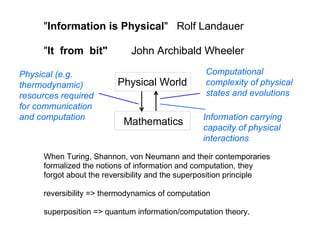
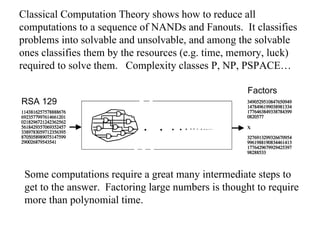
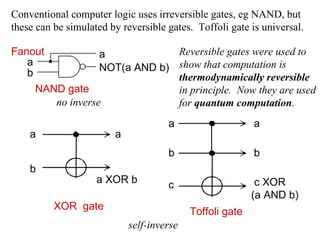
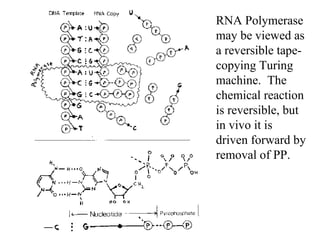
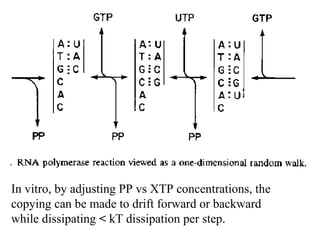
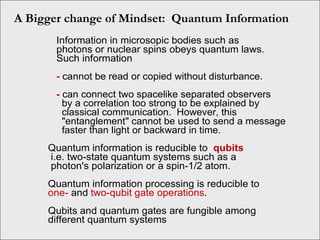
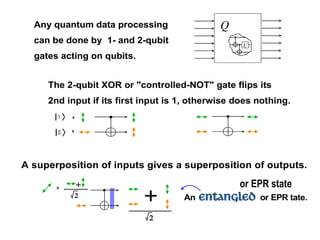
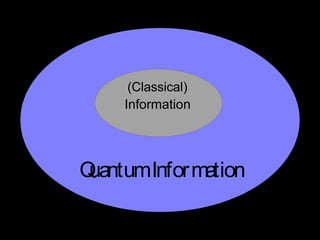
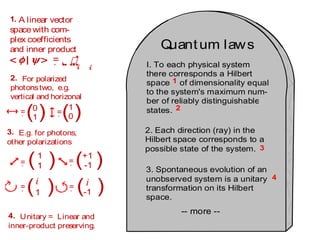
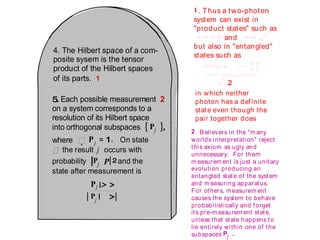
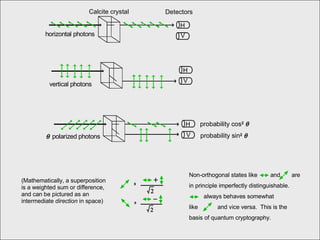
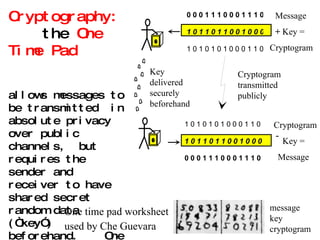
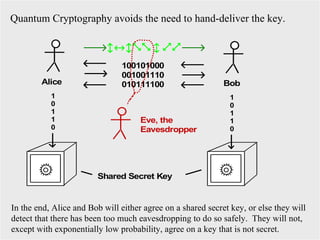
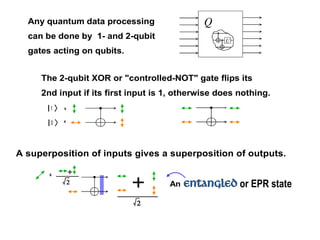
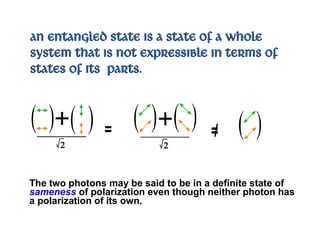
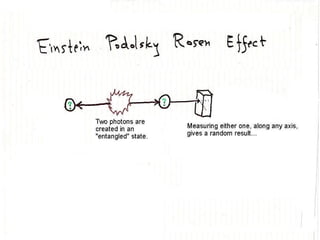
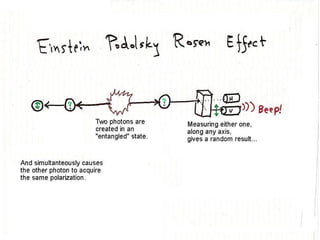
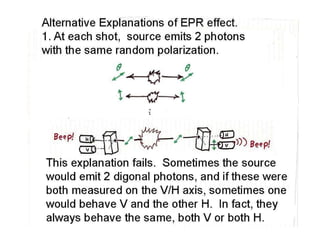
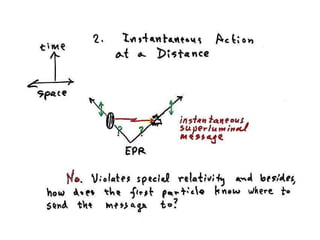
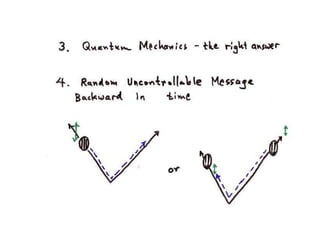
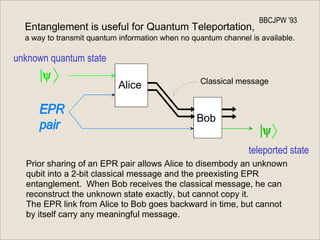
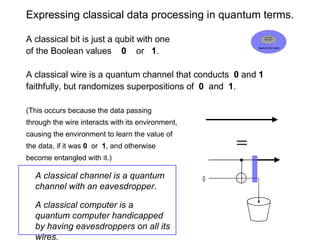
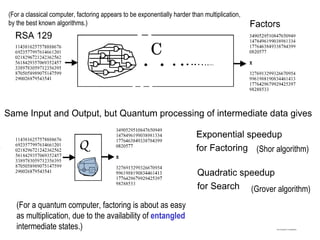
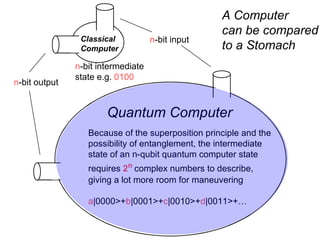
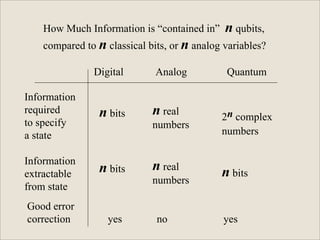
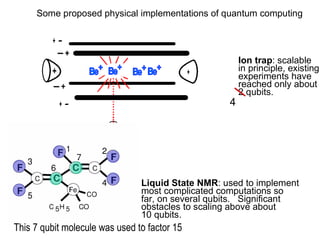
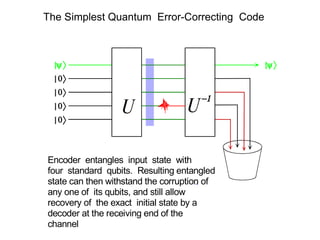
