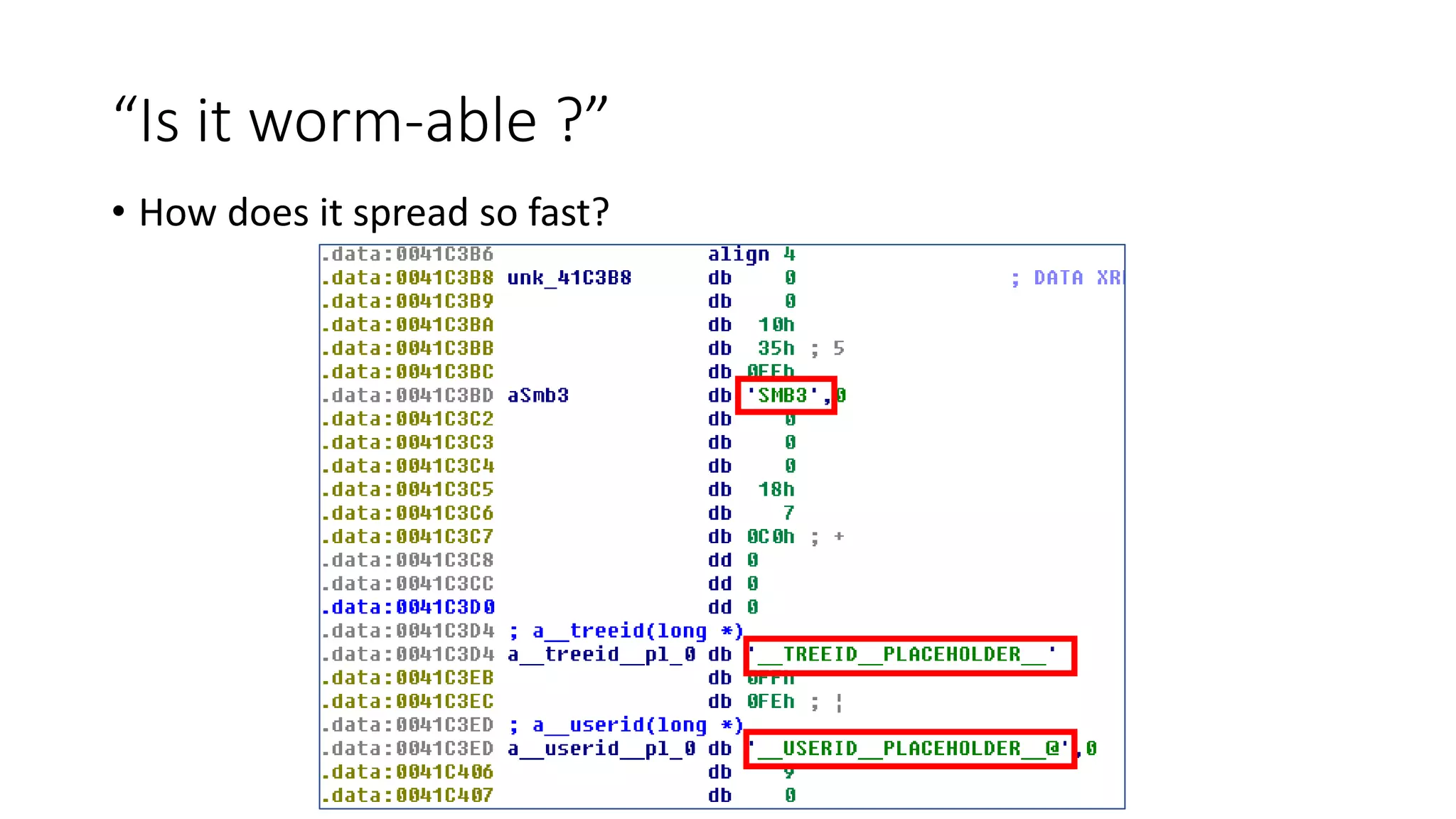
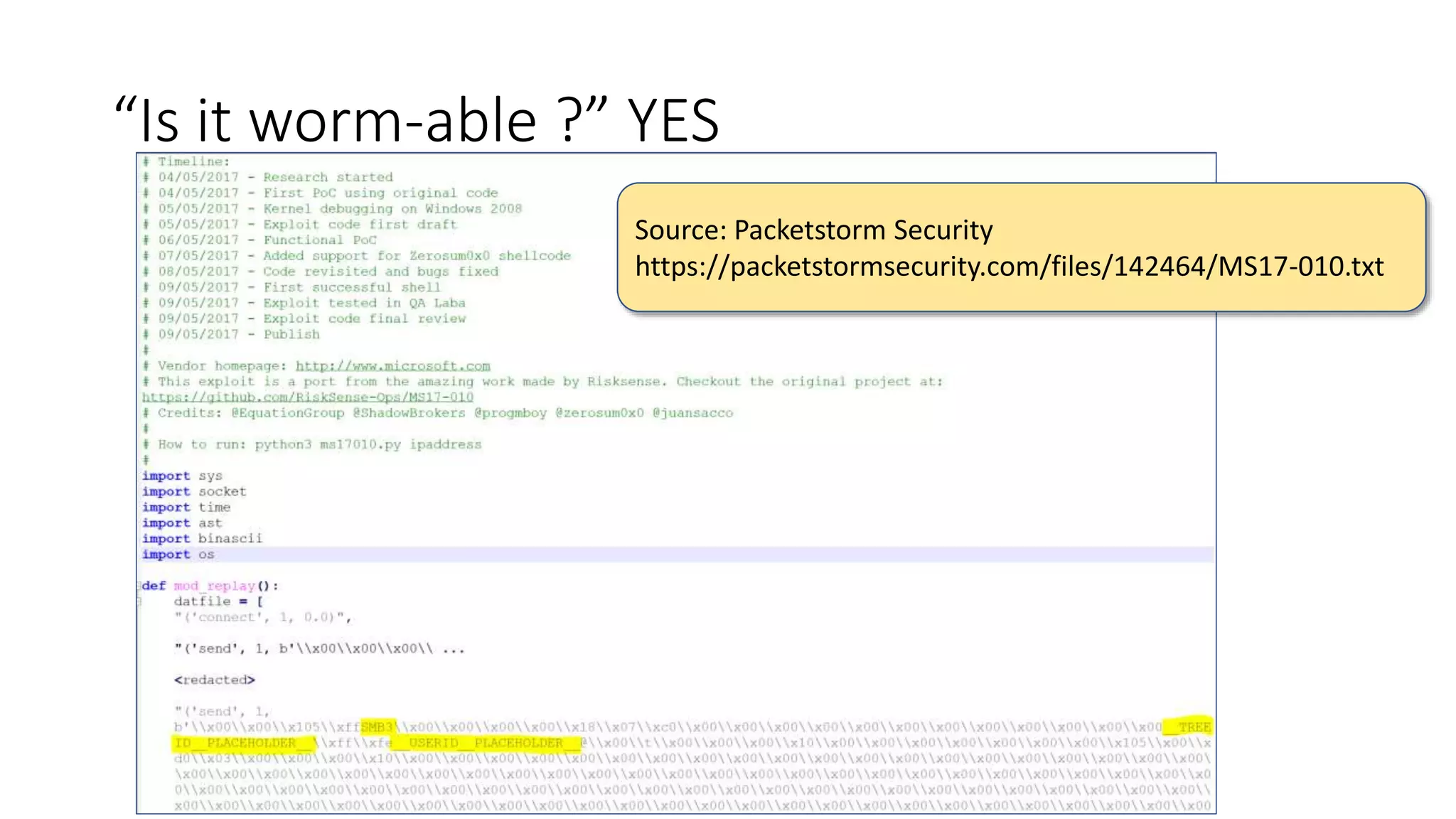
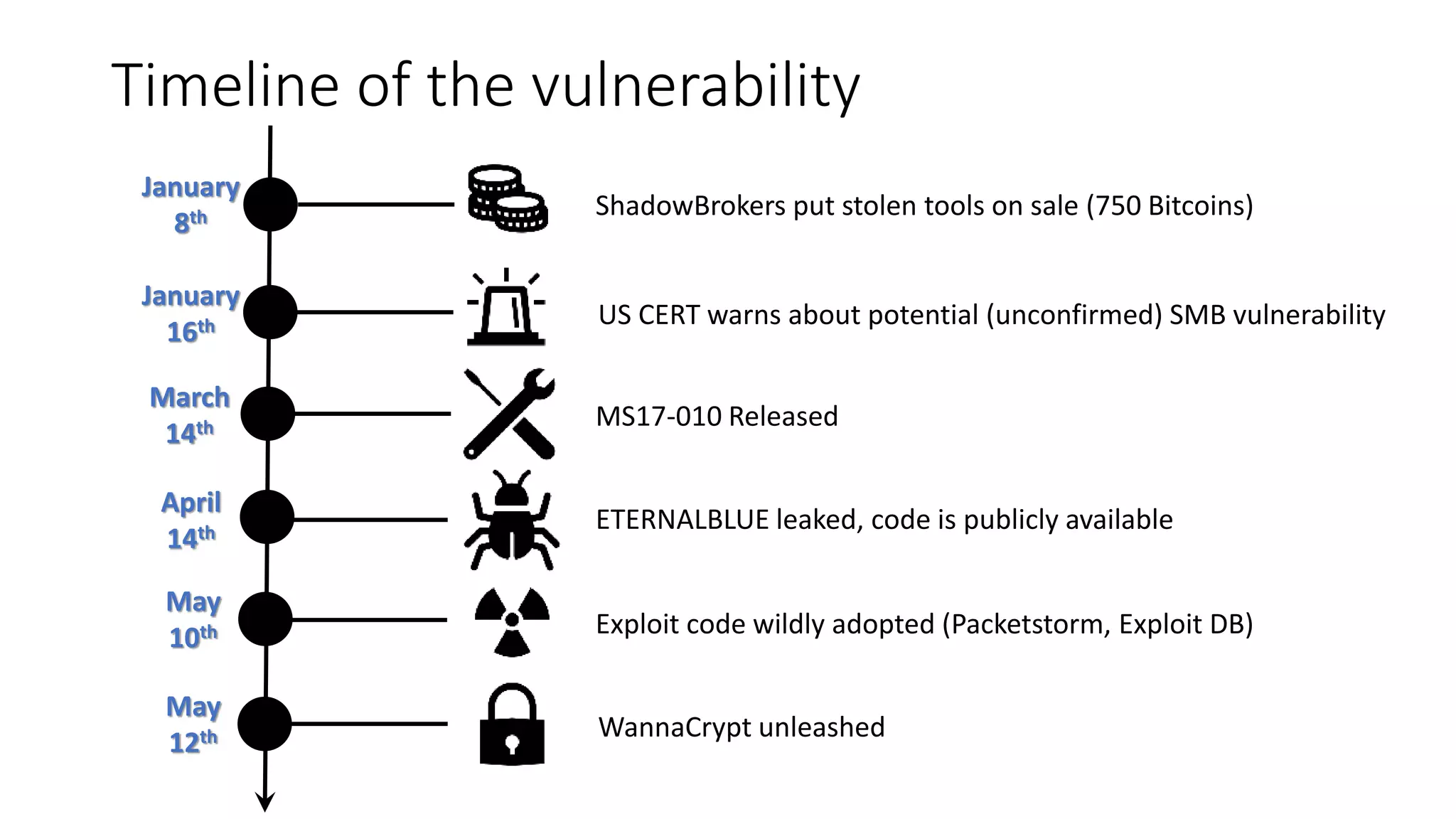
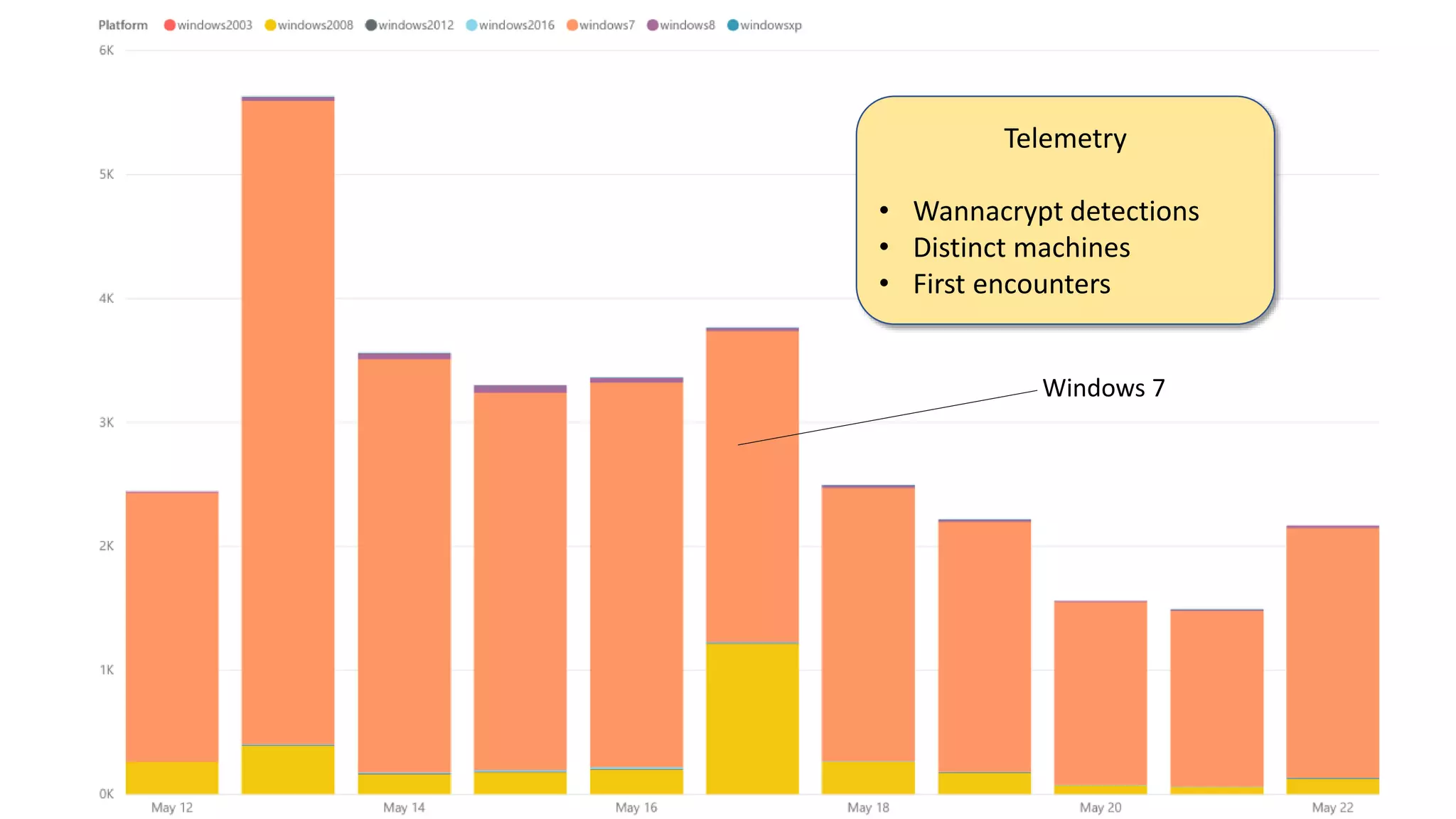
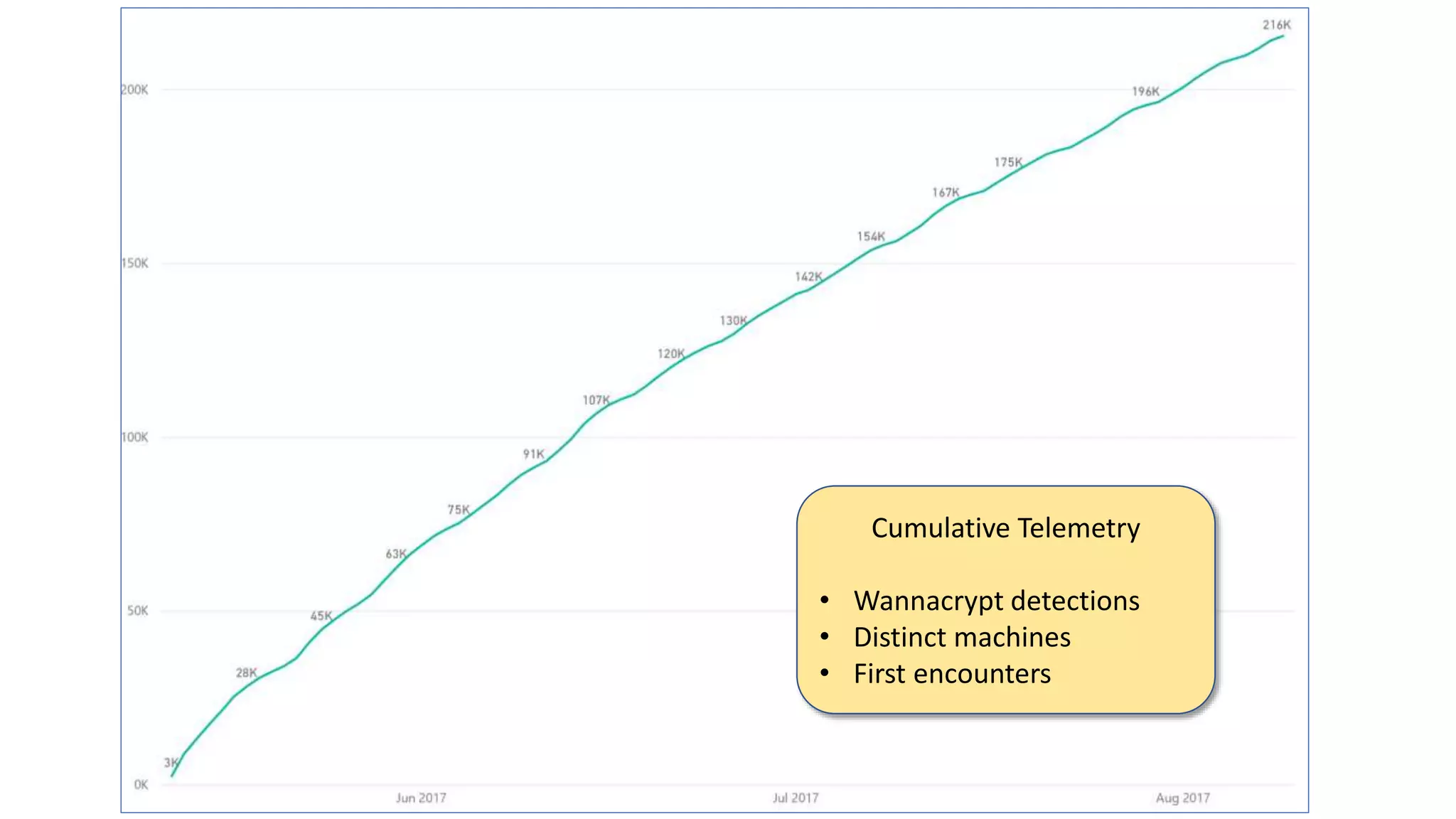
