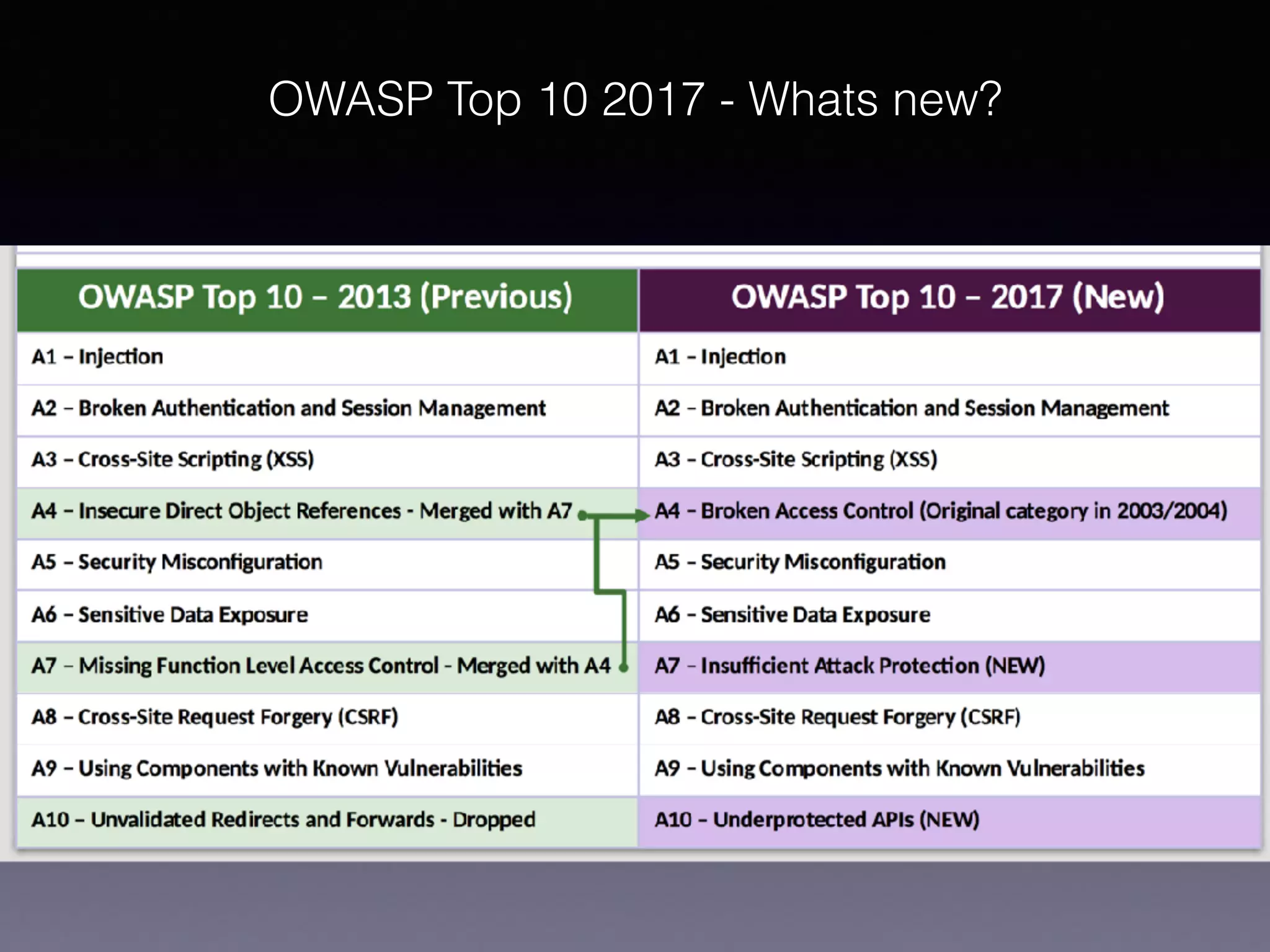
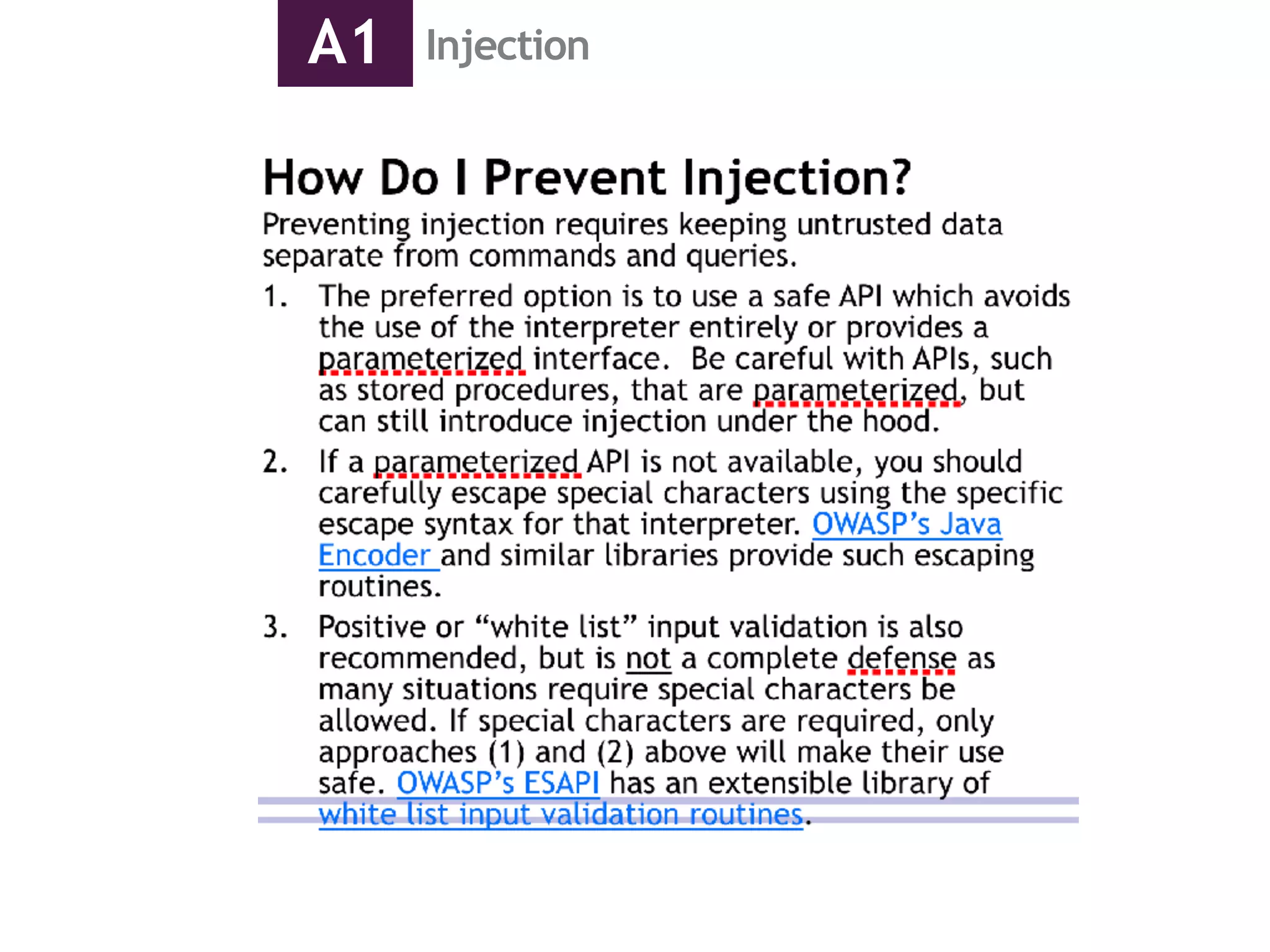
This document discusses application security and the OWASP Top 10 list of vulnerabilities. It covers topics like injection flaws, broken authentication, sensitive data exposure, and denial of service attacks. Application security involves adequately defending against easy-to-find vulnerabilities to achieve Level 1 certification. The OWASP Top 10 lists the most critical web app security risks, including injection, XSS, broken access control, and using components with known vulnerabilities. Denial of service attacks work by consuming limited resources like bandwidth or database connections to prevent legitimate use.