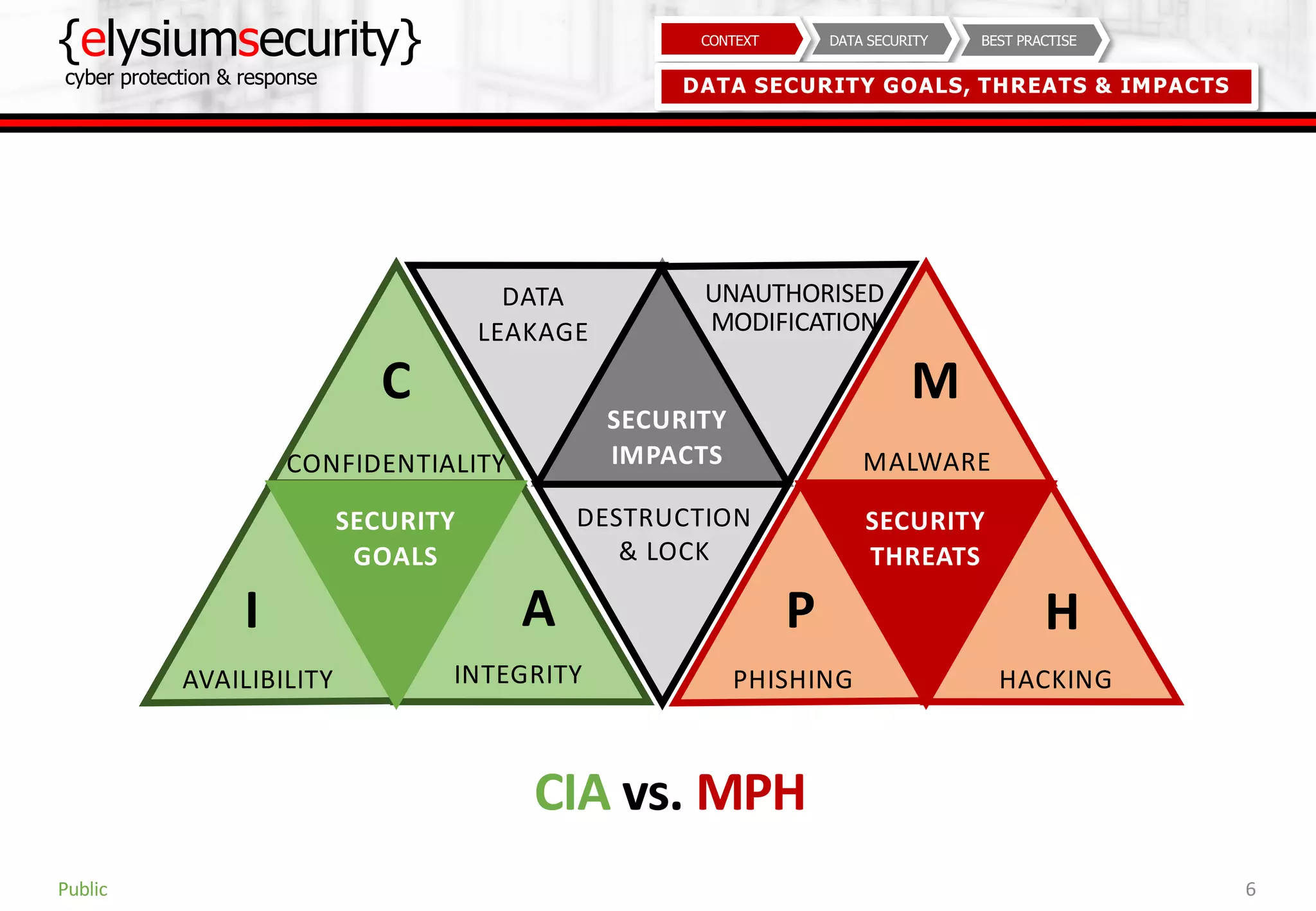
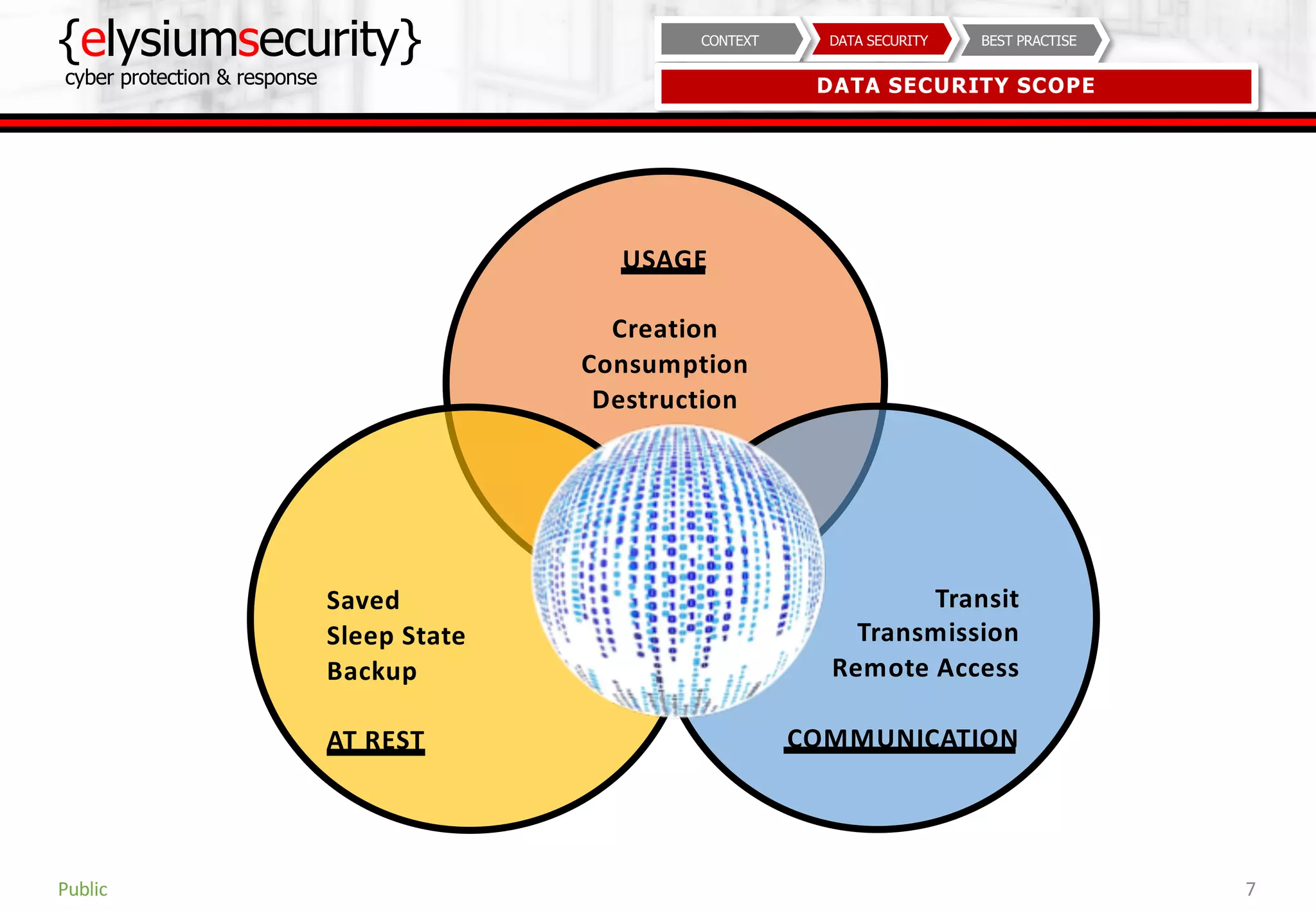
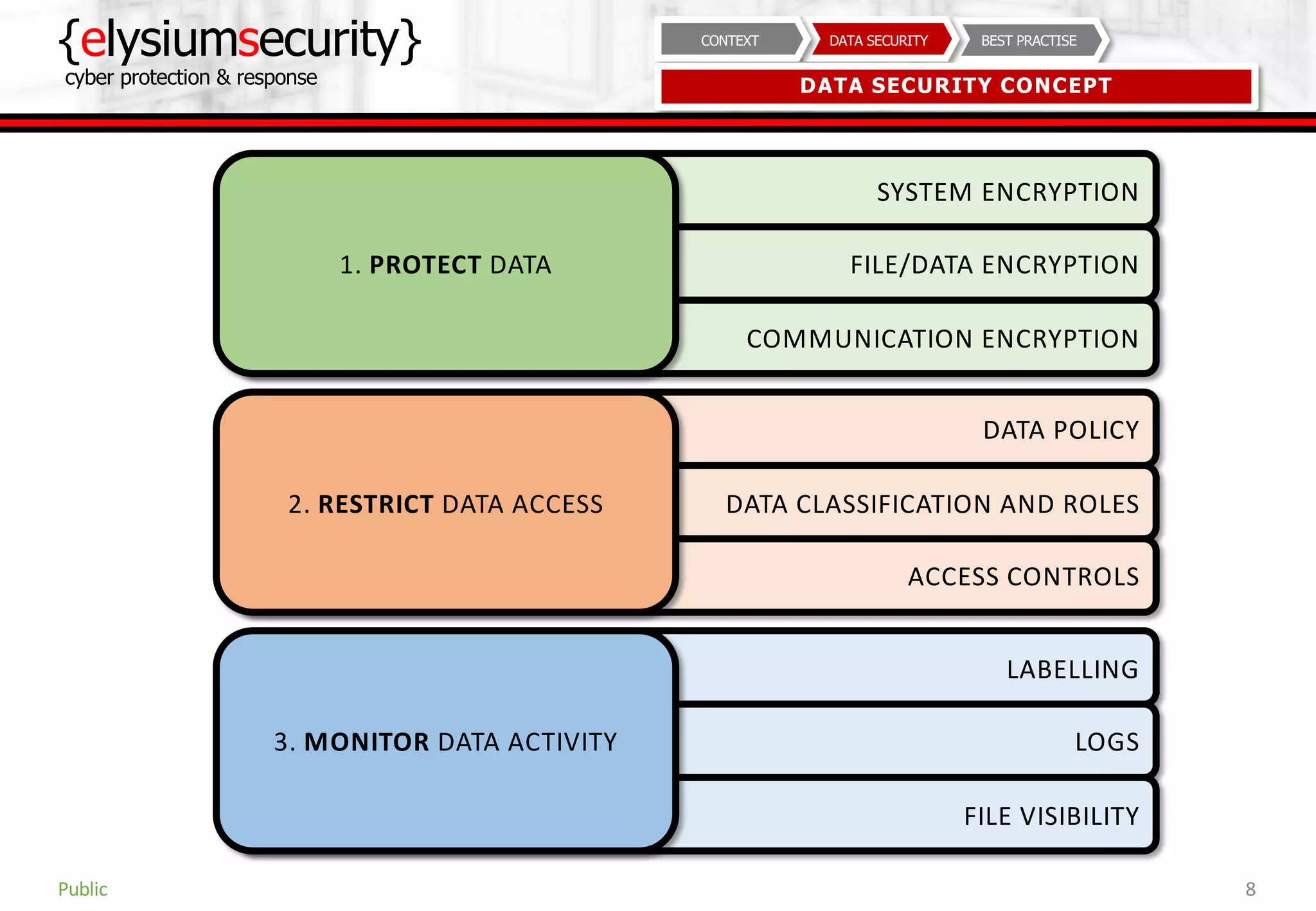
