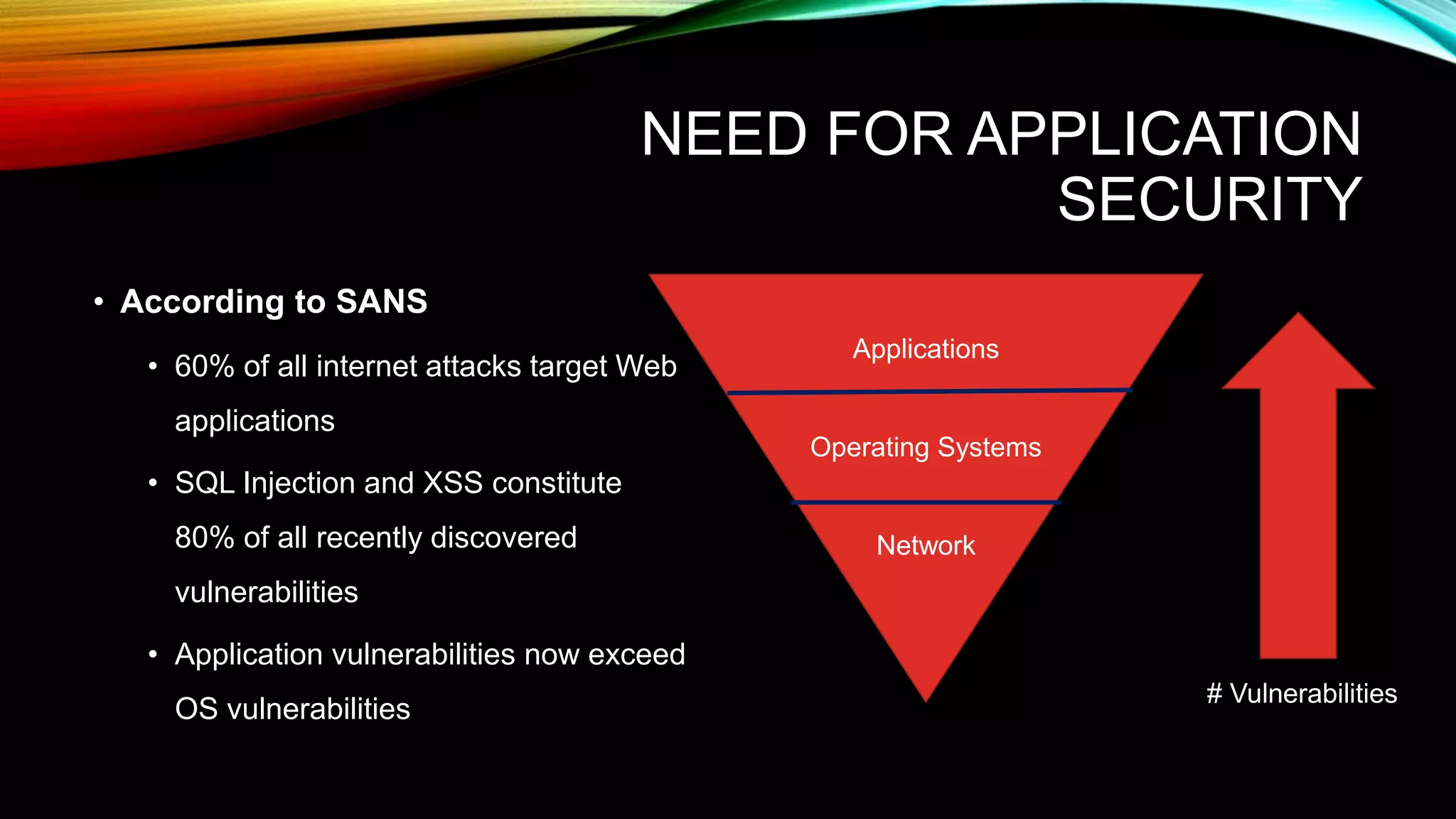
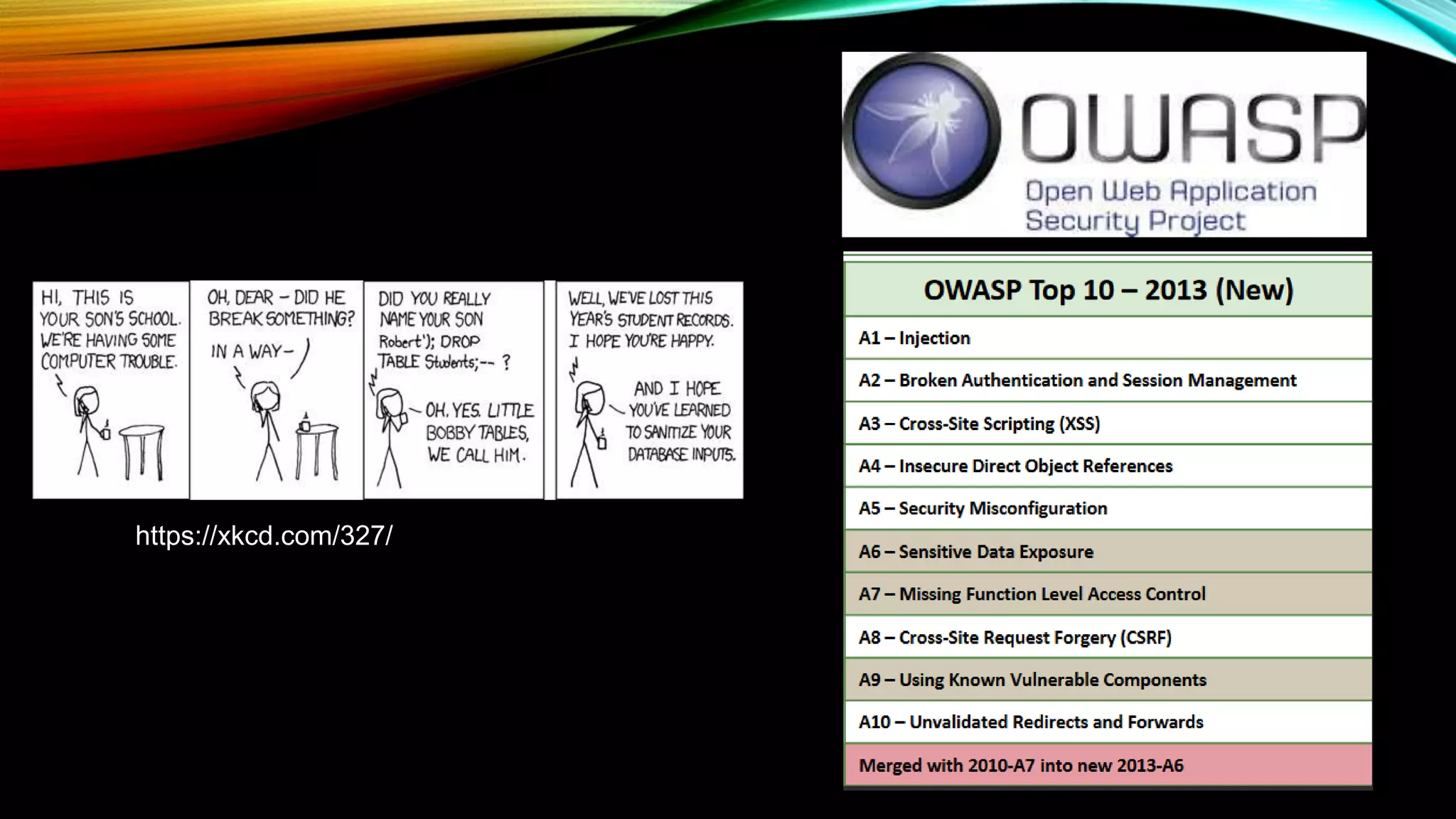
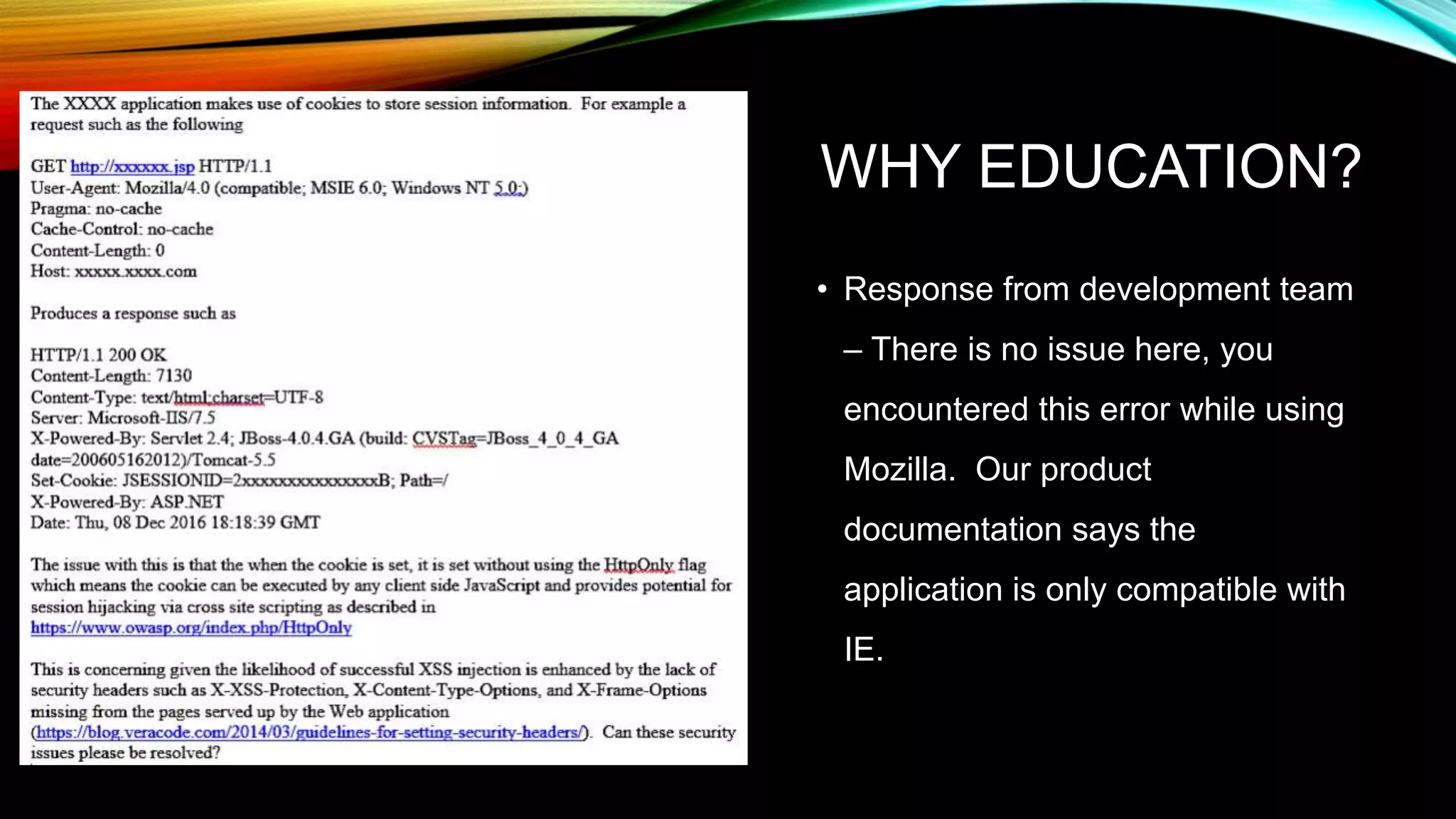
