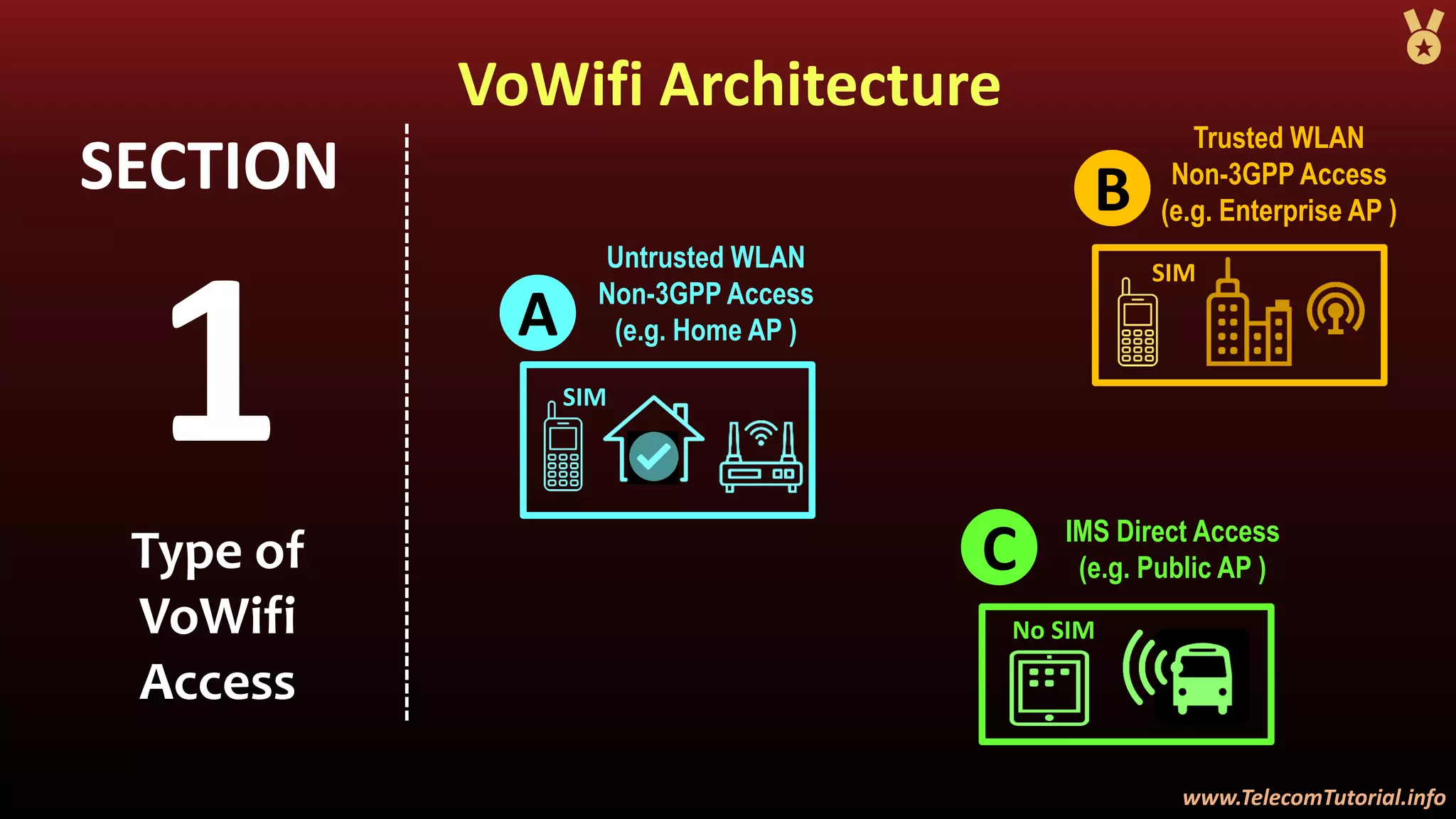
