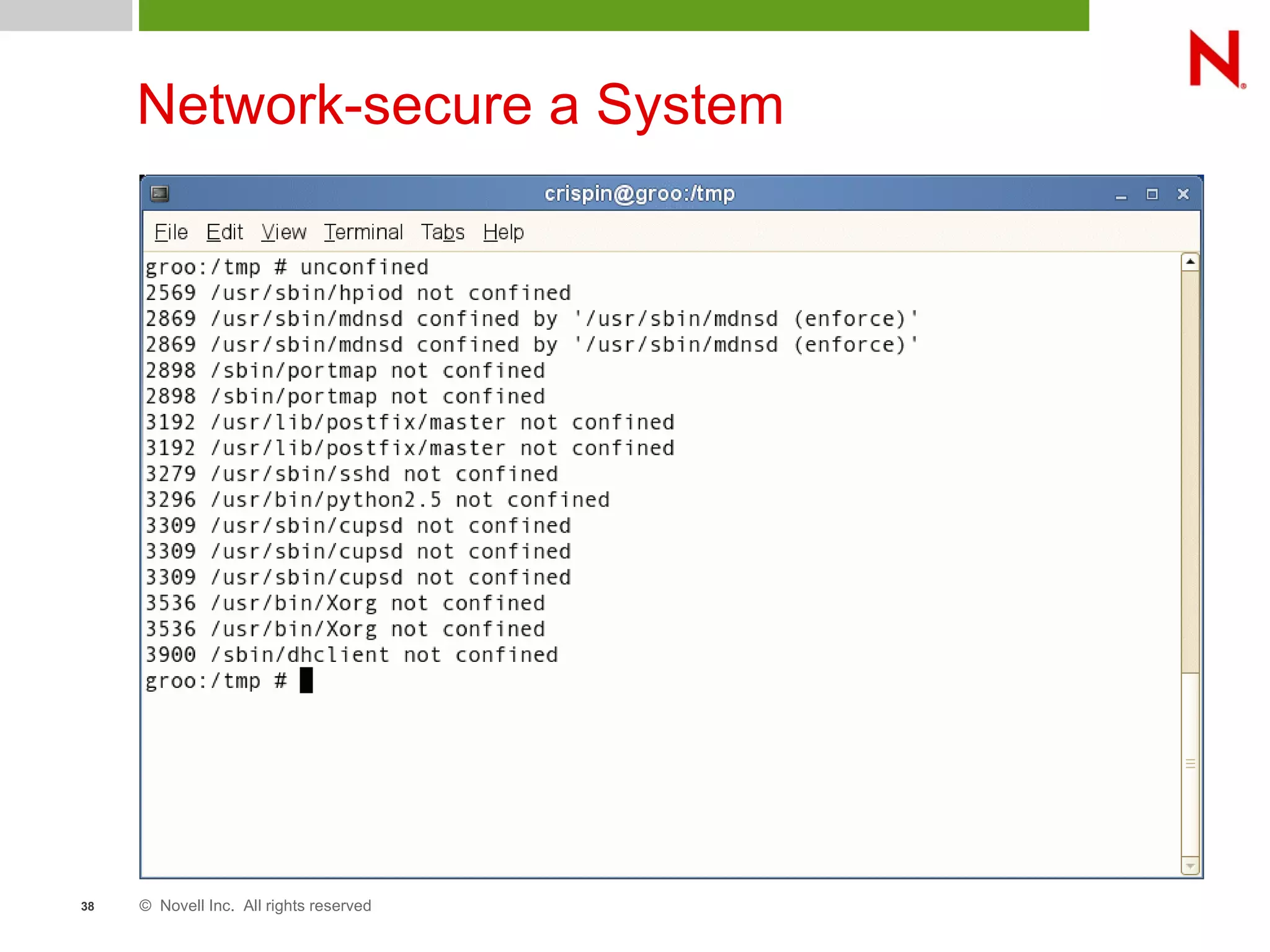
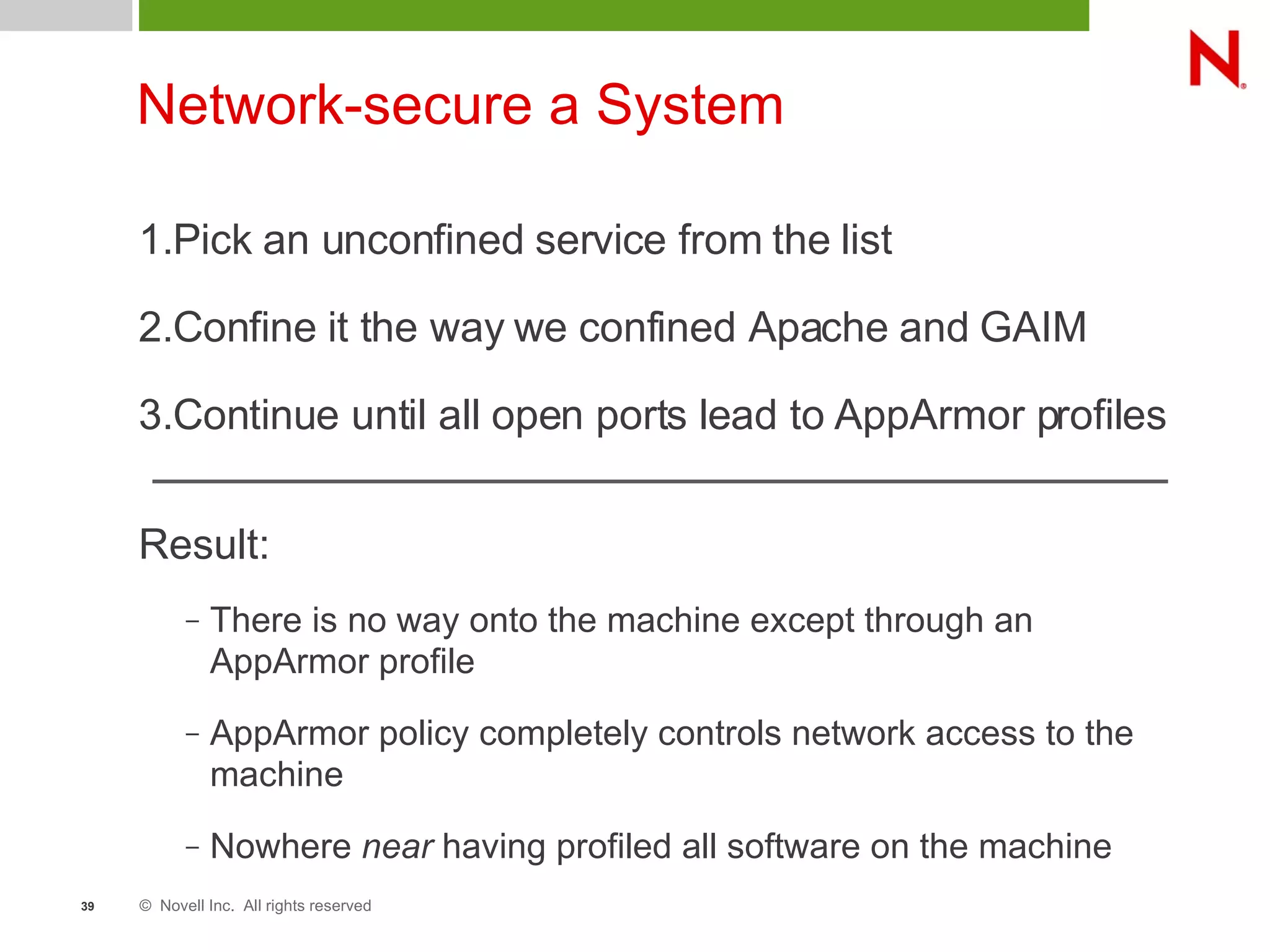
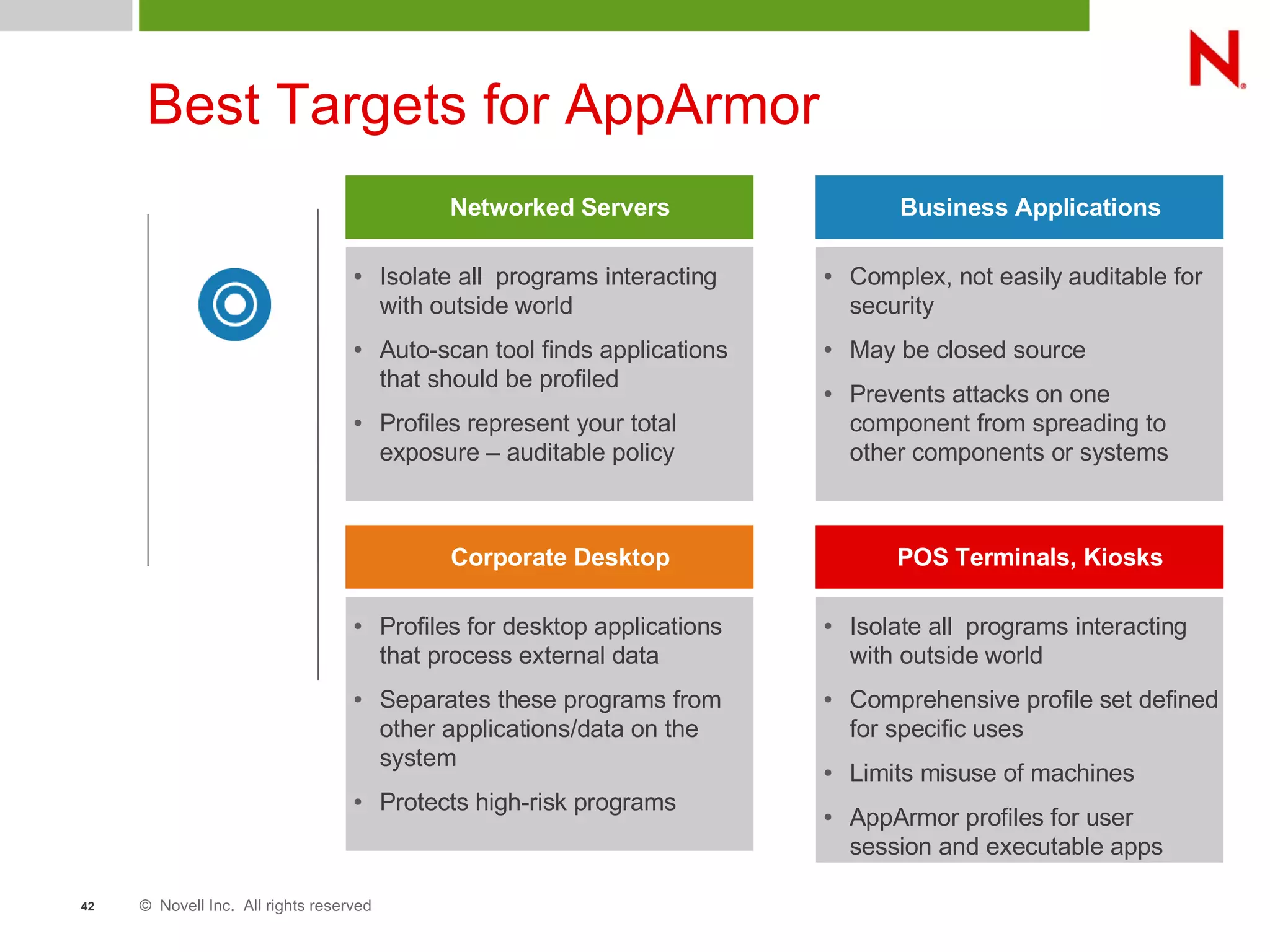
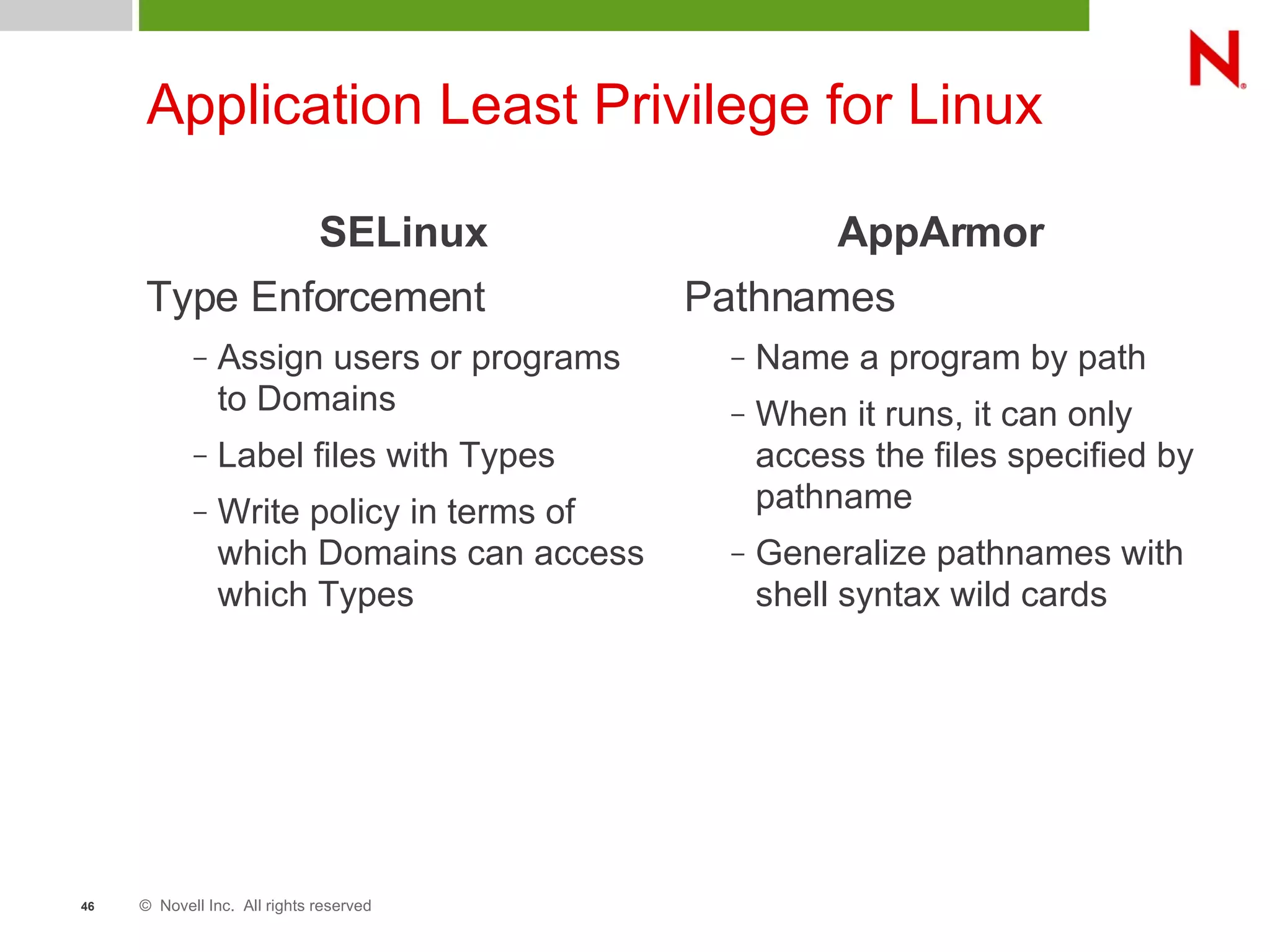
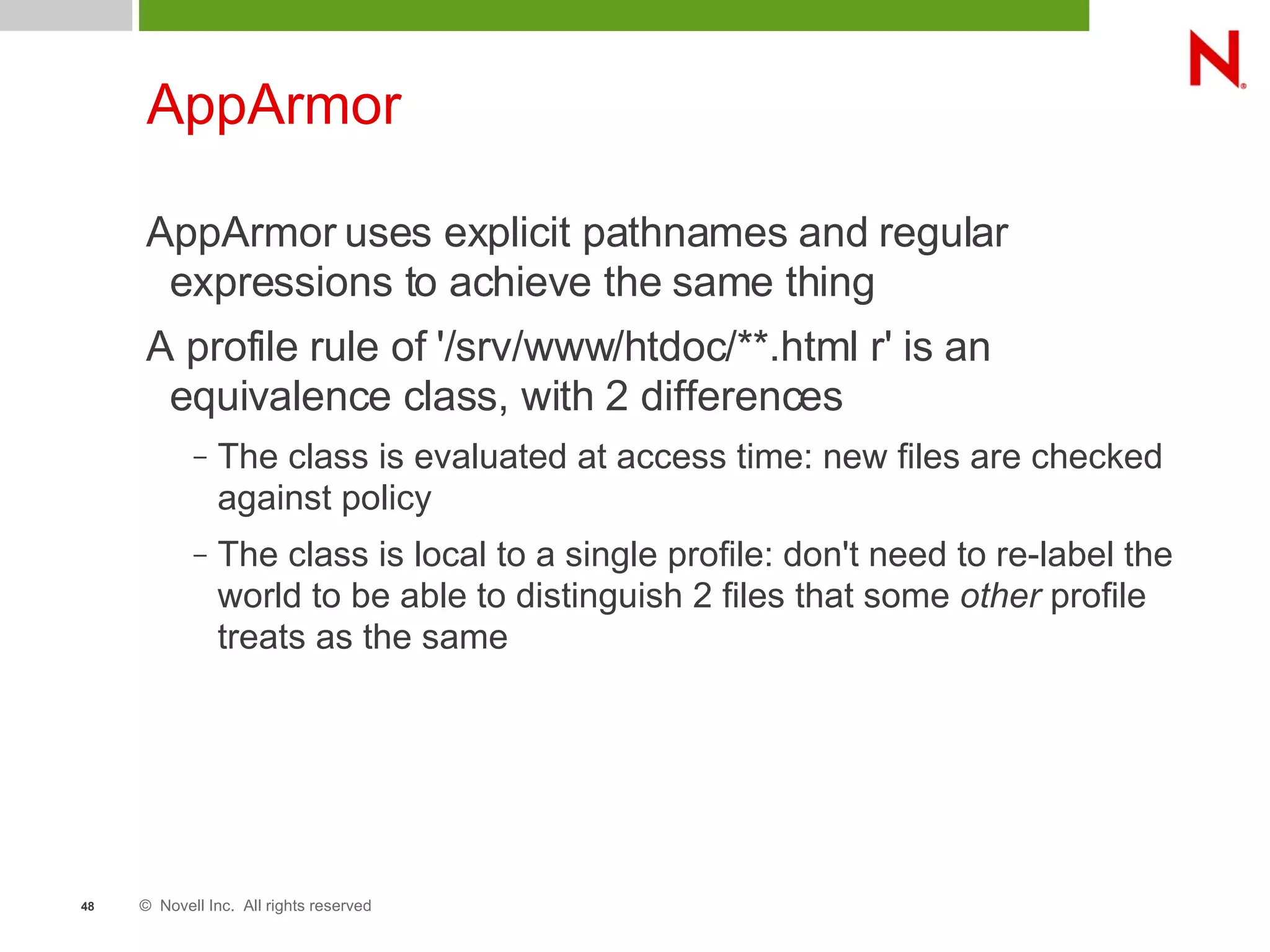
