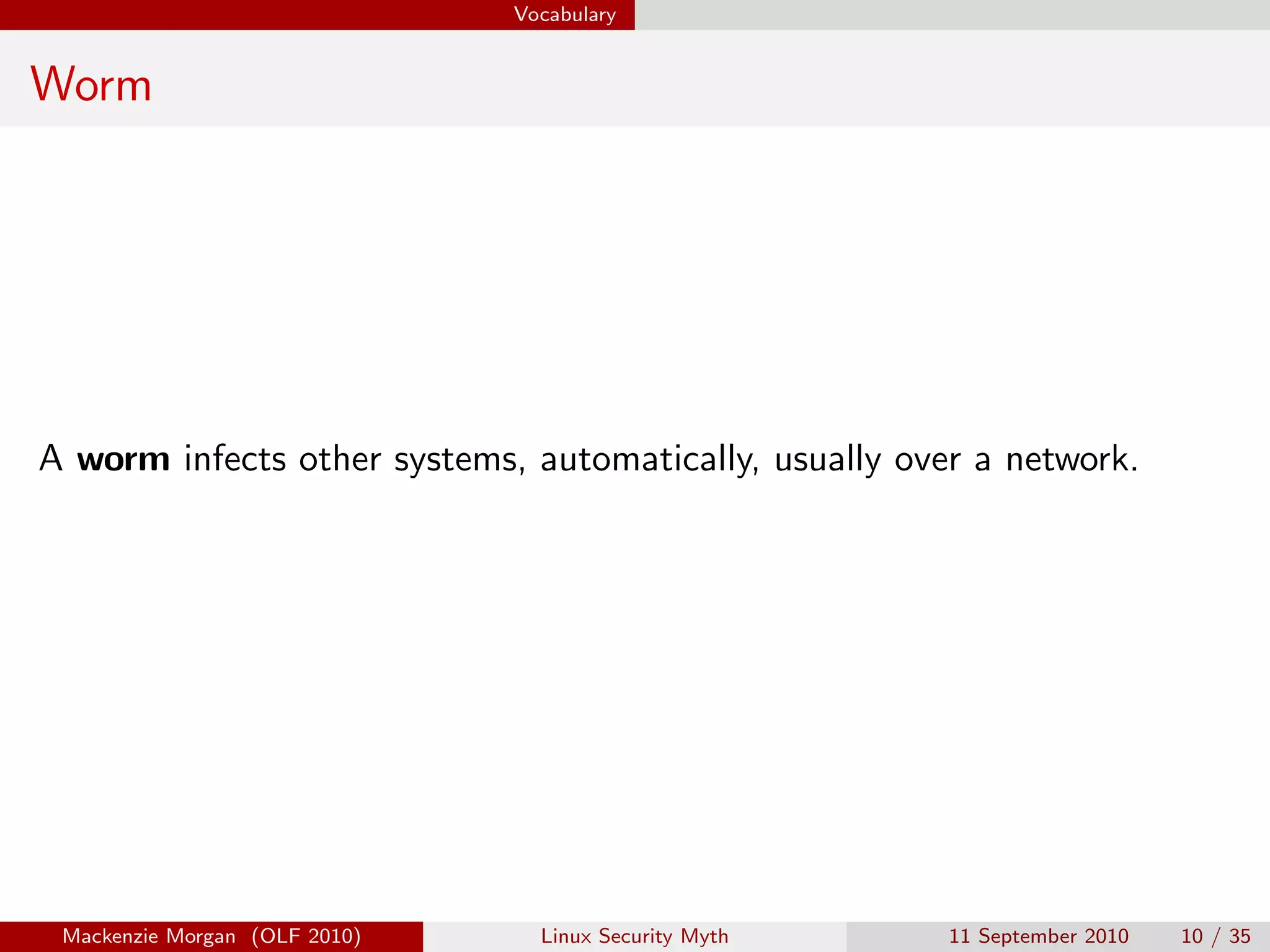
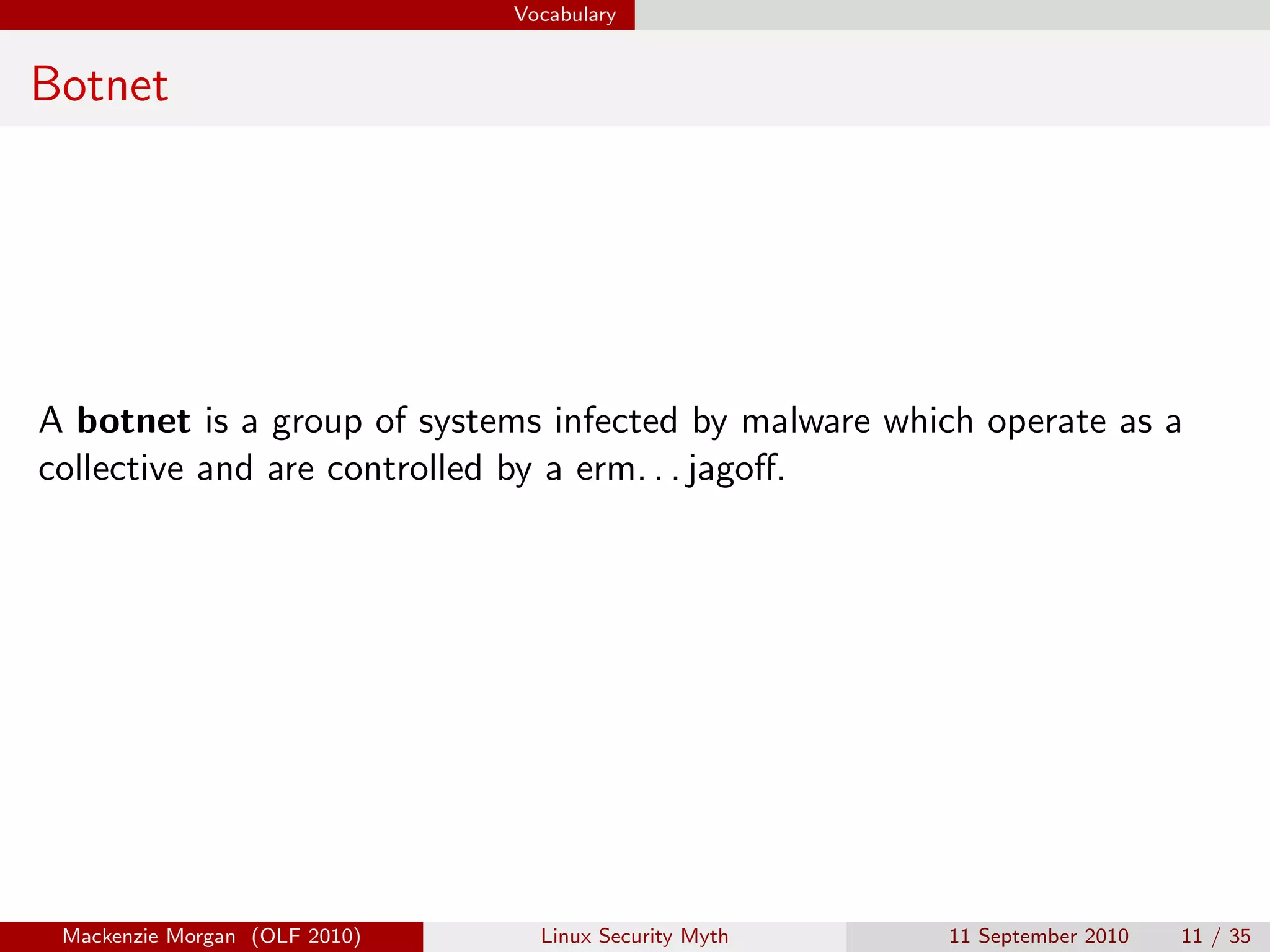
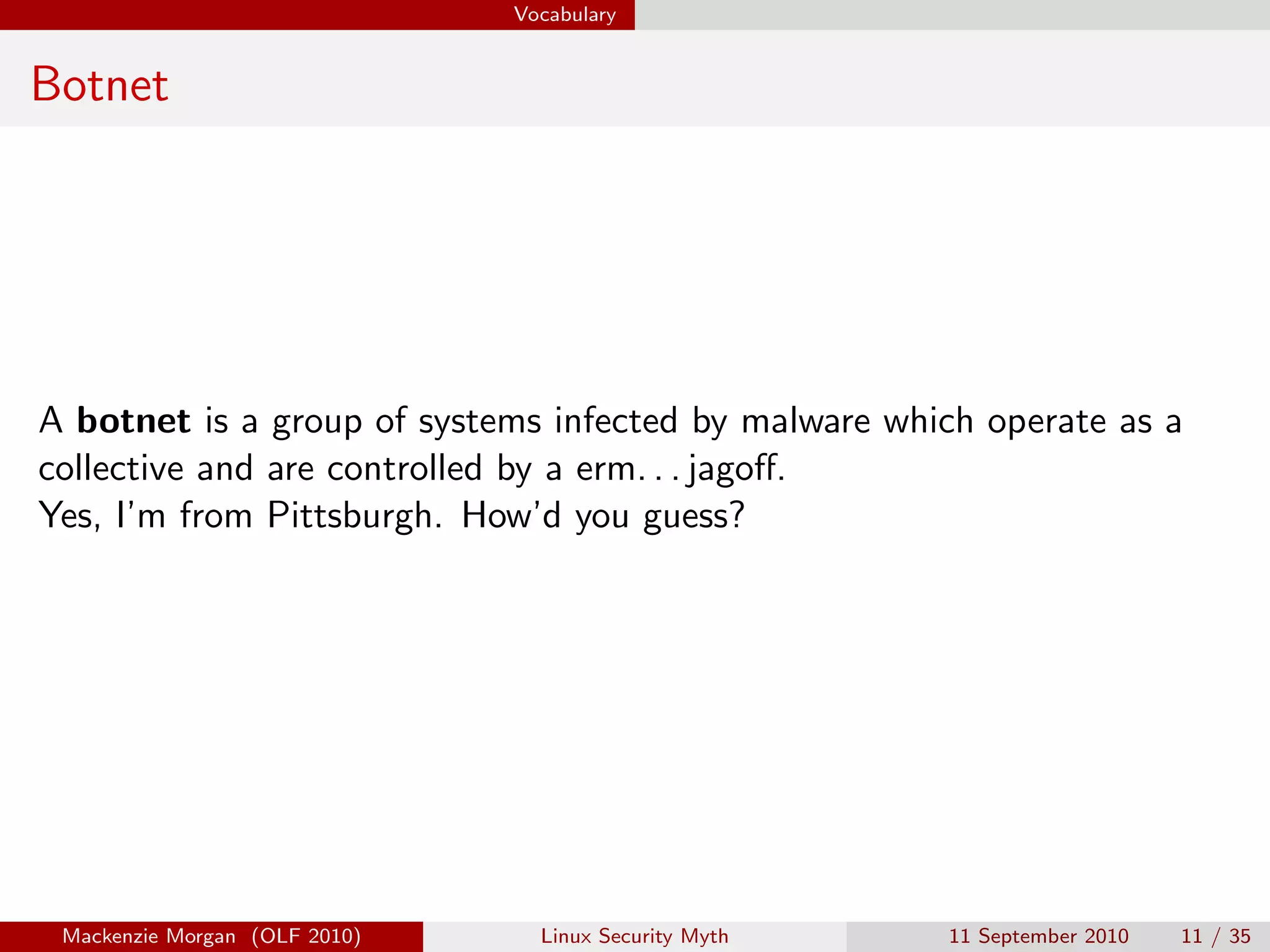
