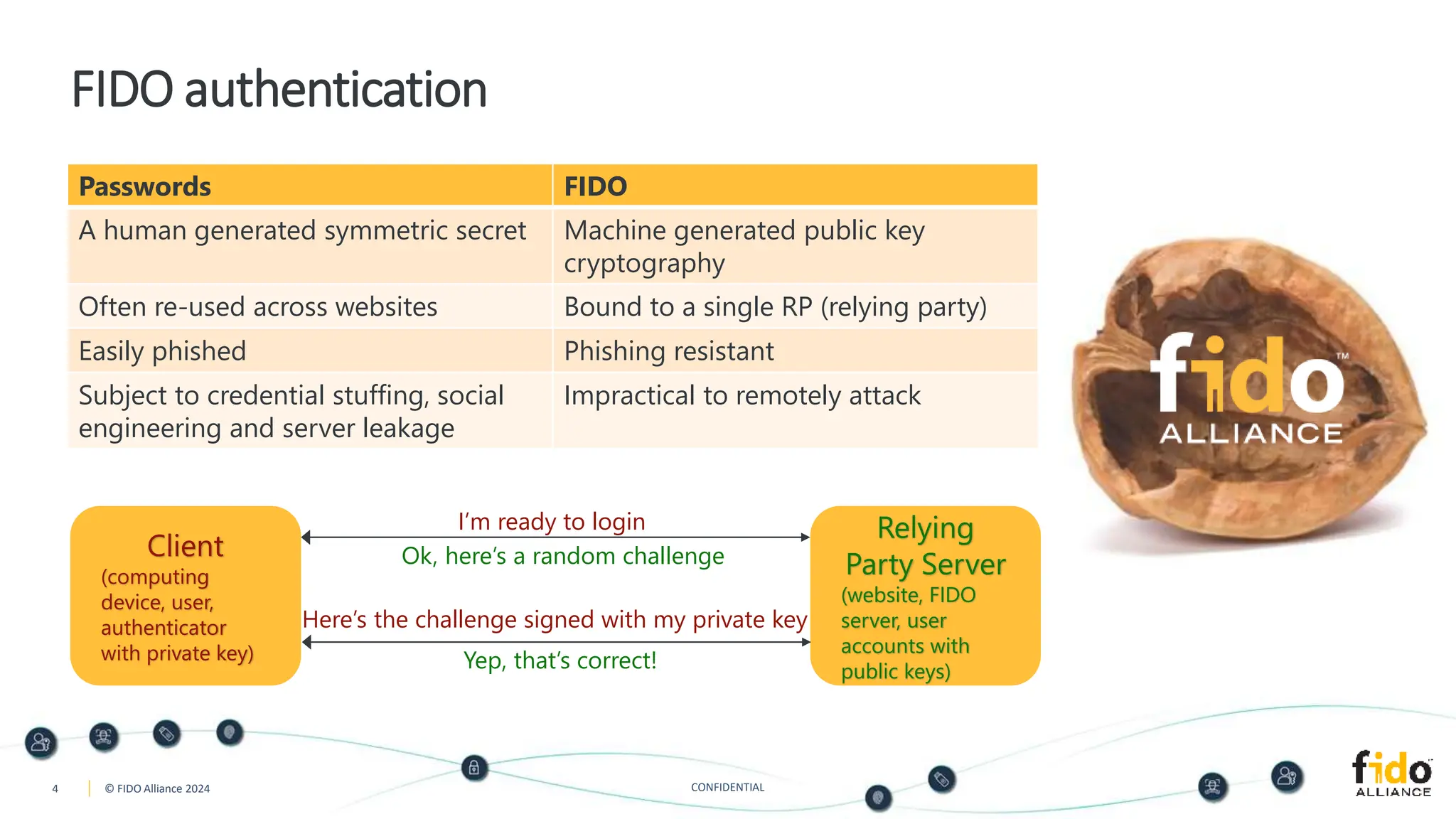
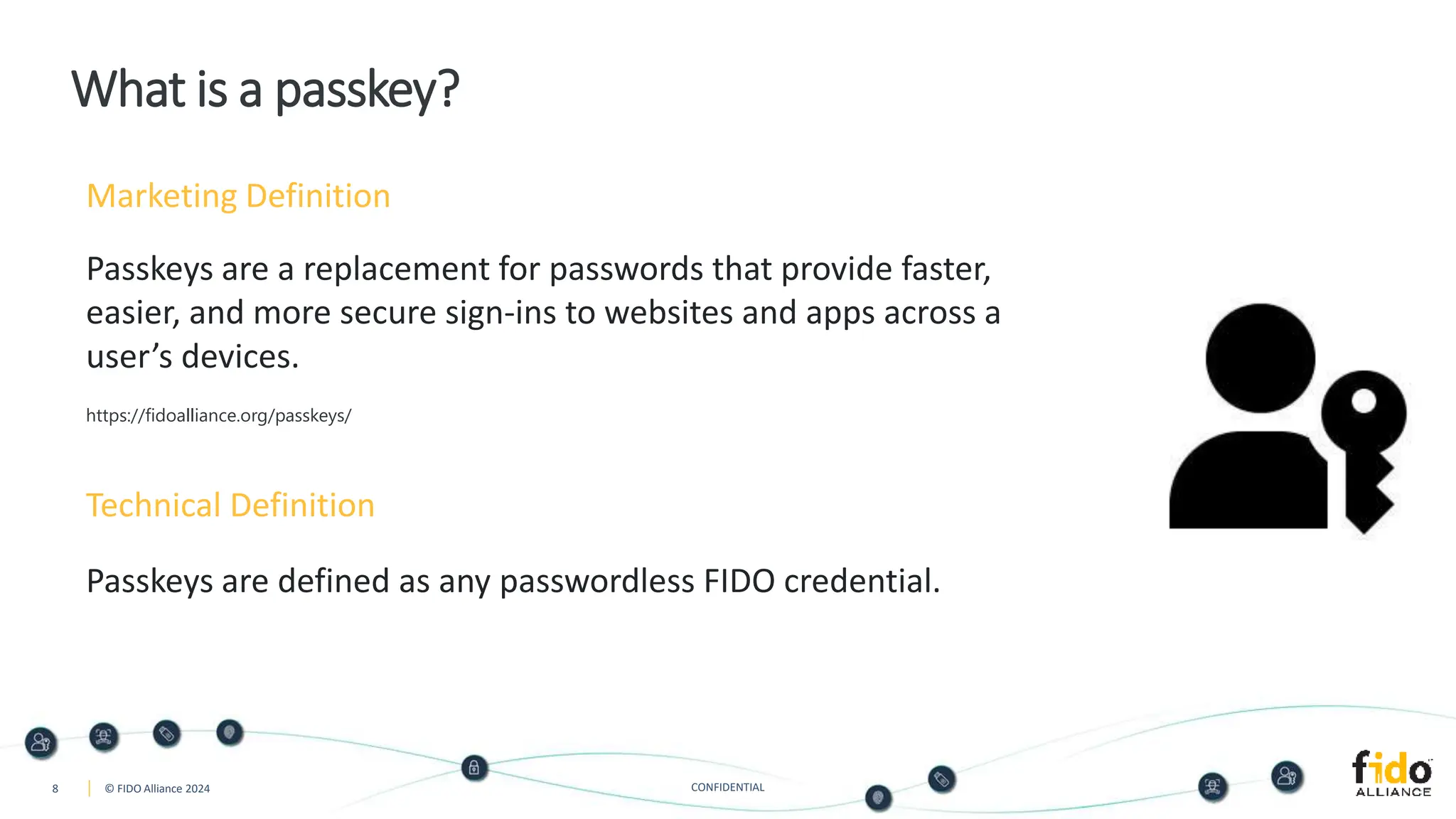