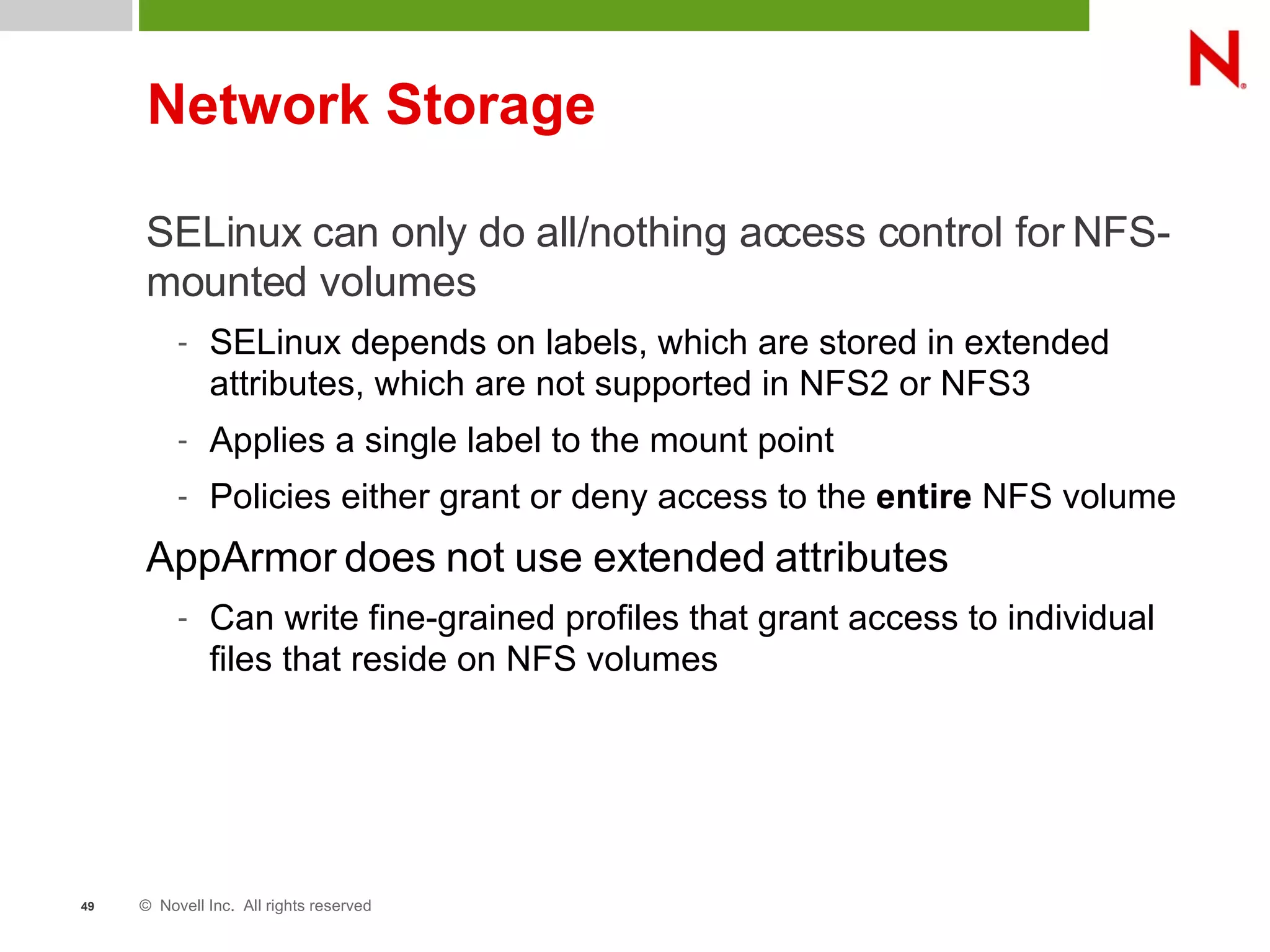
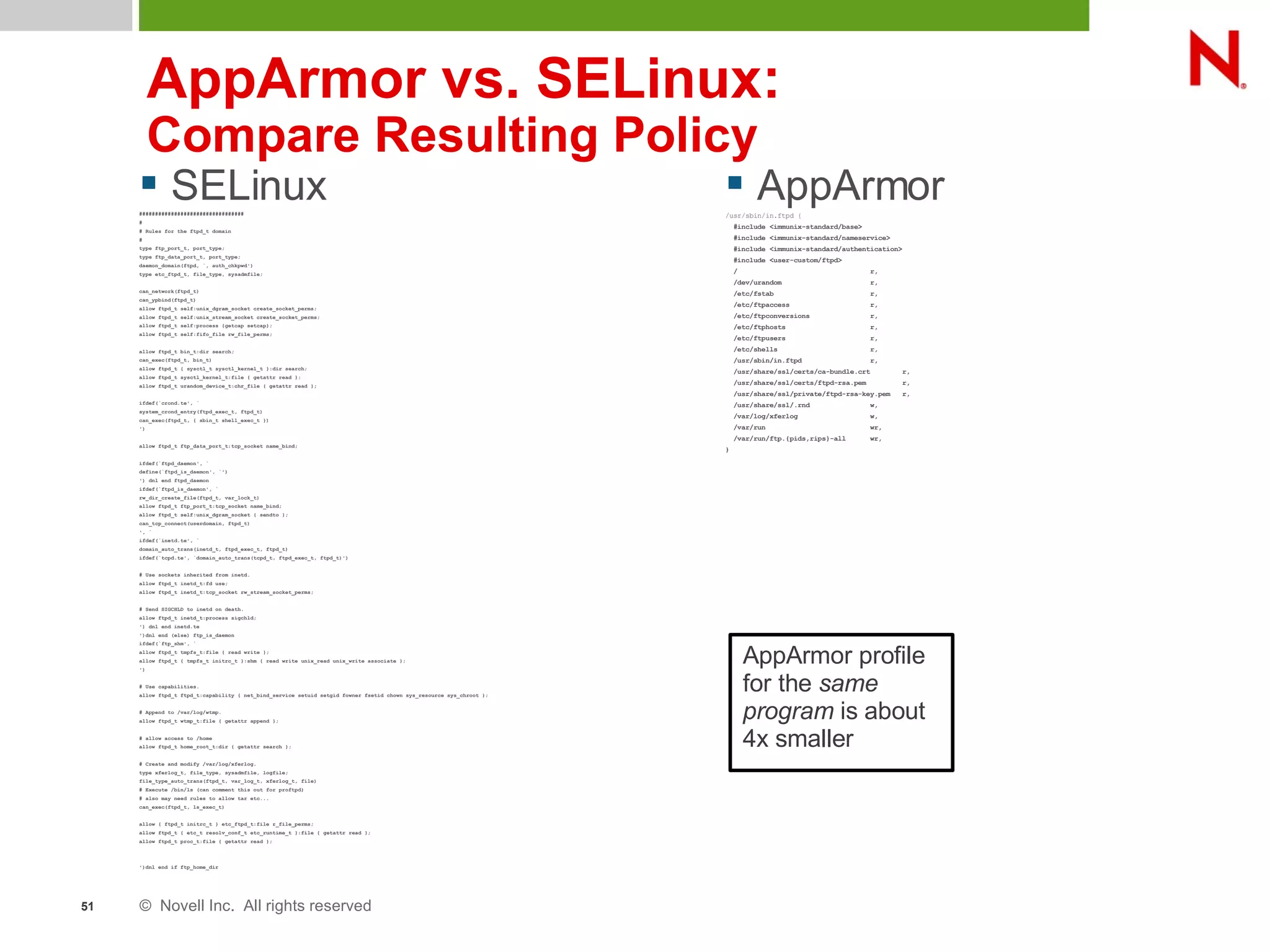
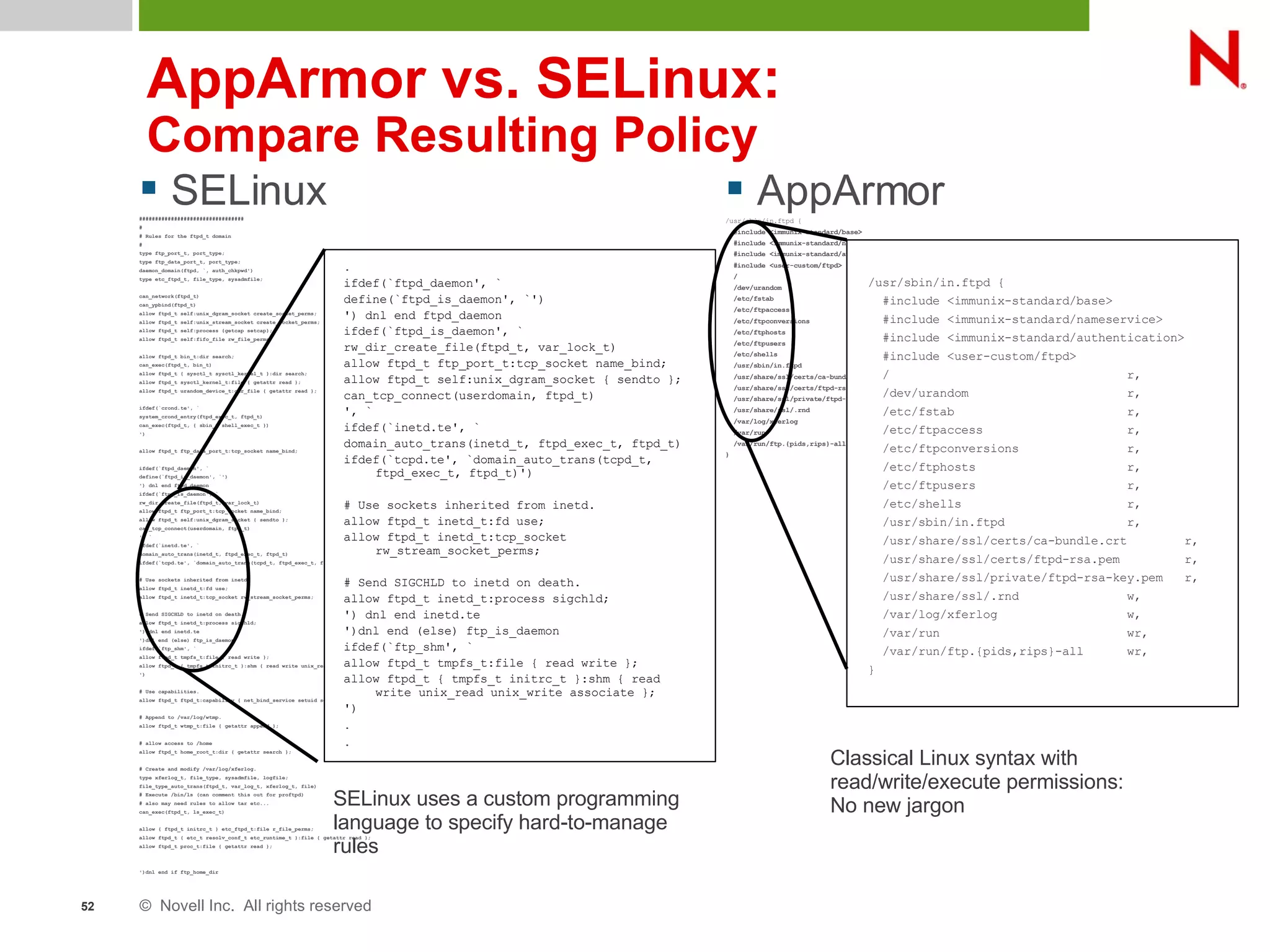
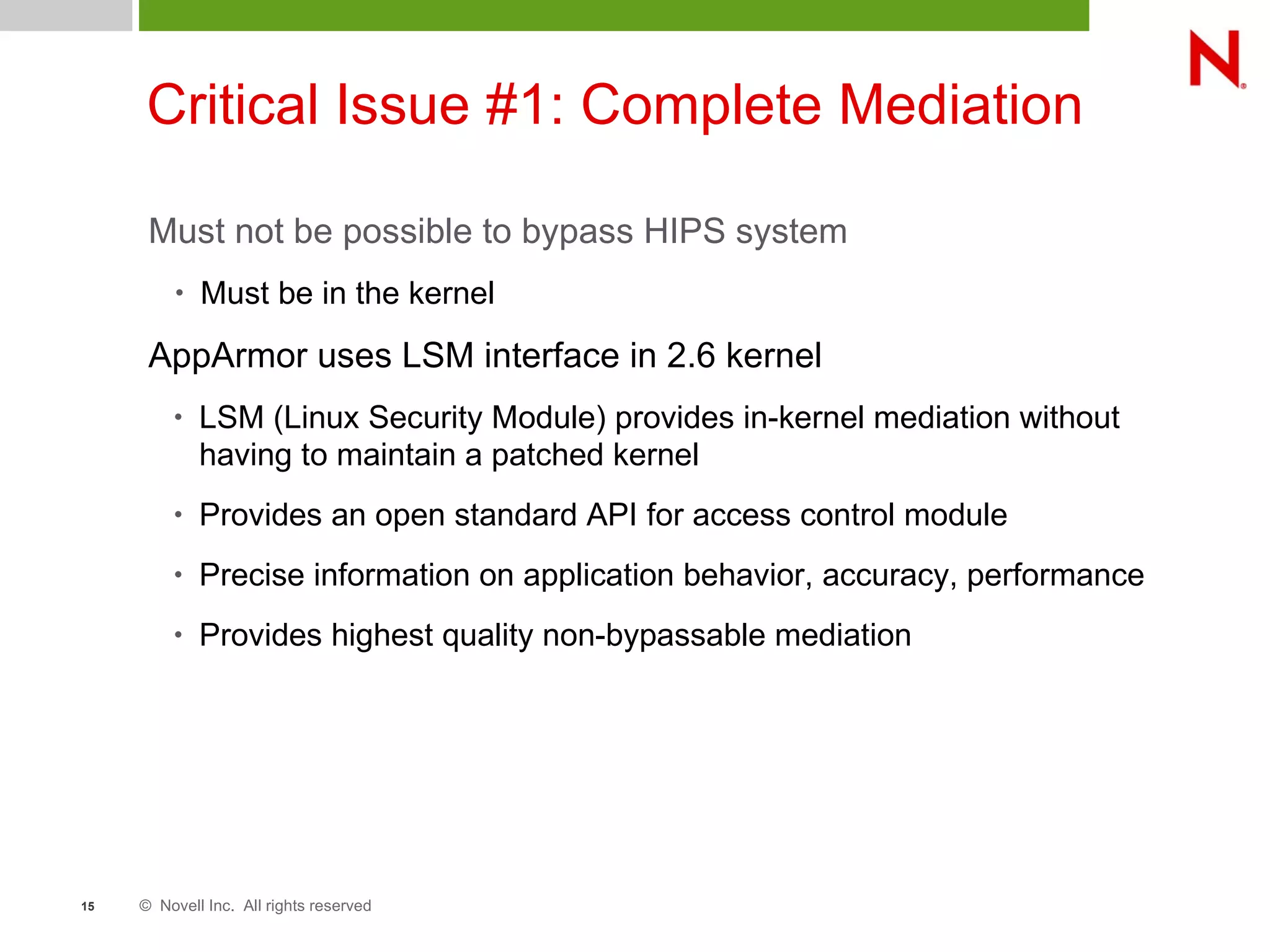
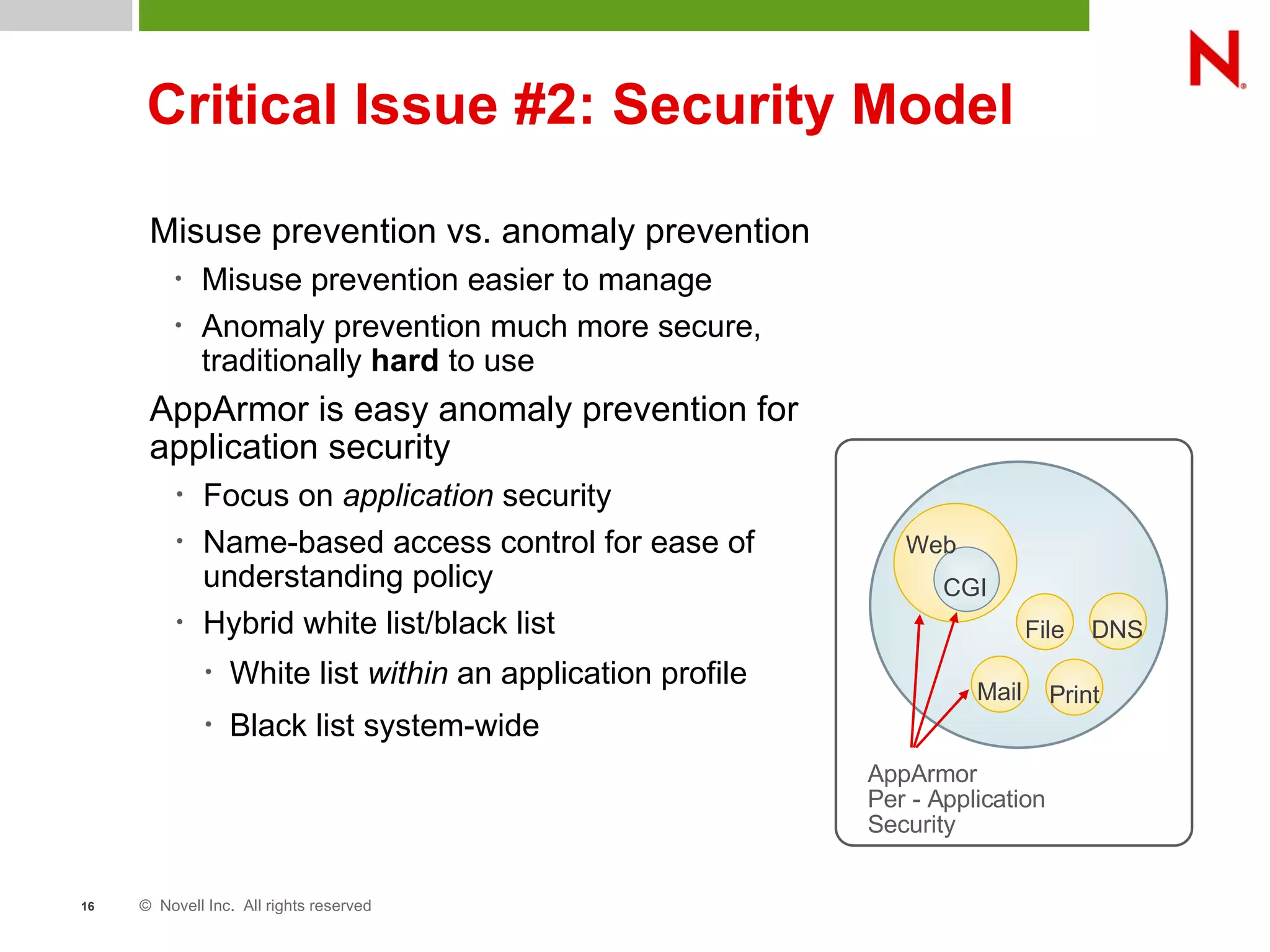
