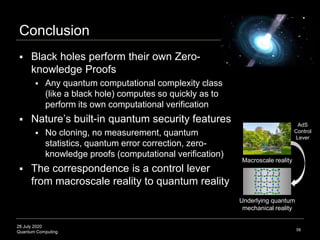
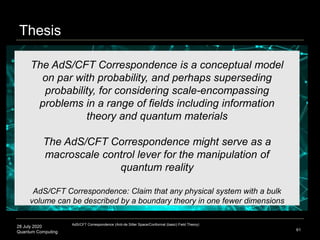
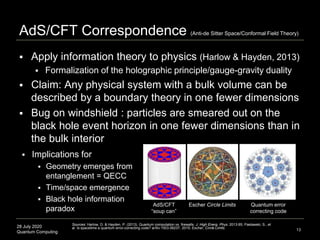
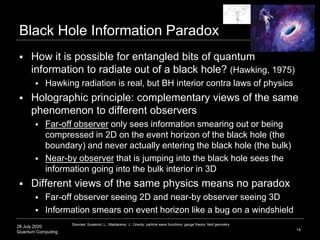
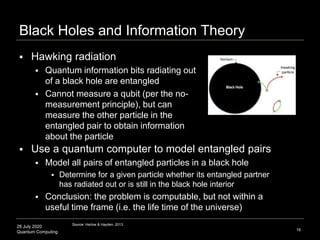
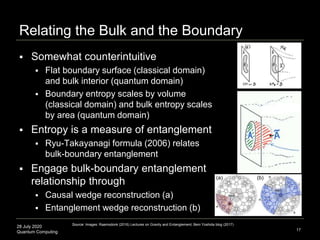
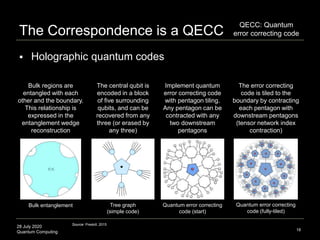
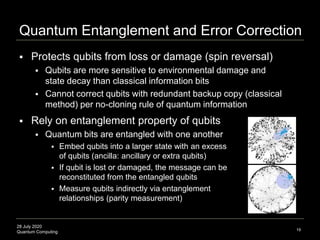
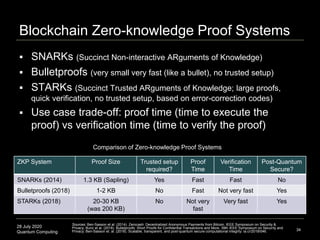
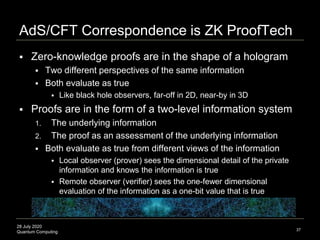
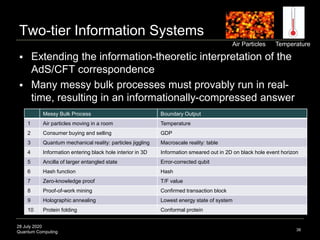
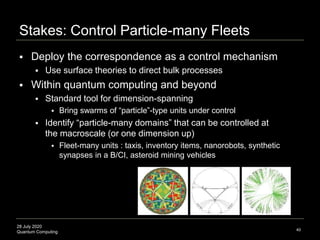
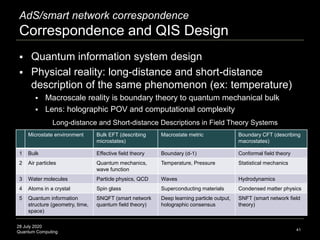
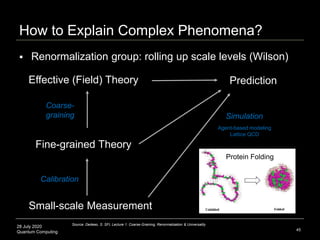
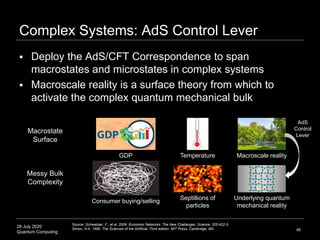
The document presents an advanced lecture on quantum computing, detailing theoretical concepts such as the ADS/CFT correspondence, black holes, and information theory. It discusses the implications of how quantum systems can be modeled and computed, particularly focusing on the nature of entanglement and quantum error correction. Additionally, it highlights the relationship between classical and quantum entropy and the significance of these findings for understanding computational complexity within quantum mechanics.



