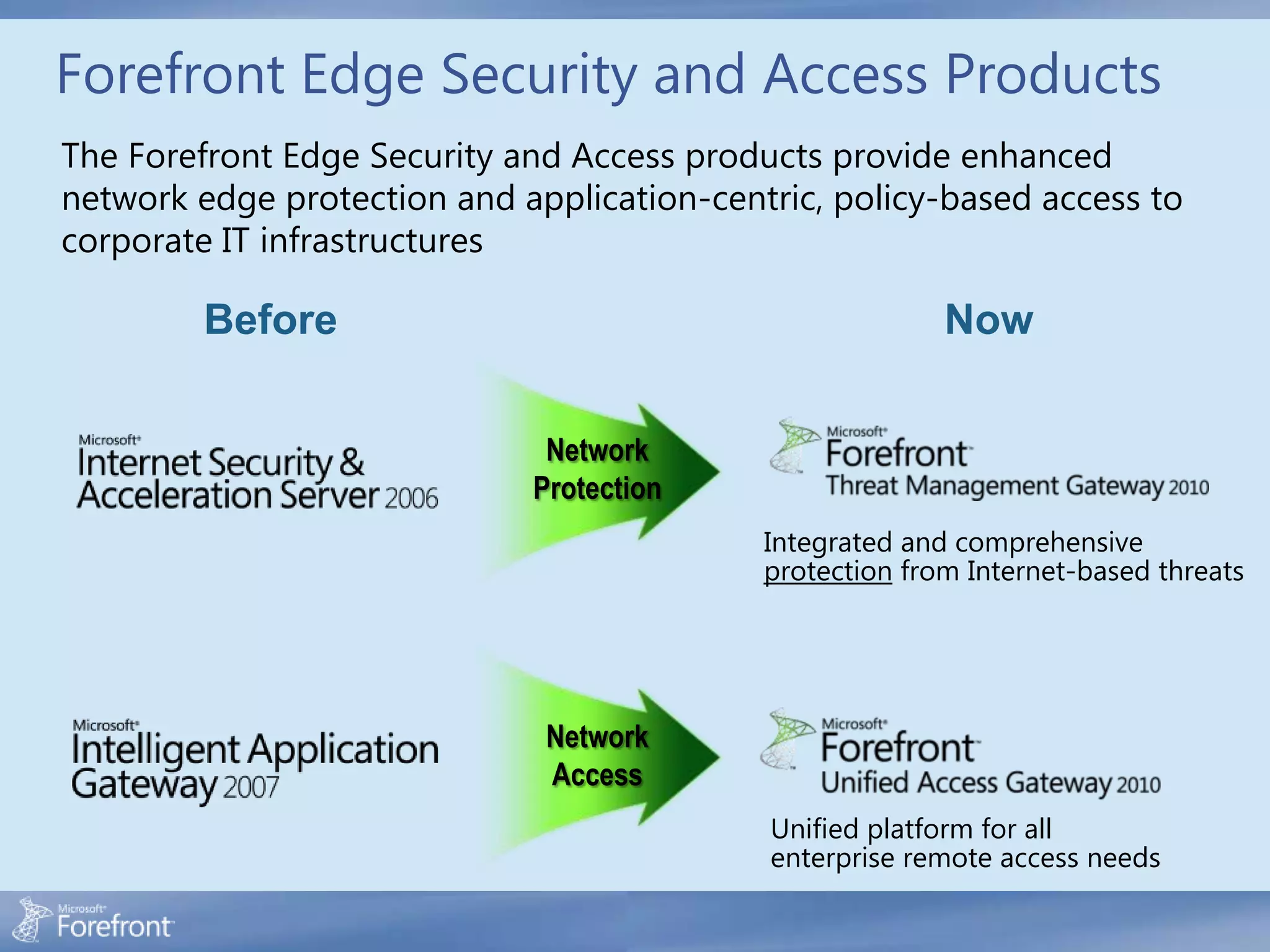
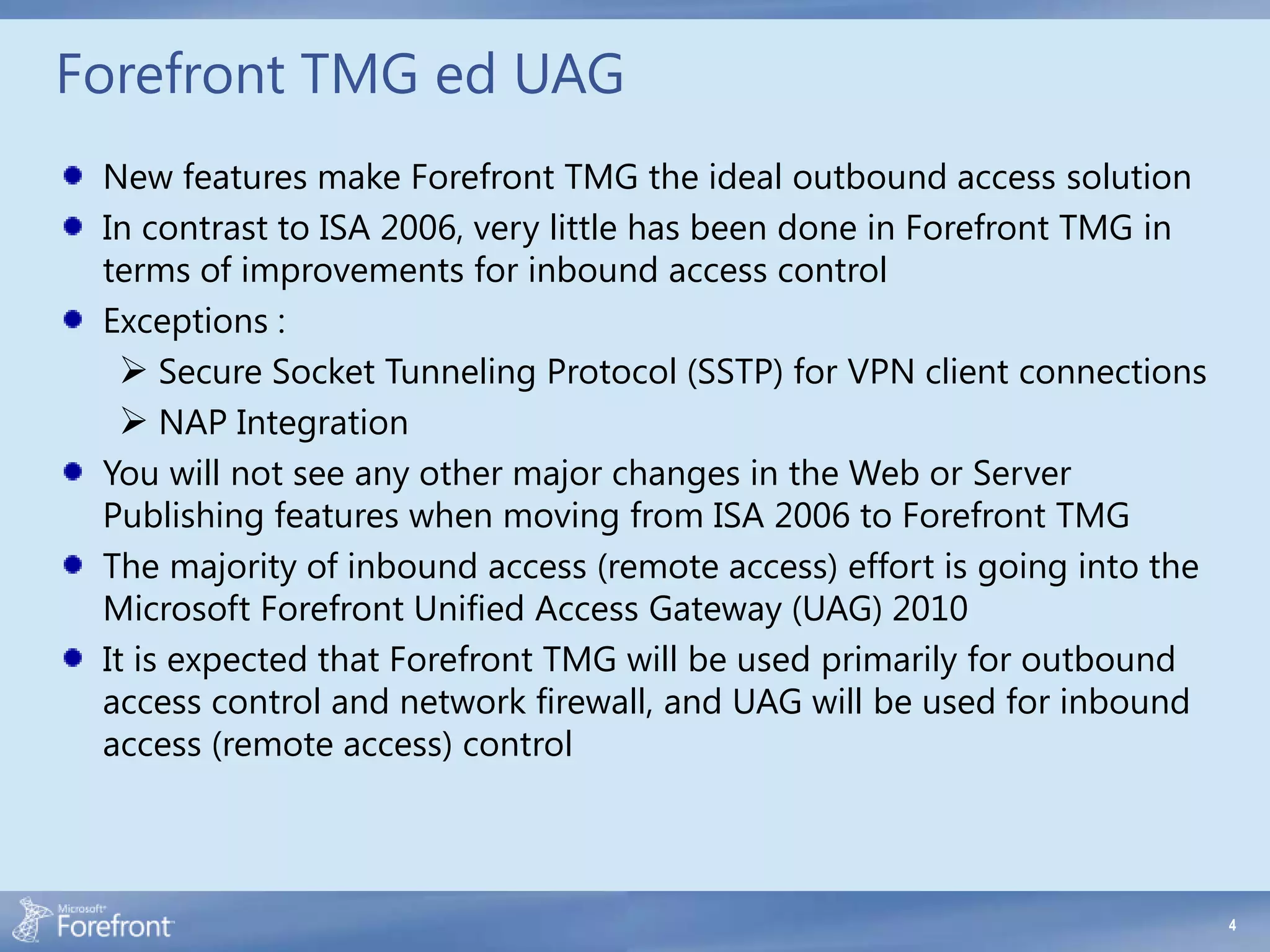
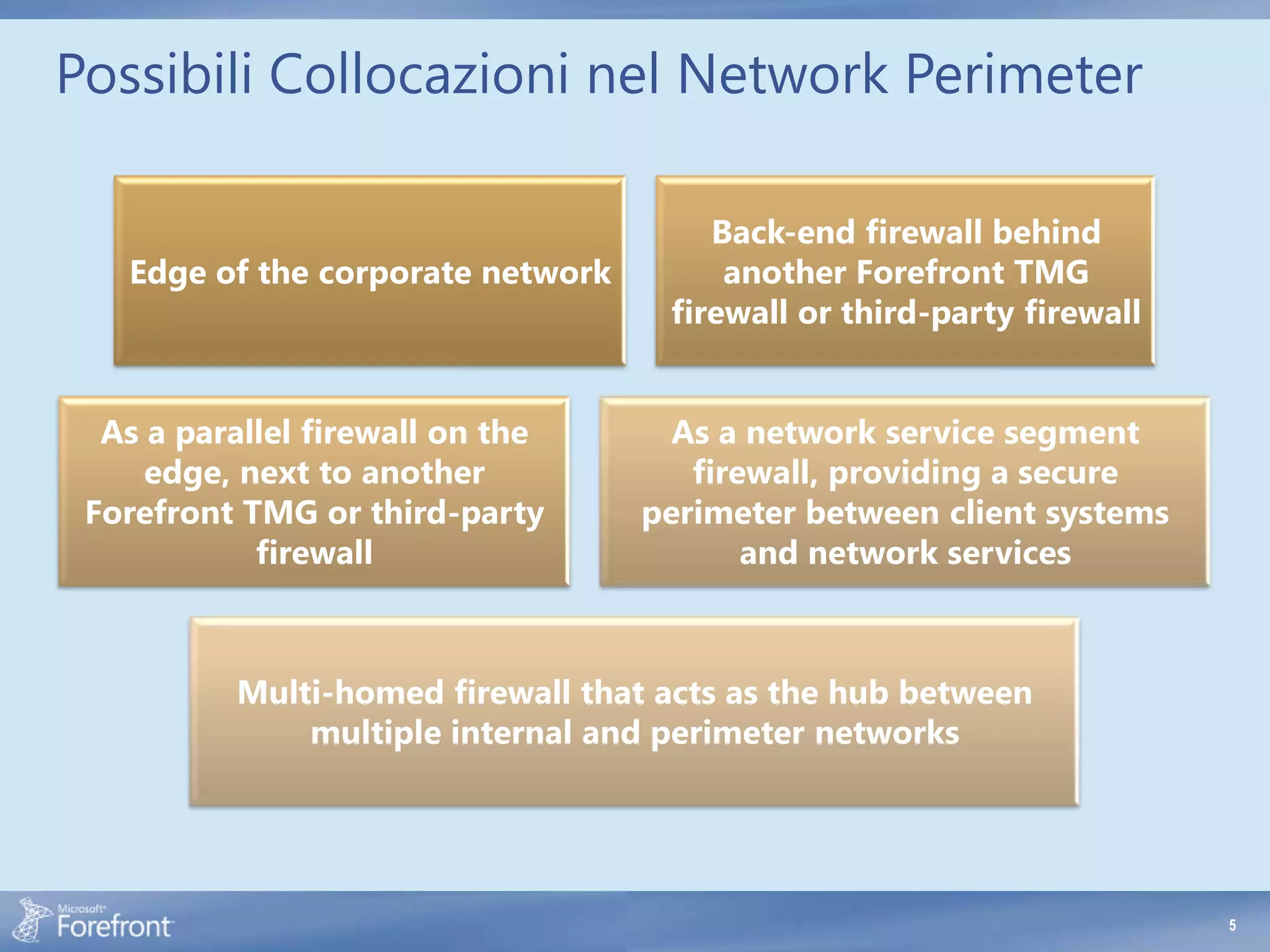
