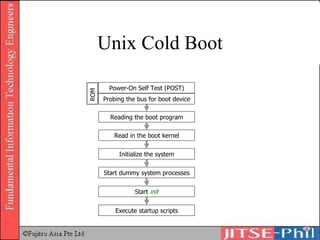
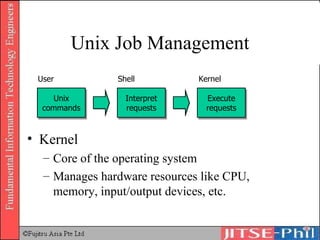
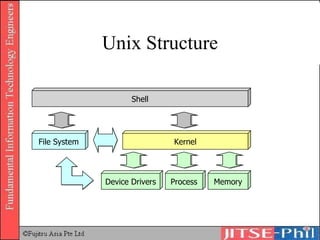
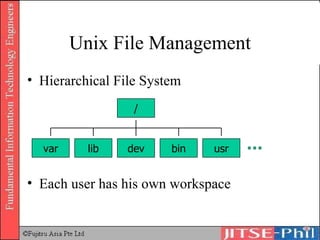
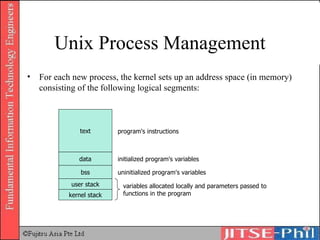
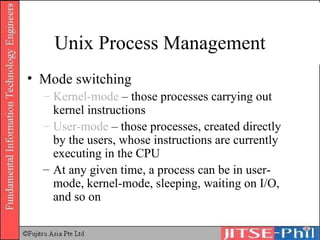
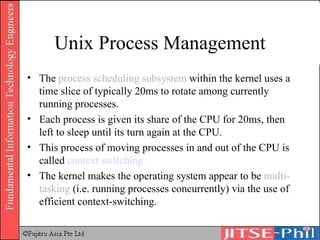
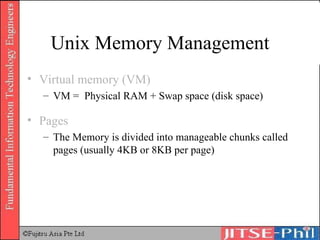
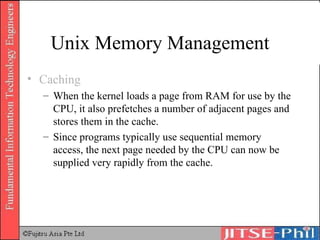
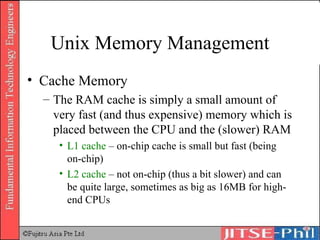
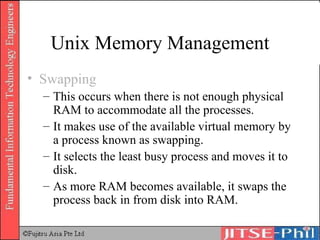
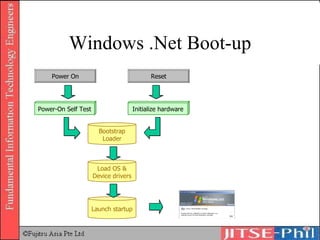
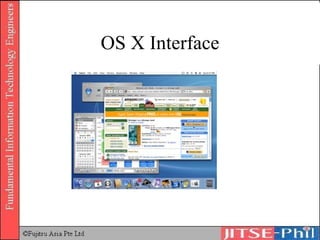
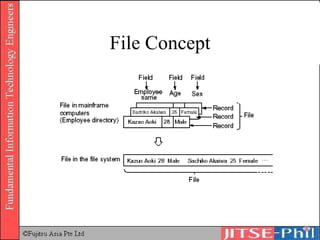
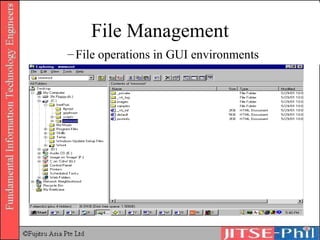
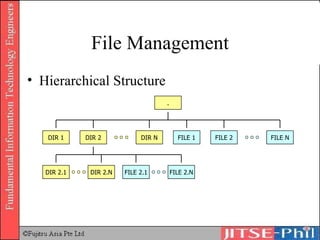
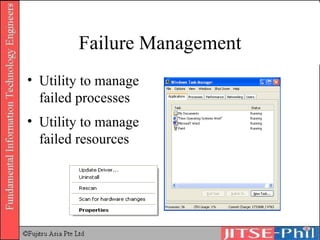
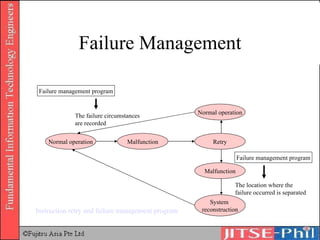
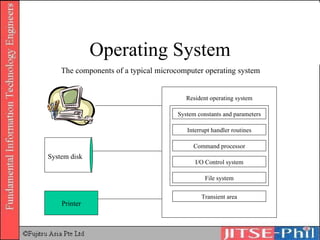
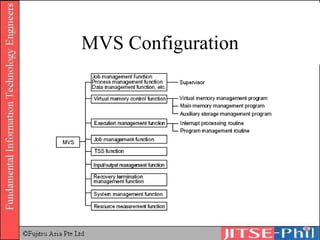
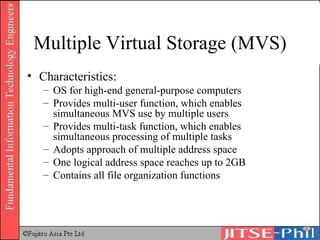
The document provides an overview of basic computer operating systems concepts. It discusses file management, file systems, directories, paths, file operations, and roles in file management. It also summarizes concepts related to security management, failure management, supervisors, and where to find more information on operating systems.
























![Unix Family Tree UNICS (Uniplexed Operating and Computing System) 7 th Edition [1978] BSD (Berkeley Software Distribution) [1969] 5 th Edition [1973] 6 th Edition [1976] SVR5 (System V) [1979] [1983] Sun OS 5.x/Solaris HP HP-UX IBM AIX SGI IRIX DEC Digital UNIX (formerly OSF/1) Sun OS 4.x DEC Ultrix Canon NextStep Apple OS X](https://image.slidesharecdn.com/16-computersystems-basicsoftware2-091127215709-phpapp01/85/16-Computer-Systems-Basic-Software-2-36-320.jpg)