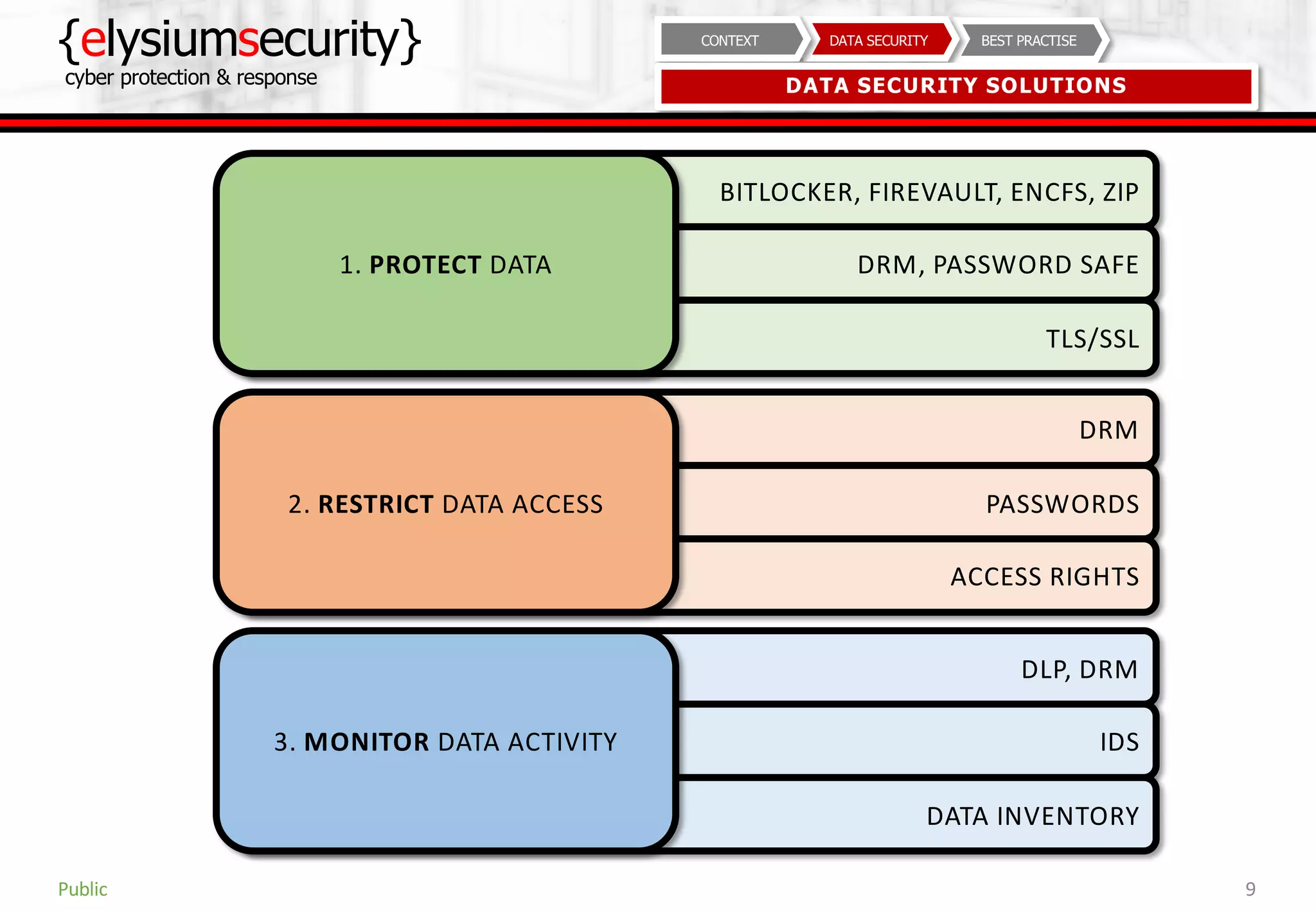
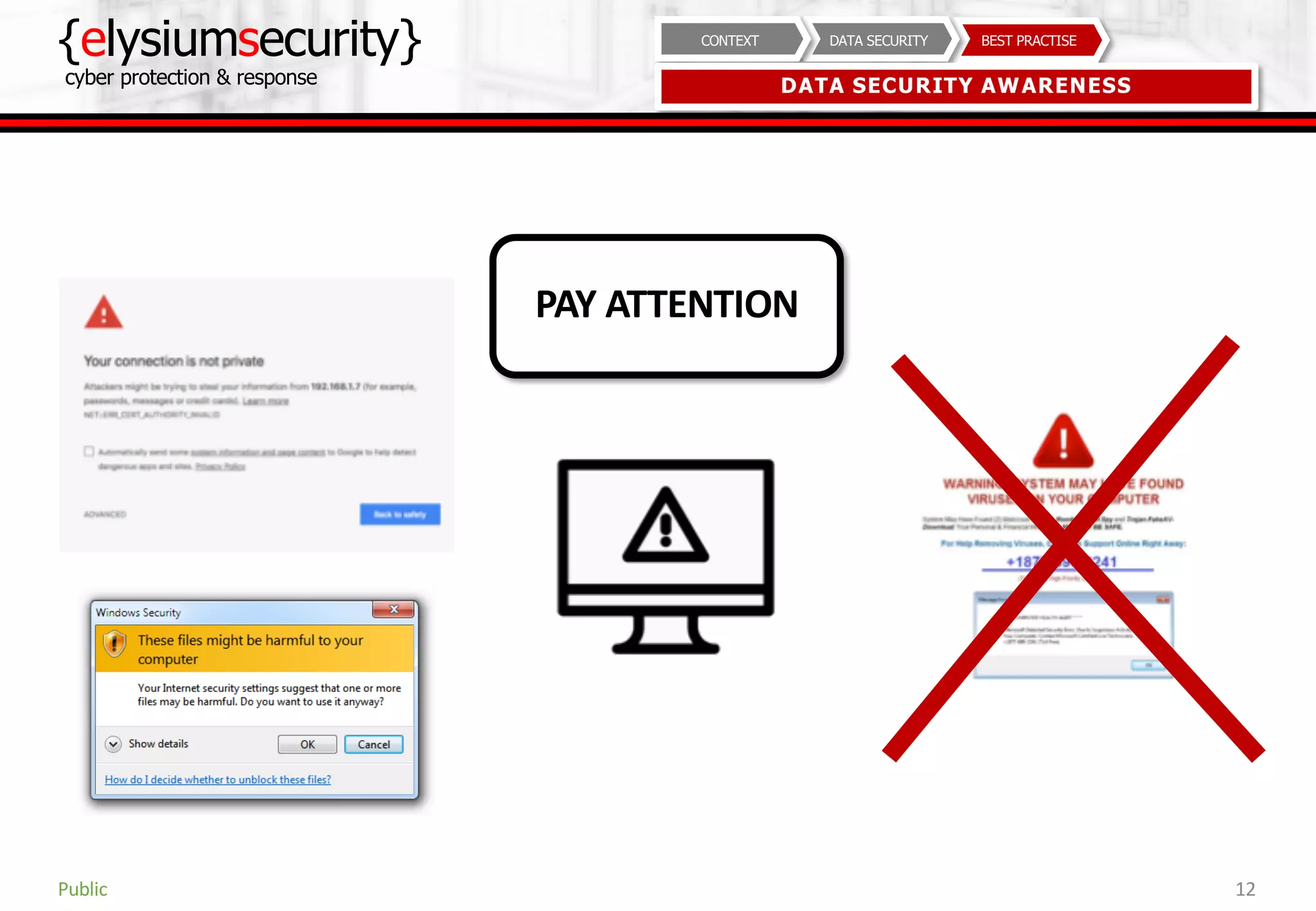
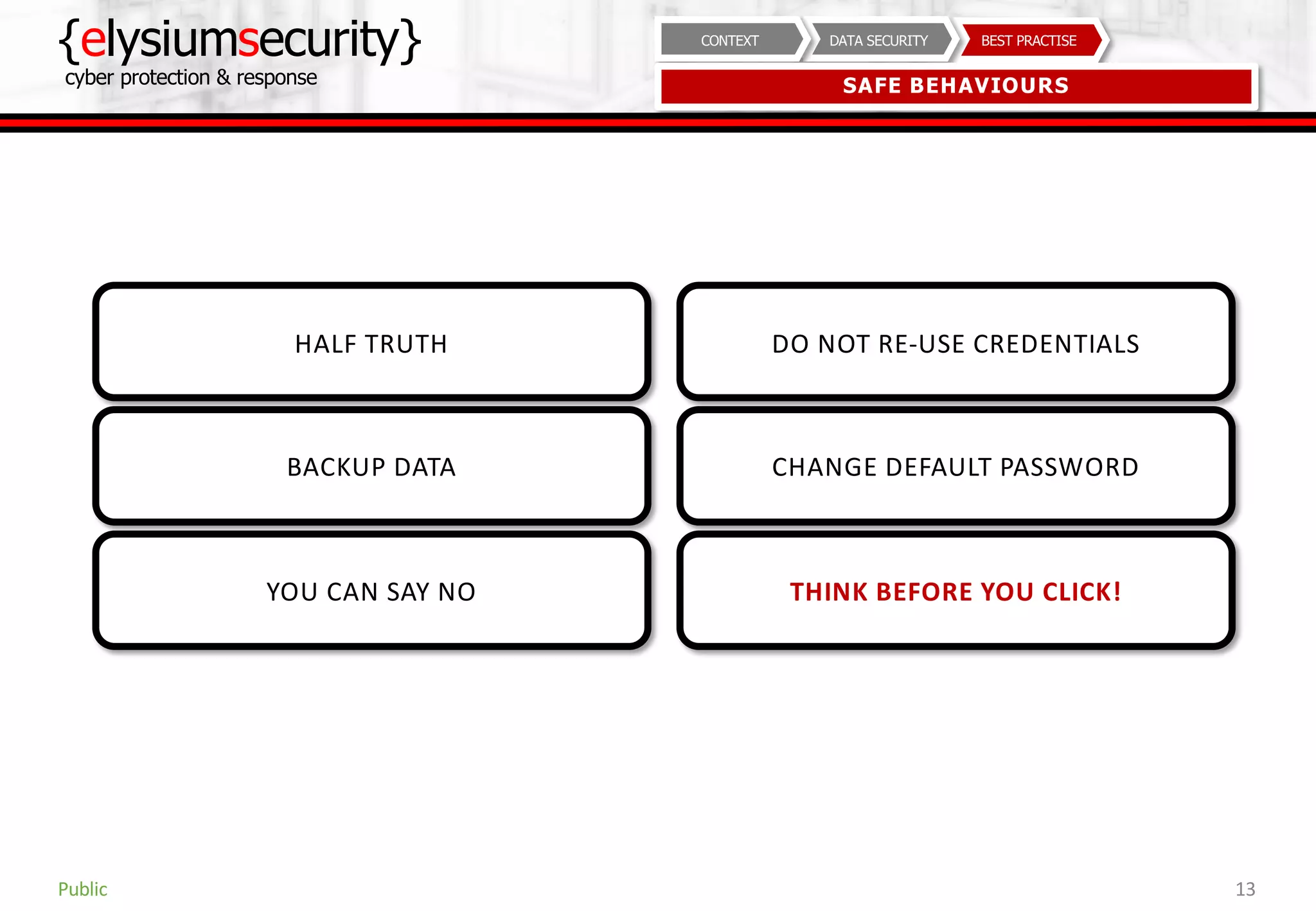
