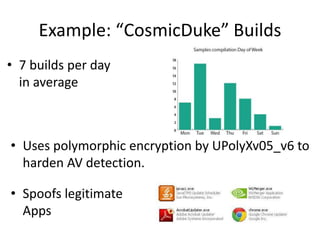
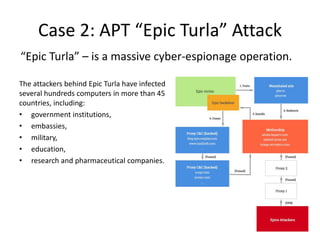
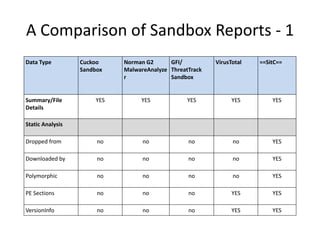
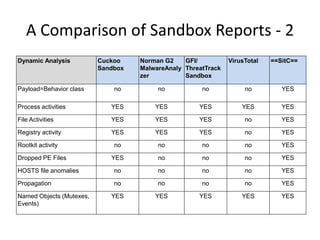
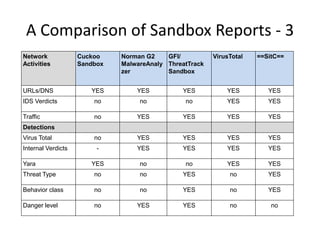
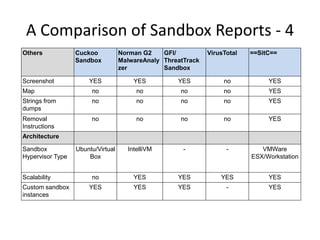
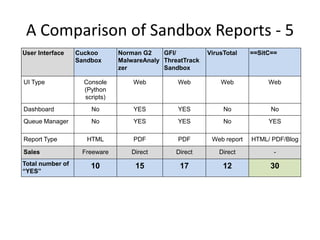
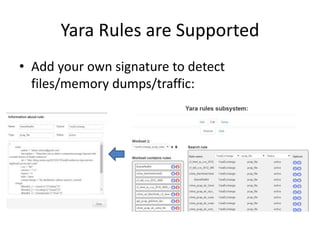
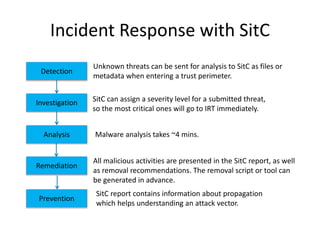
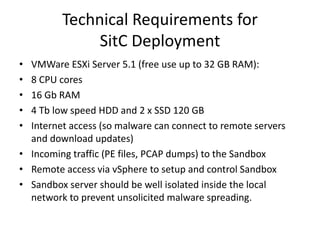
This document discusses using a cloud-based sandbox called SitC for malware analysis. It provides two use case examples of analyzing the CosmicDuke and Epic Turla advanced persistent threats. It then compares the report features of various sandbox solutions and provides sample SitC reports. It outlines the incident response workflow and technical requirements for deploying SitC. The document concludes that SitC could be useful for malware detection and analysis tasks and offers one of the most comprehensive reports currently available.