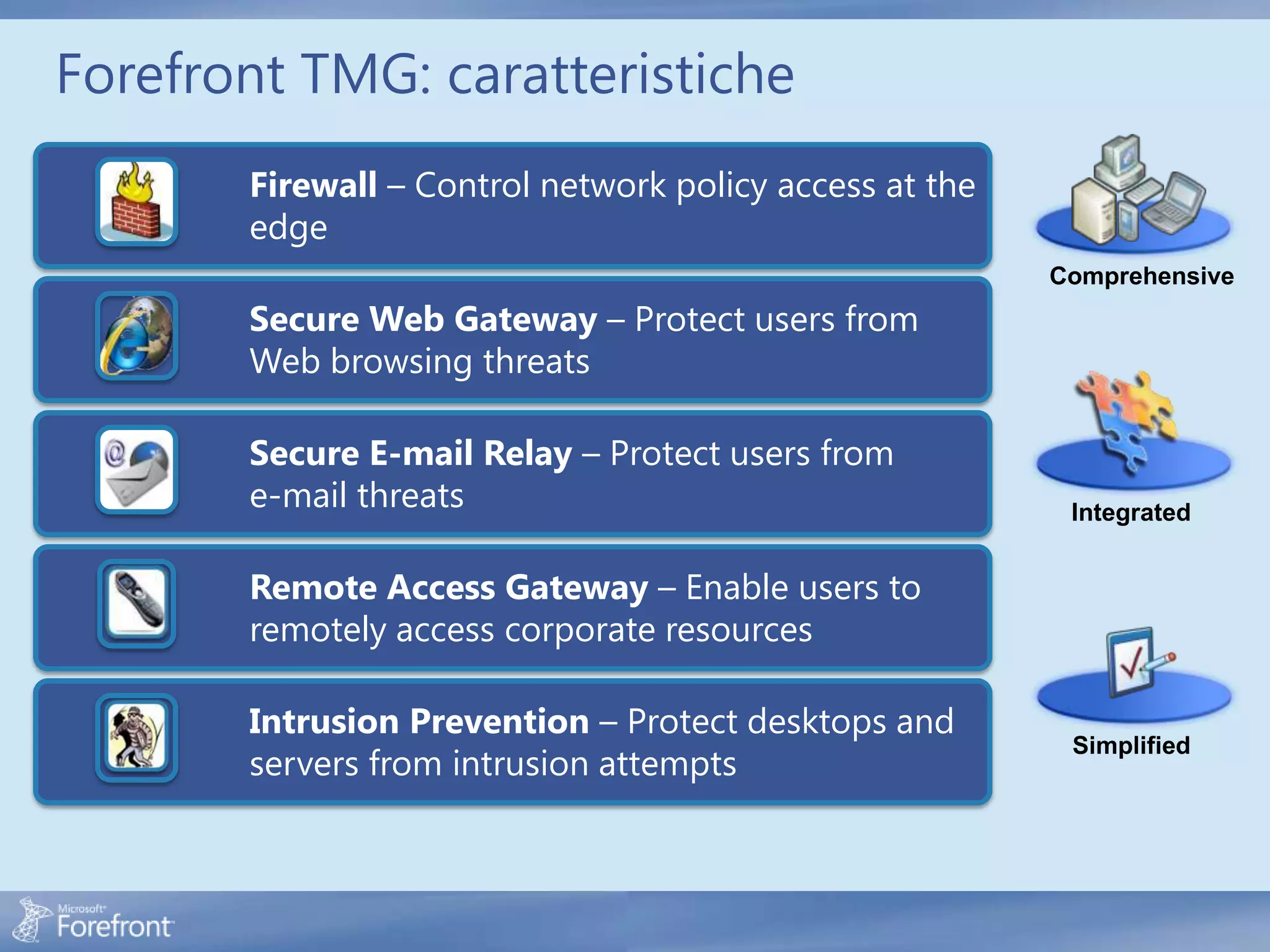
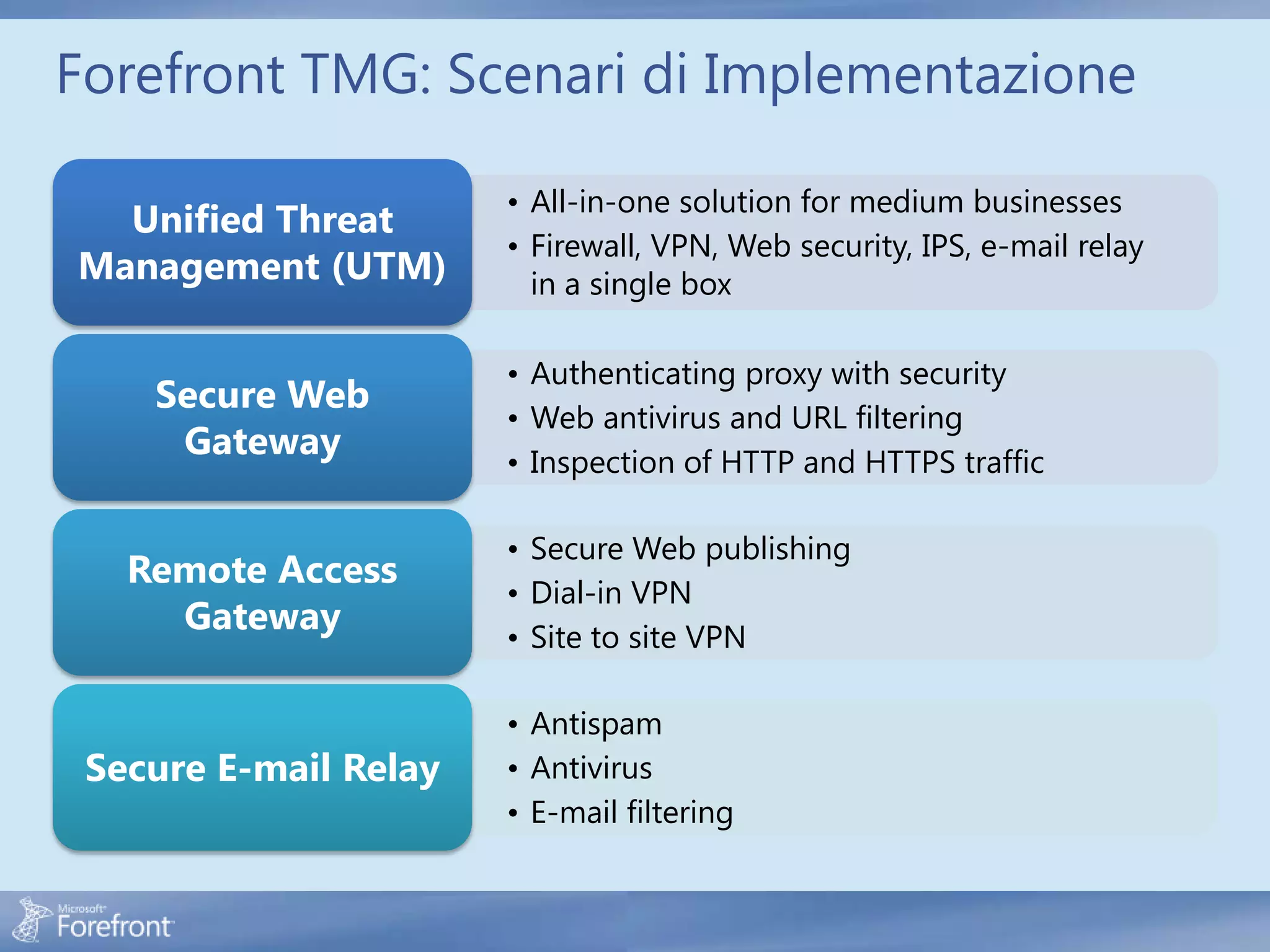
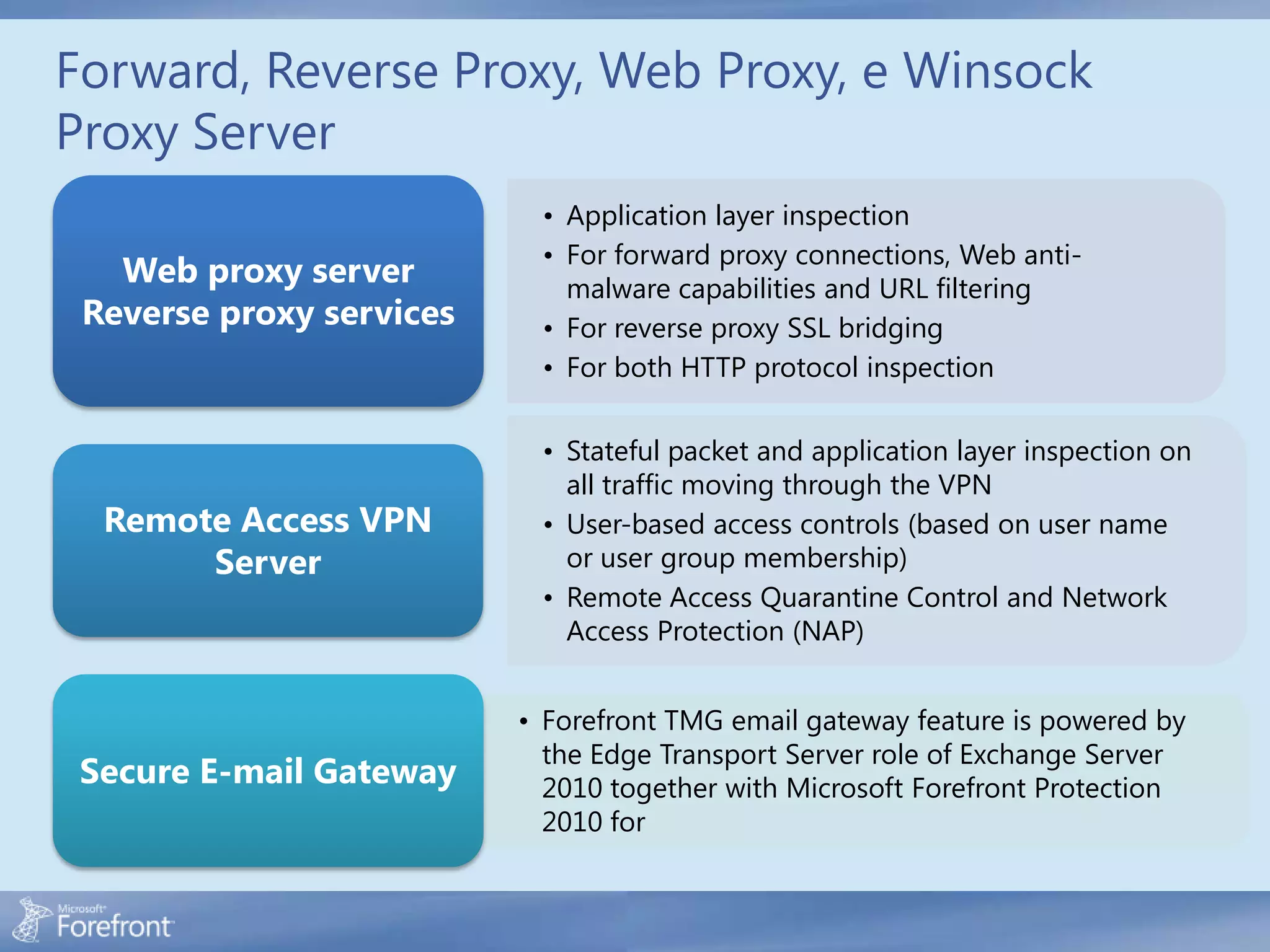
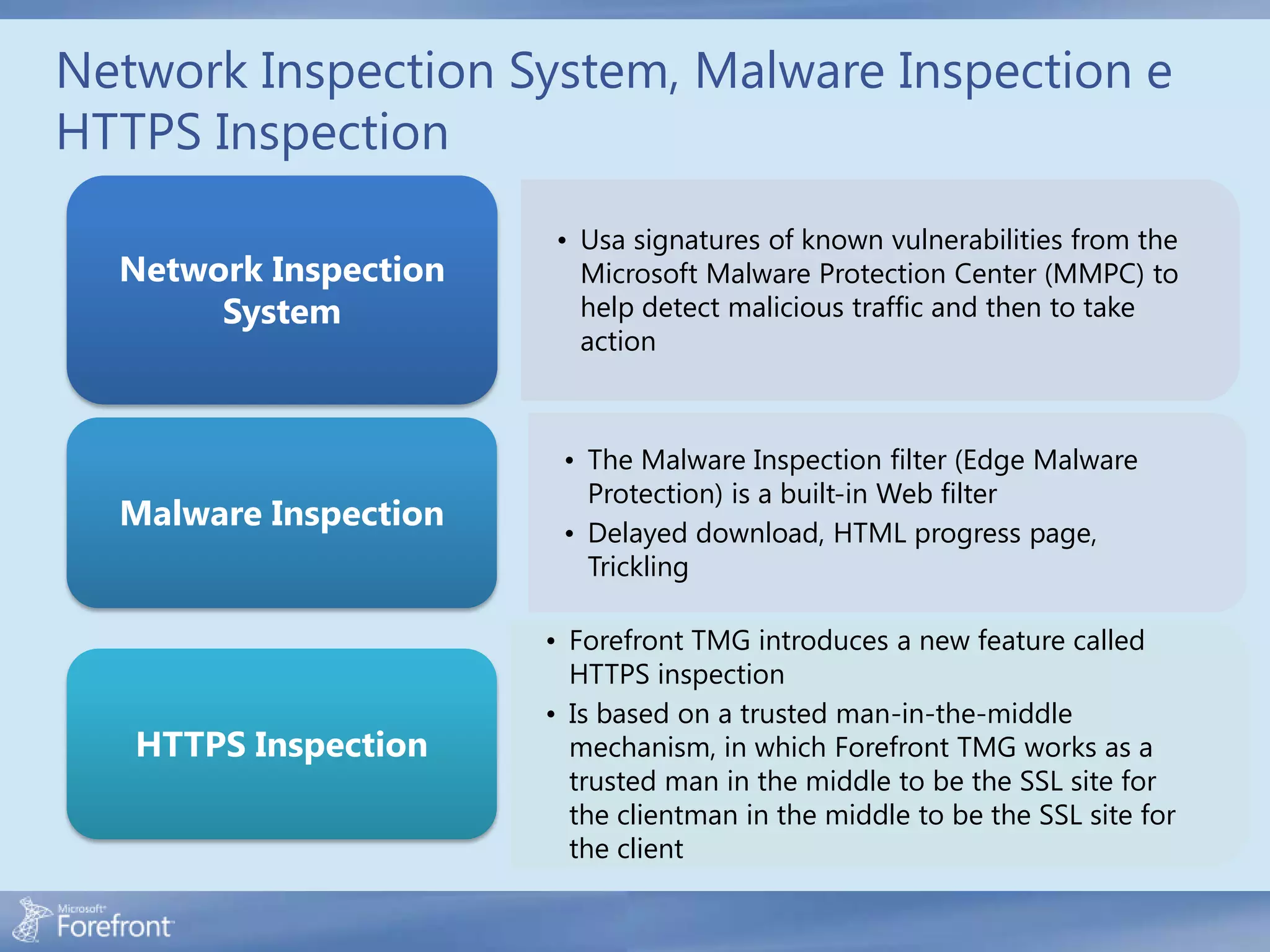