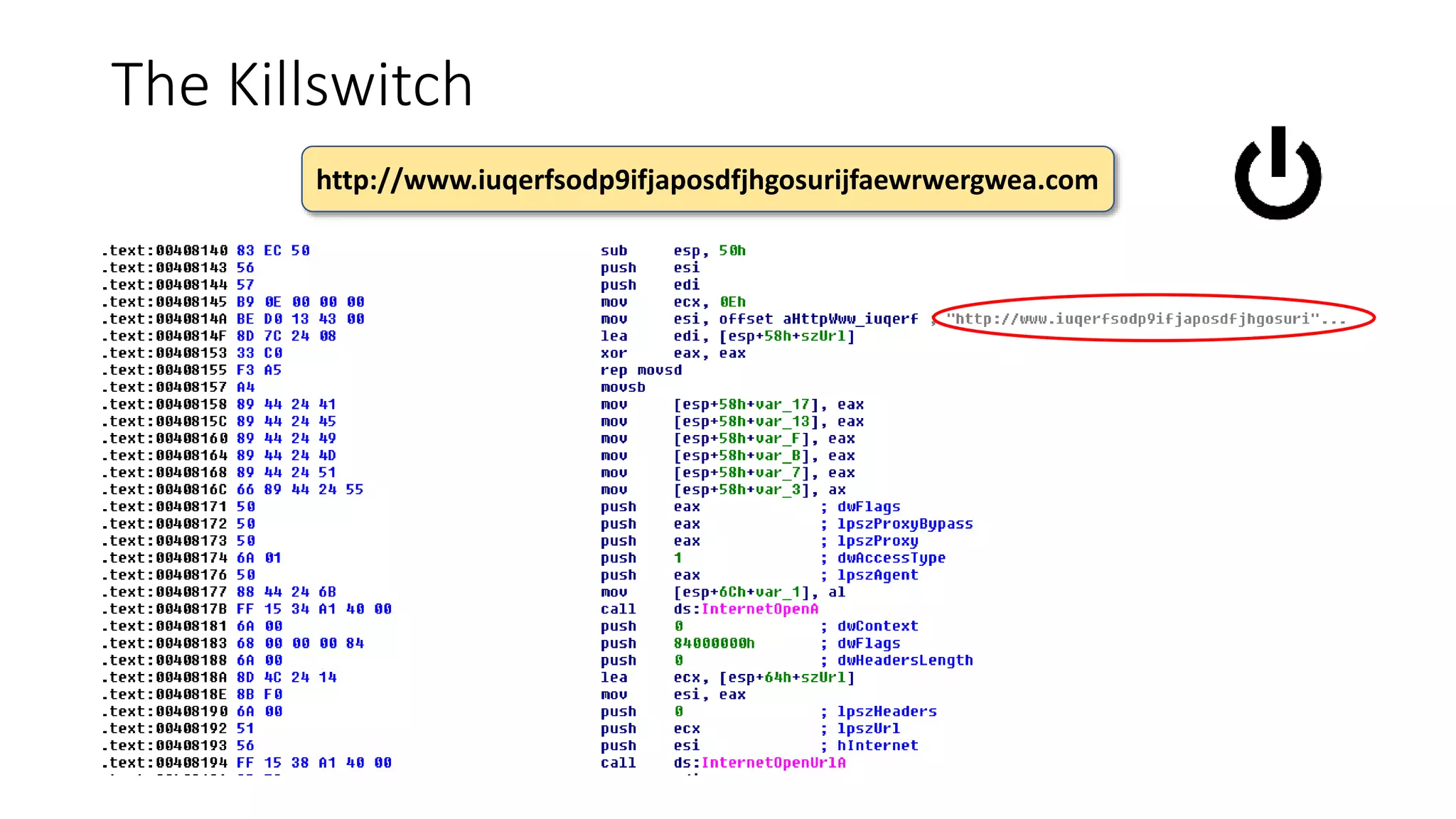
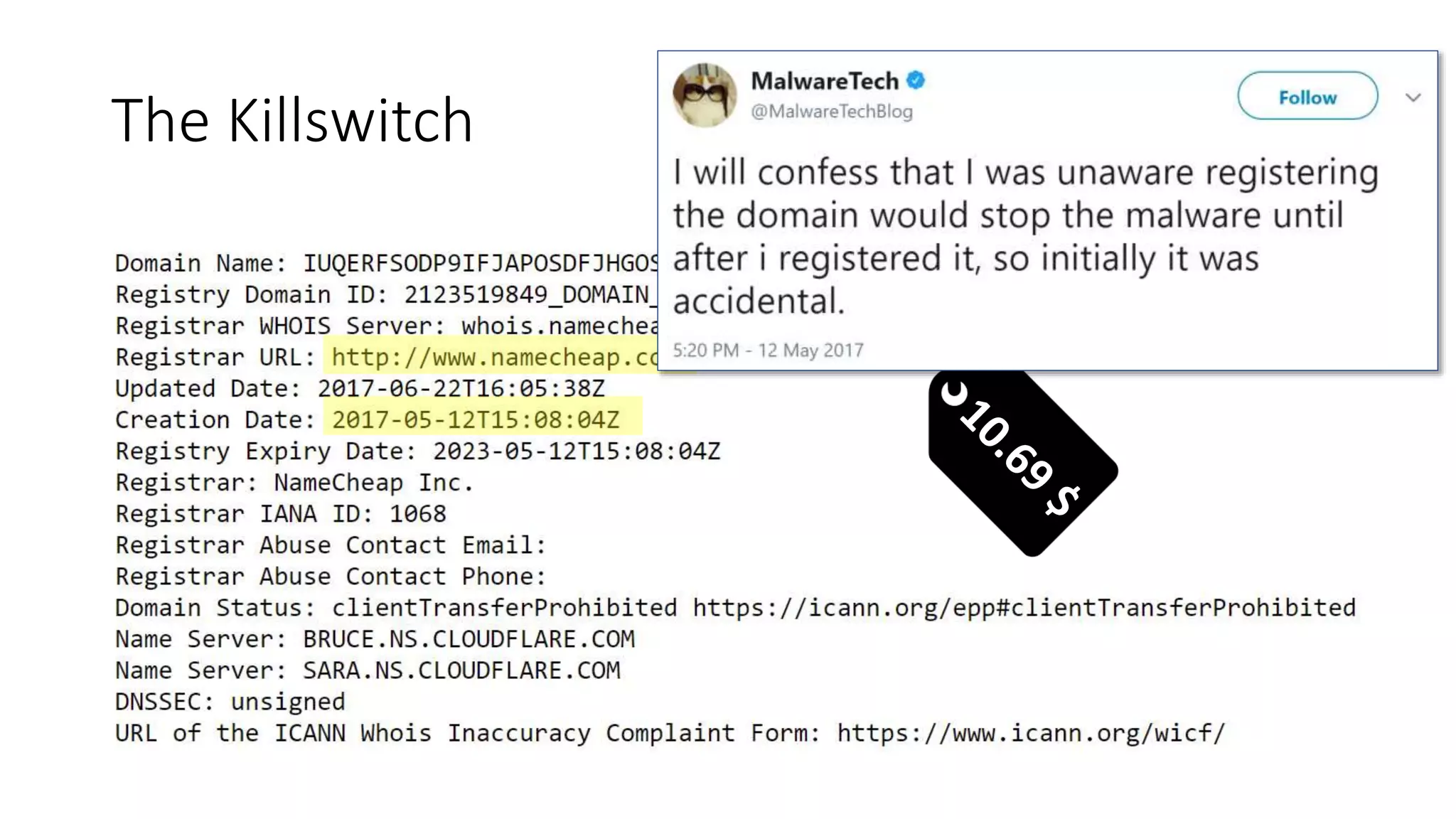
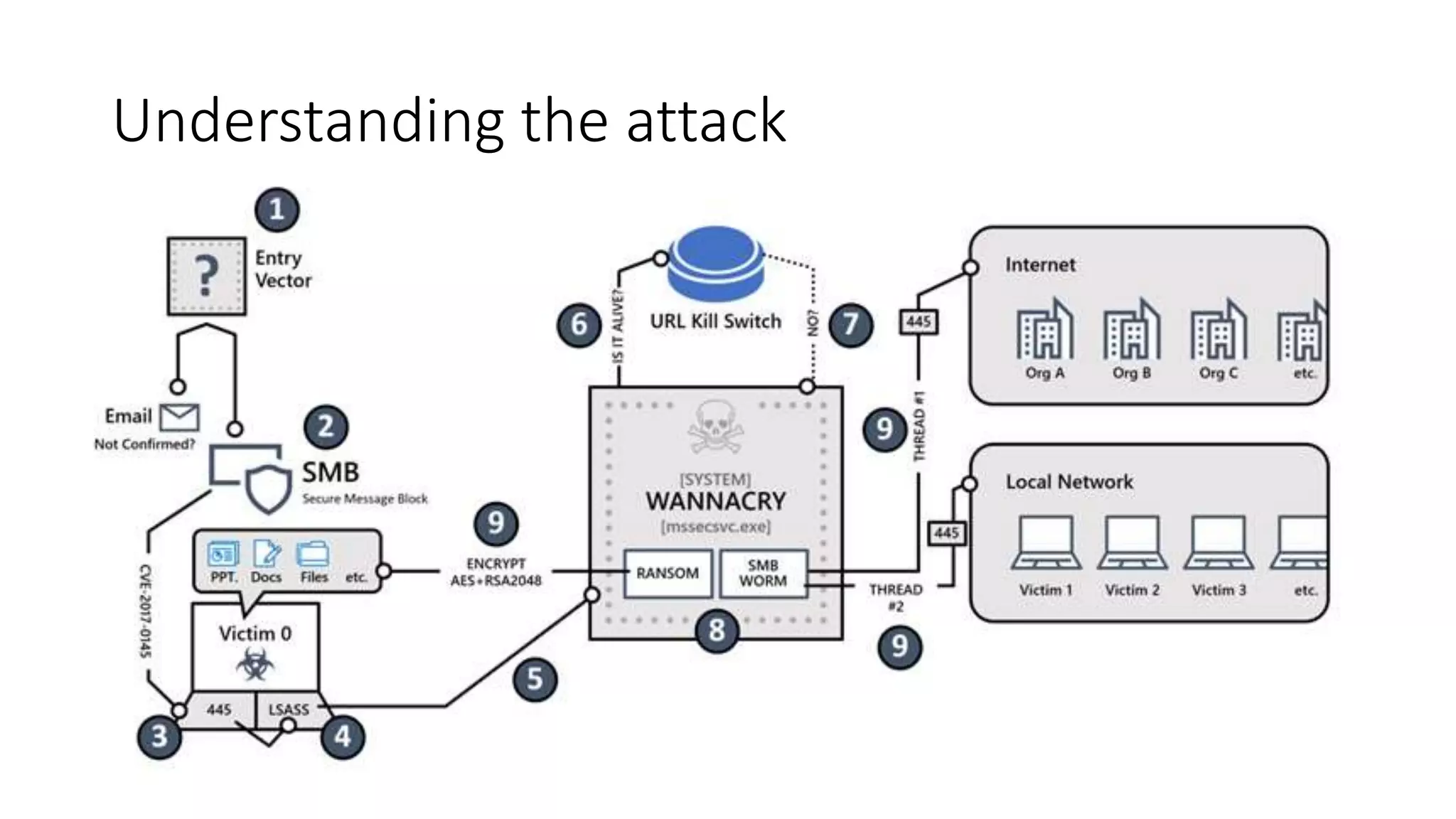
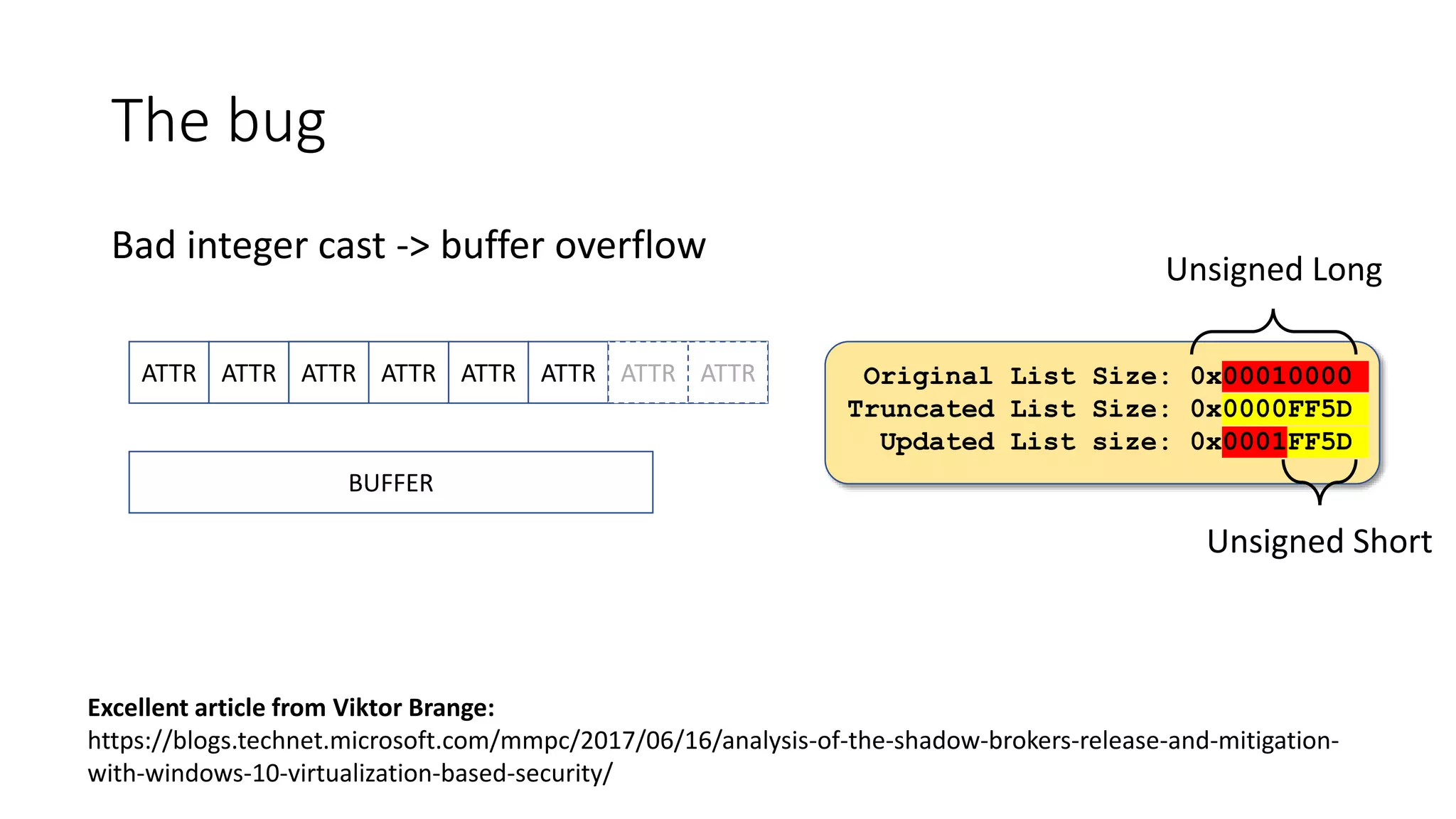
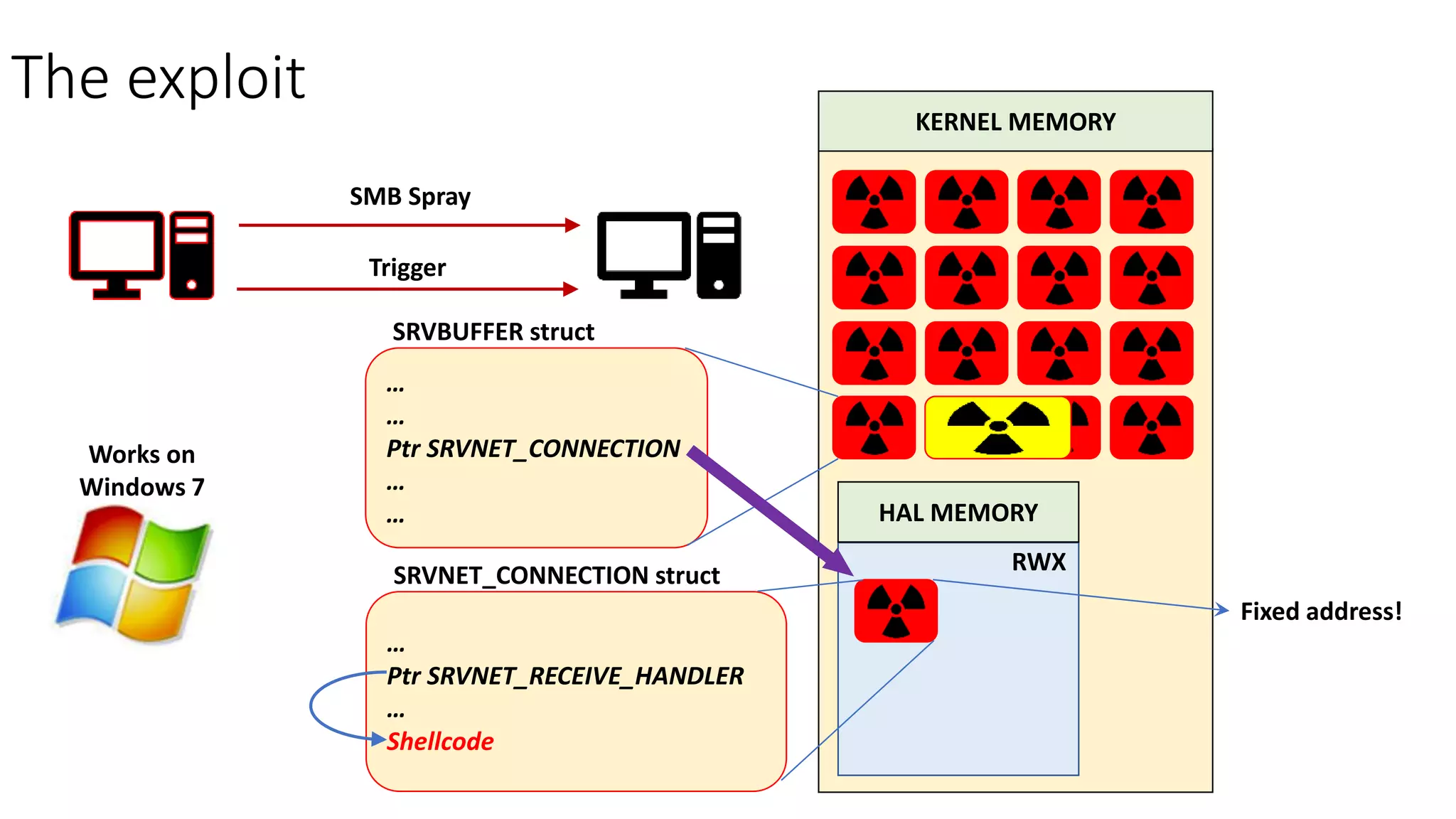
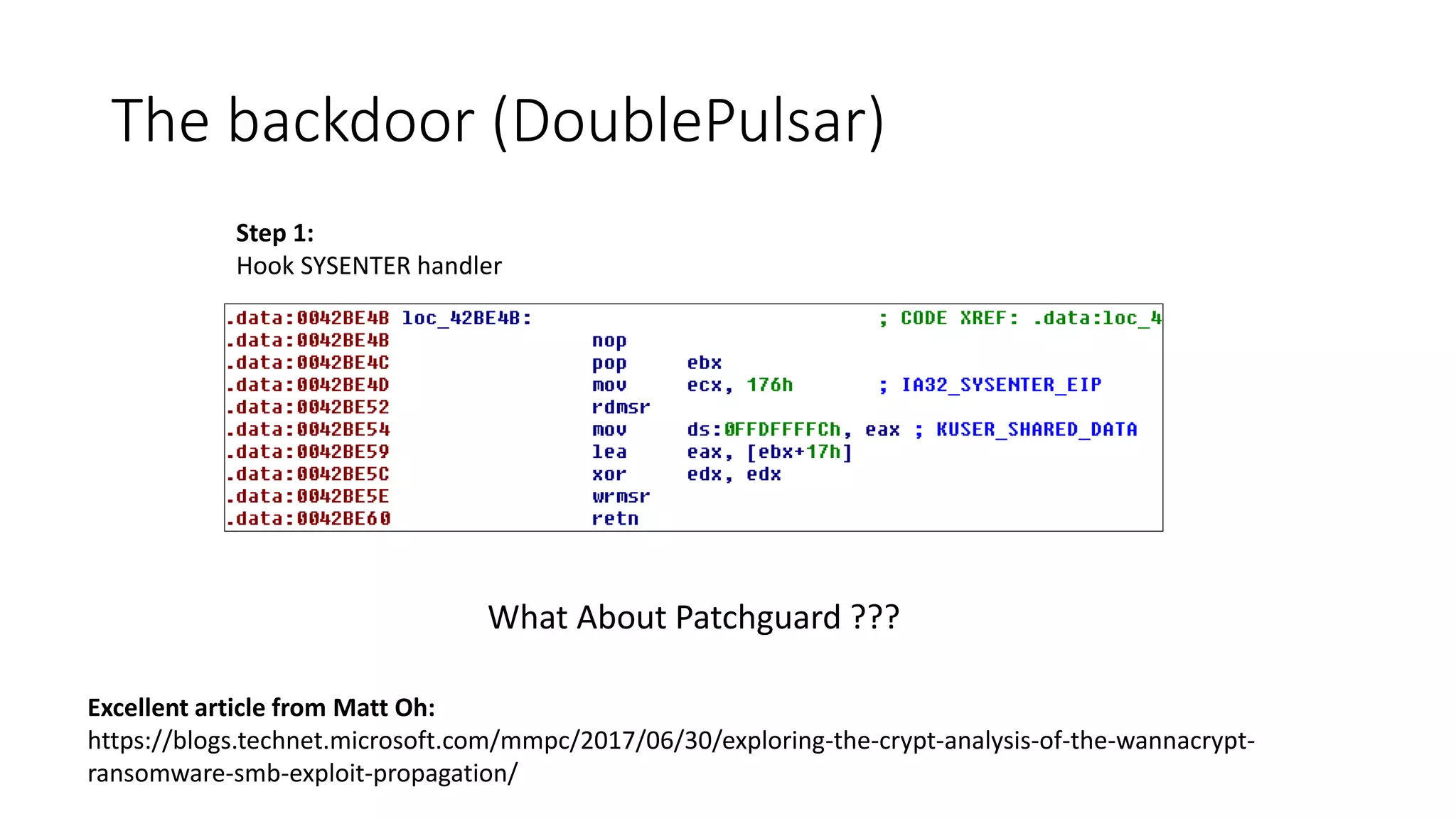
