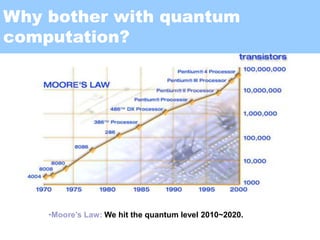
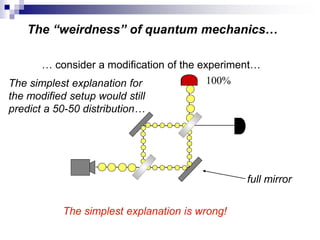
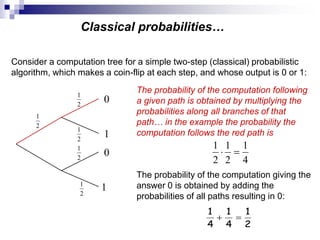
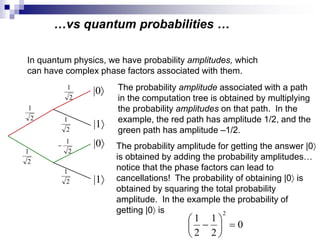
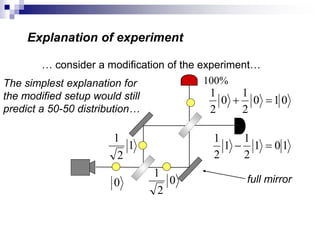
This document provides an overview of quantum computing, including:
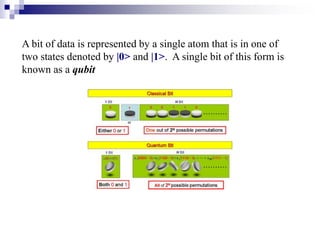
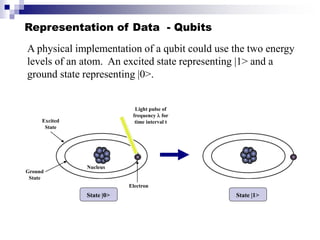
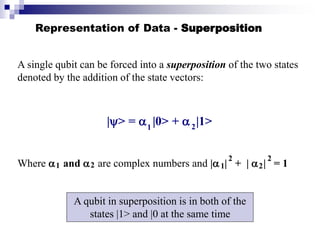
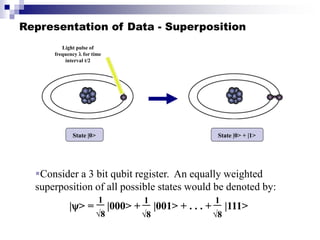
- Quantum computers store and process information using quantum bits (qubits) that can exist in superpositions of states allowing exponential increases in processing power over classical computers.
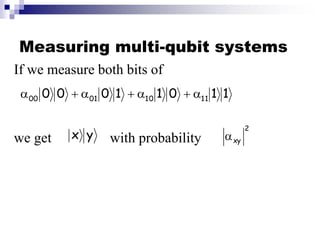
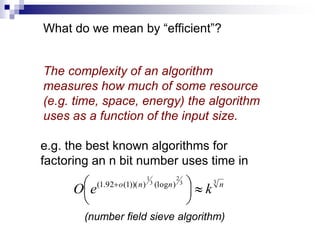
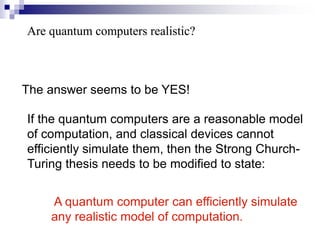
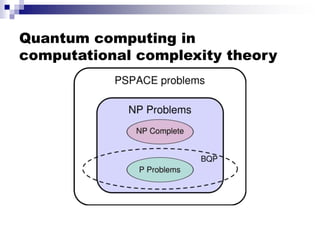
- Key concepts include qubit representation and superpositions, entanglement, measurement and computational complexity classes like BQP.
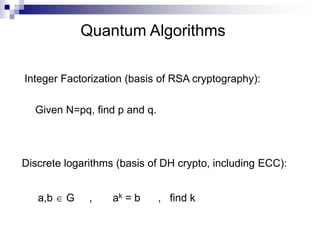
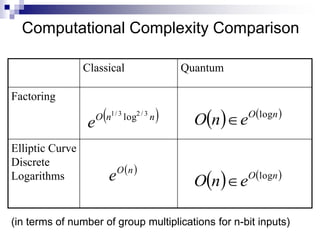
- Quantum algorithms show exponential speedups over classical for factoring, discrete log, and some other problems.
- Implementation challenges include building reliable qubits, controlling operations, and error correction. Leading approaches use trapped ions, NMR, photonics, and solid state systems.