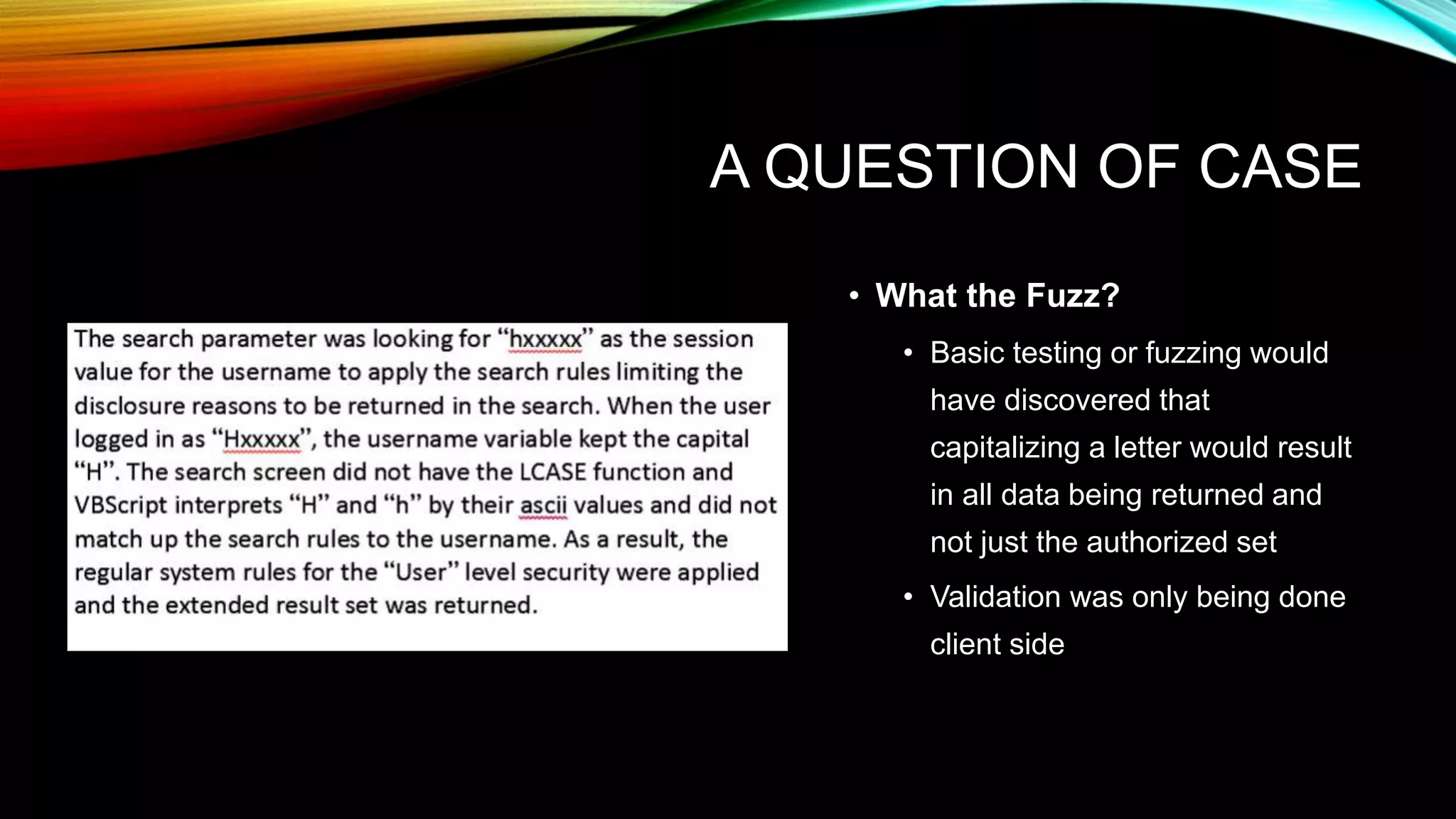
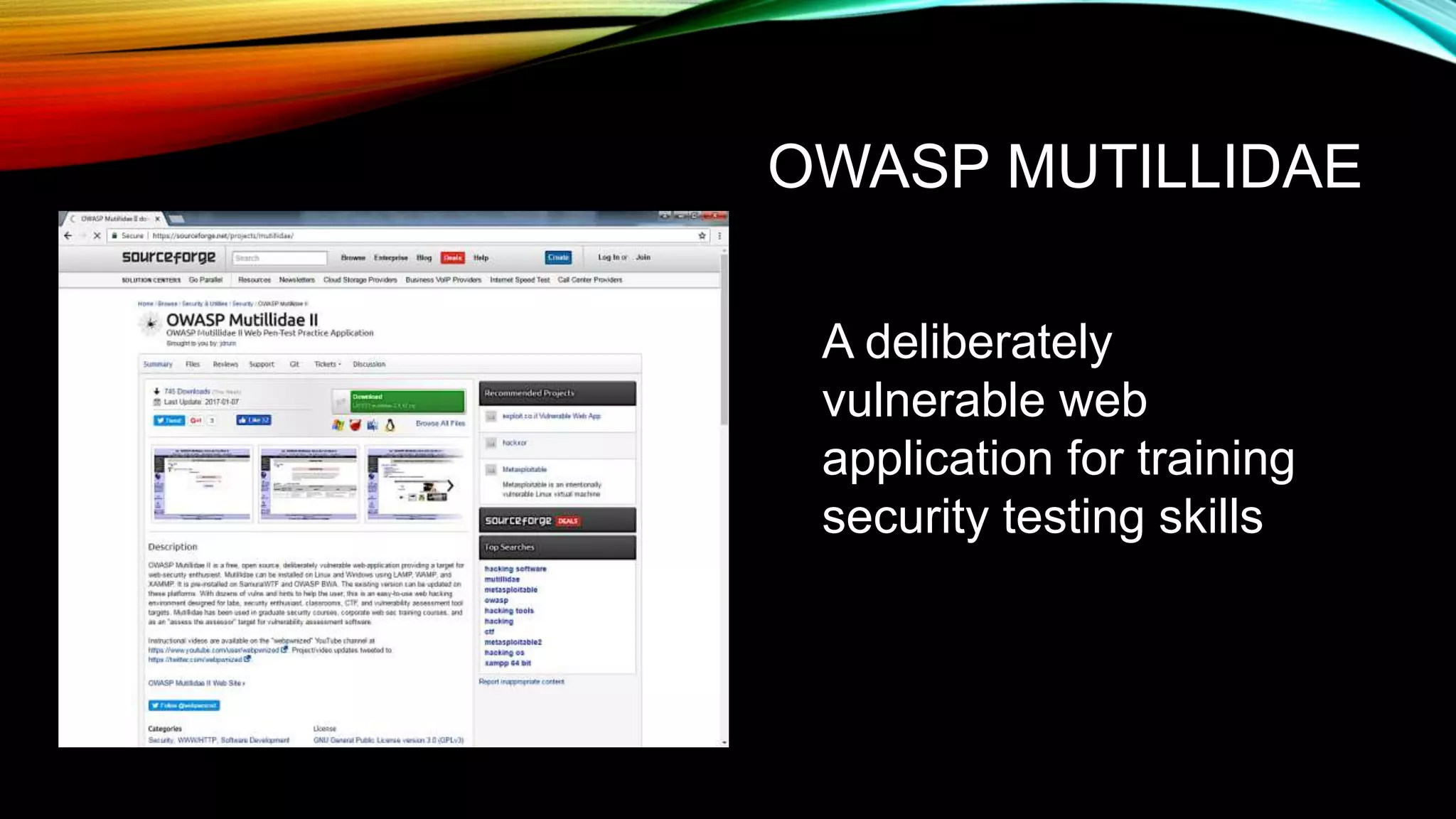
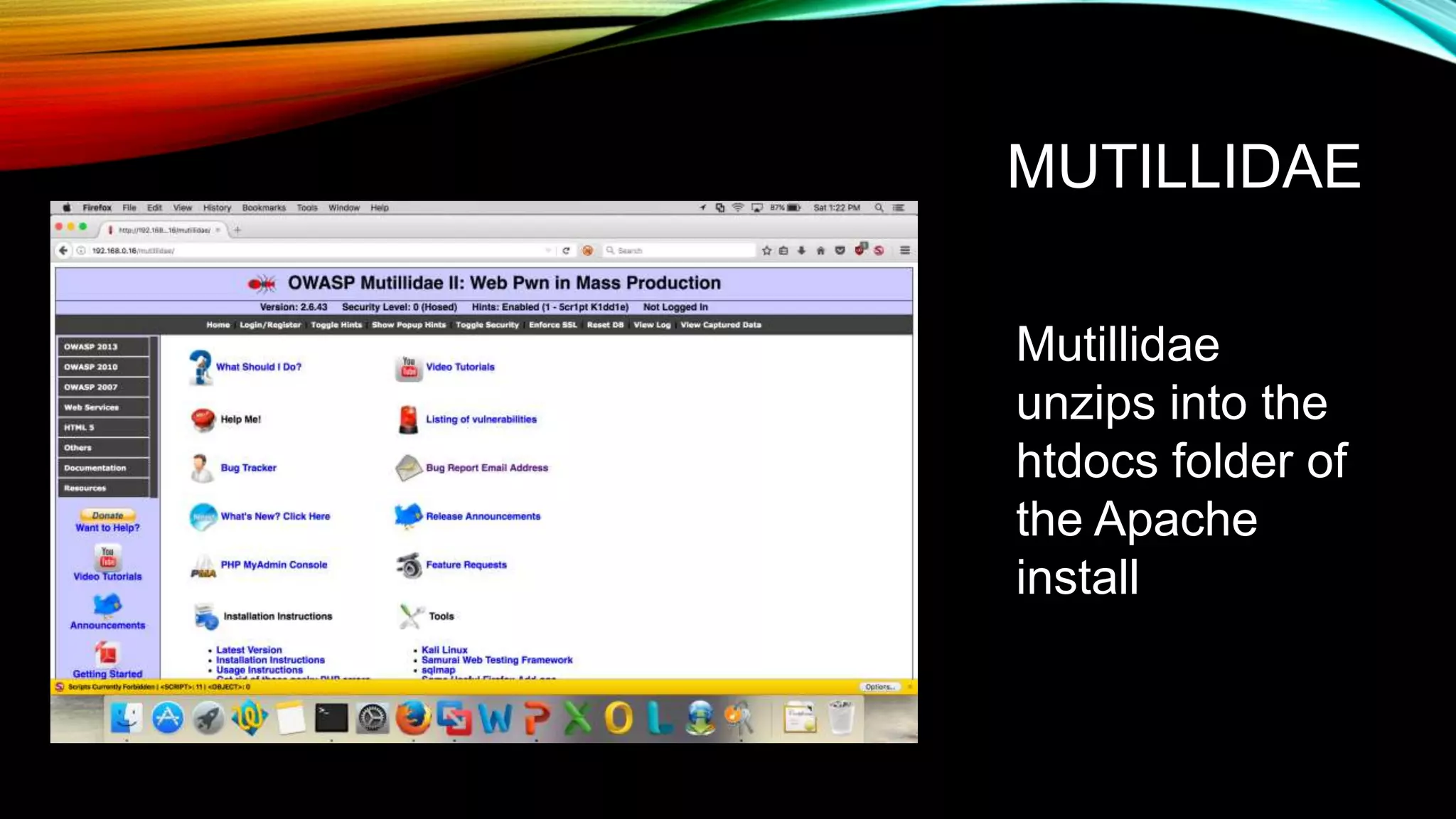
