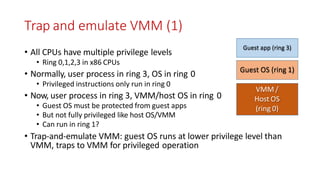
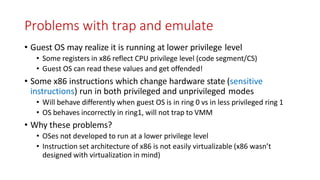
VMMs use various techniques to virtualize CPU, memory, and I/O for multiple VMs. For CPU virtualization, approaches include paravirtualization (modifying guest OS), full virtualization (binary translation), and hardware-assisted virtualization (using CPU virtualization mode). For memory, shadow paging combines guest and host page tables, while EPT uses separate tables. I/O is virtualized through emulation or direct device passthrough. The VMM handles scheduling VMs and trapping privileged operations to provide isolation between VMs.