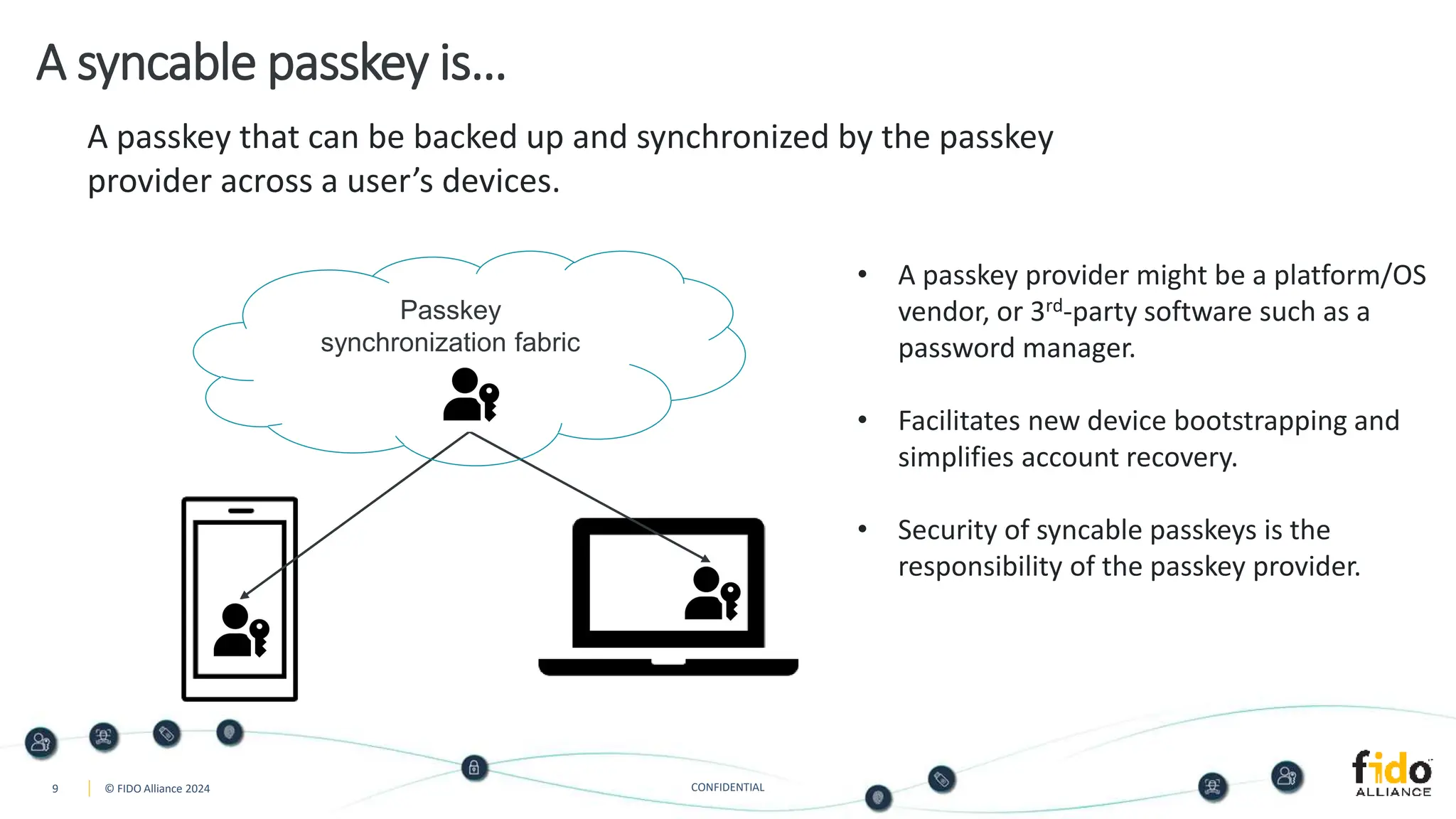
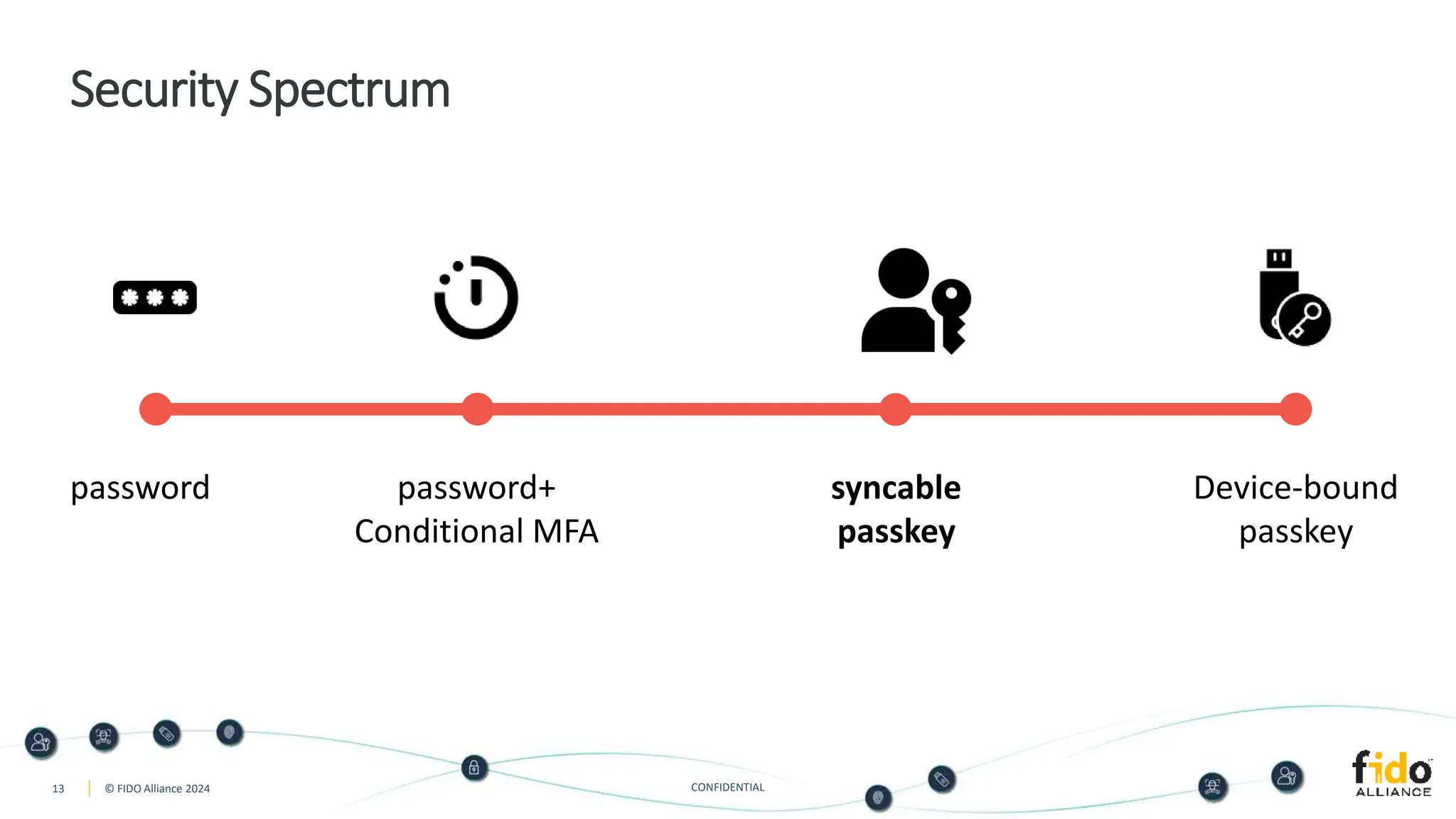
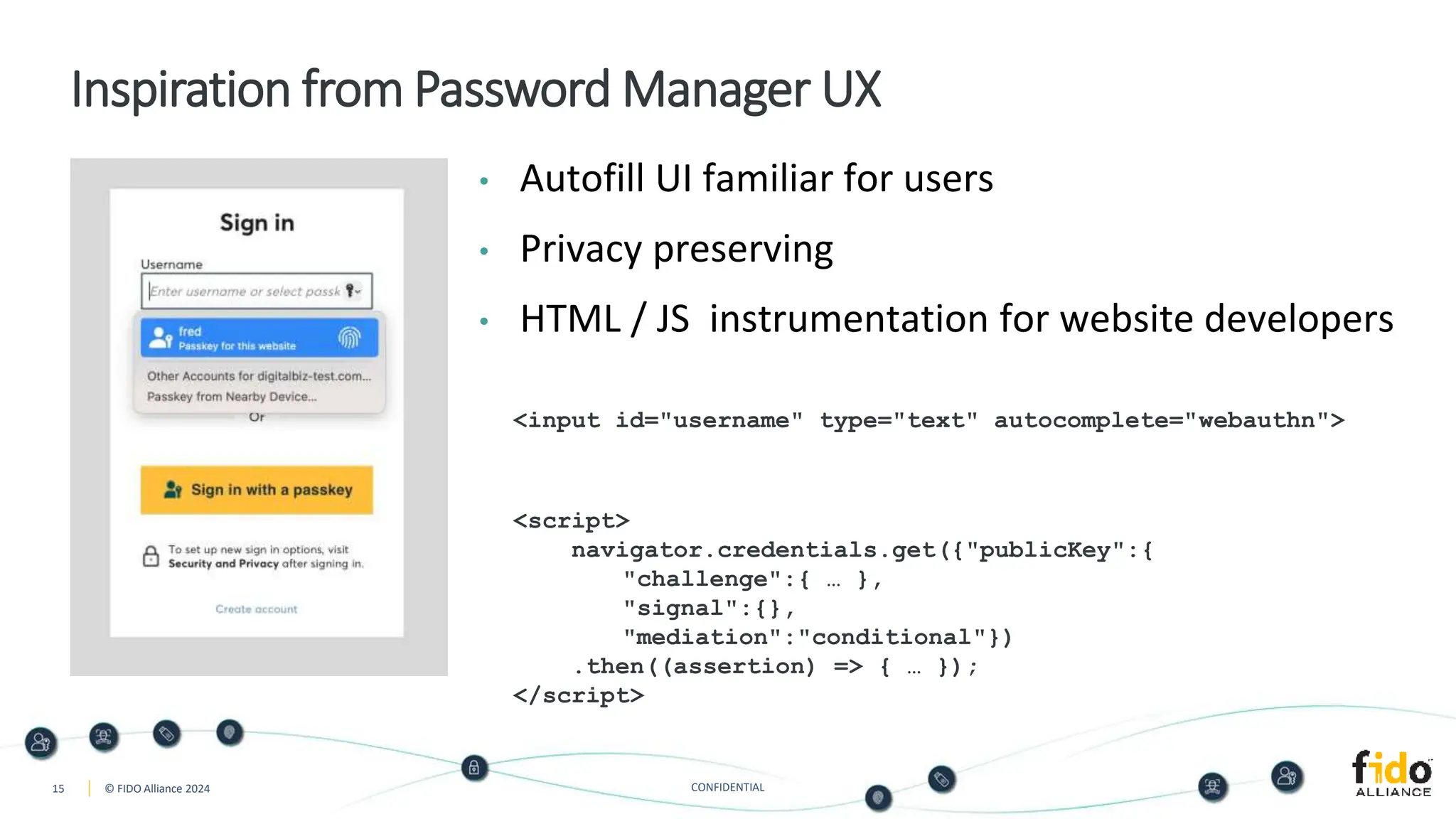