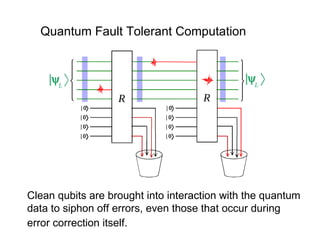
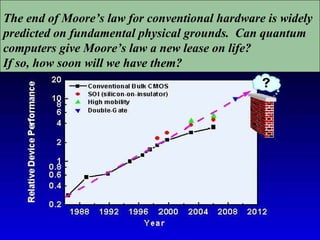
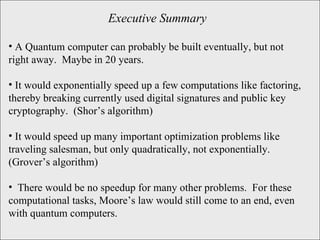
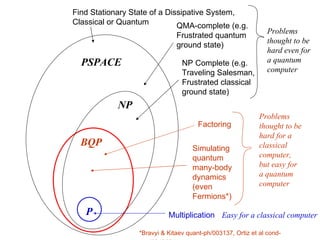
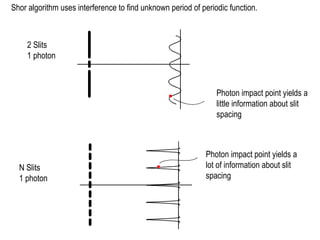
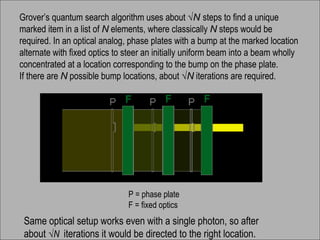
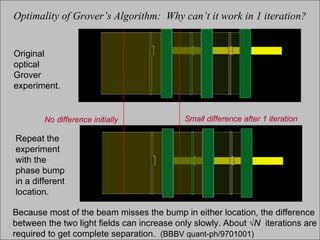
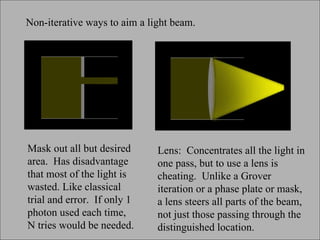
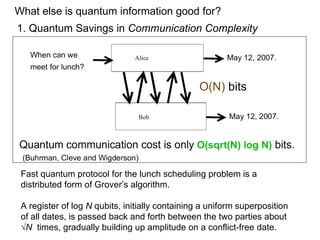
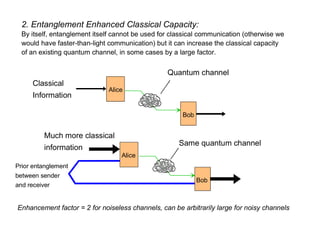
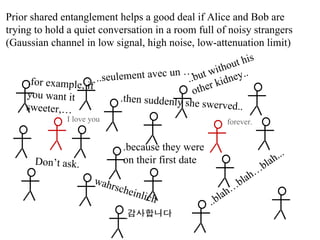
The document discusses quantum computing and its potential applications and implications. It notes that quantum computers could provide exponential speedups for some computations like factoring, breaking current cryptography. However, they would provide only quadratic speedups for many optimization problems. While speeding up simulations of quantum systems, there are no speedups for many other problems. Quantum information is also useful for applications beyond computation like cryptography, communication, and metrology. Overall, quantum computing is an exciting area of basic science but practical quantum computers able to outperform classical ones may still be decades away.