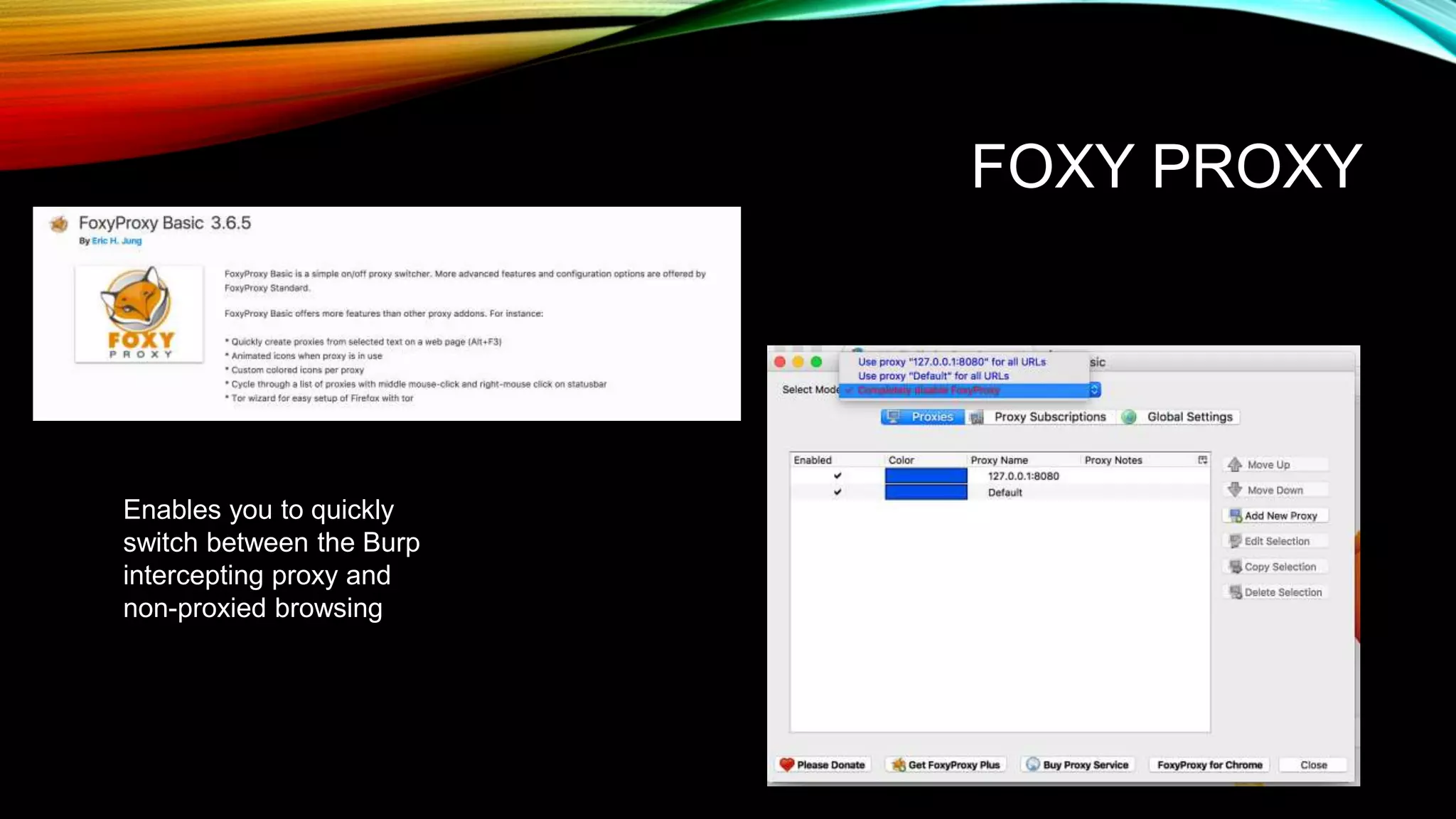
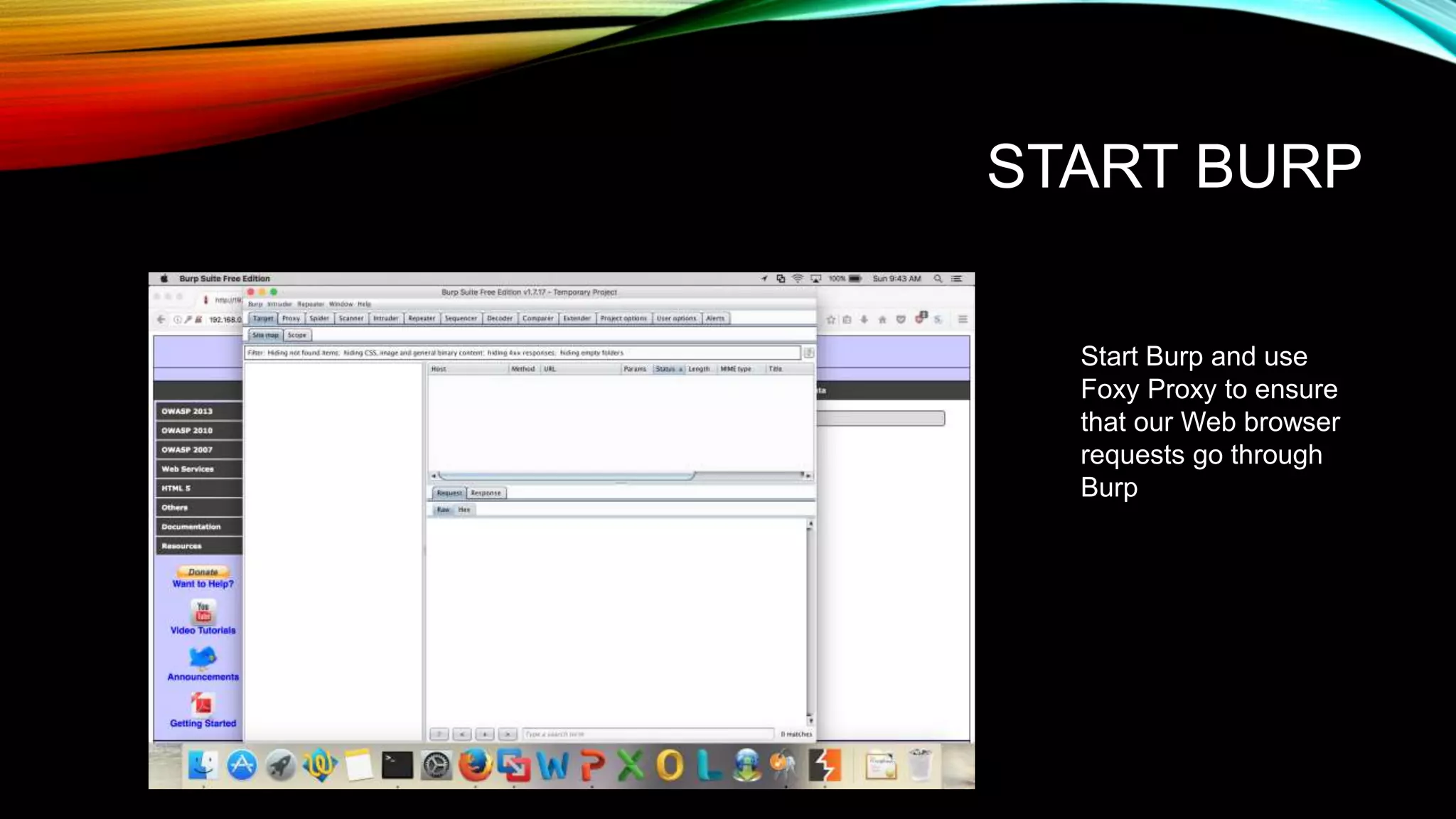
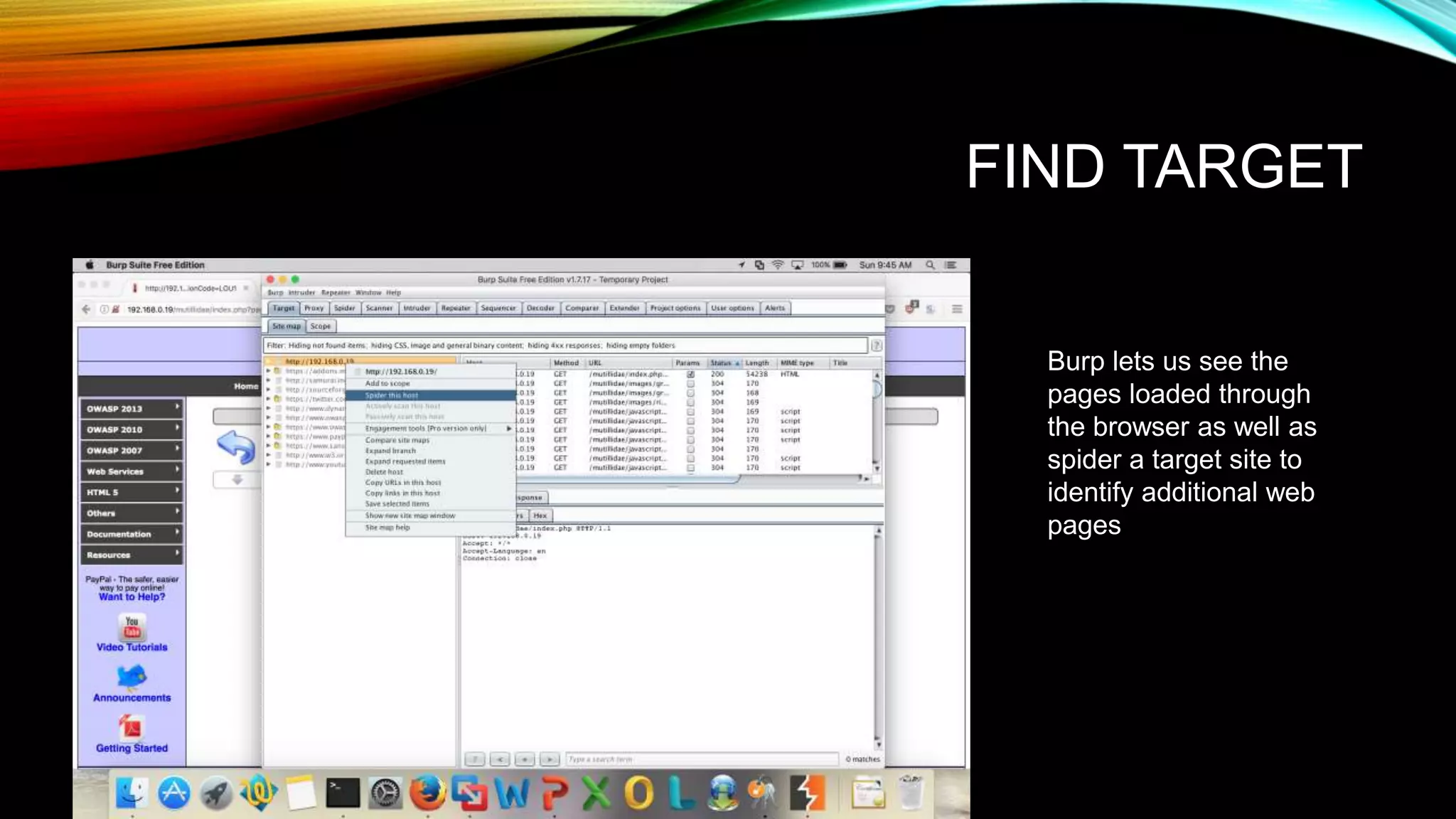
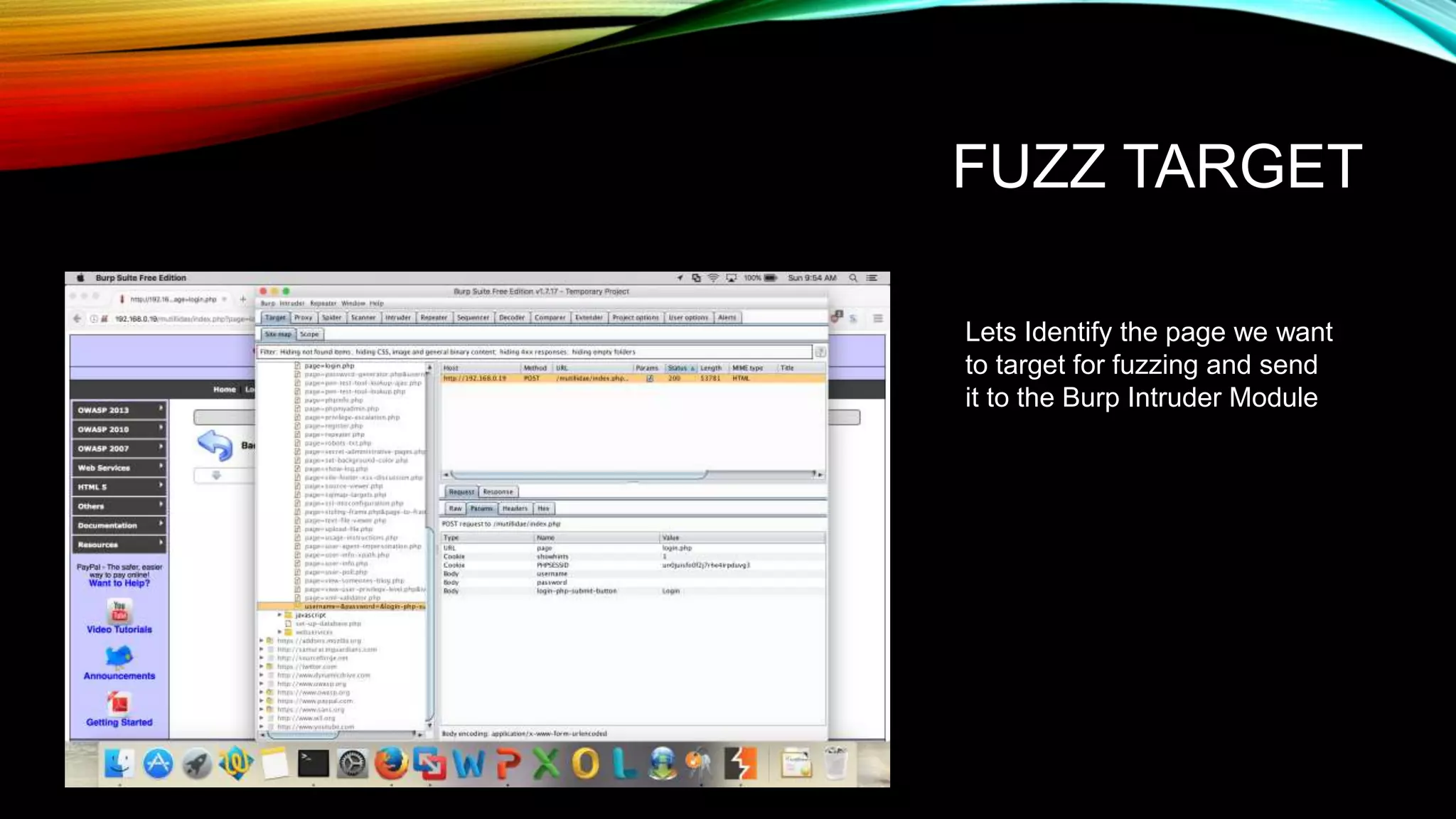
