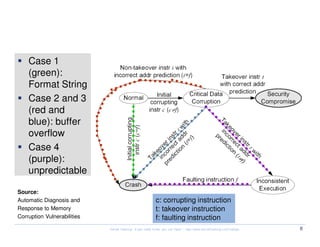
The document discusses the current state of security research, emphasizing challenges faced by exploit writers and the complexities of vulnerability coordination in the industry. It highlights myths about security, the growing market for vulnerabilities, and the necessity of building effective research teams within companies. Additionally, it calls for better understanding and resource allocation to enhance security practices in a rapidly evolving threat landscape.


![Security nowadays – 0day challenge
First host All vulnerable hosts
attacked attacked
Reaction time
Slammer: 10 mins
Future worms: < 1 minute [Staniford et. al. 2002]
“0day Statistics
Average 0day lifetime:
348 days
Shortest life:
99 days
Longest life:
1080 (3 years)"
- Justine Aitel
Kernel Hacking: If you really know, you can hack! – http://www.kernelhacking.com/rodrigo 5](https://image.slidesharecdn.com/rubira-111012185147-phpapp02/85/Vale-Security-Conference-2011-17-Rodrigo-Rubira-Branco-BSDaemon-5-320.jpg)