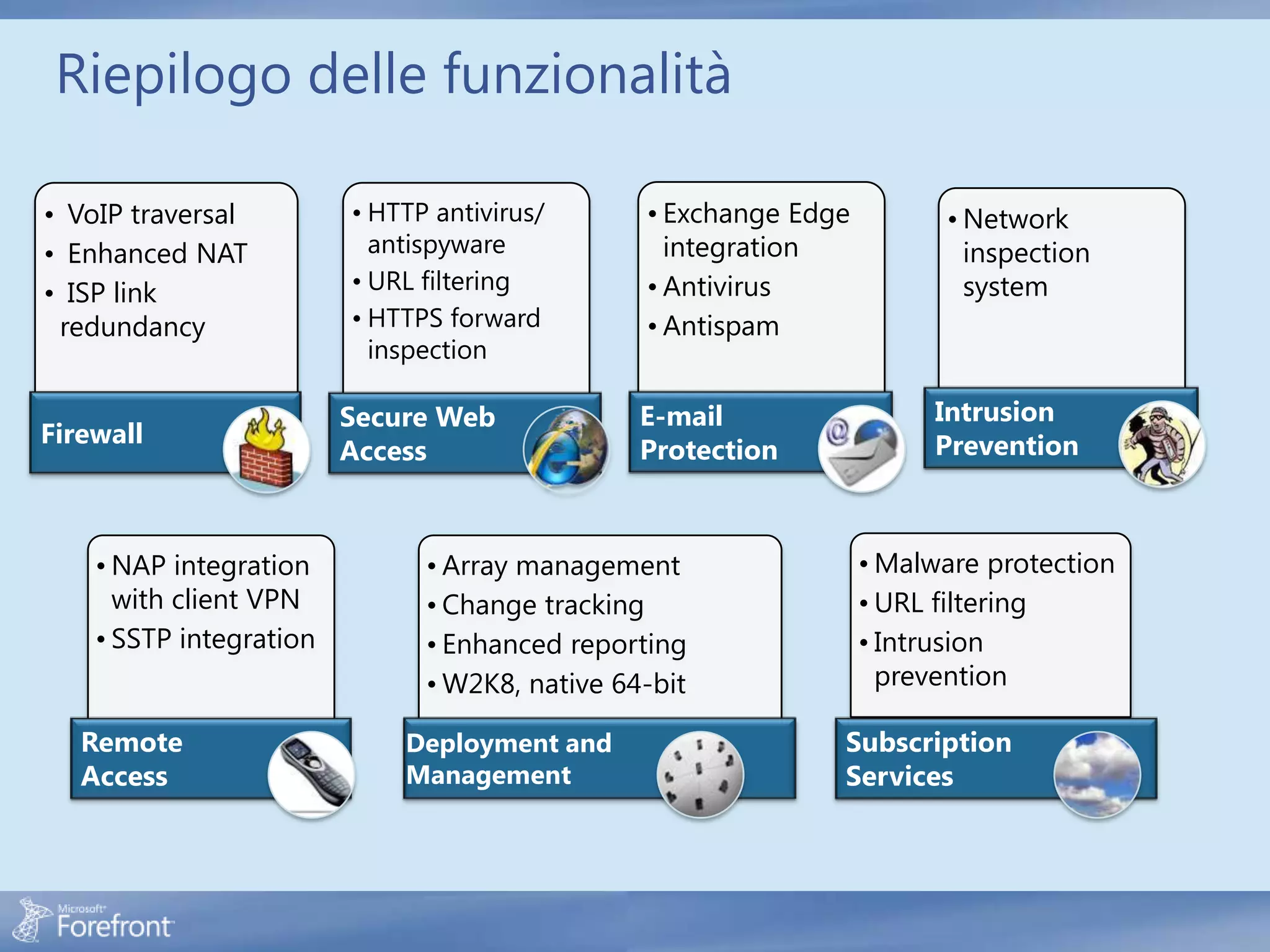
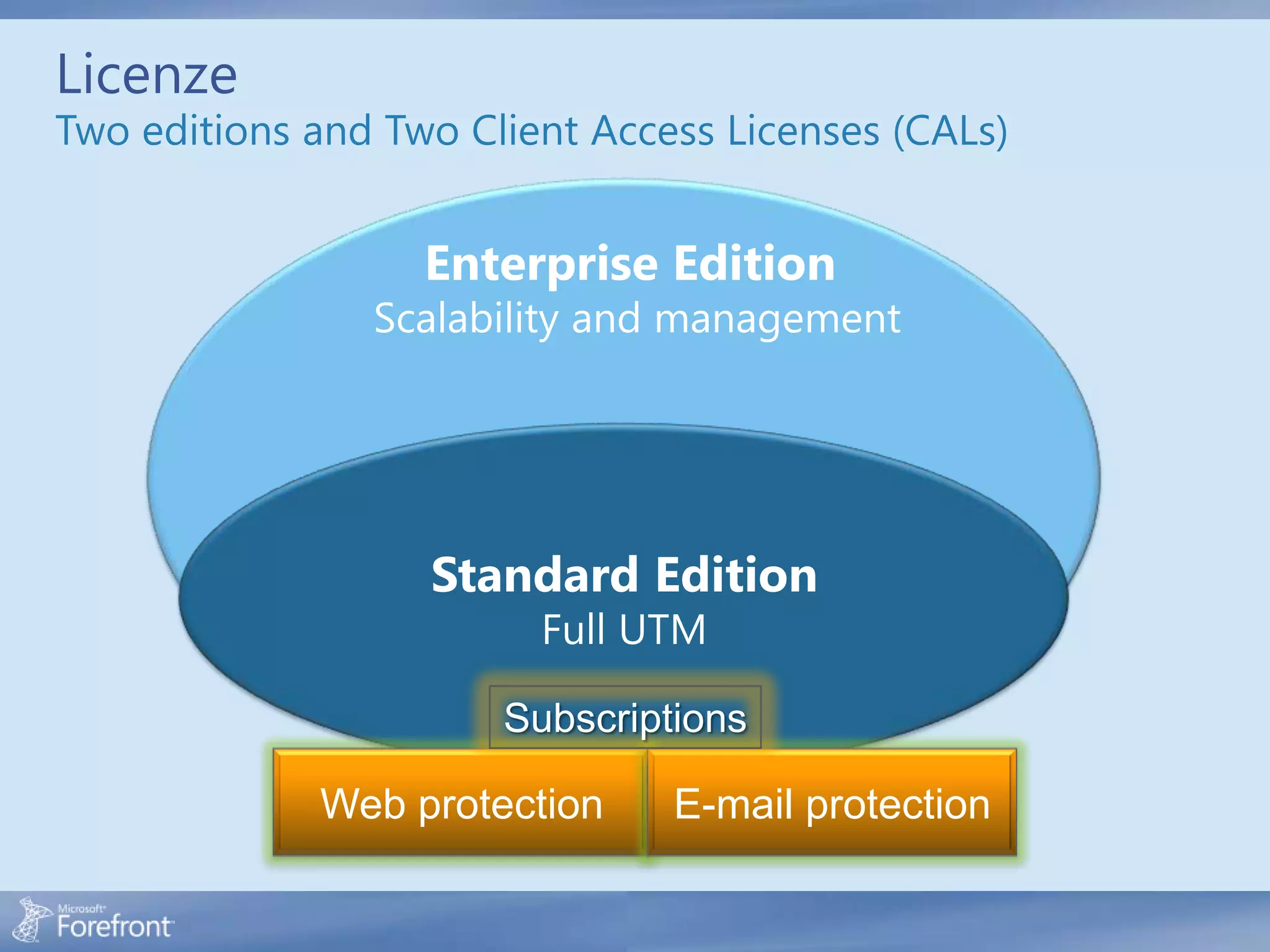
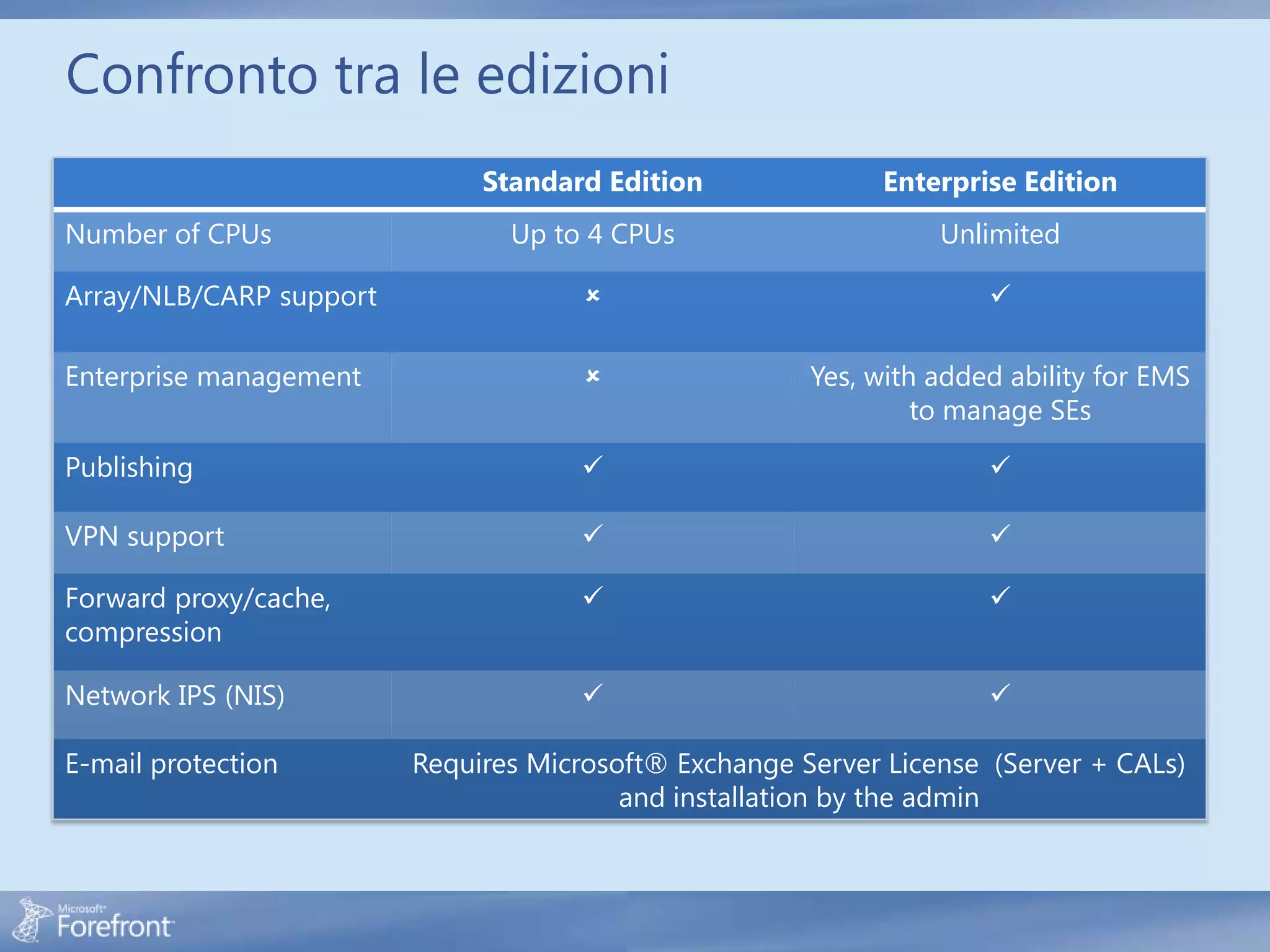