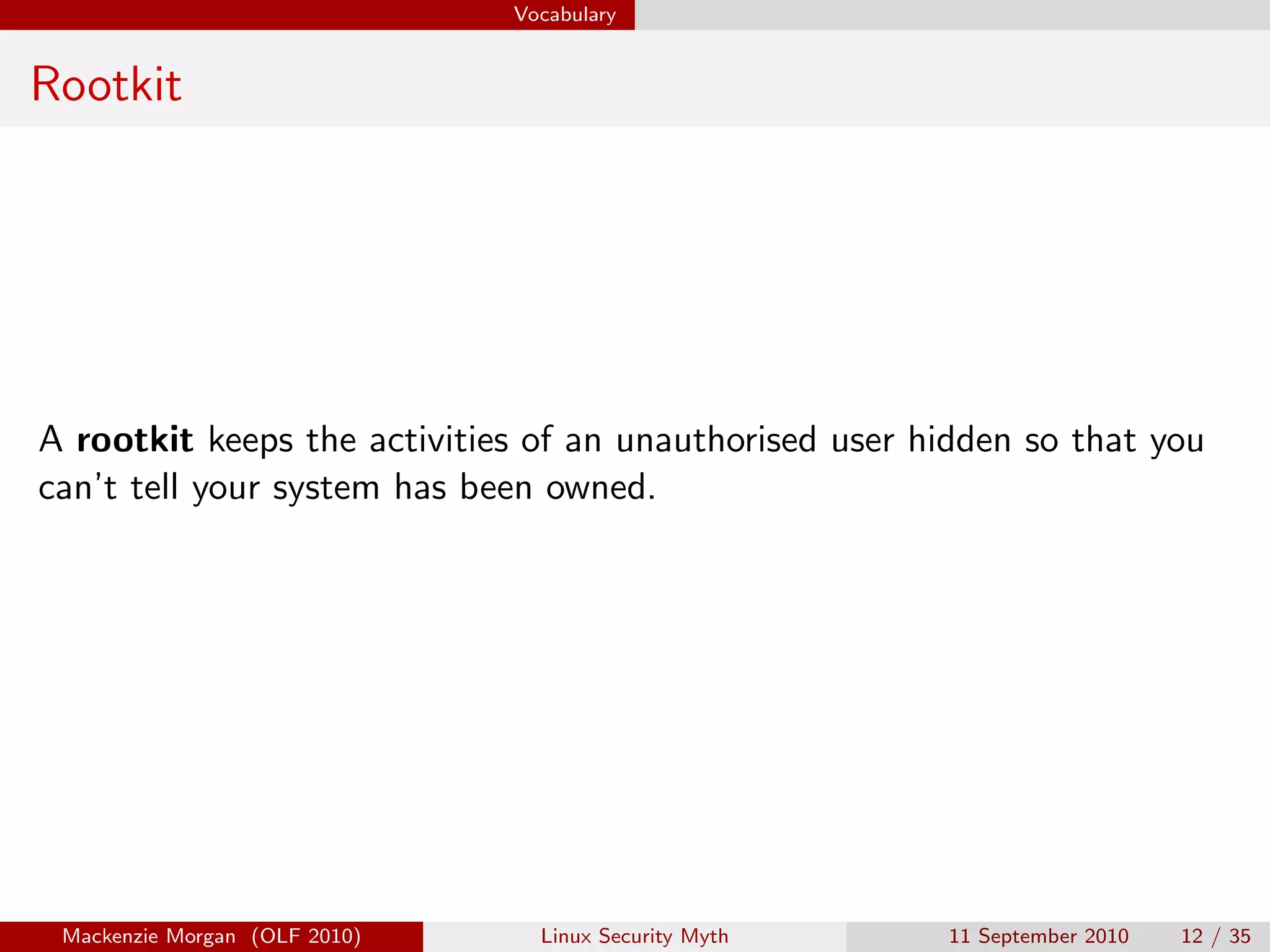
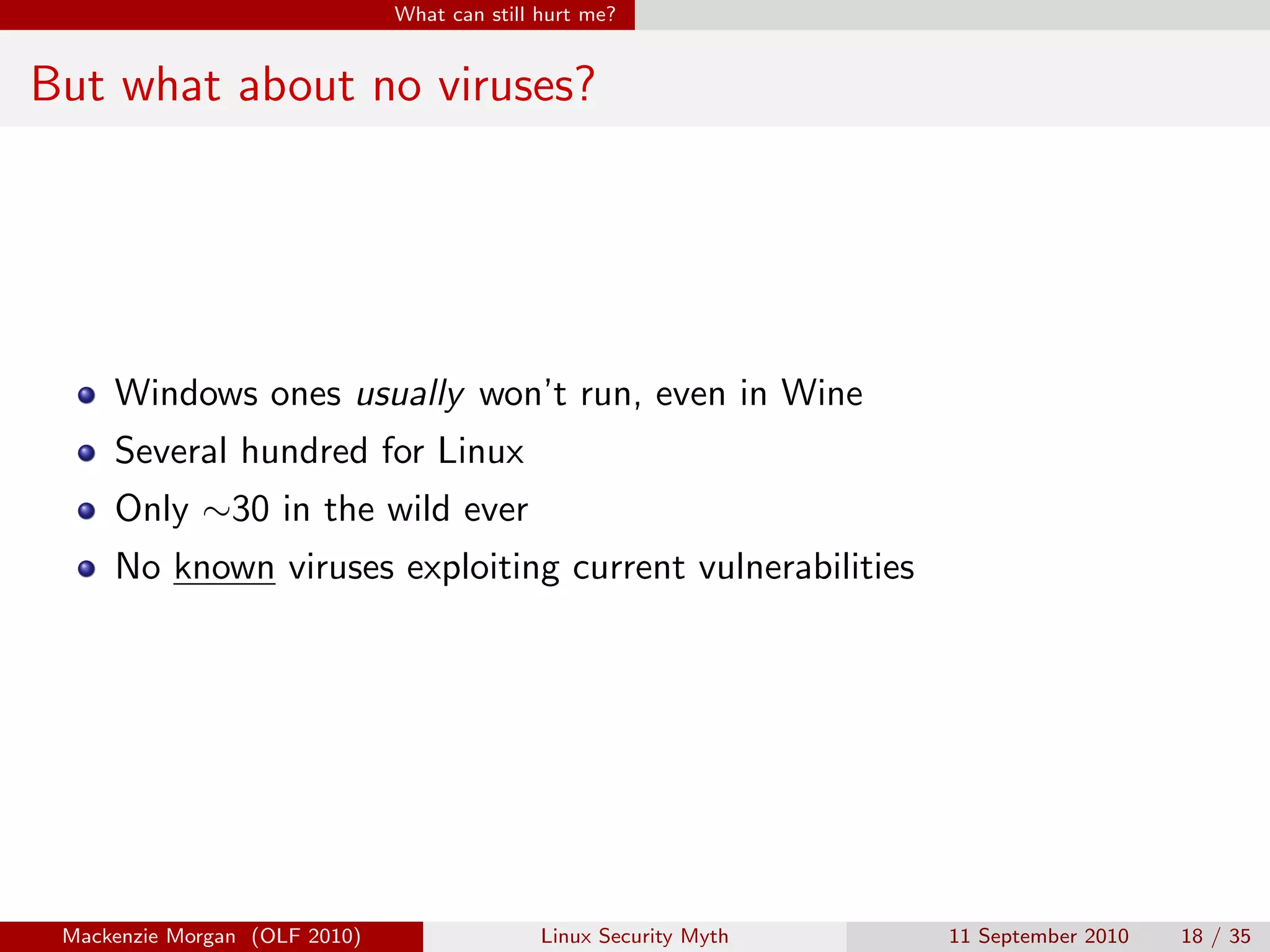
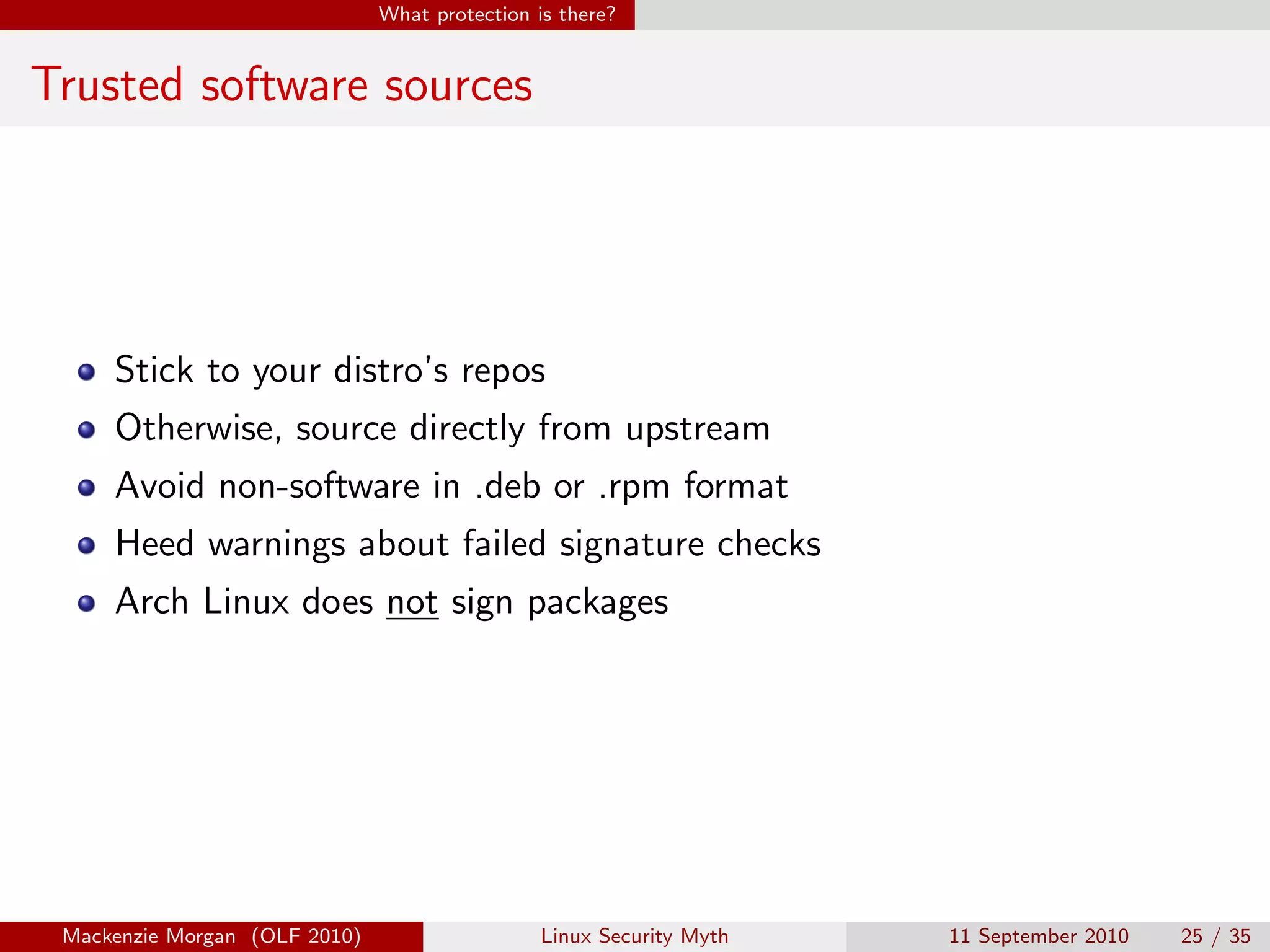
