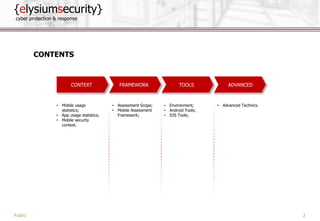
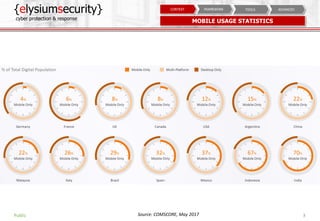
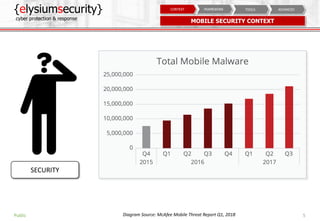
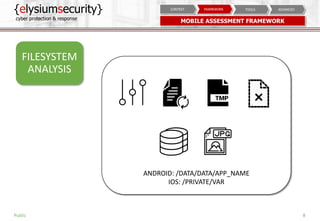
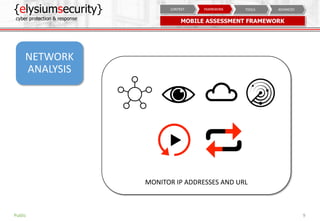
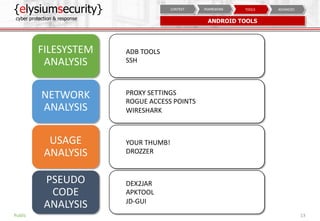
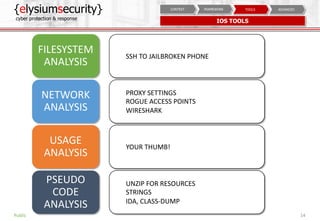
The document is a mobile security assessment report by ElysiumSecurity, detailing its version 1.2a dated 29/08/2018. It covers mobile usage statistics, app usage, security contexts, and advanced assessment methodologies for Android and iOS platforms. ElysiumSecurity aims to assist organizations in identifying vulnerabilities, implementing risk remediation, and enhancing overall cyber security responses.