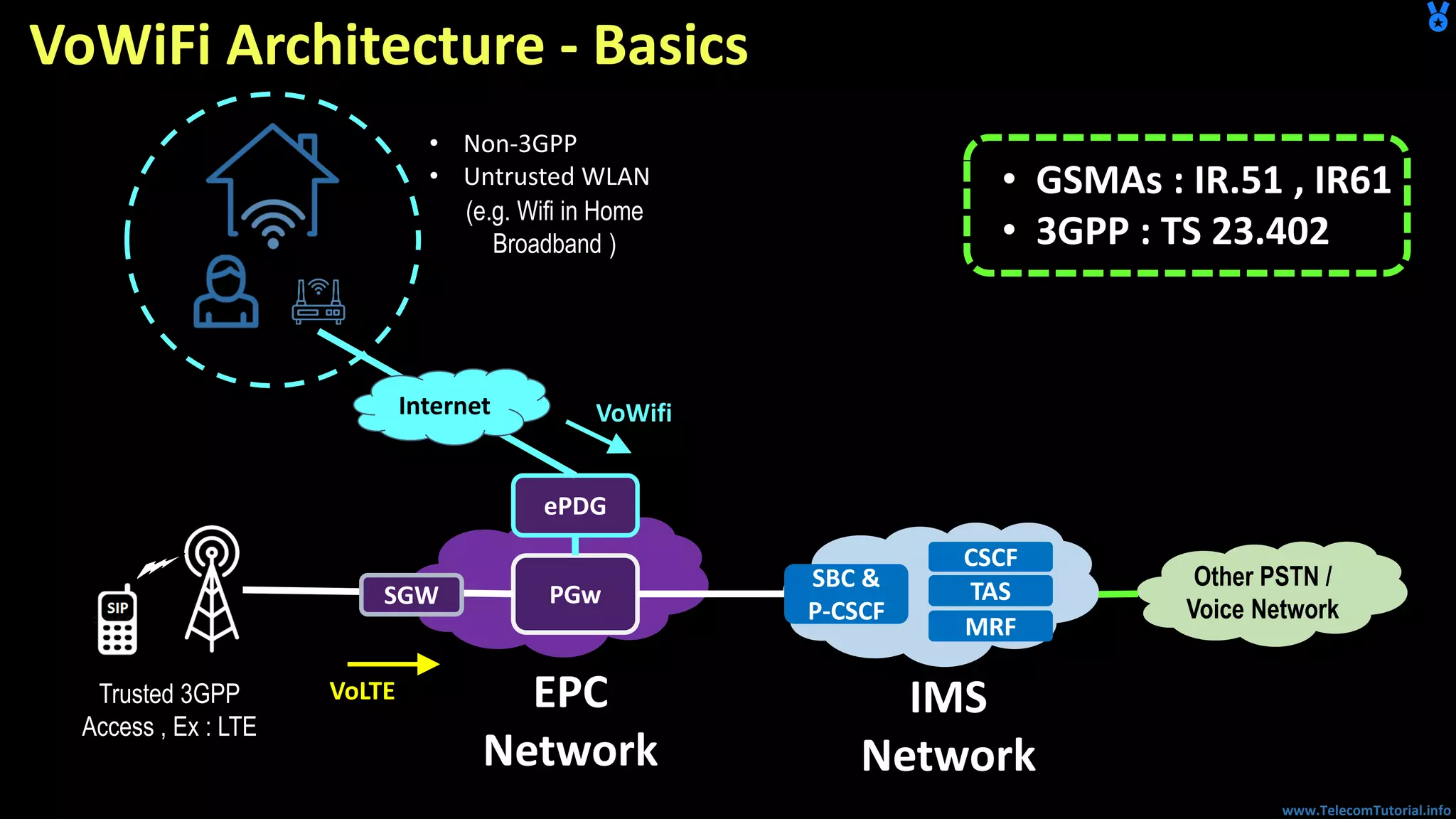