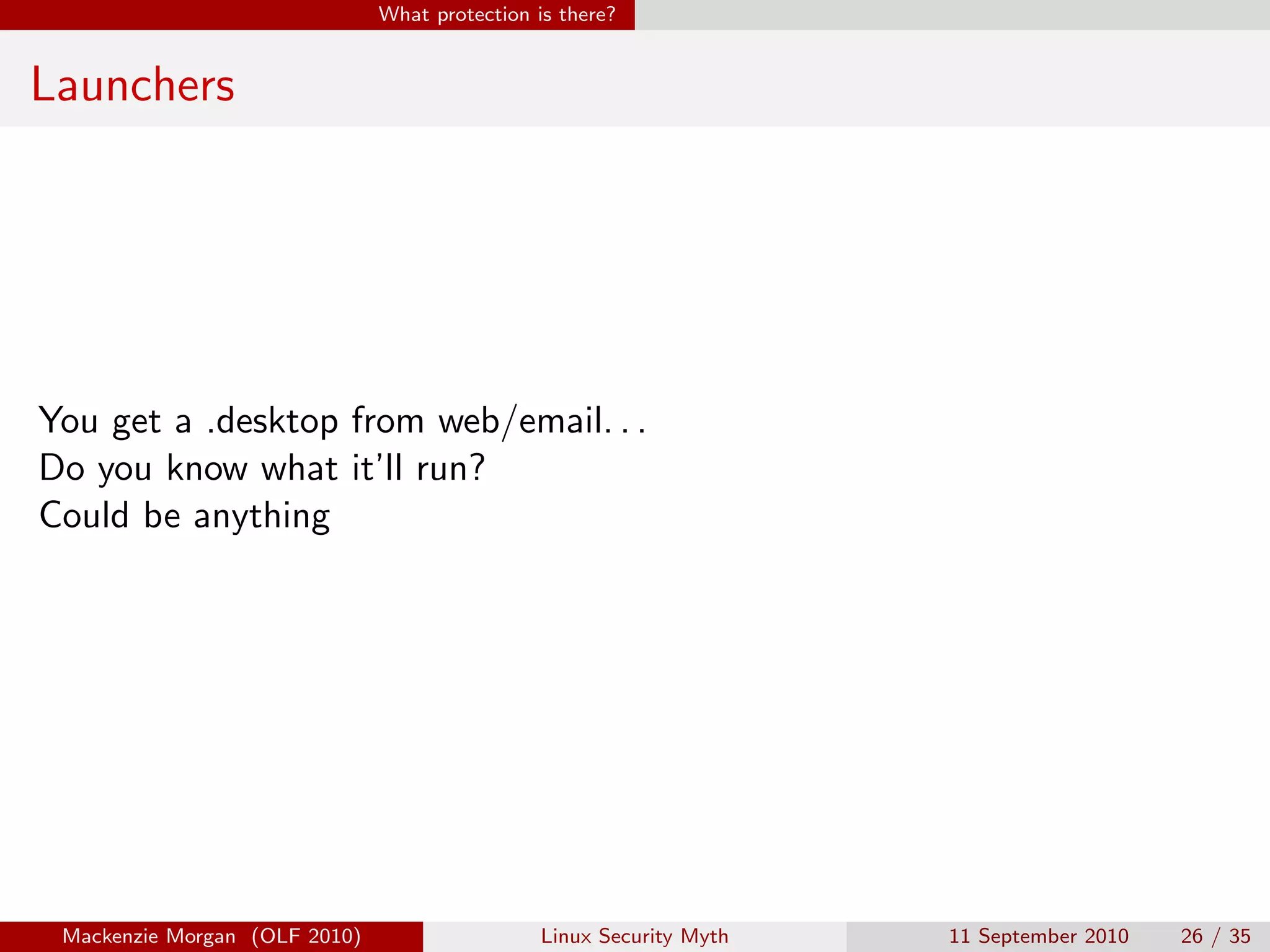
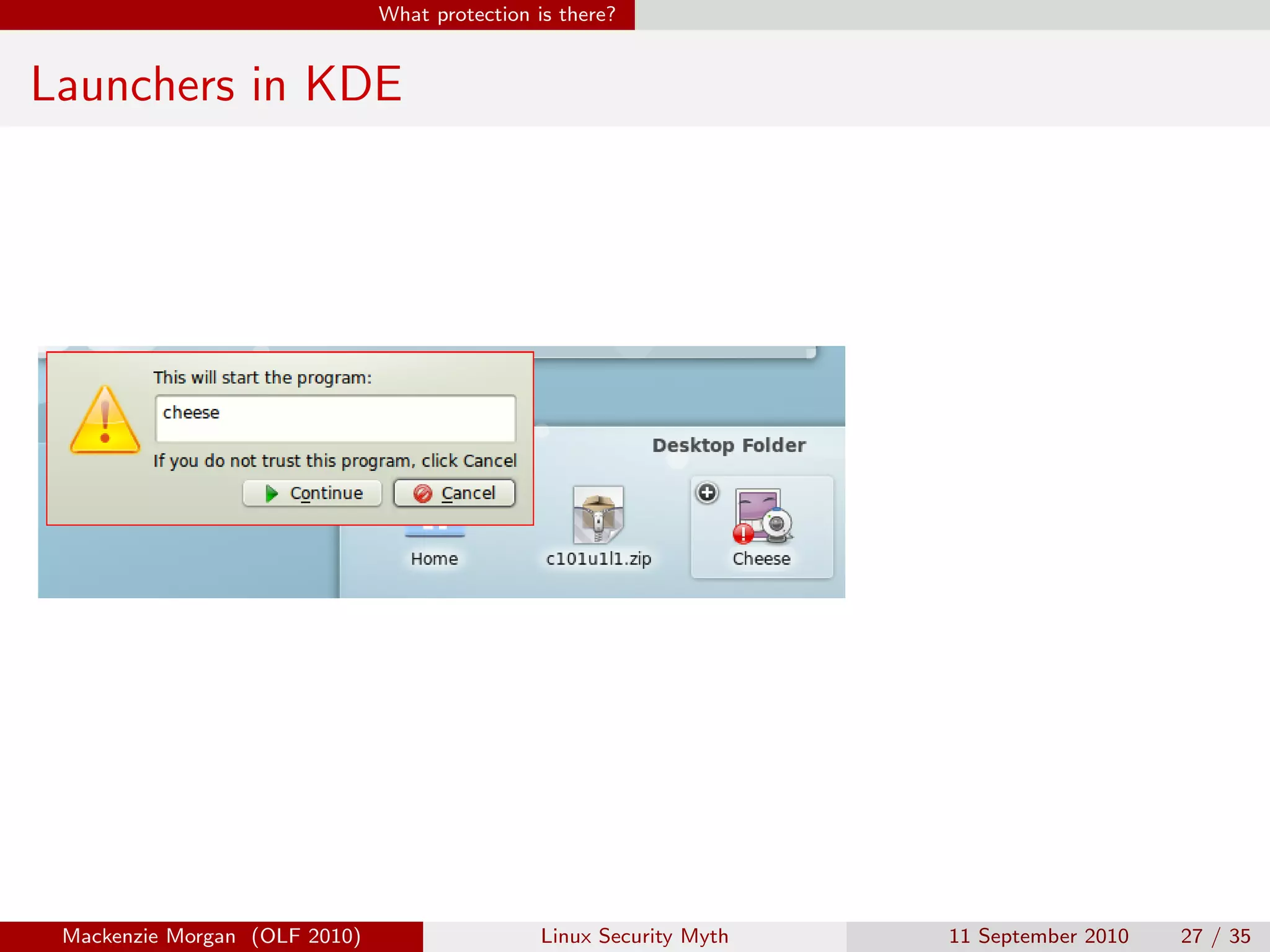
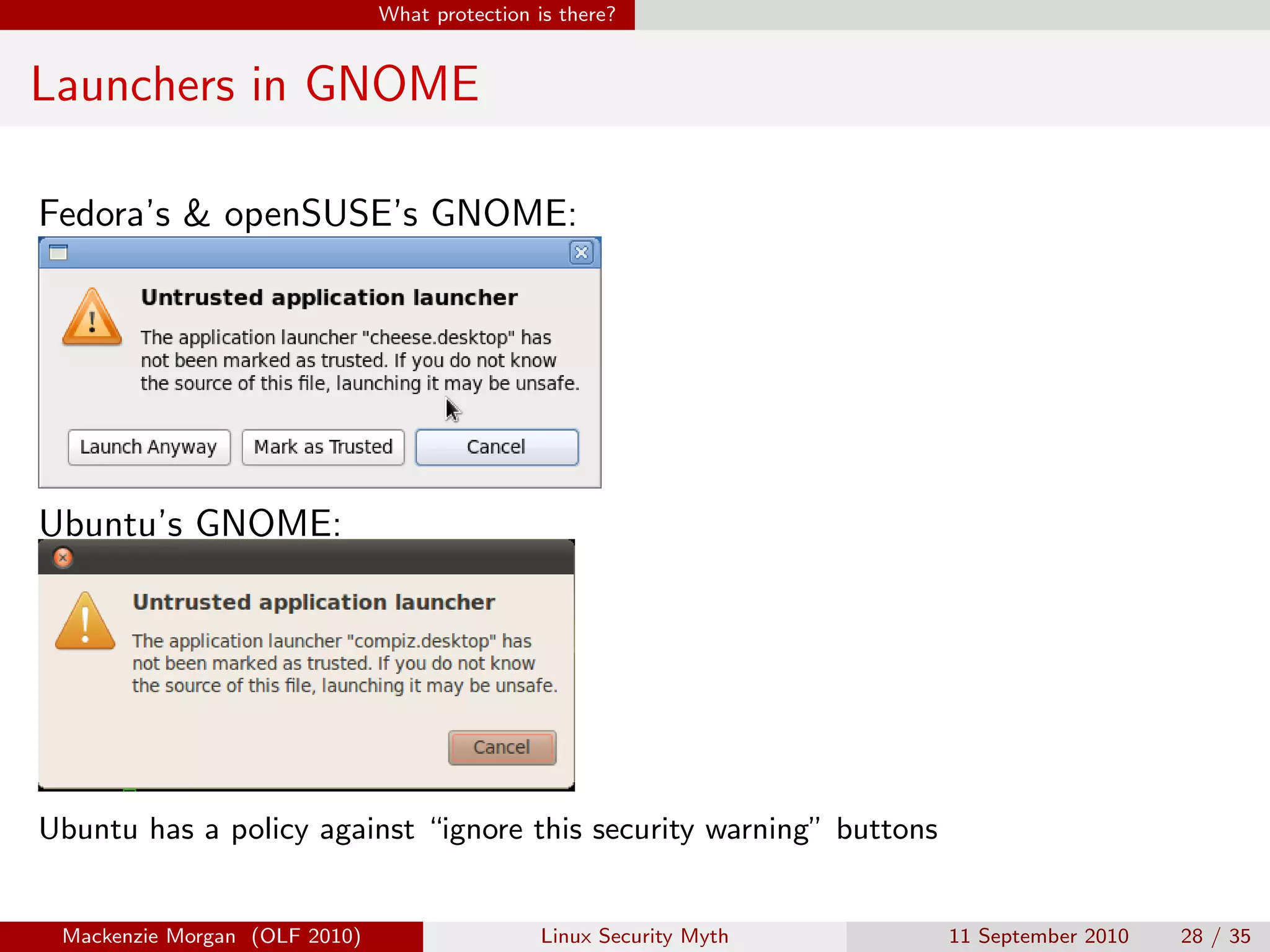