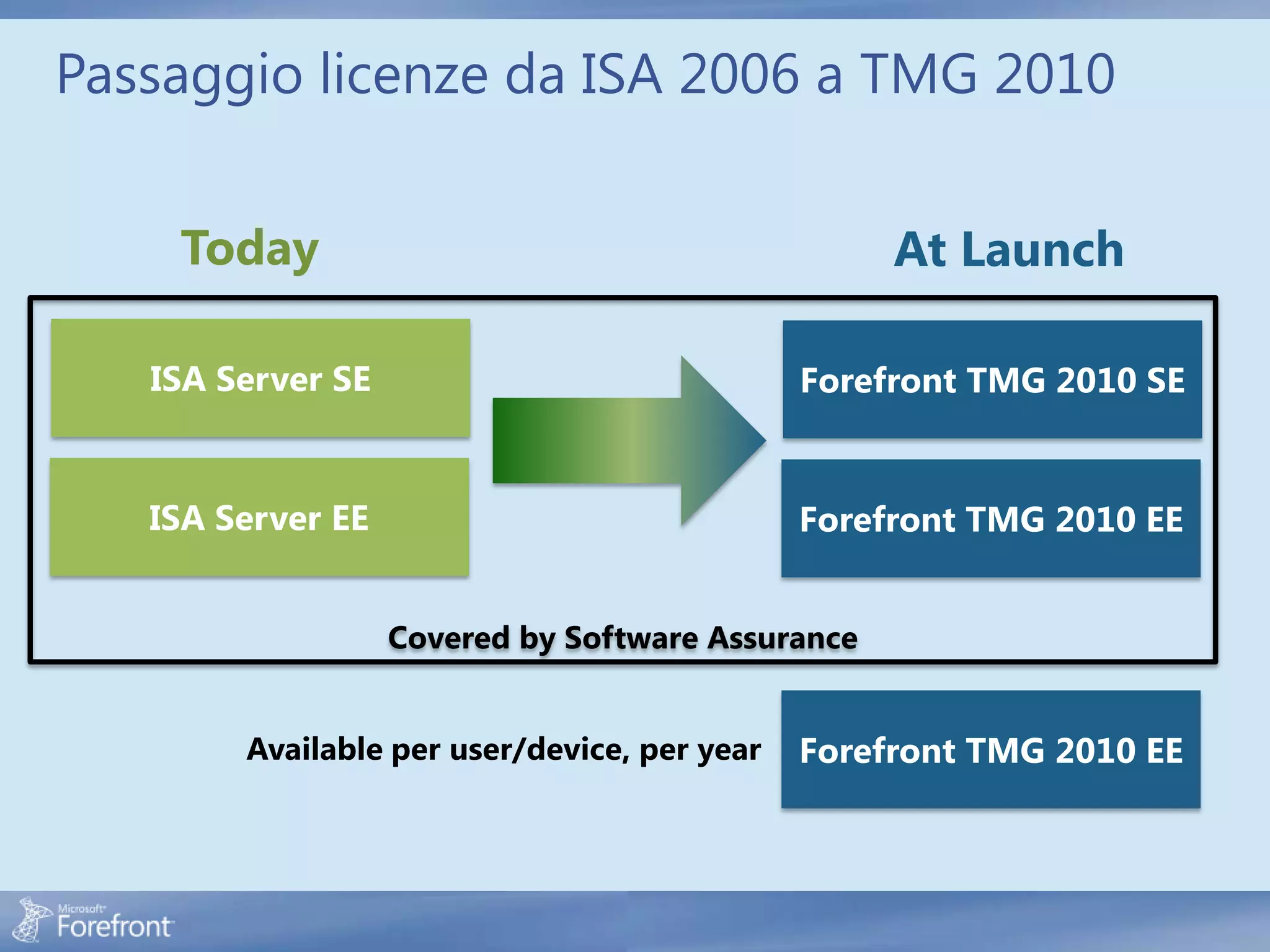
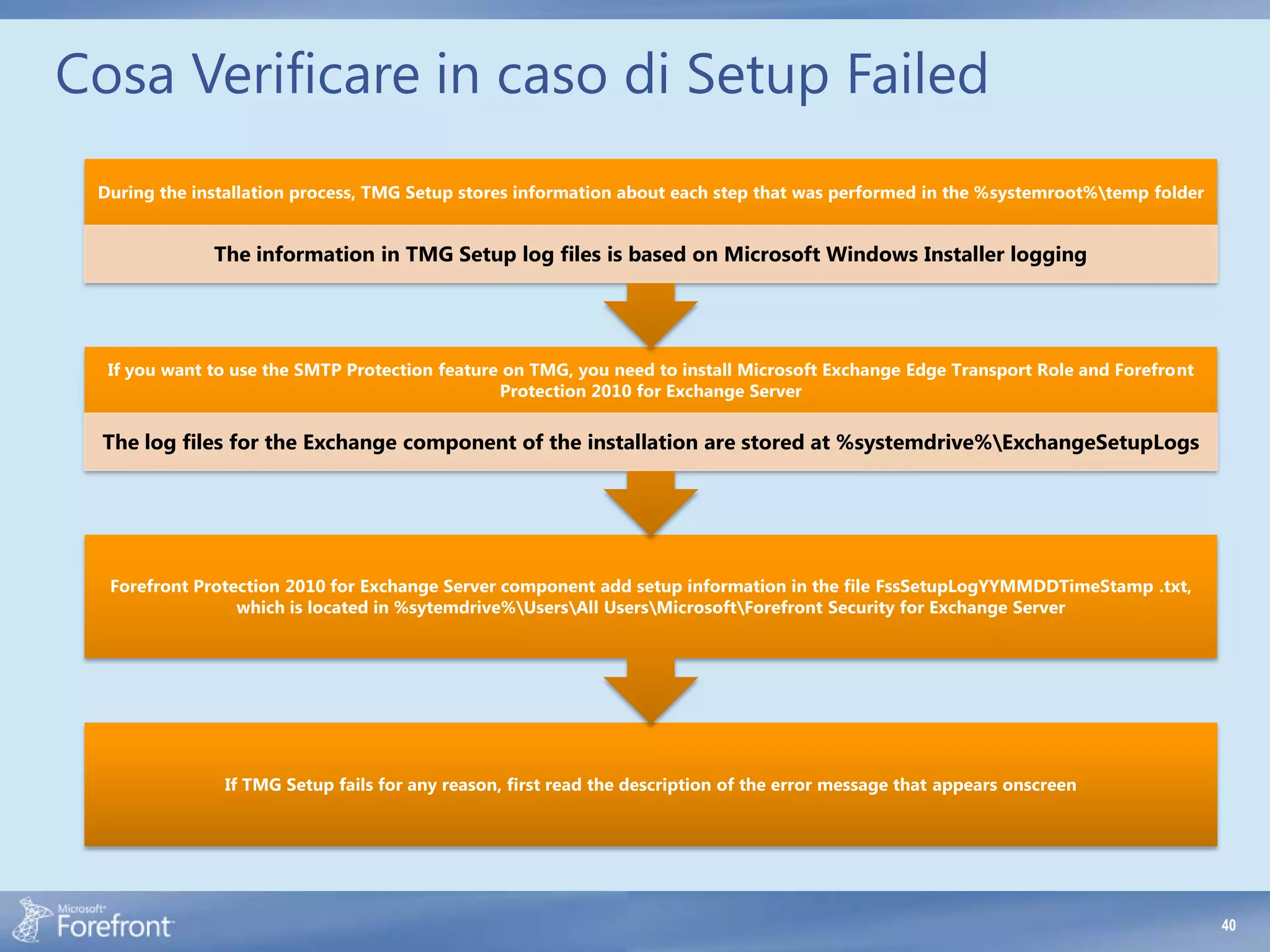
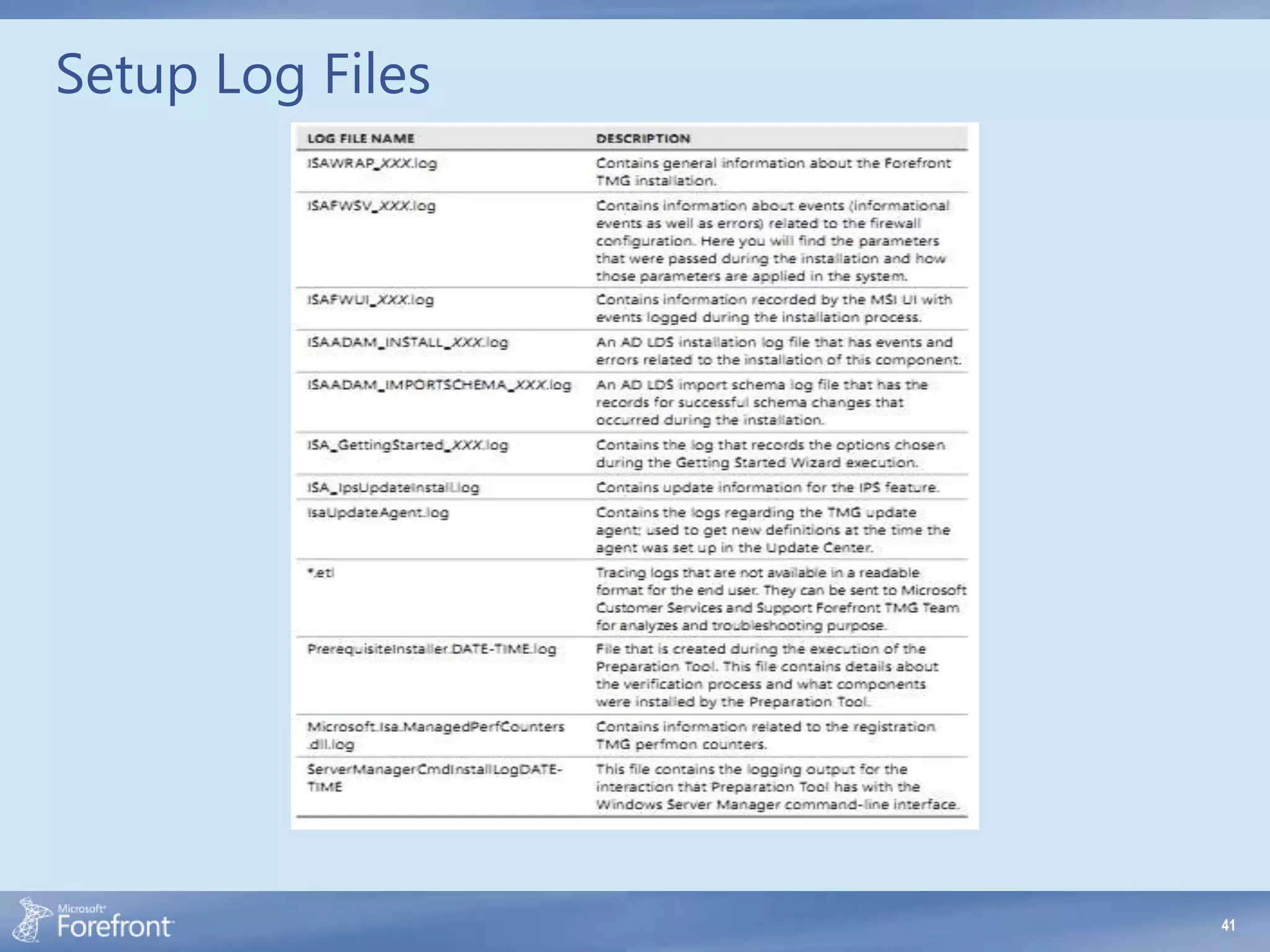