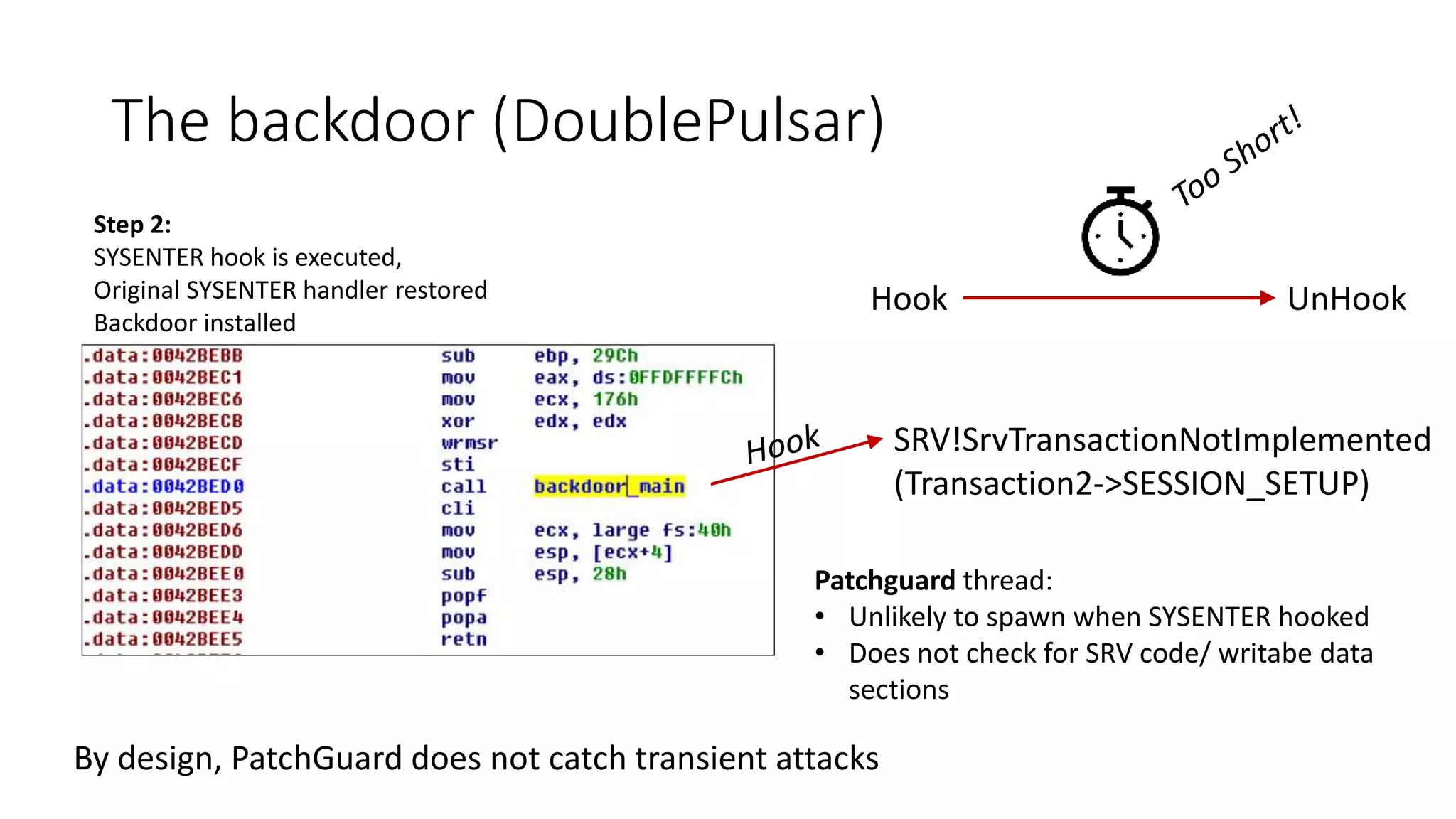
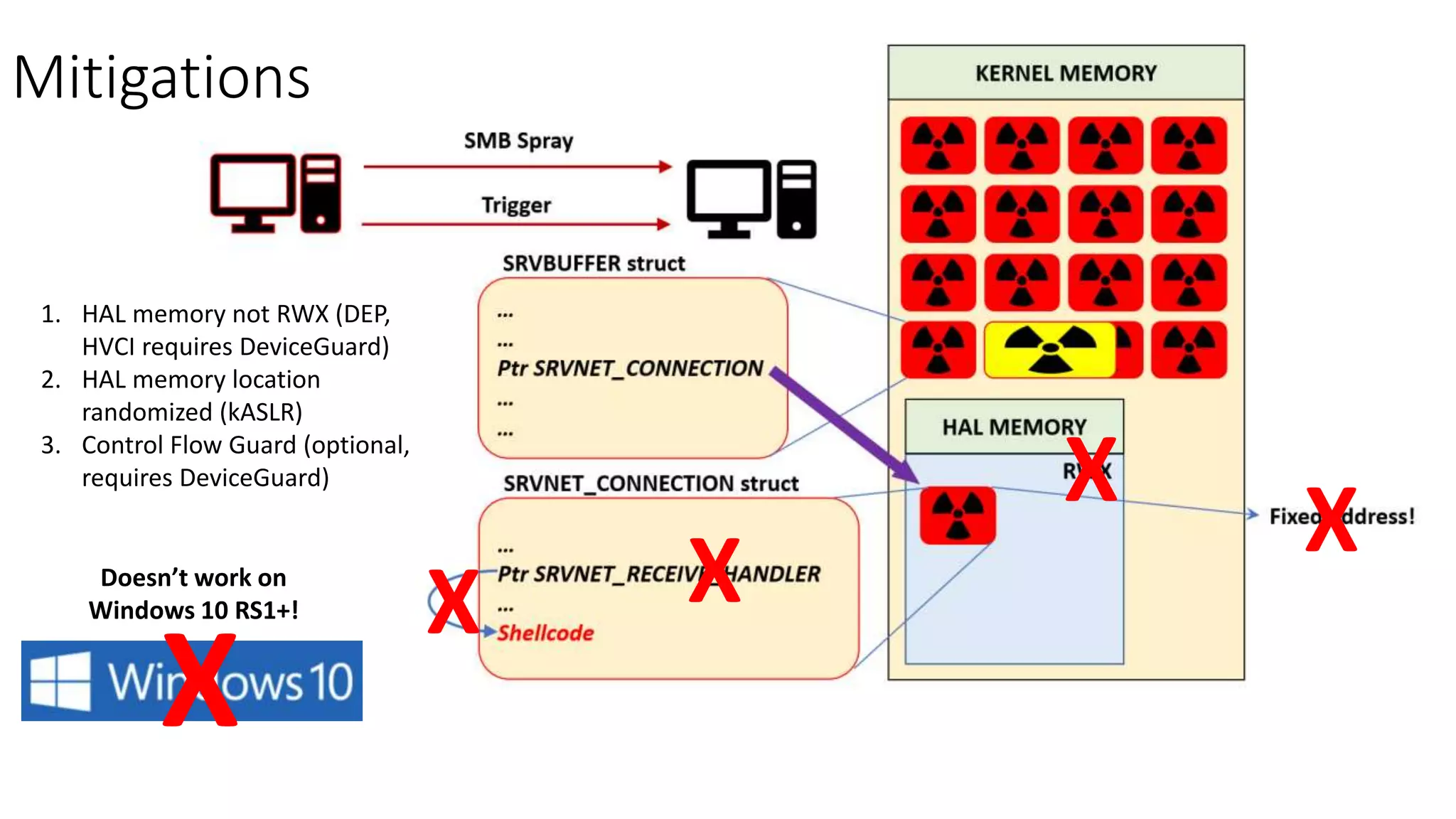
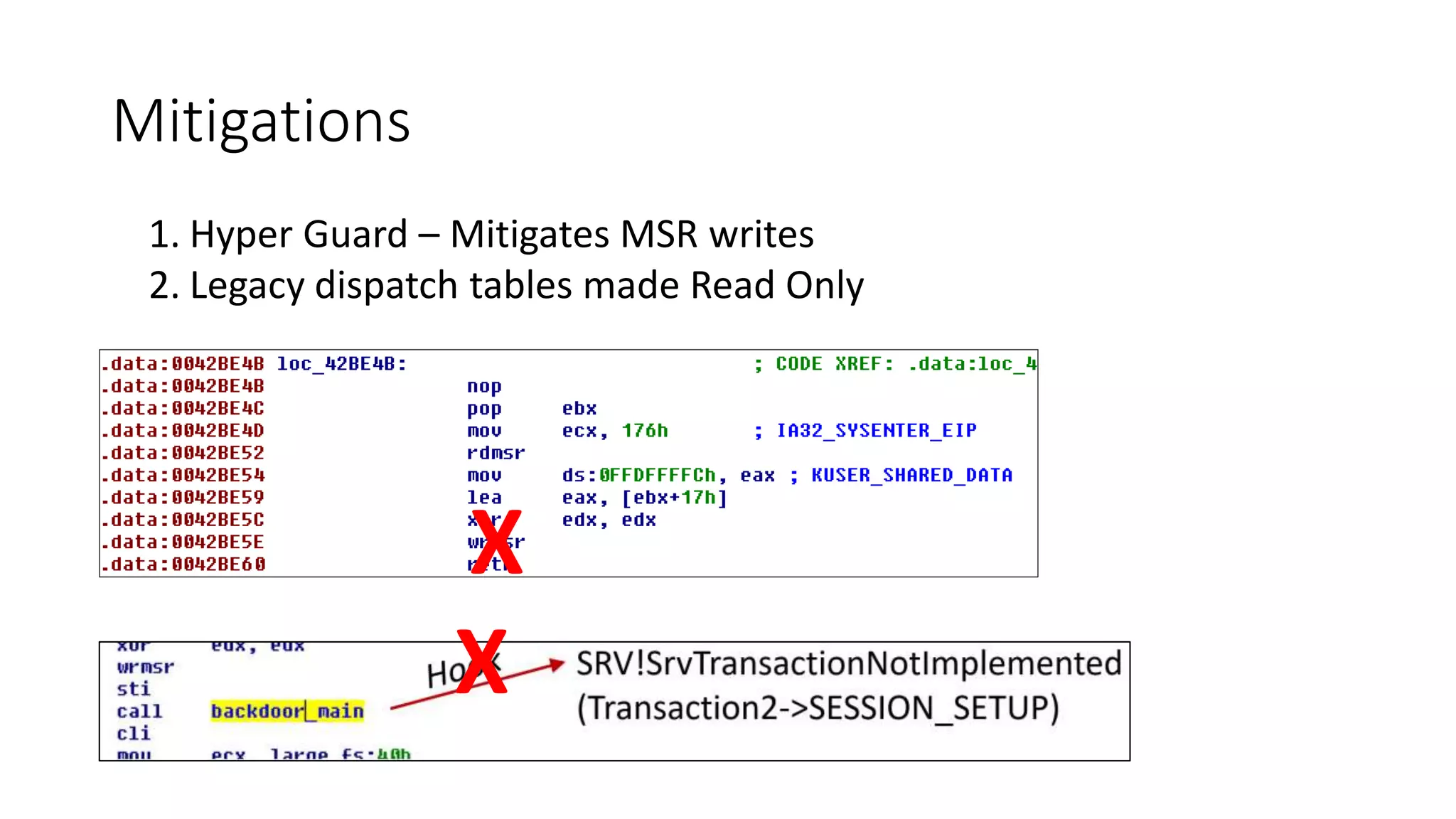
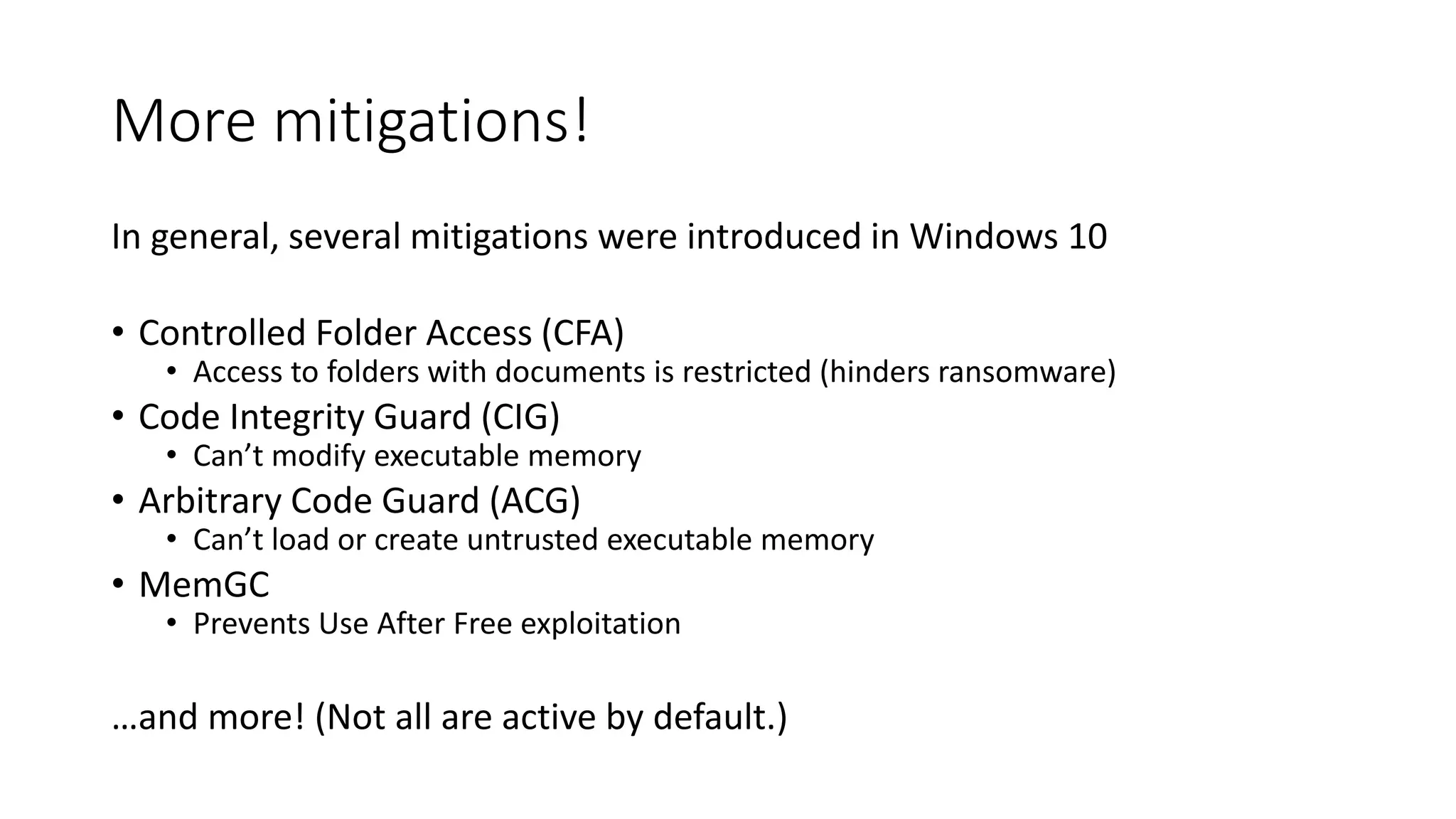
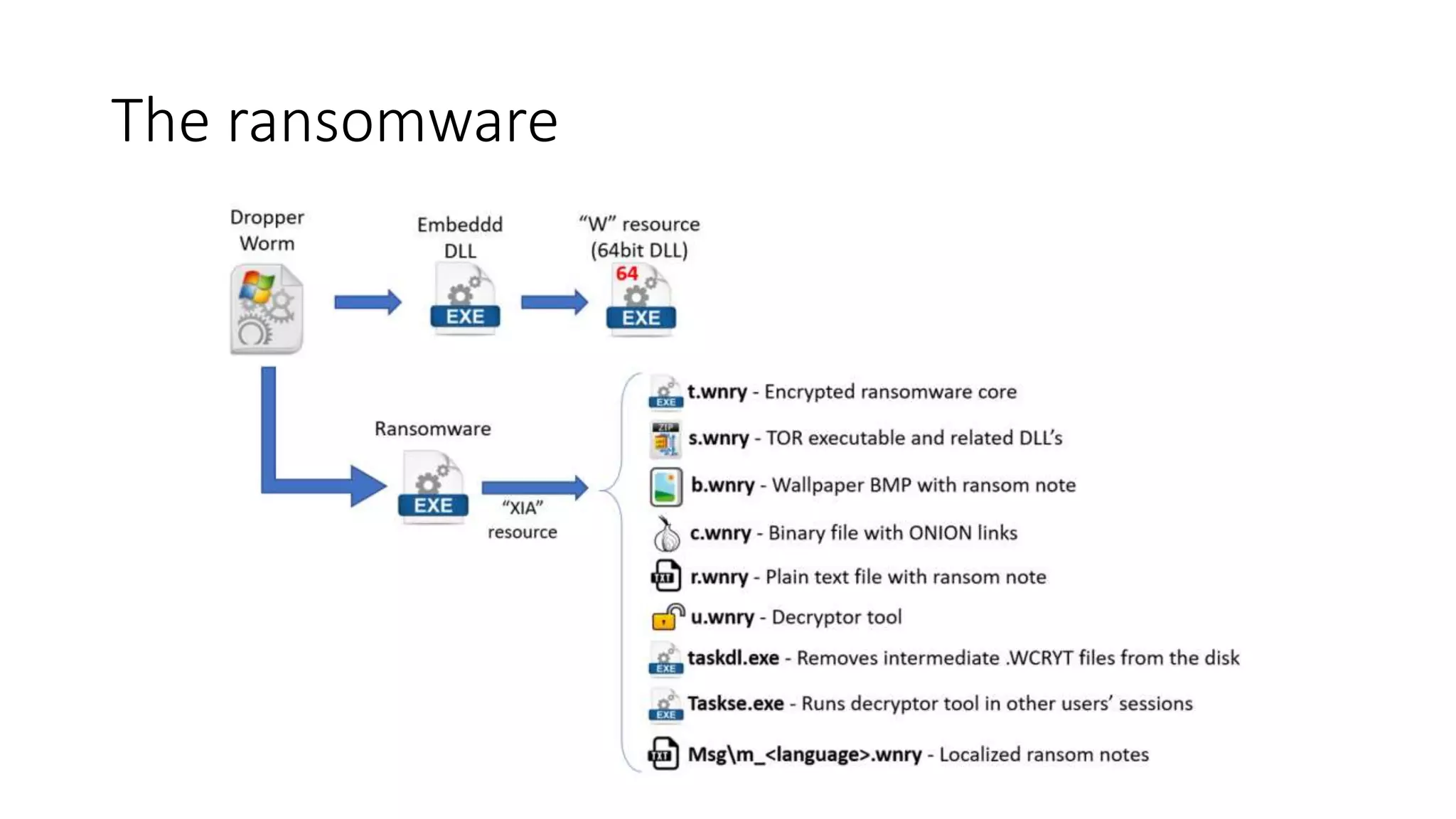