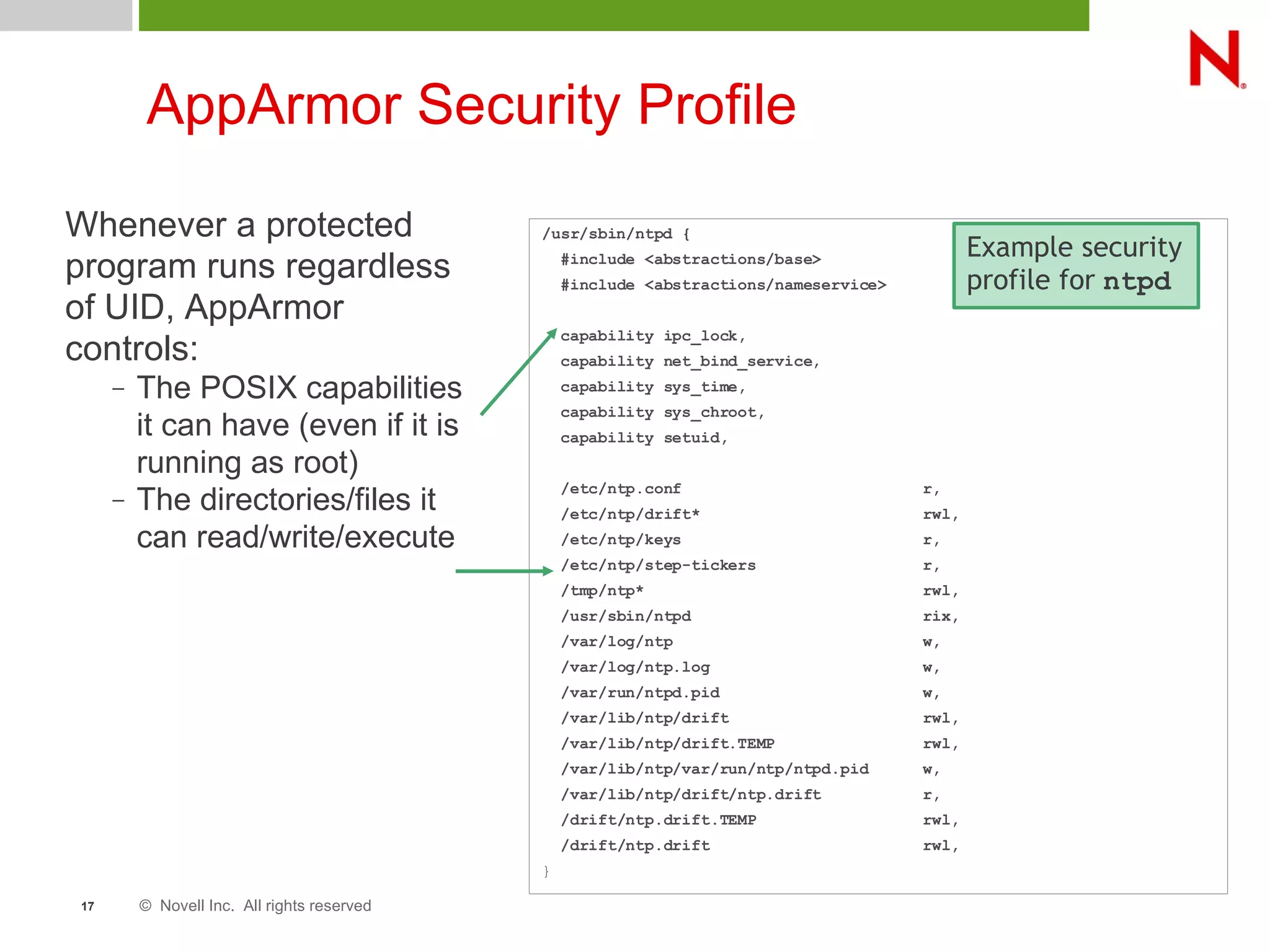
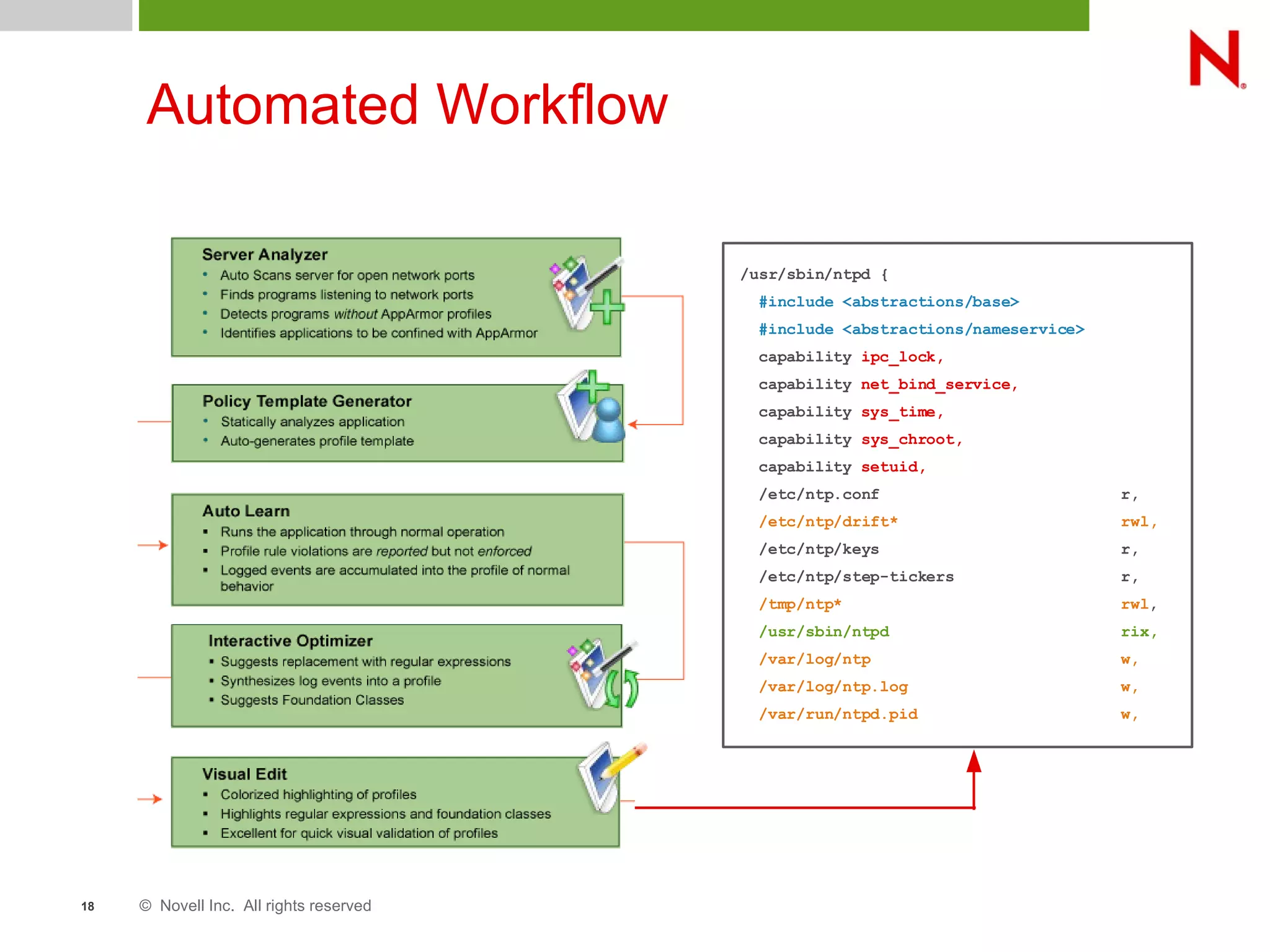
This document discusses AppArmor, a security module for Linux that confines programs to only be able to access specific files and resources. It begins with an overview and introduction to AppArmor, then discusses how AppArmor works by enforcing that applications only access what they need through file and resource restrictions. The document demonstrates AppArmor through a scenario where it prevents a hack on an Apache server. It also discusses best uses cases for AppArmor such as securing networked servers, business applications, and desktops. Comparisons are made between AppArmor and SELinux.









![© Novell Inc. All rights reserved37
GAIM Profile
Console Tools
• Create the profile template
– cd /opt/gnome/bin
– genprof gaim
• Exercise GAIM
– start, chat, stop
• Create profile entries
– [S]can log for profile entries
– [F]inish (GAIM profile is loaded)
• View profile
– vim opt.gnome.bin.gaim
– syntax on
– set syntax=subdomain
Makes it safe to
talk to strangers](https://image.slidesharecdn.com/apparmorstructure-200321001900/75/App-armor-structure-37-2048.jpg)