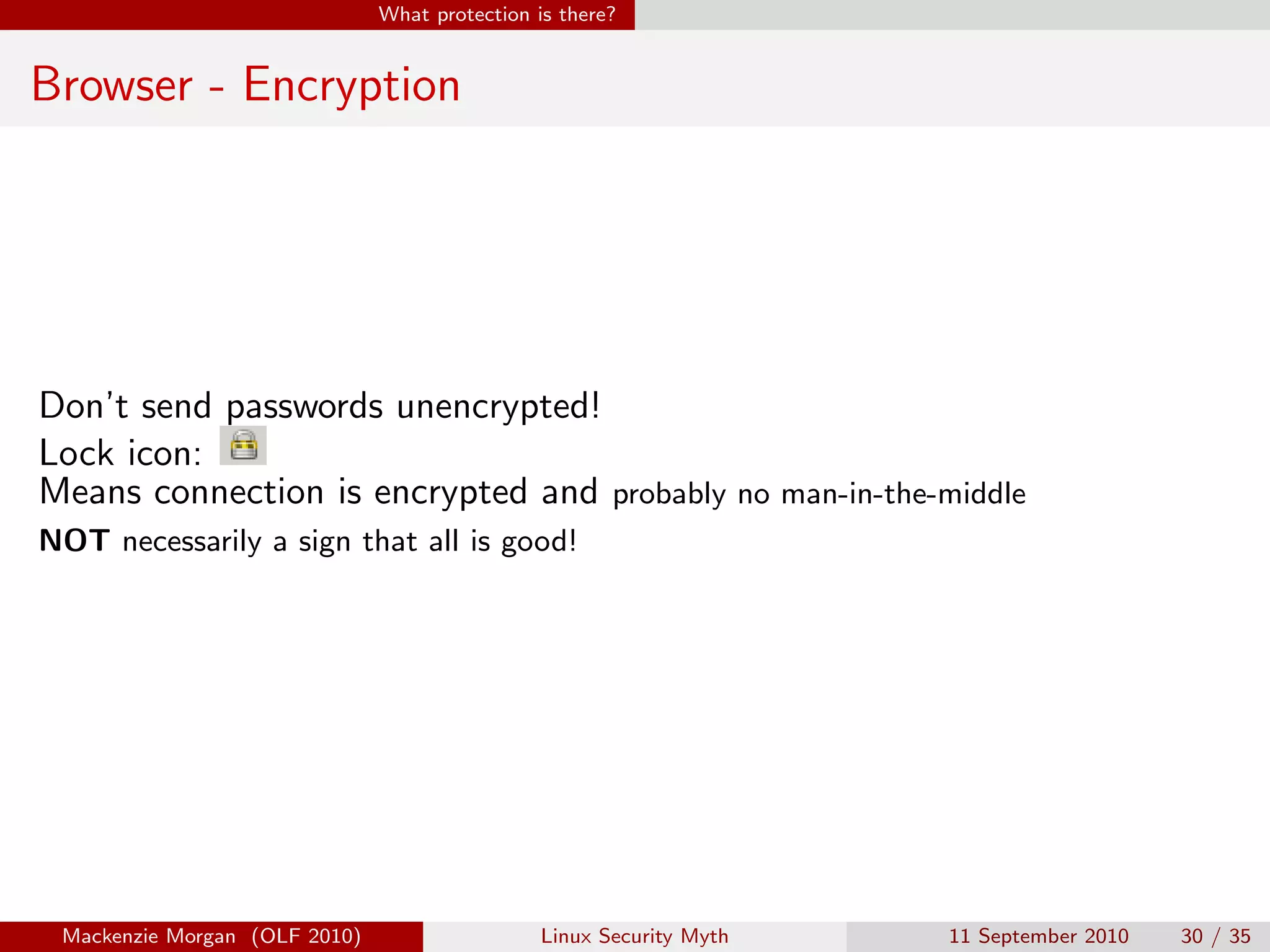
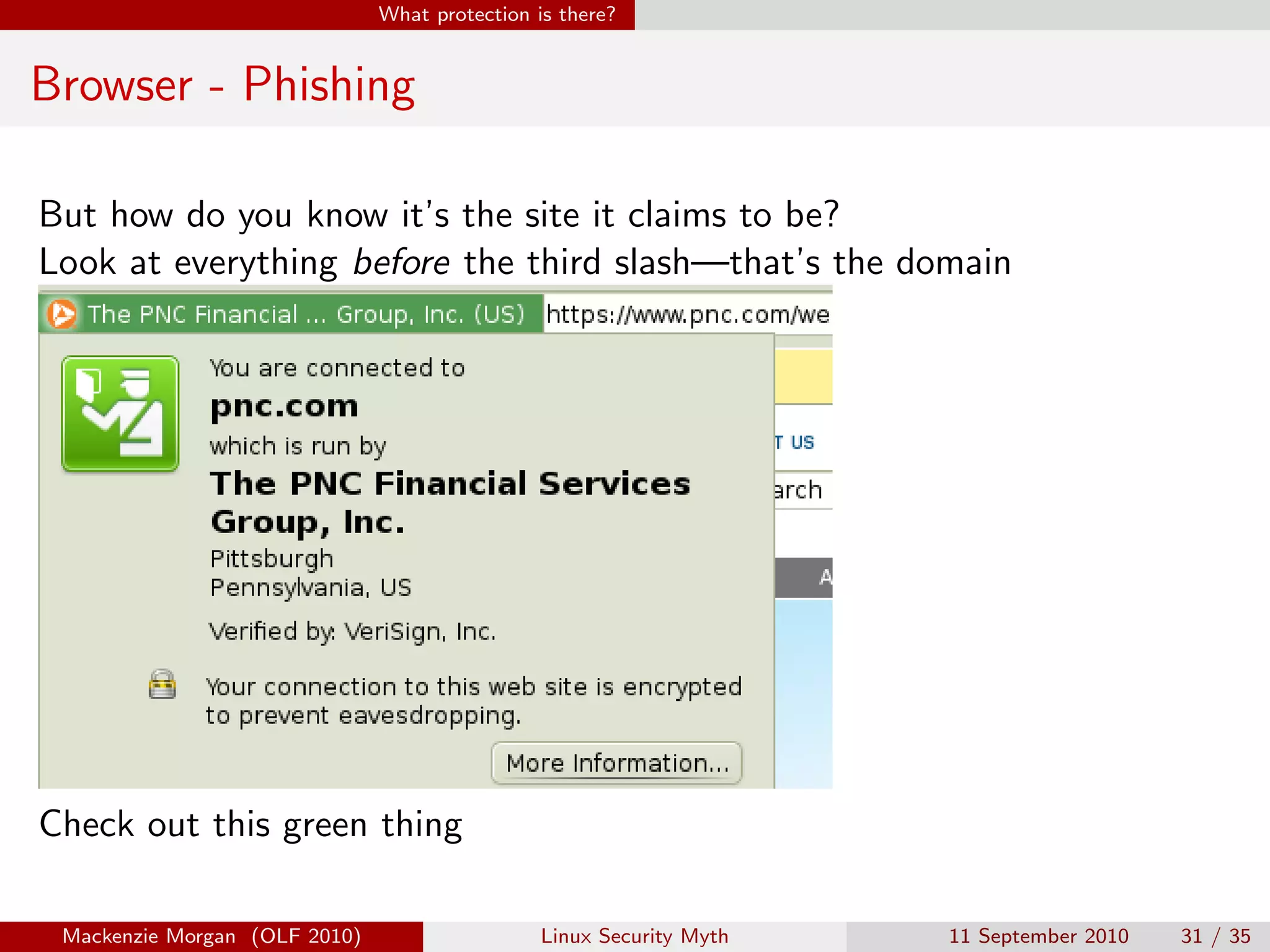
Mackenzie Morgan gave a presentation at Ohio LinuxFest 2010 about the Linux security myth. They discussed that while Linux is less vulnerable to viruses than Windows, it can still be affected by malware through email trojans, untrusted software from third-party repositories, and browser-based attacks. However, users can protect themselves by only installing software from trusted software sources, being cautious of launchers from unknown origins, and using browser plugins like NoScript to block malicious scripts.