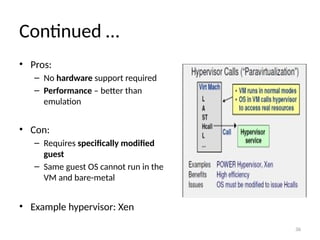
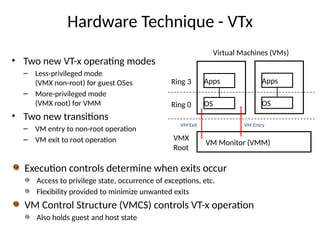
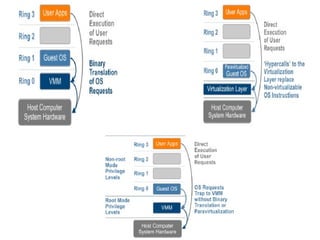
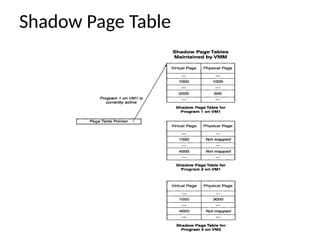
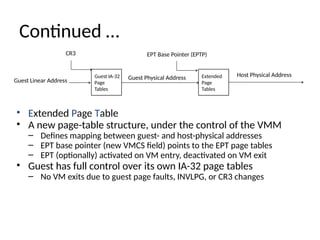
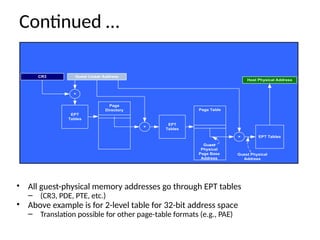
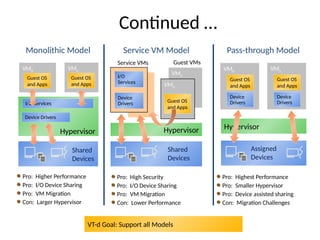
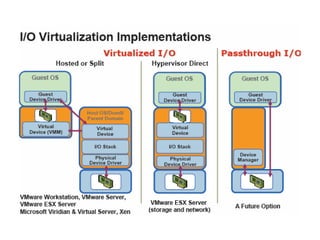
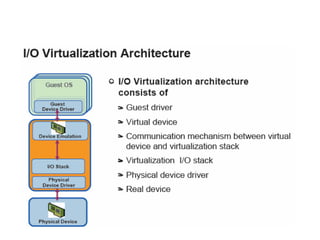
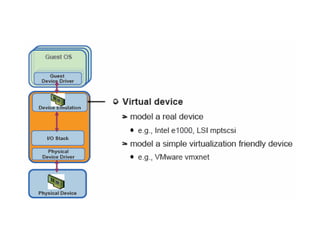
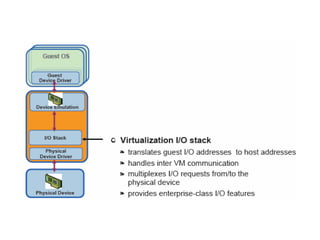
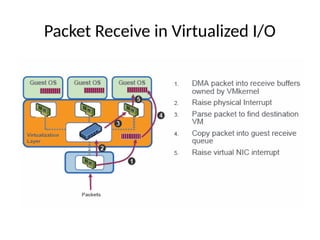
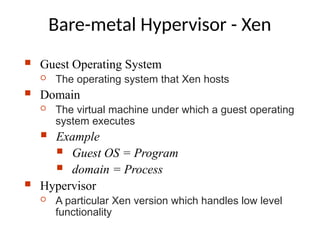
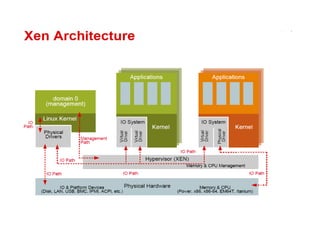
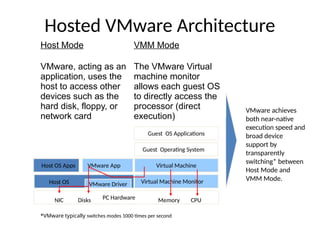
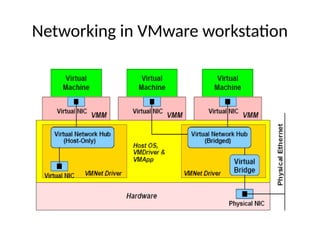
The document provides a comprehensive overview of virtualization, defining it as the division of computer resources into multiple execution environments to enhance resource utilization. It explores the history of virtualization, the challenges associated with x86 architecture, various types of virtual machines, and key techniques in CPU and memory virtualization. The document also discusses hypervisors, emphasizing their role in enabling virtual machines to operate on physical hardware, and compares different virtualization technologies and their implications.










![29
1.Emulation
• Do whatever the CPU does but in software
• Fetch the next instruction
• Decode – is it an ADD, a XOR, a MOV?
• Execute – using the emulated registers and memory
Example:
addl %ebx, %eax
is emulated as:
enum {EAX=0, EBX=1, ECX=2, EDX=3, …};
unsigned long regs[8];
regs[EAX] += regs[EBX];](https://image.slidesharecdn.com/virtualizationnew-240915024230-ac2b7d6e/85/Operating-system-Virtualization_NEW-pptx-28-320.jpg)