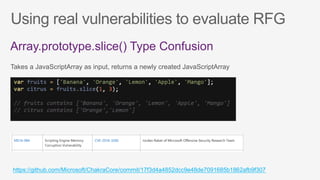
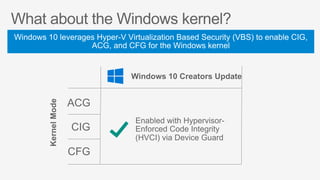
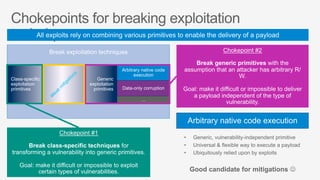
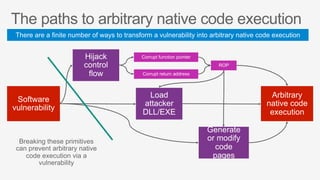
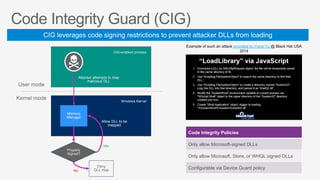
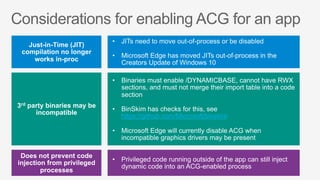
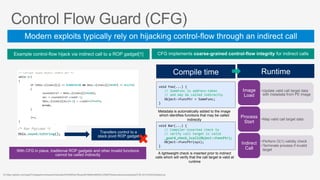
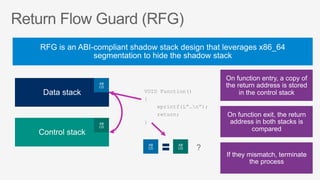
This document summarizes security features in Microsoft Azure to prevent control-flow hijacking and arbitrary code generation. It describes Control Flow Guard, Arbitrary Code Guard, and Code Integrity Guard which enforce control flow integrity, prevent dynamic code generation and modification, and only allow signed code pages. It also discusses some known limitations and bypasses that Microsoft is working to address through additional security features like Control-flow Enforcement Technology (CET).












![644c8b1c24 mov r11,qword ptr fs:[rsp]
4c3b1c24 cmp r11,qword ptr [rsp]
0f8518a00300 jne DLL!__guard_ss_verify_failure
488b0424 mov rax,qword ptr [rsp]
6448890424 mov qword ptr fs:[rsp],rax](https://image.slidesharecdn.com/westonmillercsw17mitigatingnativeremotecodeexecution-170317032849/85/CSW2017-Weston-miller-csw17_mitigating_native_remote_code_execution-21-320.jpg)