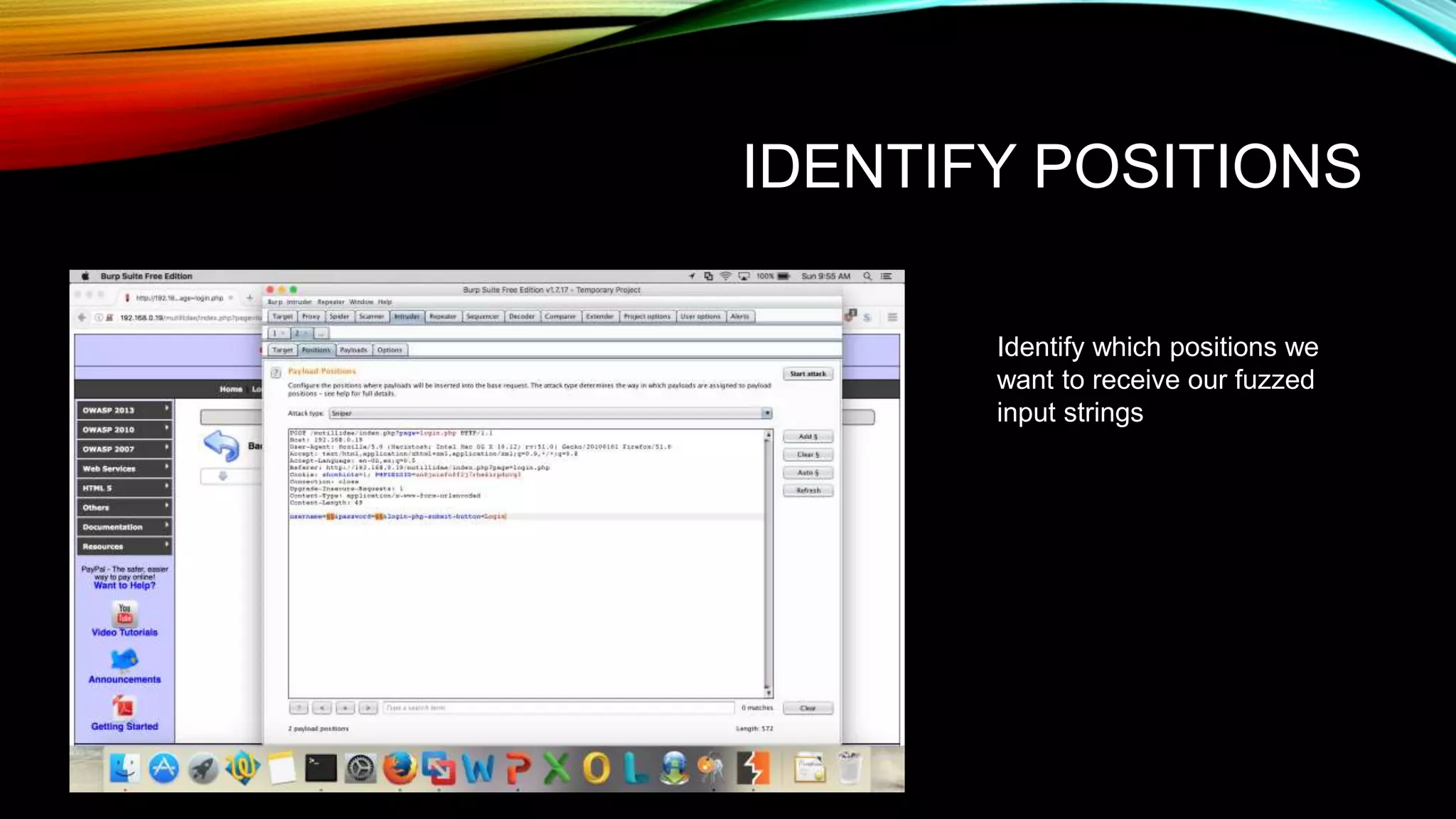
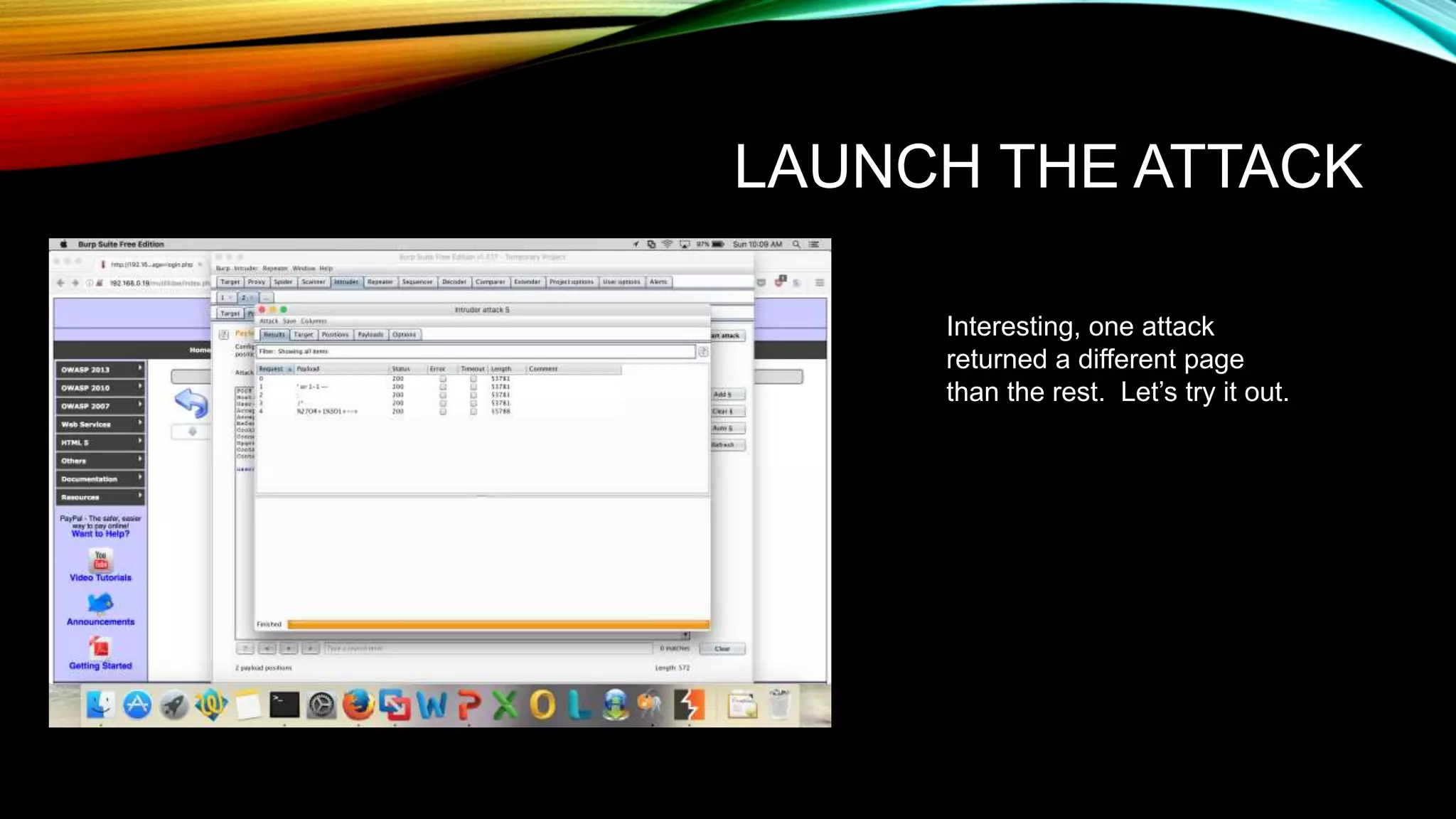
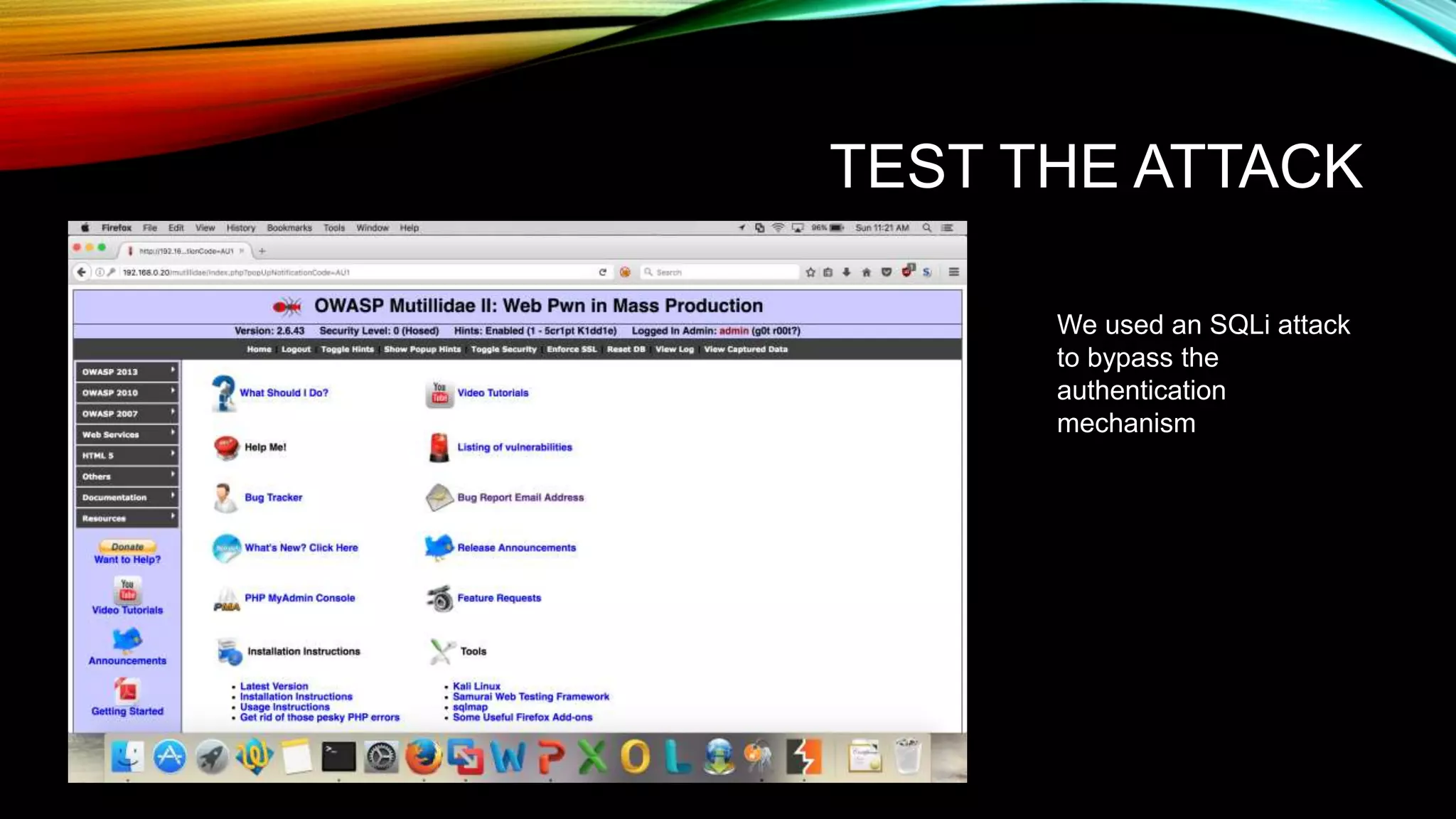
The document discusses the need for application security and secure software development practices. It notes that 60% of internet attacks target web applications, with SQL injection and XSS making up 80% of discovered vulnerabilities. It emphasizes that security needs to be incorporated throughout the entire software development lifecycle, from requirements to testing. Specific secure development practices mentioned include threat modeling, risk assessment using STRIDE, fuzz testing, and the OWASP Mutillidae tool.