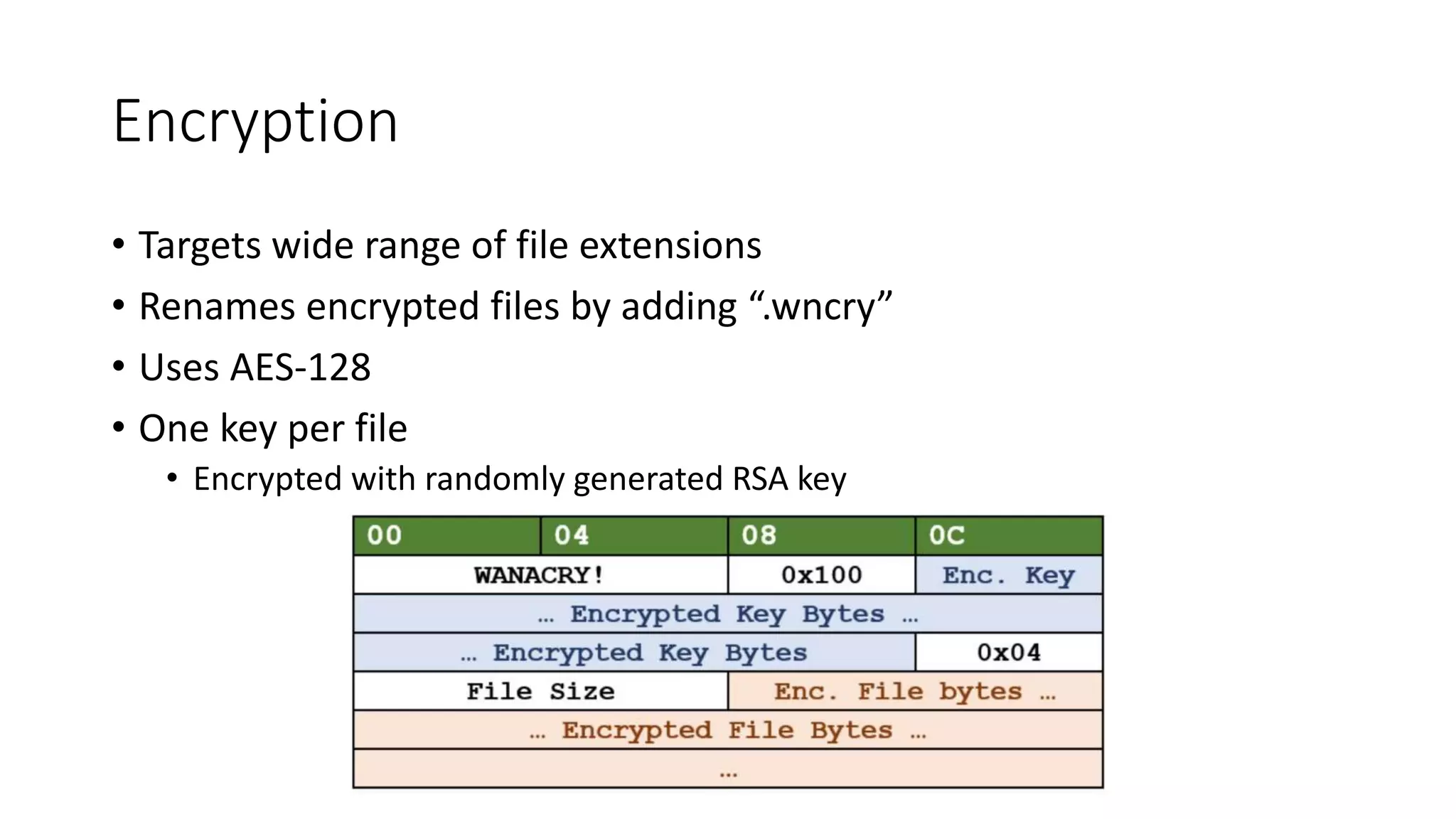
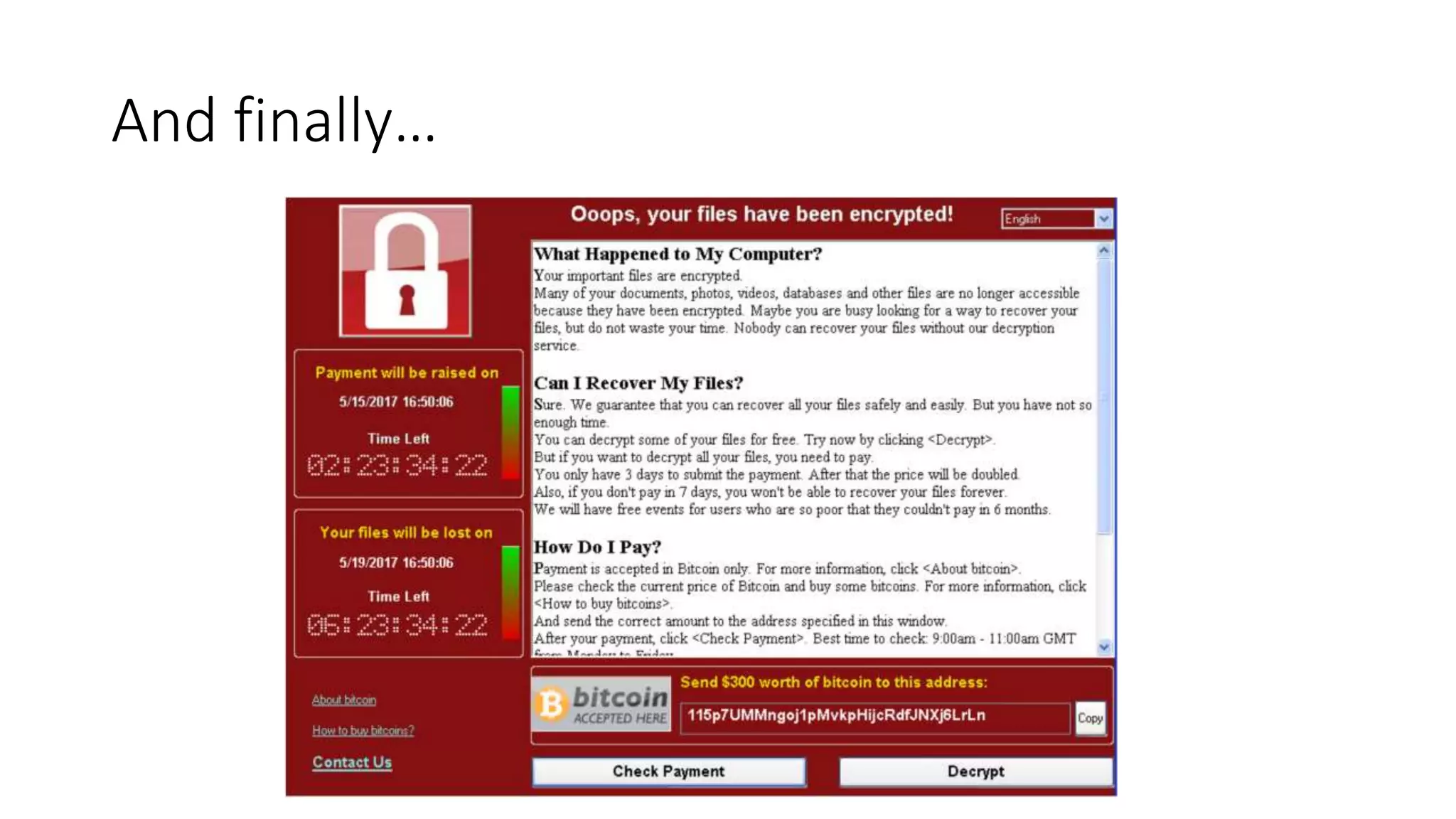
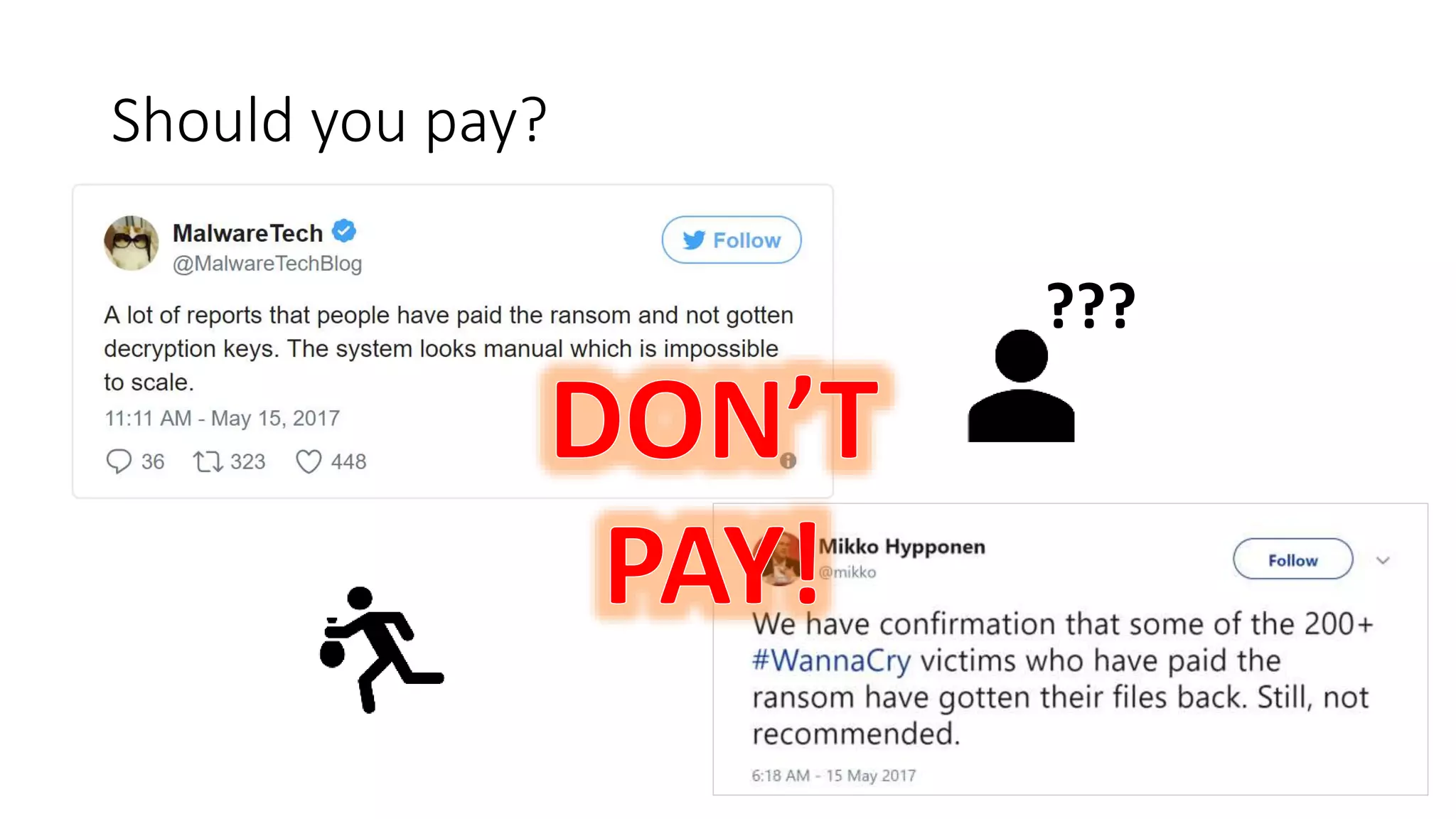
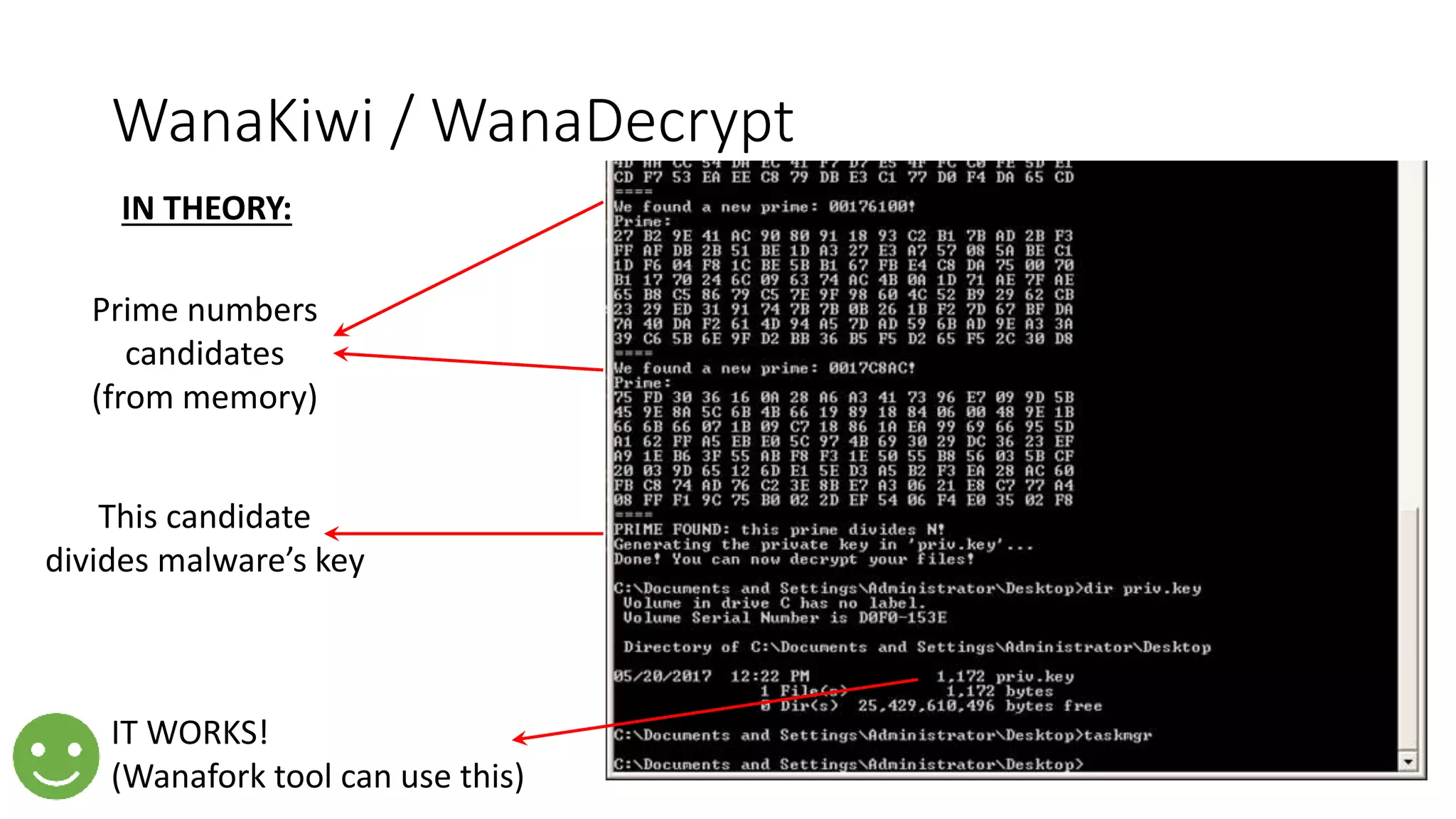
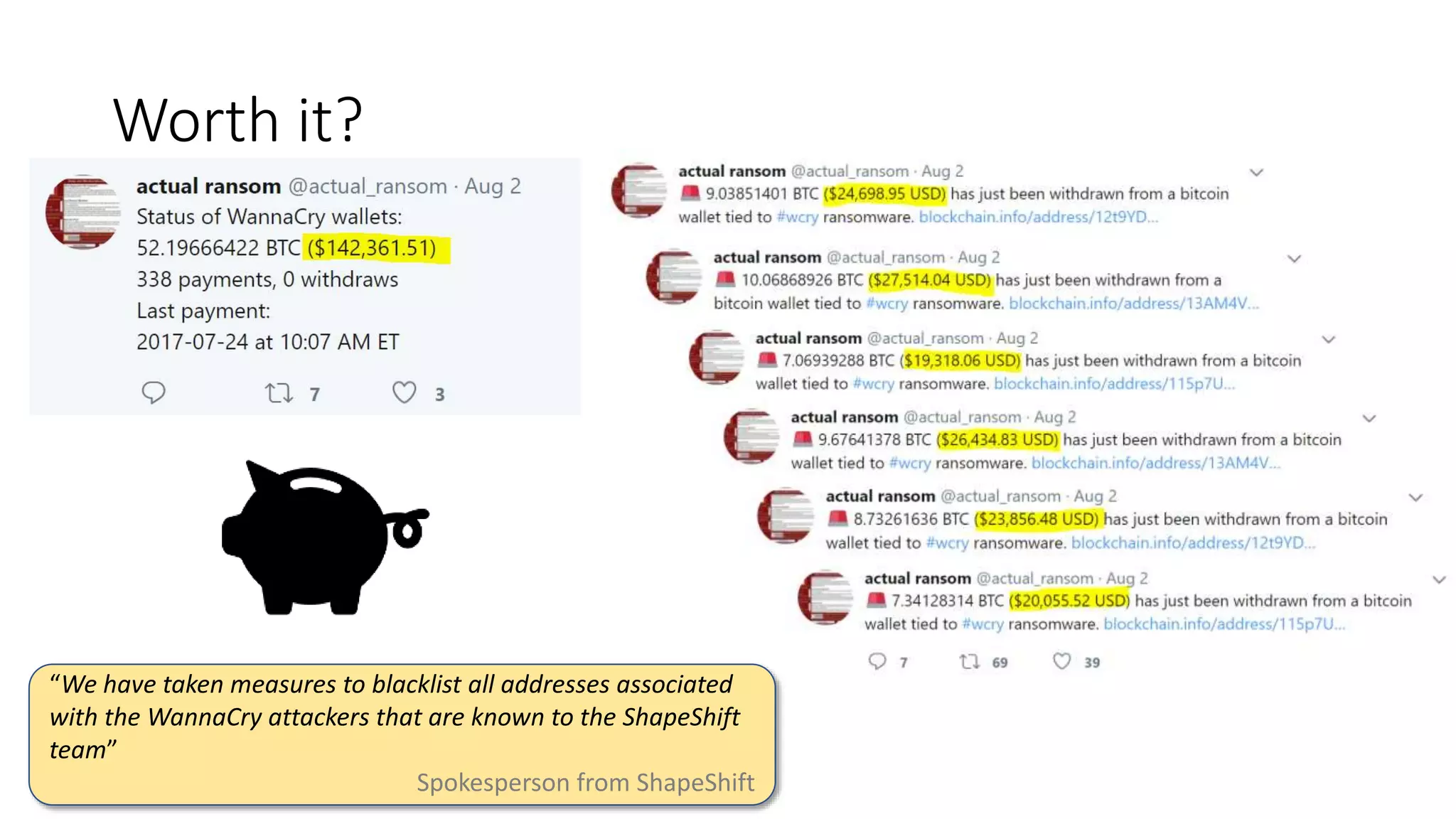
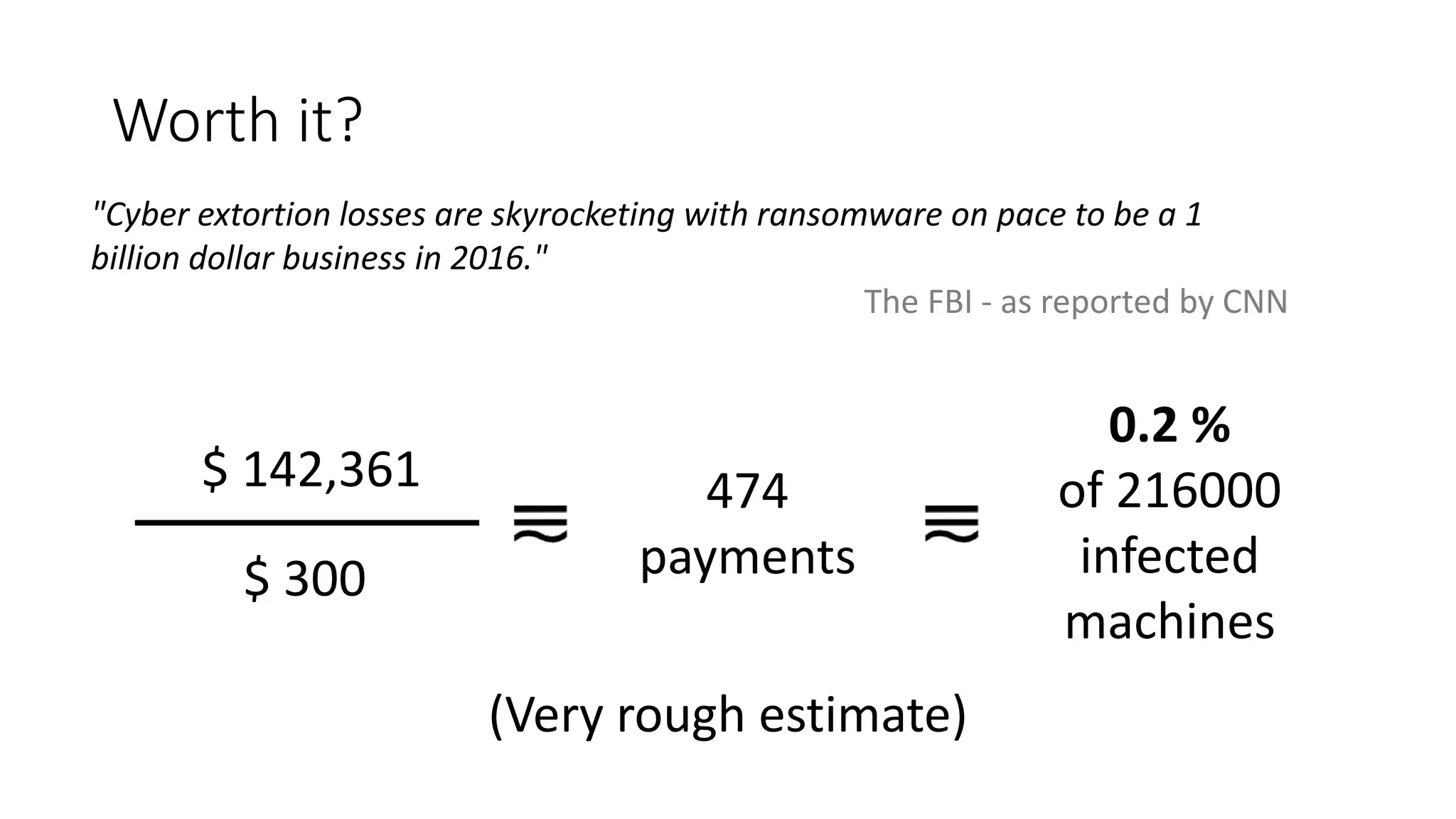