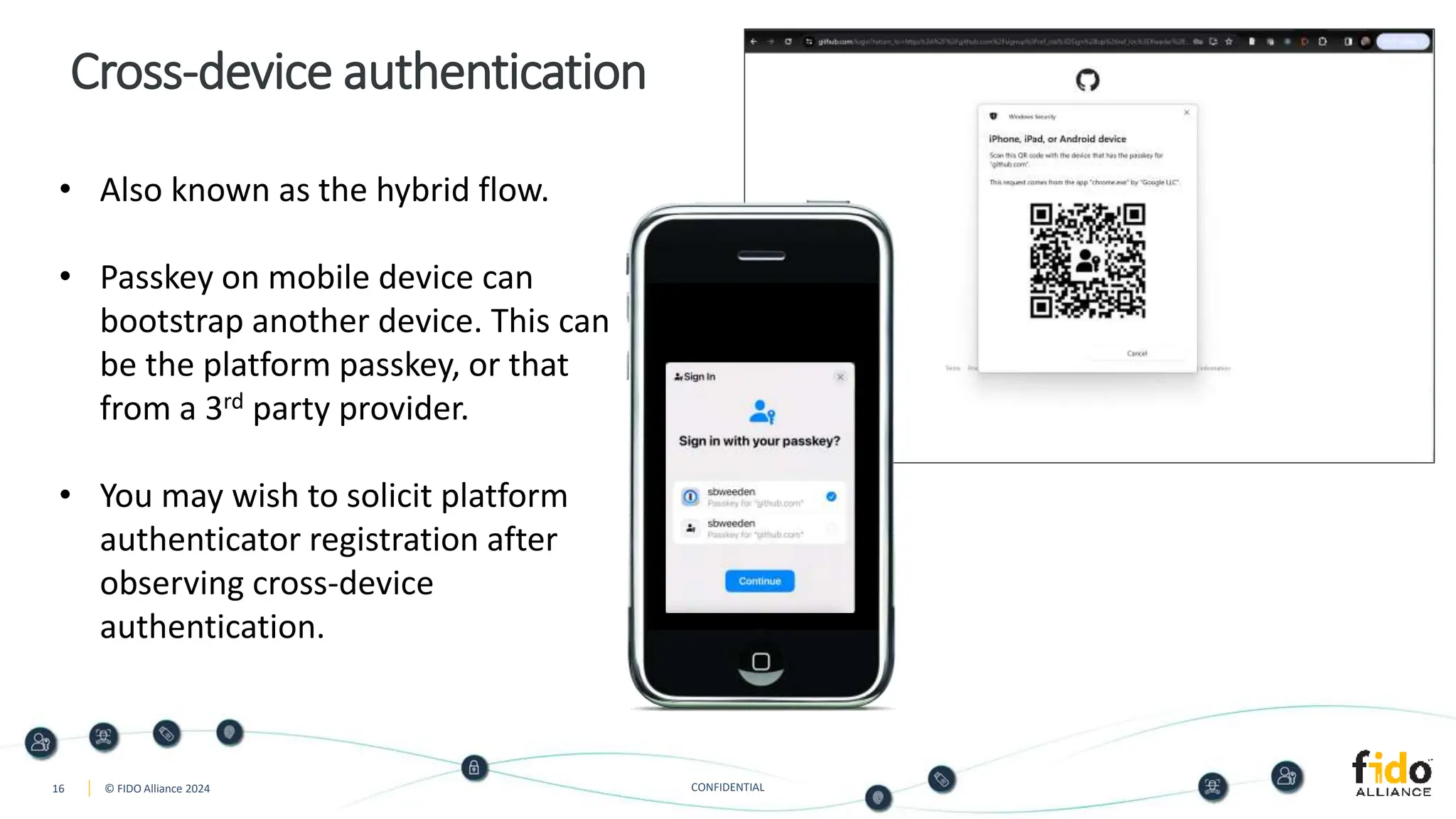
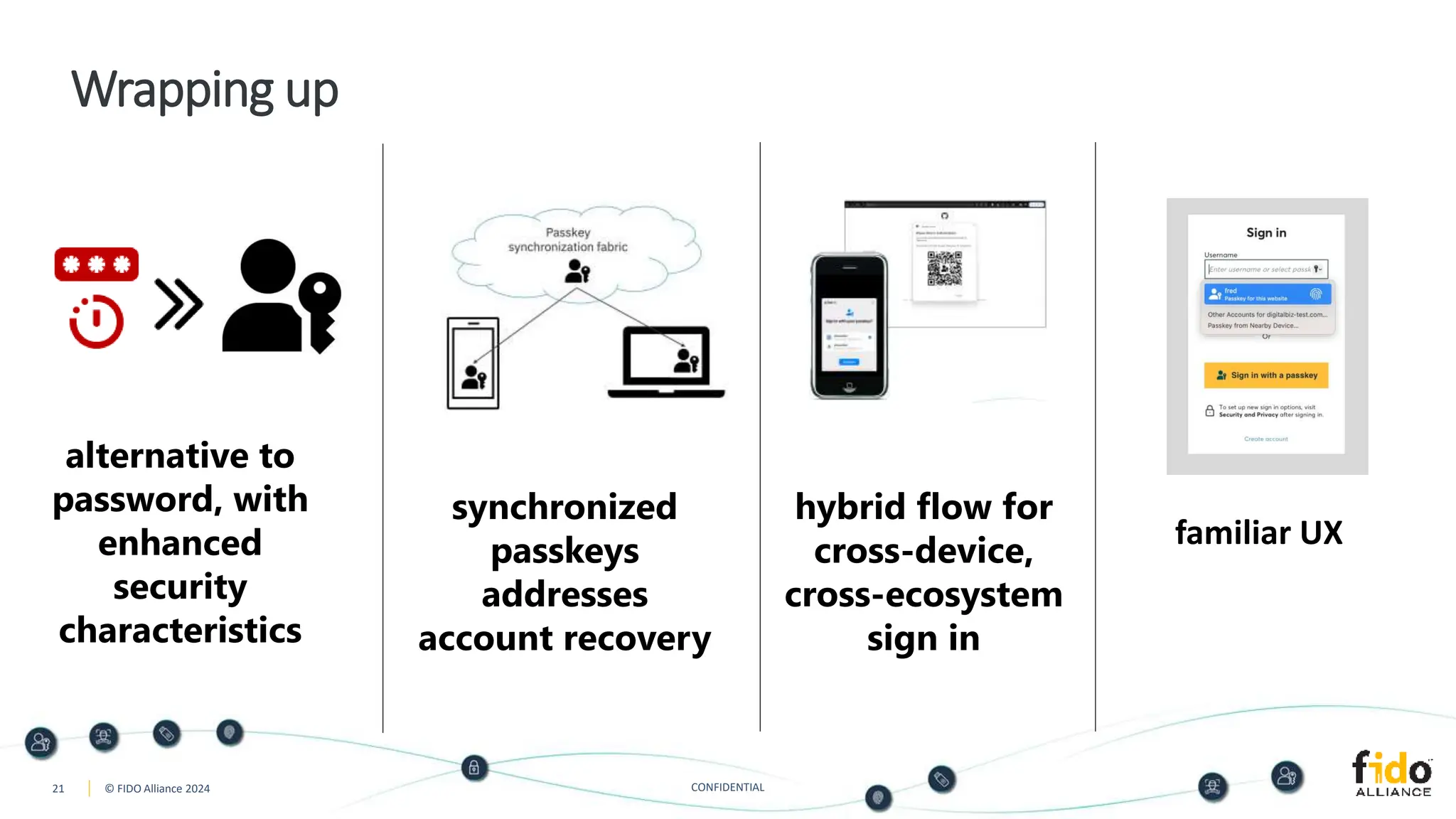