Here are some common configuration errors in Forefront TMG and suggestions to resolve them:
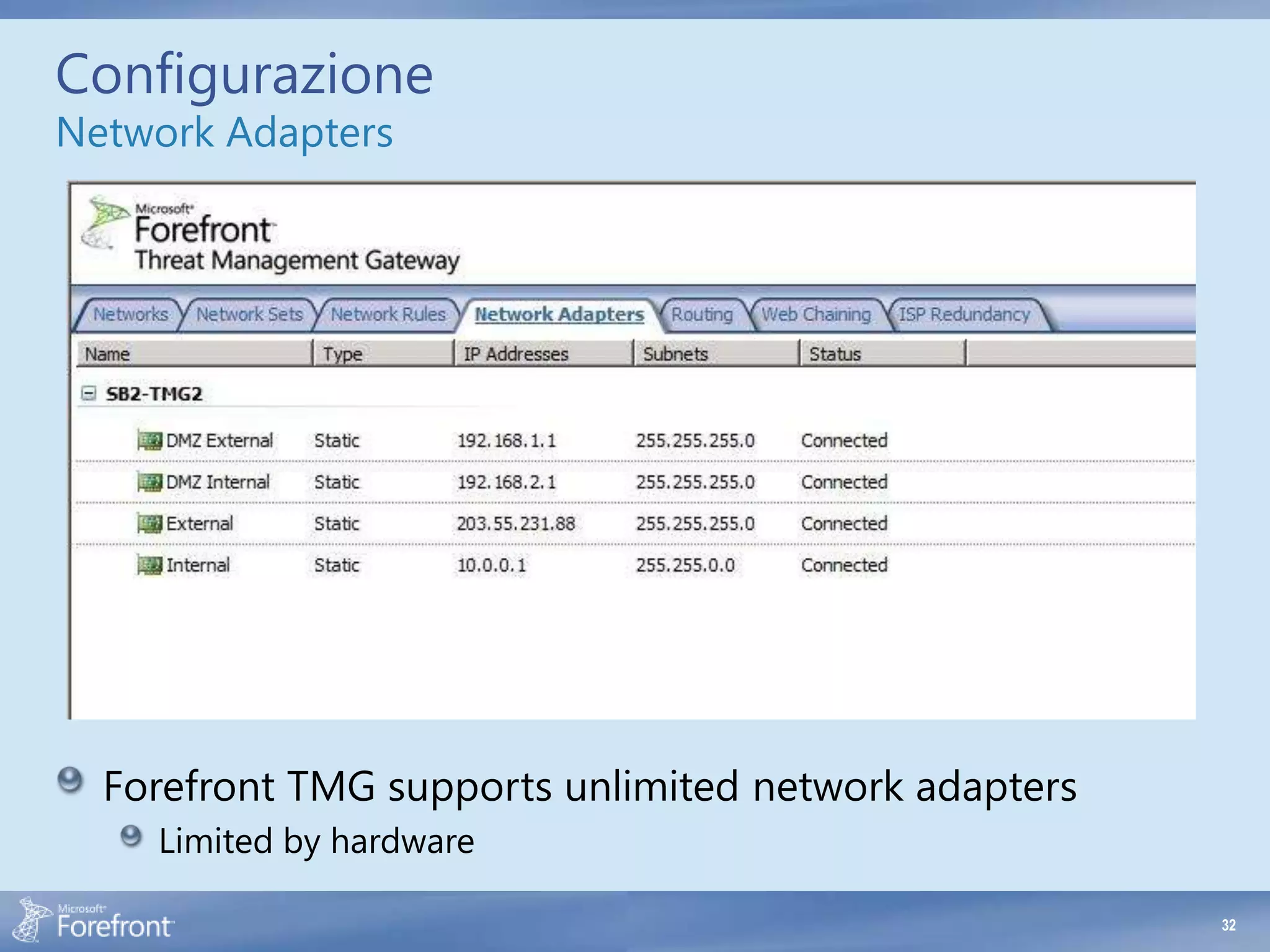
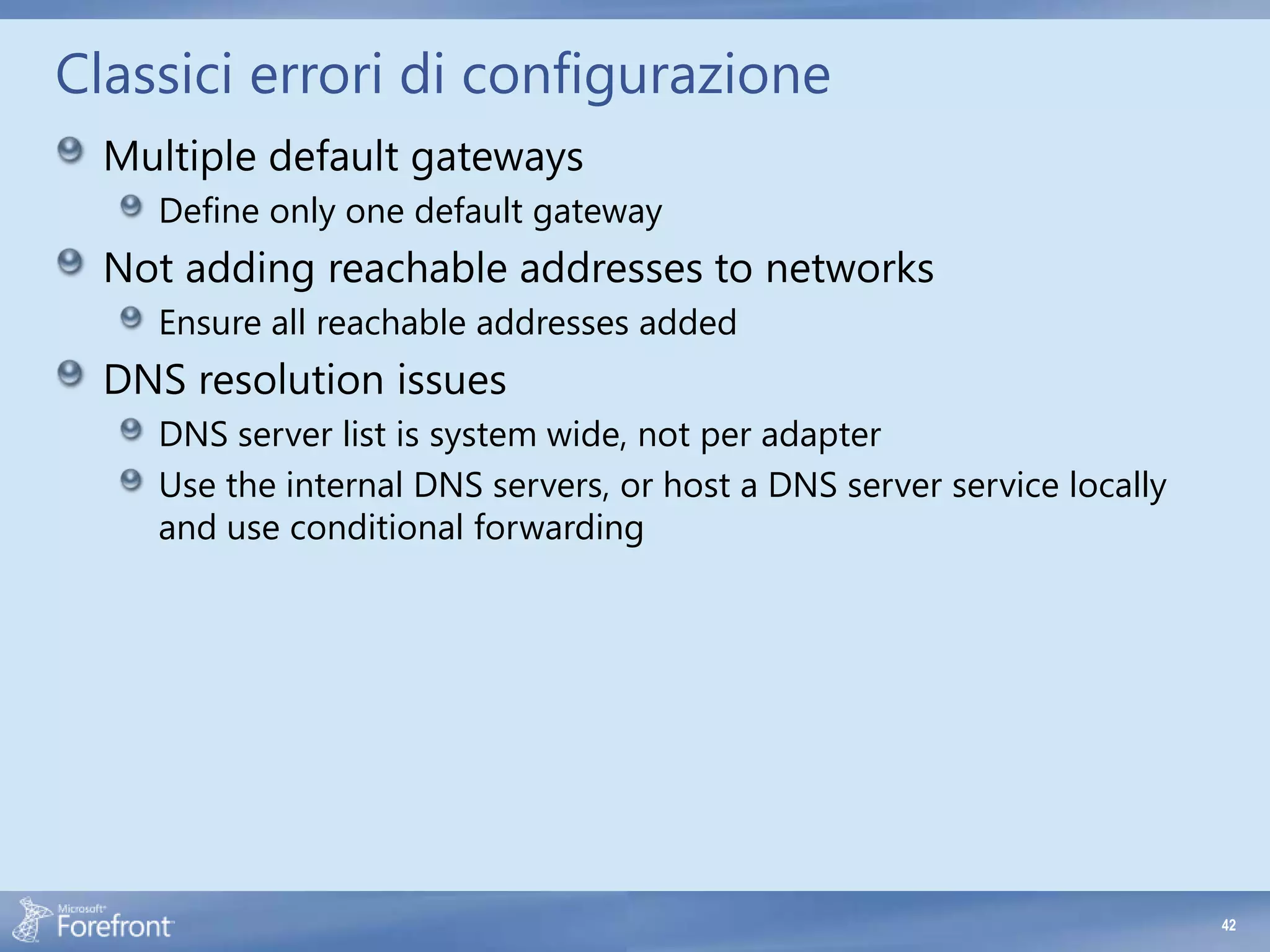
- Defining multiple default gateways on the same network adapter. TMG only supports one default gateway per adapter.
