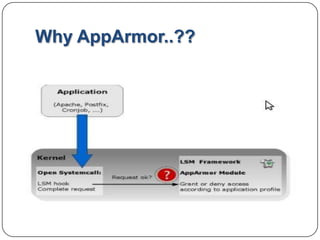
The document discusses AppArmor, a security framework that protects Linux systems and applications from external threats by enforcing good program behavior and access privileges. It can generate profiles for individual programs that define allowed system resources and privileges. Profiles include rules for filesystem access, capabilities, and network access. The document provides an example profile and discusses profile types, generation, and modes like enforce and complain that are used to test and implement profiles.







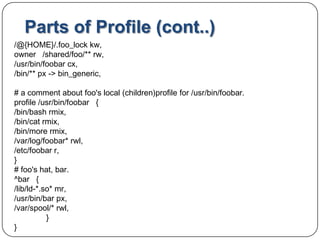
![Parts of Profile:Example: Hypothetical application -- /usr/bin/foo#include <tunables/global>/usr/bin/foo{ #include <abstractions/base> capability setgid , network inettcp , link /etc/sysconfig/foo -> /etc/foo.conf, /bin/mount ux, /dev/{,u} random r, /etc/ld.so.cache r, /etc/foo/* r, /lib/ld-*.so* mr, /lib/lib*.so* mr, /proc/[0-9]** r, /usr/lib/** mr, /tmp/ r, /tmp/foo.pid wr, /tmp/foo.* lrw, /@{HOME} /.foo_filerw,](https://image.slidesharecdn.com/apparmor1-110825131731-phpapp01/85/Apparmor-11-320.jpg)