![28 July 2020
Quantum Computing
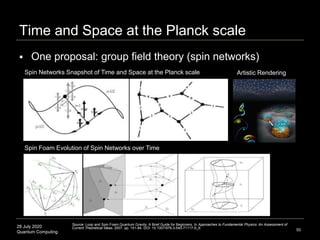
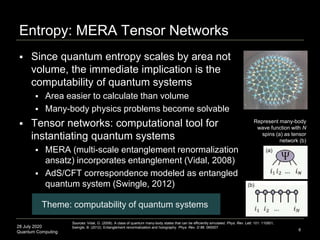
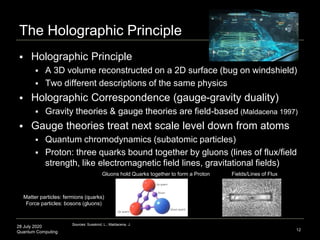
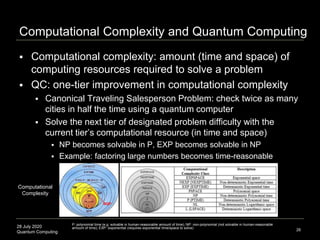
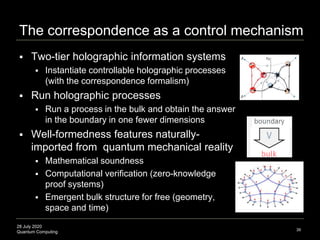
Quantum Error Correction Codes (QECC)
22
Various encoding schemes proposed
Syntax: [ancilla size, logical bit size, distance], bit format
Qutrit code: [3,1,2]3 means 3 physical qutrits, to protect 1 logical
qutrit, over a distance metric of 2 (deletions up to 1 can be
protected (2–1 = 1)), and the bit format is 3 (a qutrit, not a qubit)
Pentagon code: [5,1,3]2 means 5 physical qubits, 1 logical qubit,
with distance 3, and bit format 2 (qubit as opposed to qutrit)
1 logical degree-of-freedom in the bulk (pentagon center) to 5
physical degrees-of-freedom on the boundary (5 sides of pentagon)
Holographic
Code
Code Structure
[ancilla size, logical
bit size, distance]
Quantum
Information Bits
Physical Logical
Distance and
# Deletions
Protected
Quantum
Information
Digit Format
Qutrit code [3,1,2]3 3 1 2;1 Qutrit
Pentagon code [5,1,3]2 5 1 3;2 Qubit](https://image.slidesharecdn.com/quantumcomputing2-software-200826175742/85/Quantum-Computing-Lecture-2-Advanced-Concepts-23-320.jpg)









![28 July 2020
Quantum Computing
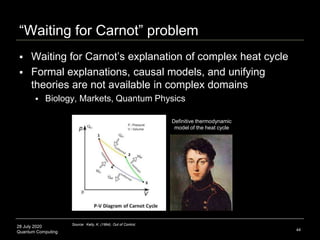
Emergence of bulk geometry, space, time
Spatial transformations
Symmetry (Bogoliubov transformations)
Radial directionality (inward-outward orientation to bulk center)
Entropy (Ryu-Takayanagi bulk-boundary entanglement entropy)
Temporal transformations
Boundary defined as Cauchy surface (plane with time dimension)
MERA tensor networks and random tensors to iterate time and
connect regions with geometry and regions with particle interaction
Example: construct one-dimensional conformal field theories from
tensors that only depend on the time variable (Witten, 2016)
Geometric spacetimes (Qi, 2017, Holographic coherent states)
Superposition of geometries: boundary state described as a
superposition of different spatial geometries in the bulk
49
Sources: Witten, E. (2016). An SYK-Like Model Without Disorder. arXiv:1610.09758 [hep-th]; Qi, X.-L., Yang, Z. & You, Y.-Z. (2017).
Holographic coherent states from random tensor networks. JHEP 08(060):1-34.
Correspondence-identified Emergence](https://image.slidesharecdn.com/quantumcomputing2-software-200826175742/85/Quantum-Computing-Lecture-2-Advanced-Concepts-50-320.jpg)