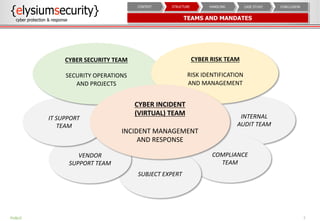
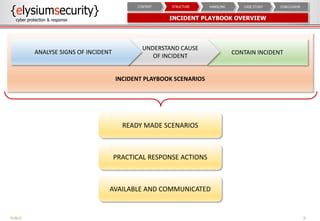
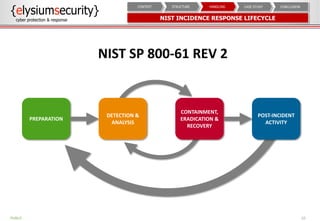
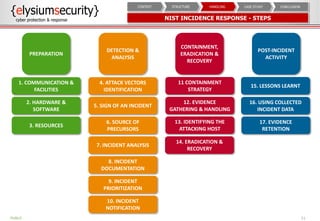
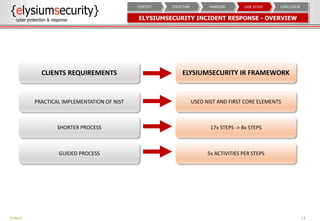
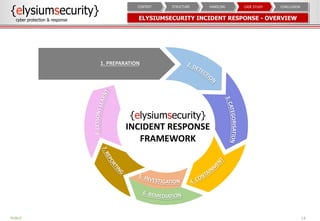
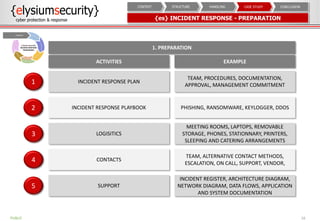
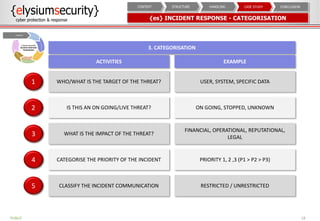
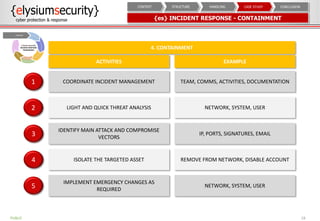
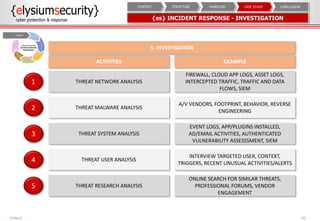
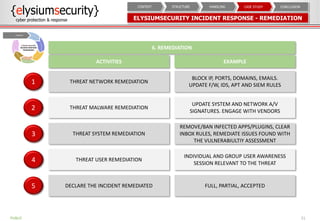
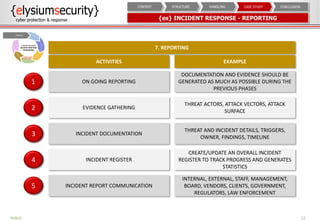
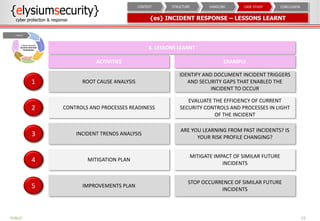
The document provides an overview of an incident response concept and framework. It discusses the benefits of incident response, common incident response structures and lifecycles. It also outlines the key steps in an incident response process including preparation, detection, analysis, containment, eradication, recovery, reporting and lessons learned. Specific approaches and activities at each step are also described for a company's incident response implementation.