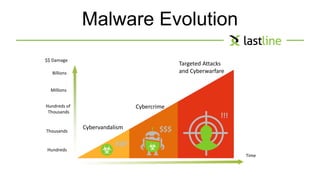
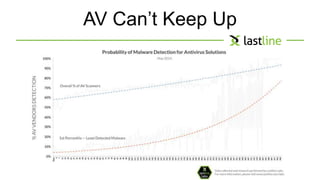
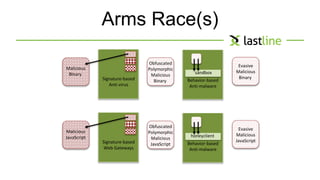
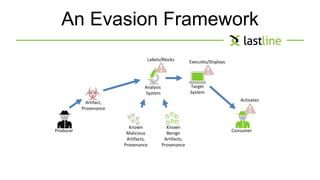
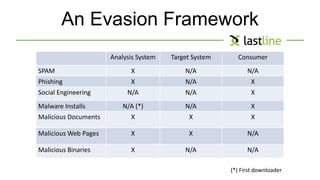
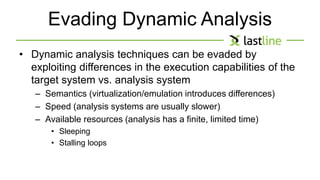
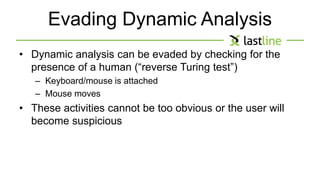
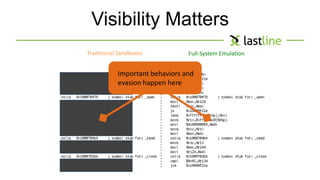
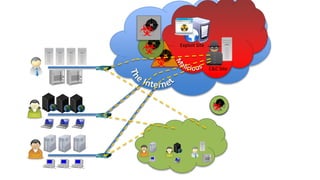
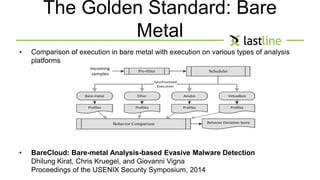
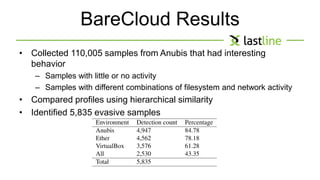
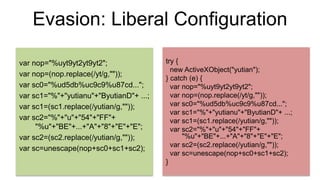
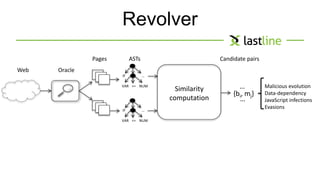
This document discusses evasive malware and techniques for detecting it. It begins with an introduction of the author and their background in malware research. It then covers how malware has evolved over time to target systems and evade detection. Various techniques used by malware to evade static and dynamic analysis are described. The document argues that eliciting dormant code and introducing honey-users could help with detection. It concludes that visibility is key to tracking evasive malware and more advanced analysis methods are needed.