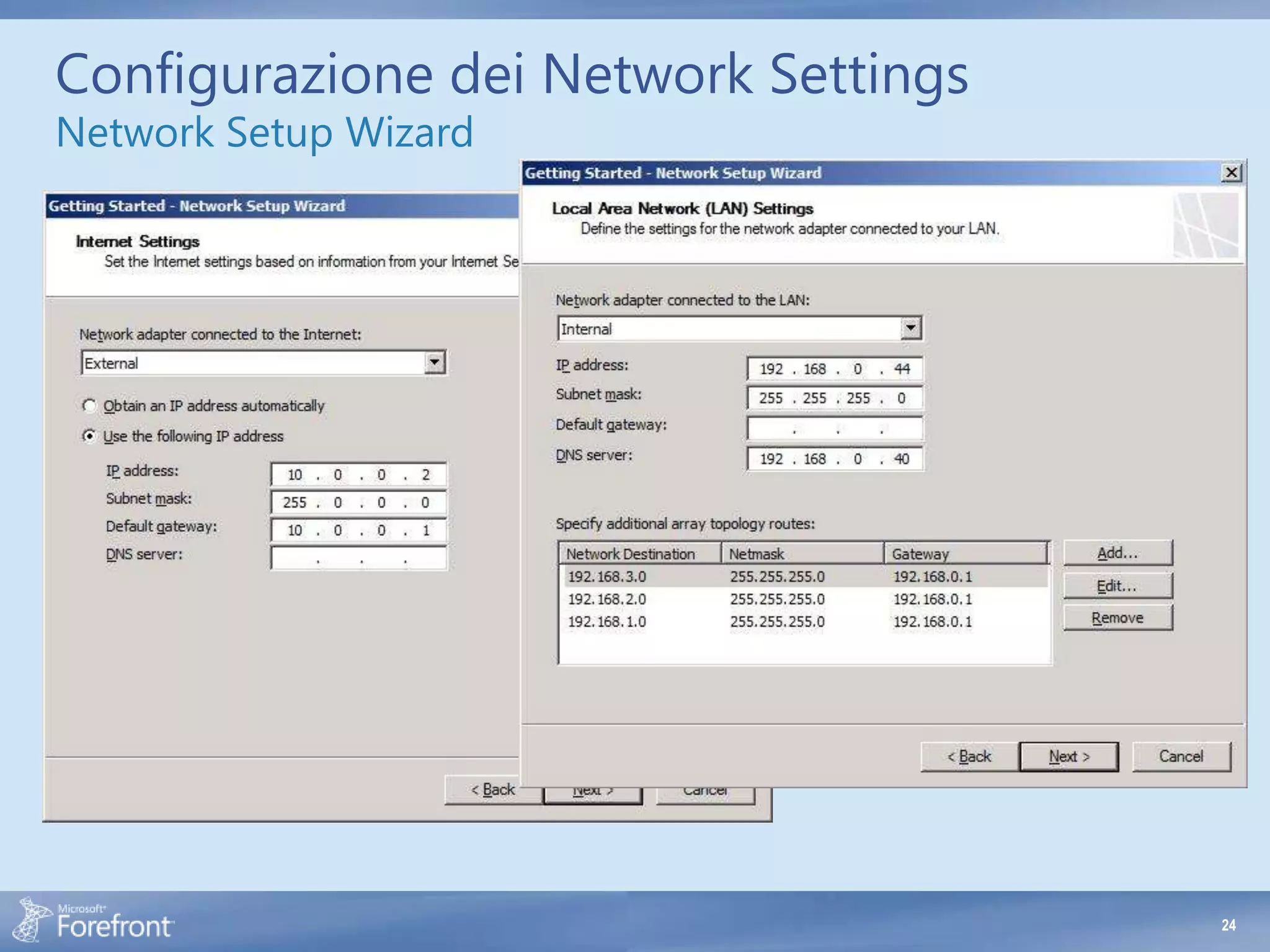
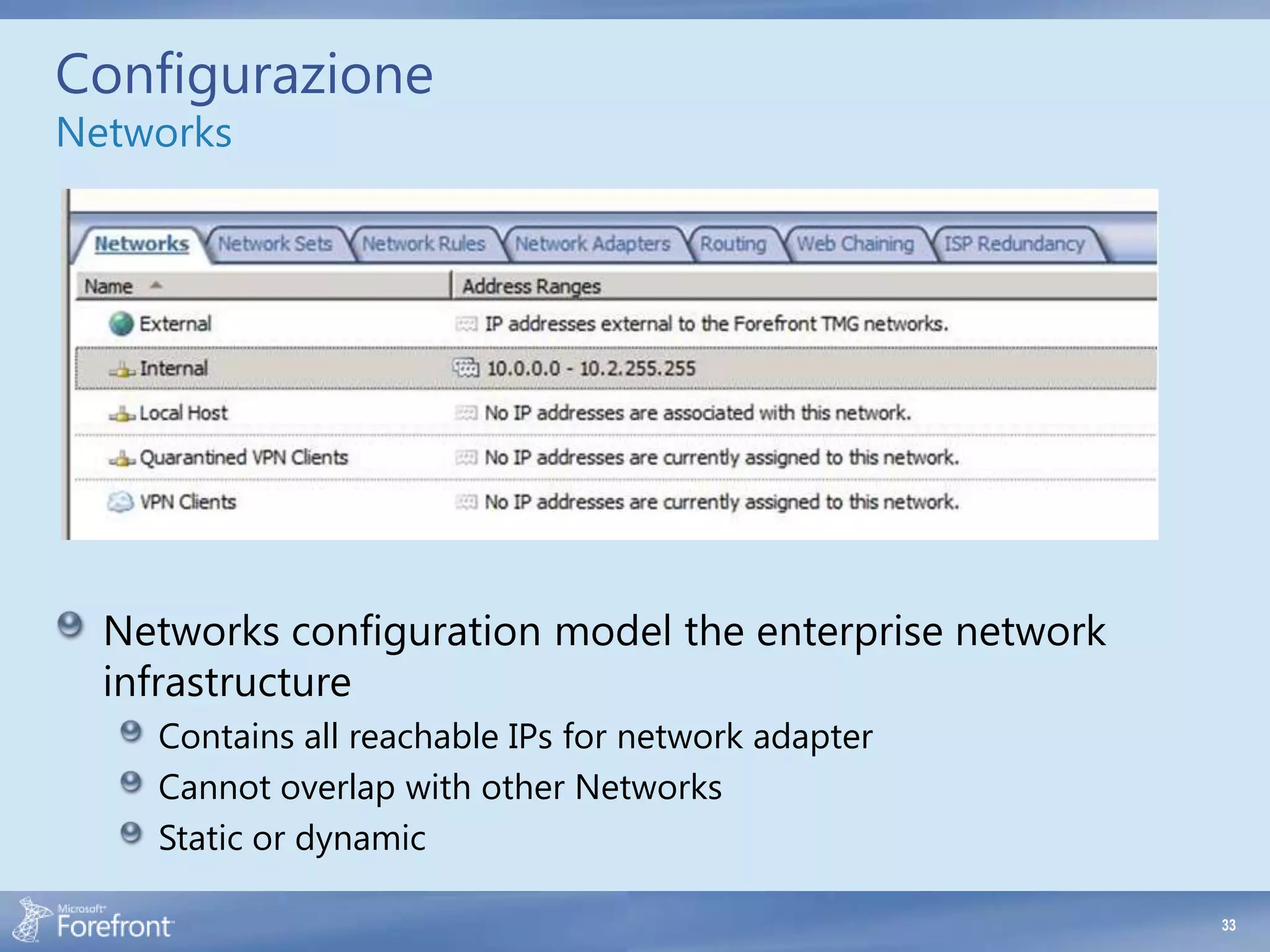
- Not adding all reachable IP addresses and subnets to the appropriate network definitions. This prevents proper routing and policy evaluation.