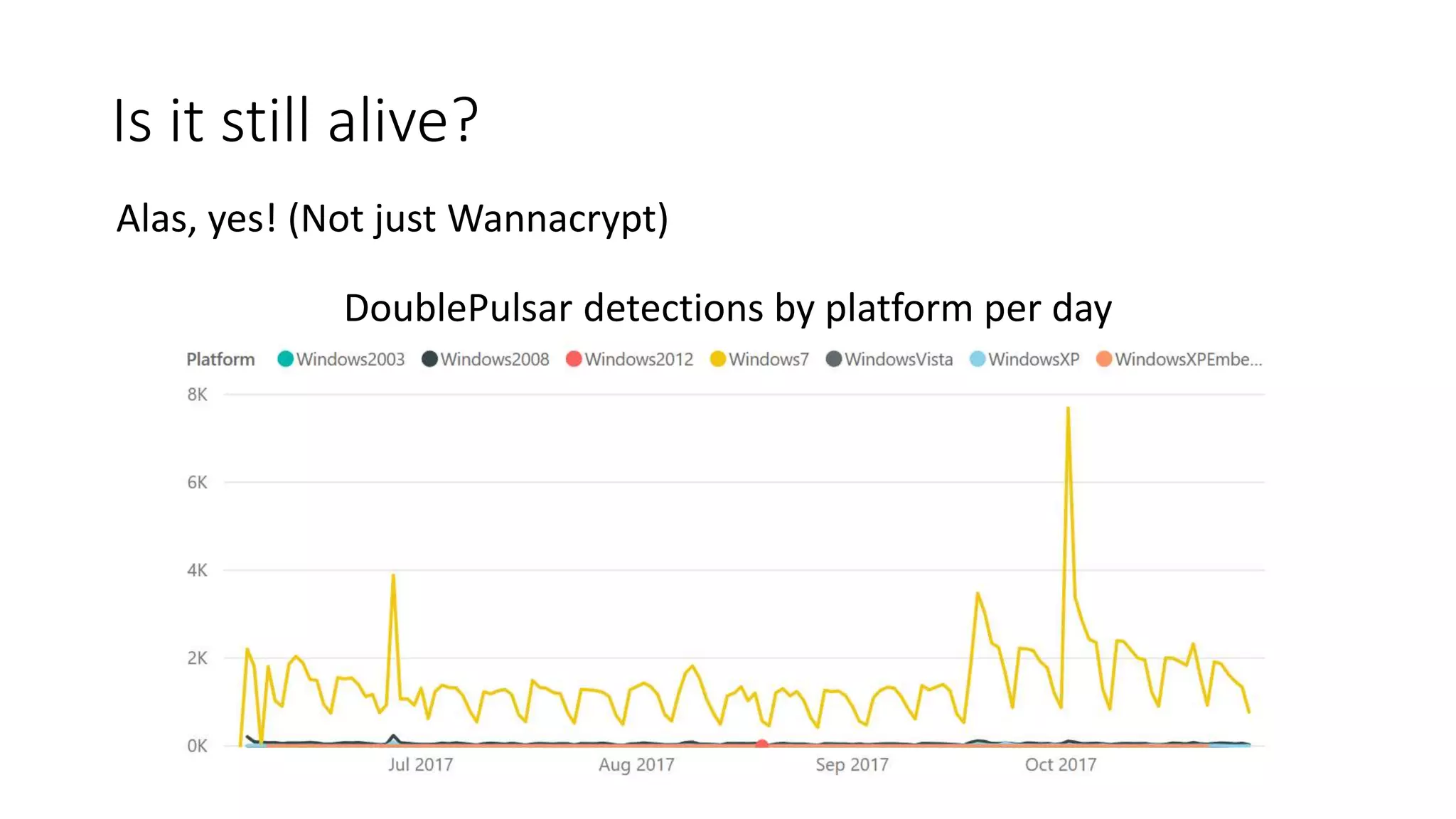
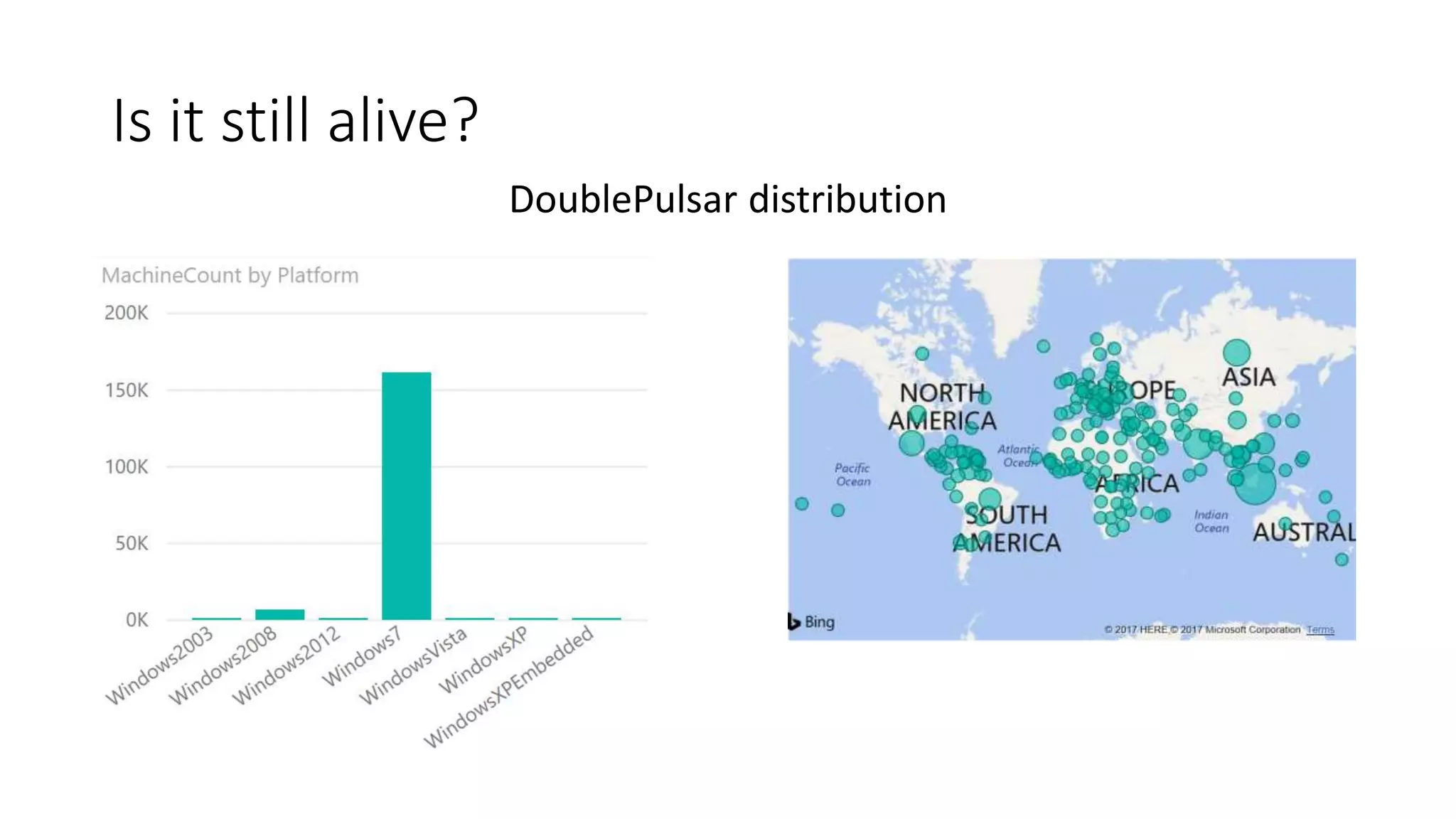
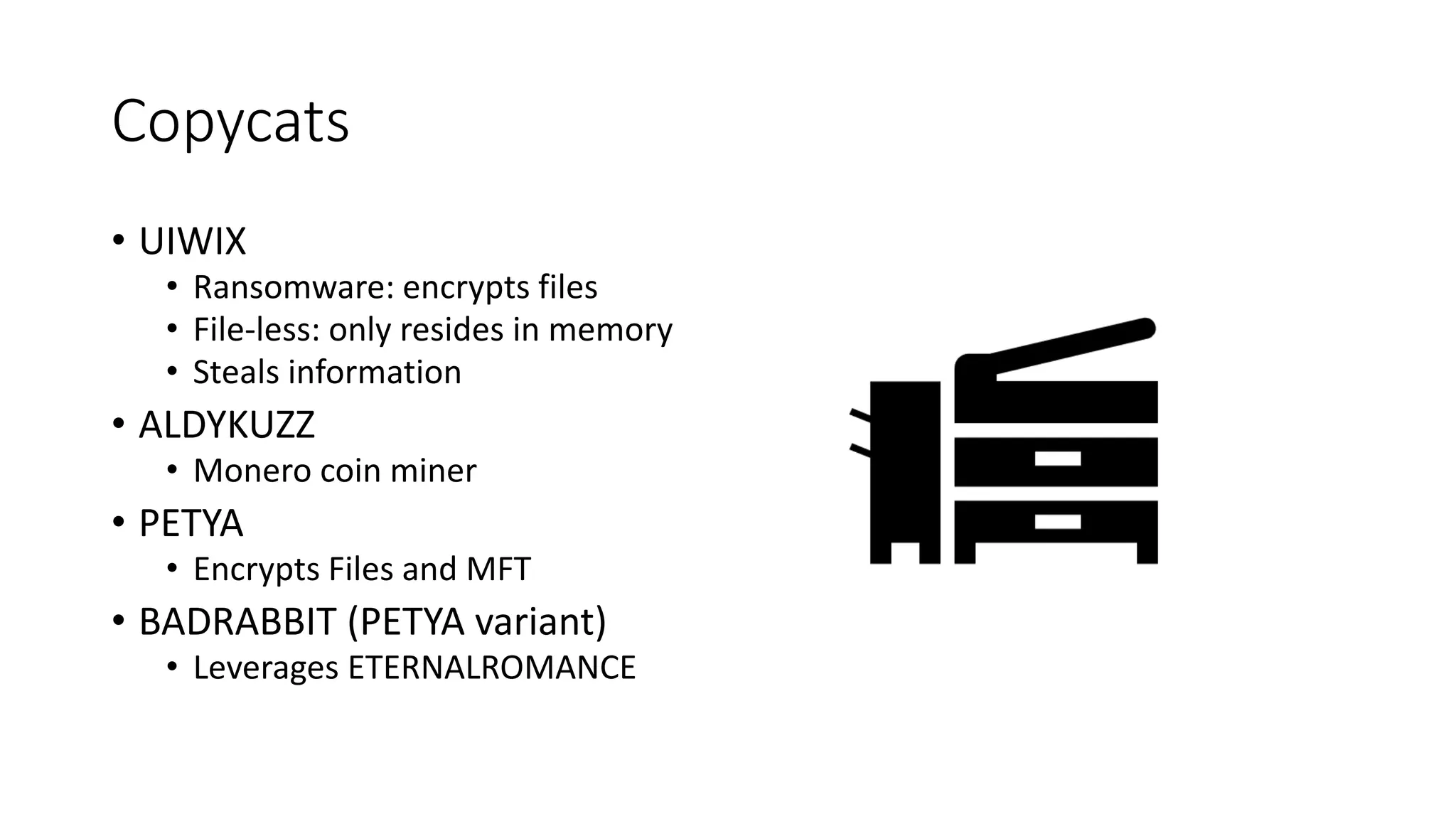
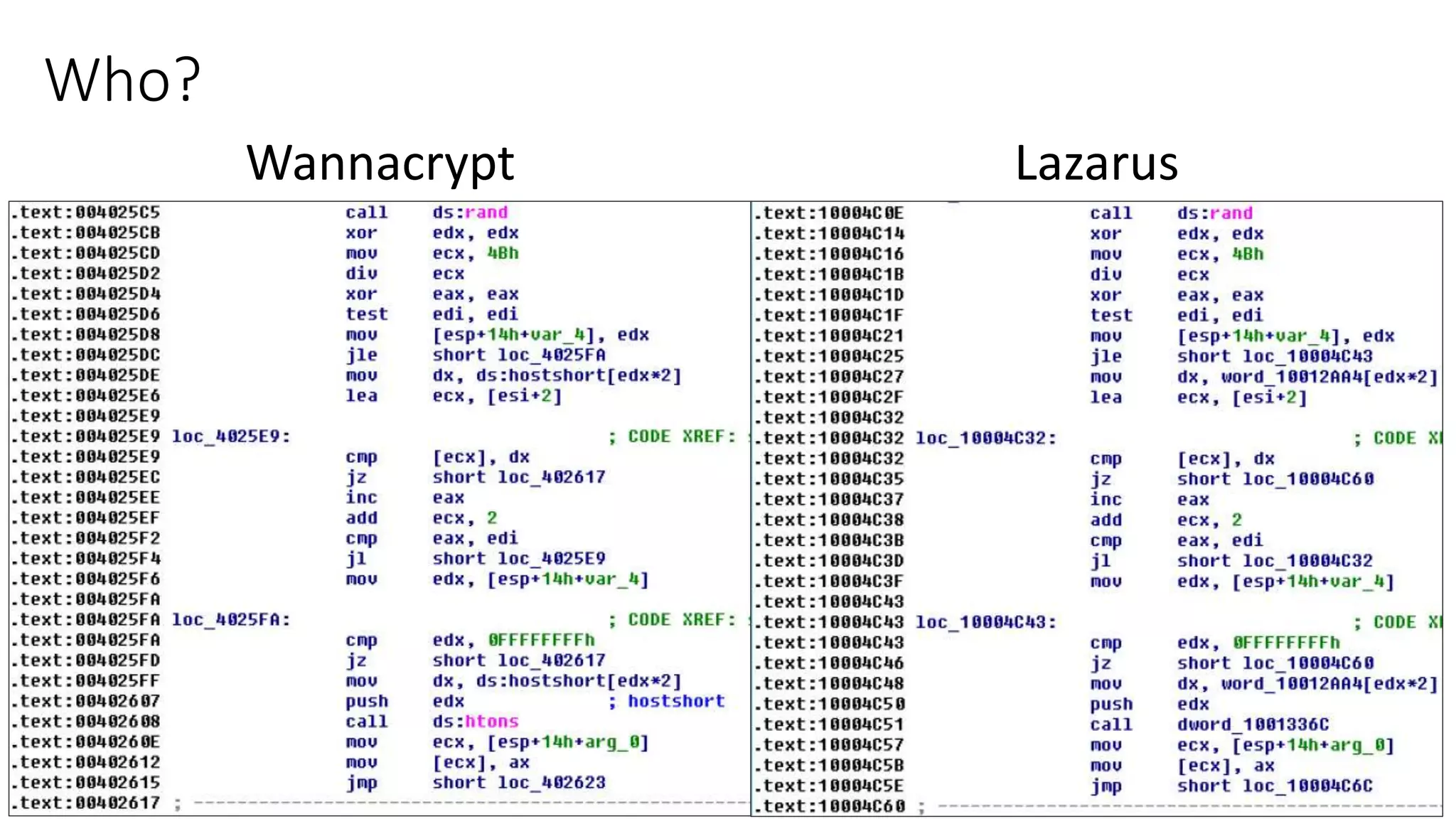
The document summarizes the Wannacrypt + Smbv1.0 ransomware attack, one of the most damaging in history. It began on a Friday in May 2017, infecting over 216,000 machines worldwide in just one day by exploiting an SMB vulnerability. The ransomware used the EternalBlue exploit leaked from the ShadowBrokers to spread rapidly through networks. Microsoft had released a patch for the vulnerability in March 2017 but many systems remained unpatched. The attack was stopped when a researcher registered a domain name hard-coded in the ransomware. The document examines the technical details and impact of the attack, and recommends steps to prevent future ransomware infections like keeping systems updated with the latest security patches.