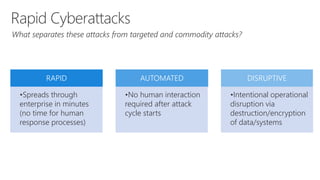
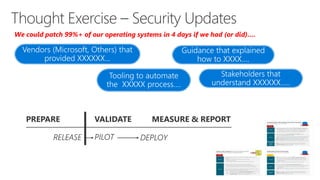
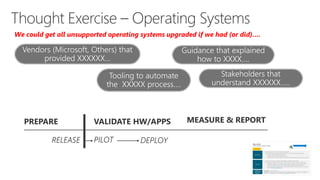
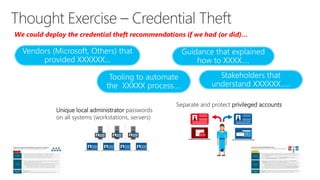
This document discusses recommendations to improve defenses against rapid cyberattacks. It begins with a review of how rapid attacks work, then provides specific recommendations in four areas: attack surface reduction, lateral traversal/securing privileged access, business continuity/disaster recovery, and exploit mitigation. Potential blockers to implementing the recommendations are also identified relating to technology, processes, and stakeholder buy-in. Next steps include assigning action items identified in the meeting.























![User Impact – Minimal negative impact on end-user experience
IT Impact – Deployment and management associated with the solutions
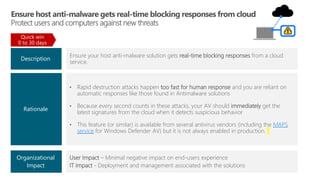
Email - Implement advanced protections for phishing attacks that include:
• Attachment/URL “sandbox detonation” – Protect against unknown malware and viruses
• Time of Click Protections – rewrite links to protect against malicious links in e-mail messages at
time of click (vs. just at time of send)
Browsing - Implement advanced browser protection solutions that include:
• Website analysis – Identify known malicious sites and suspicious site behavior
• Download file analysis – Evaluate downloaded files to warn if it came from a known malicious site
or is new/unknown (not on list of popular programs)
Organizational
Impact
Description
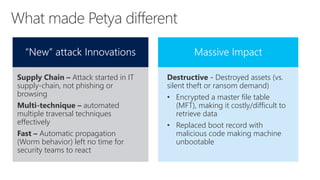
While Petya (and WannaCry [unconfirmed]) did not start with e-mail or browsing, this is an
extremely unusual phenomenon for cyber attacks.
• Phishing/Browsers are overwhelmingly used for almost all other attack patterns, so they
are very likely to be included in future attacks
Rationale
Quick win
0 to 30 days](https://image.slidesharecdn.com/mitigatingrapidcyberattacks-171128200751/85/Mitigating-Rapid-Cyberattacks-43-320.jpg)