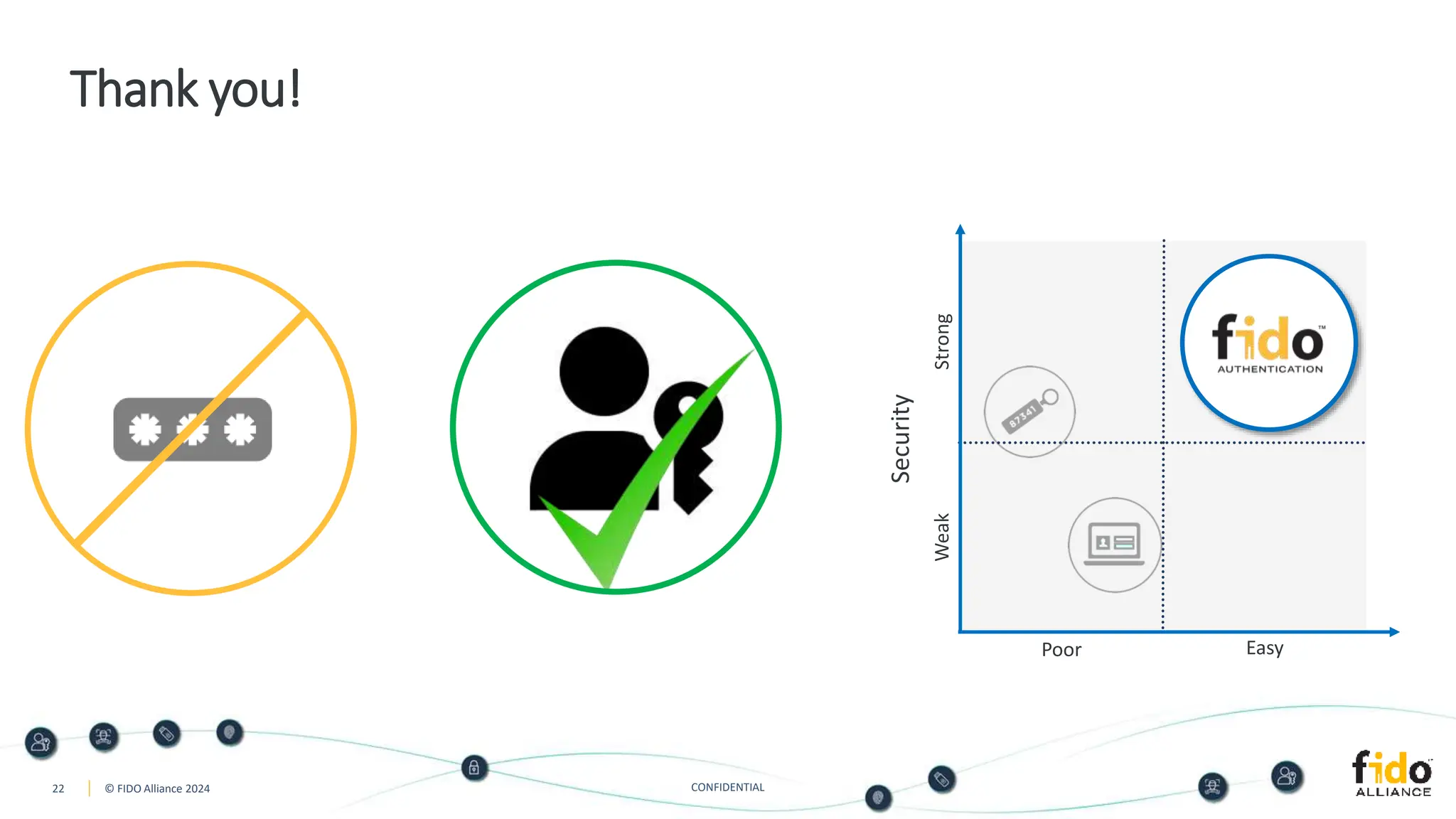
The document presents an overview of FIDO authentication and the concept of passkeys as a secure alternative to passwords for sign-ins across devices. It defines passkeys as passwordless FIDO credentials that enable faster and more secure access while outlining their synchronization capabilities for easier account recovery. The content also emphasizes a user-friendly experience inspired by password managers and discusses cross-device and cross-platform authentication methods.