- DNS resolution issues due to incorrect DNS server configuration. TMG uses the system-wide DNS server list, not per adapter. Ensure the internal DNS servers are used, or host a local DNS server service using conditional forwarding.
- Overlapping network definitions. Network ranges cannot overlap to prevent ambiguity in routing and policy matching.
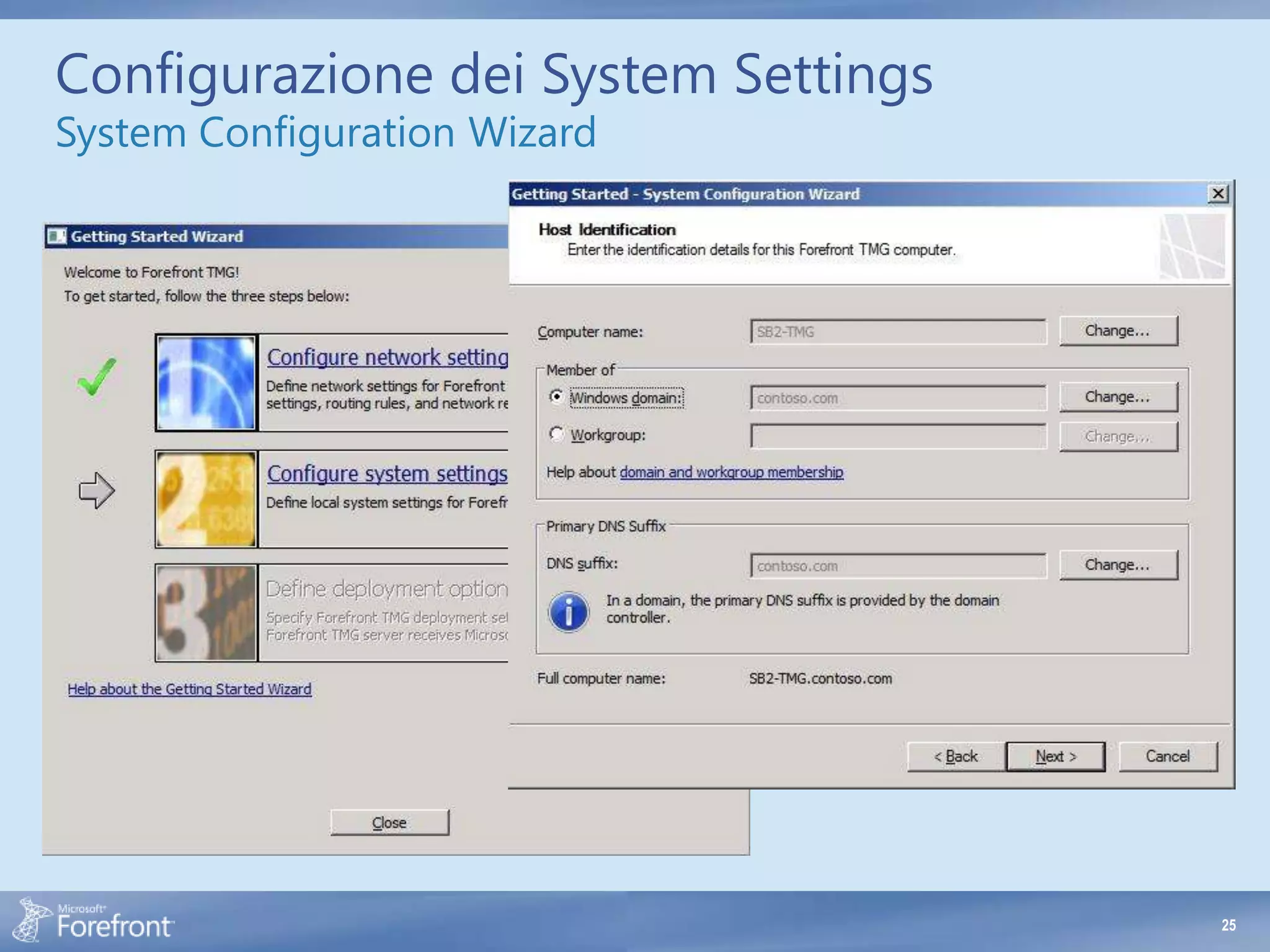
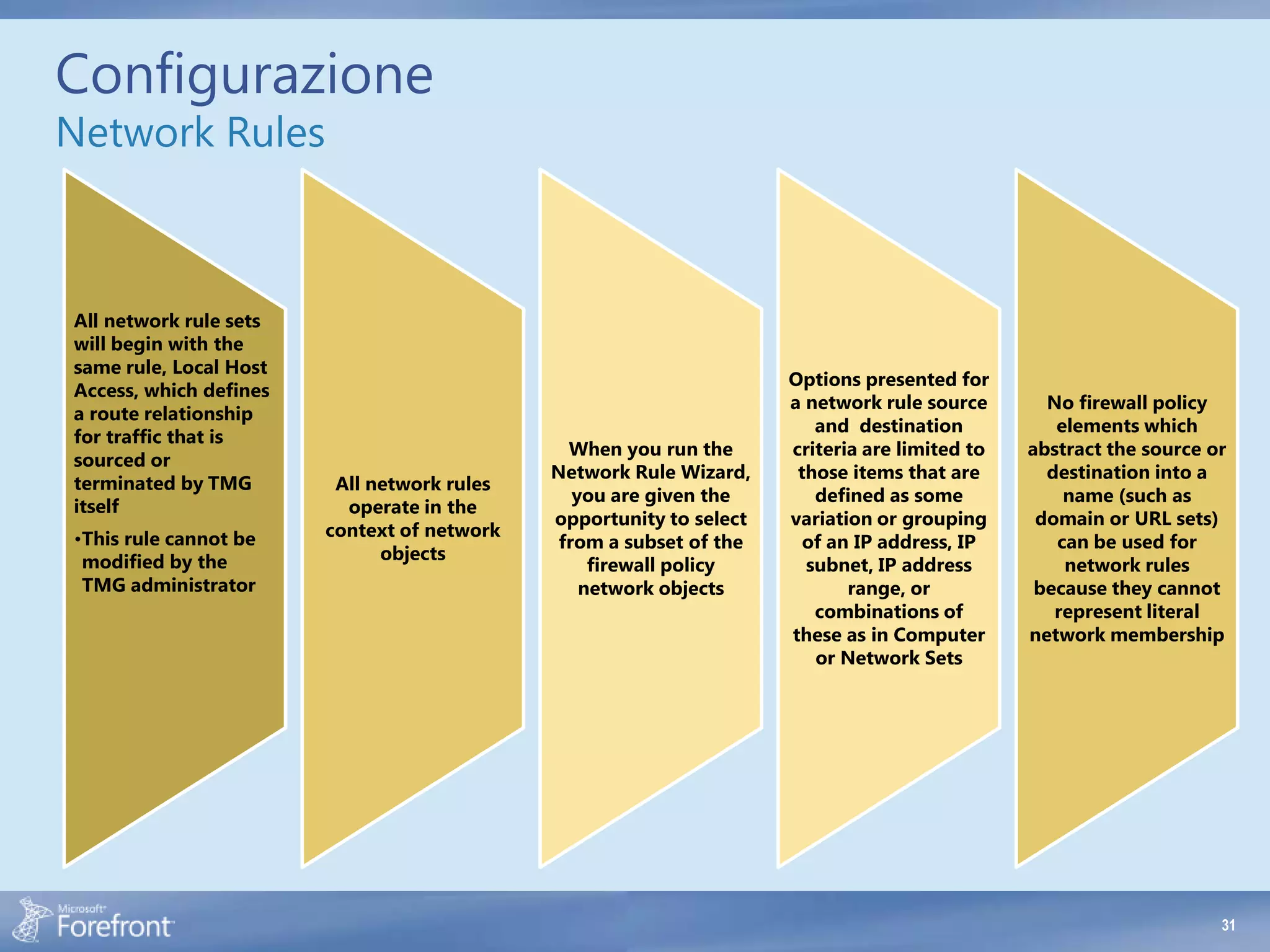
- Incorrect network relationships defined between networks. The relationship must