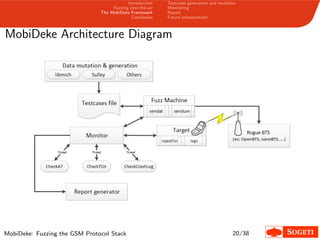
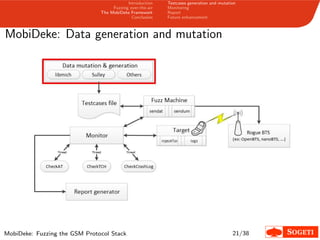
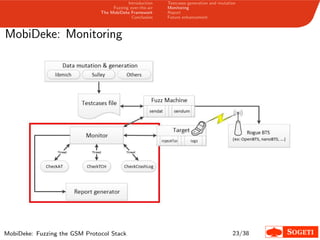
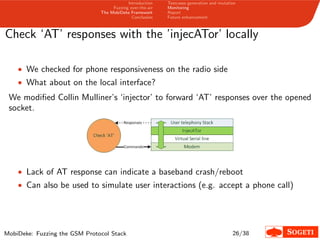
1. The document describes a framework called MobiDeke that was created to fuzz the GSM protocol stack over-the-air by generating and mutating malformed GSM messages and monitoring the target's behavior for crashes or errors.
2. MobiDeke addresses limitations with existing fuzzing methods by automating the generation, mutation, transmission and monitoring processes.
3. The key components of MobiDeke are modules for generating and mutating GSM messages, transmitting payloads over-the-air via a software-defined radio, and monitoring the target phone and base station for crashes or abnormal behavior.