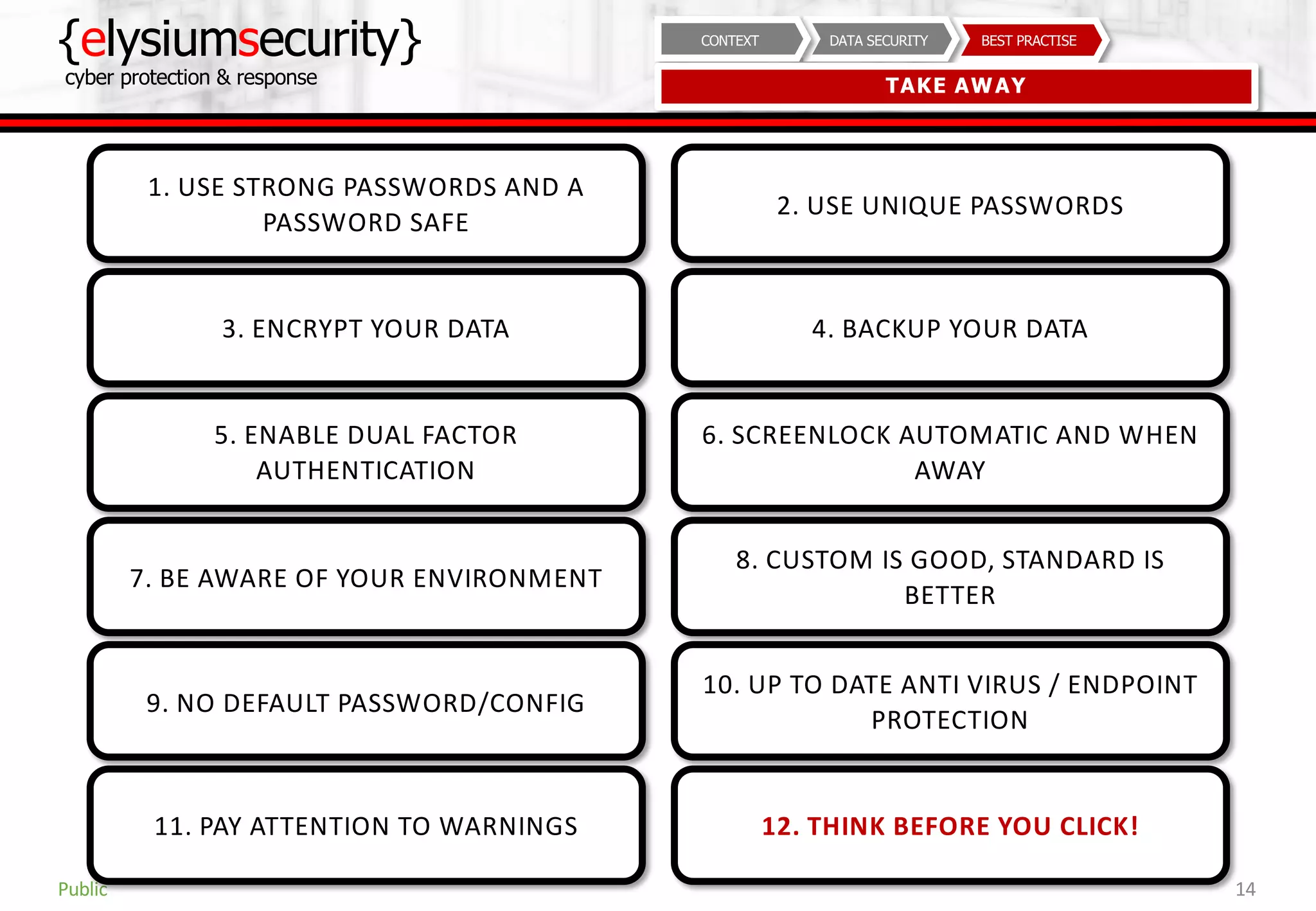
This document provides guidance on data security best practices. It defines data and describes different data types and forms. It outlines key data security goals of confidentiality, integrity and availability that can be threatened by malware, hacking and phishing. The document recommends solutions like encryption, access controls and monitoring to protect data during usage, transit and storage. It stresses the importance of security awareness, safe behaviors like strong unique passwords and backups, and taking basic precautions.