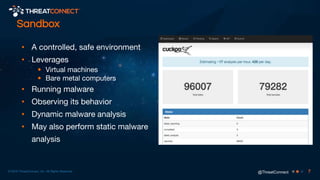
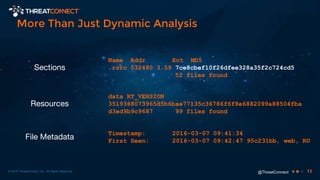
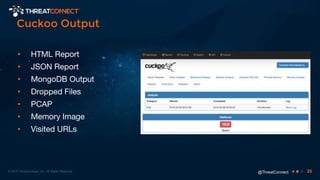
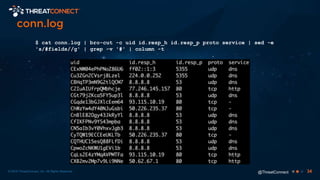
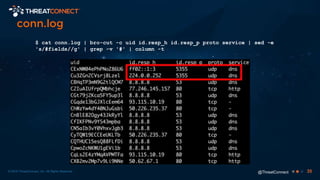
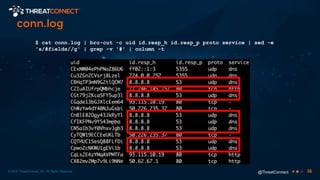
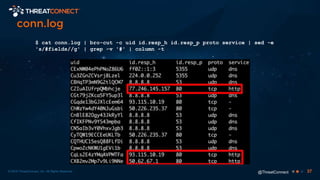
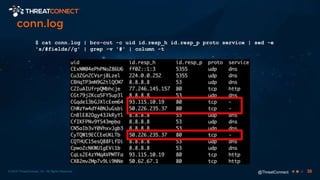
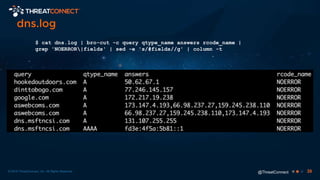
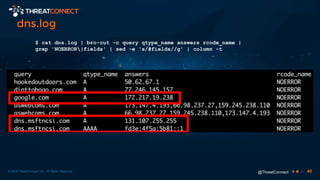
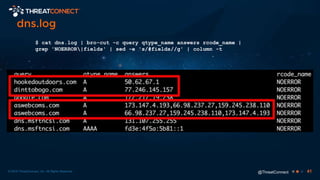
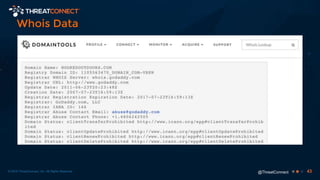
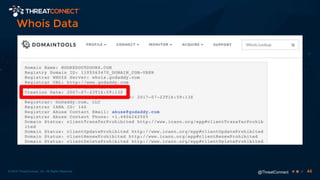
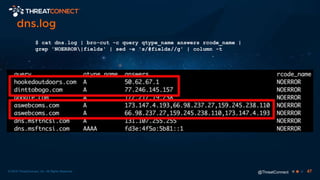
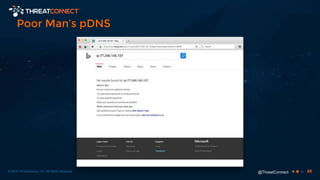
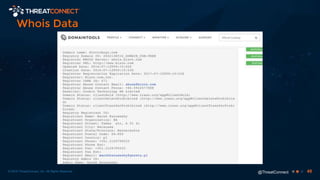
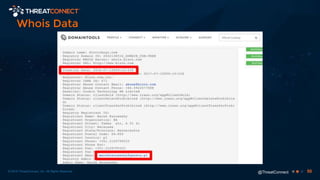
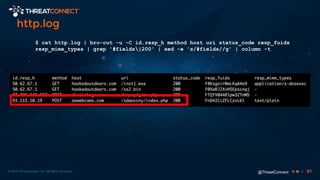
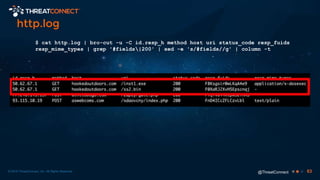
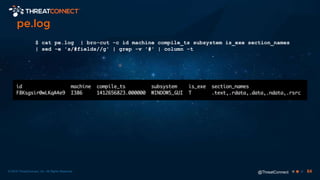
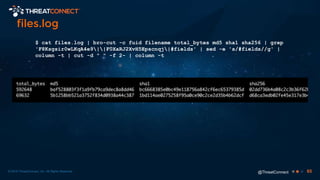
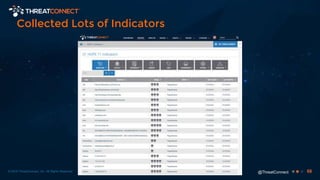
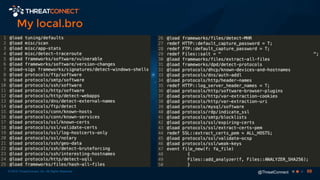
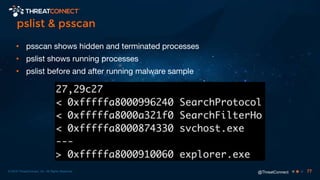
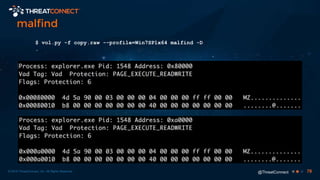
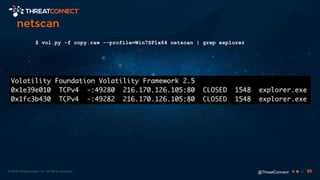
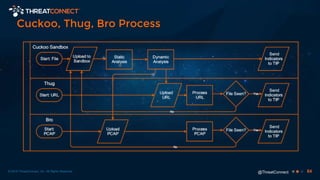
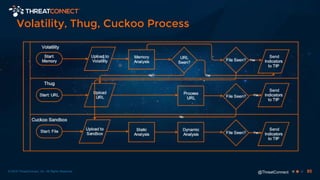
The document outlines the importance of a malware analysis lab, detailing the malware analysis process, tools like Cuckoo sandbox, and techniques for both dynamic and static malware analysis. It covers various components including entry points for malware, user agents for low-interaction honeyclients, and the role of network analysis frameworks like Bro. Additionally, the document highlights the integration of advanced analysis techniques to improve detection and response capabilities against malware.