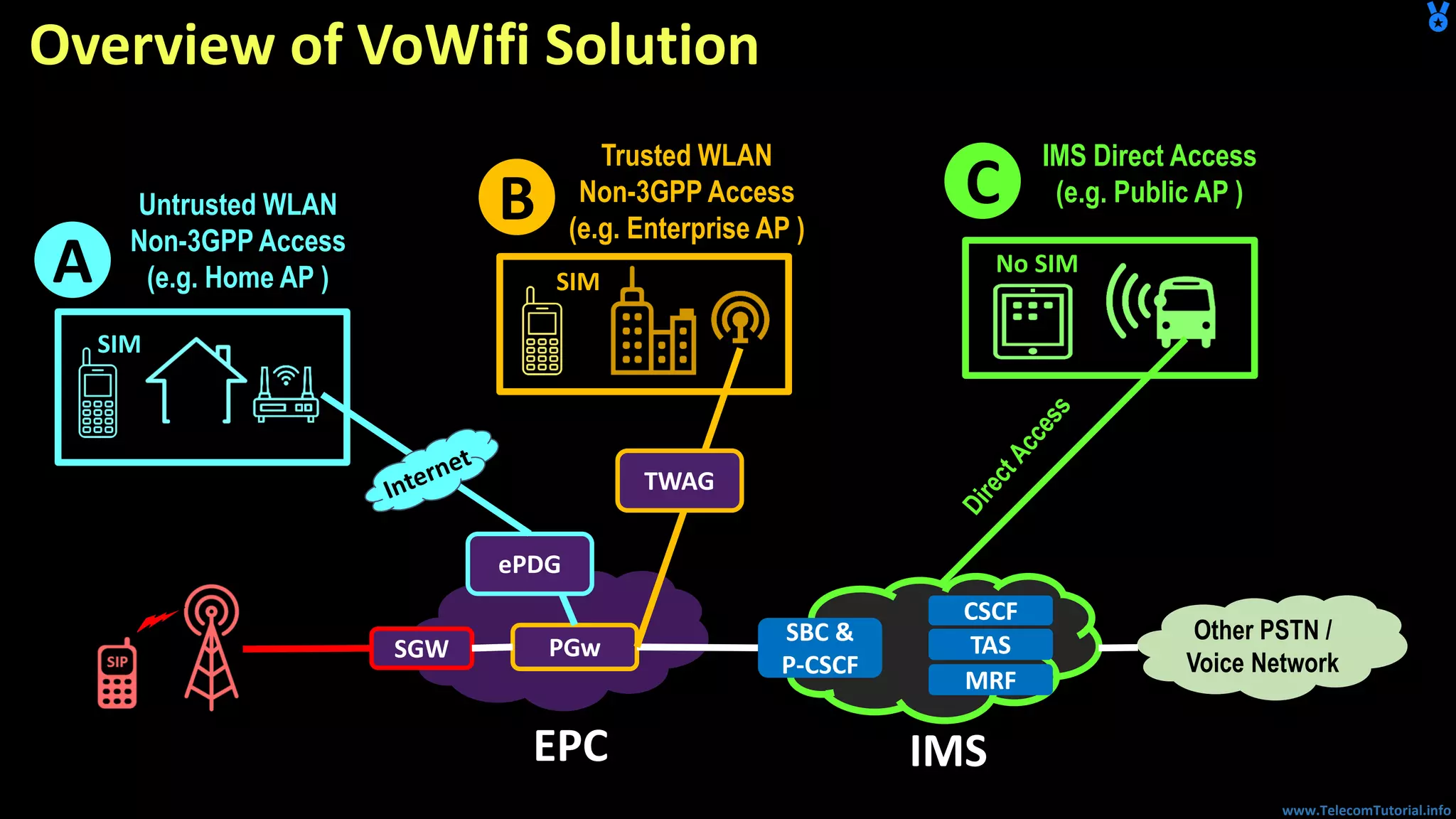
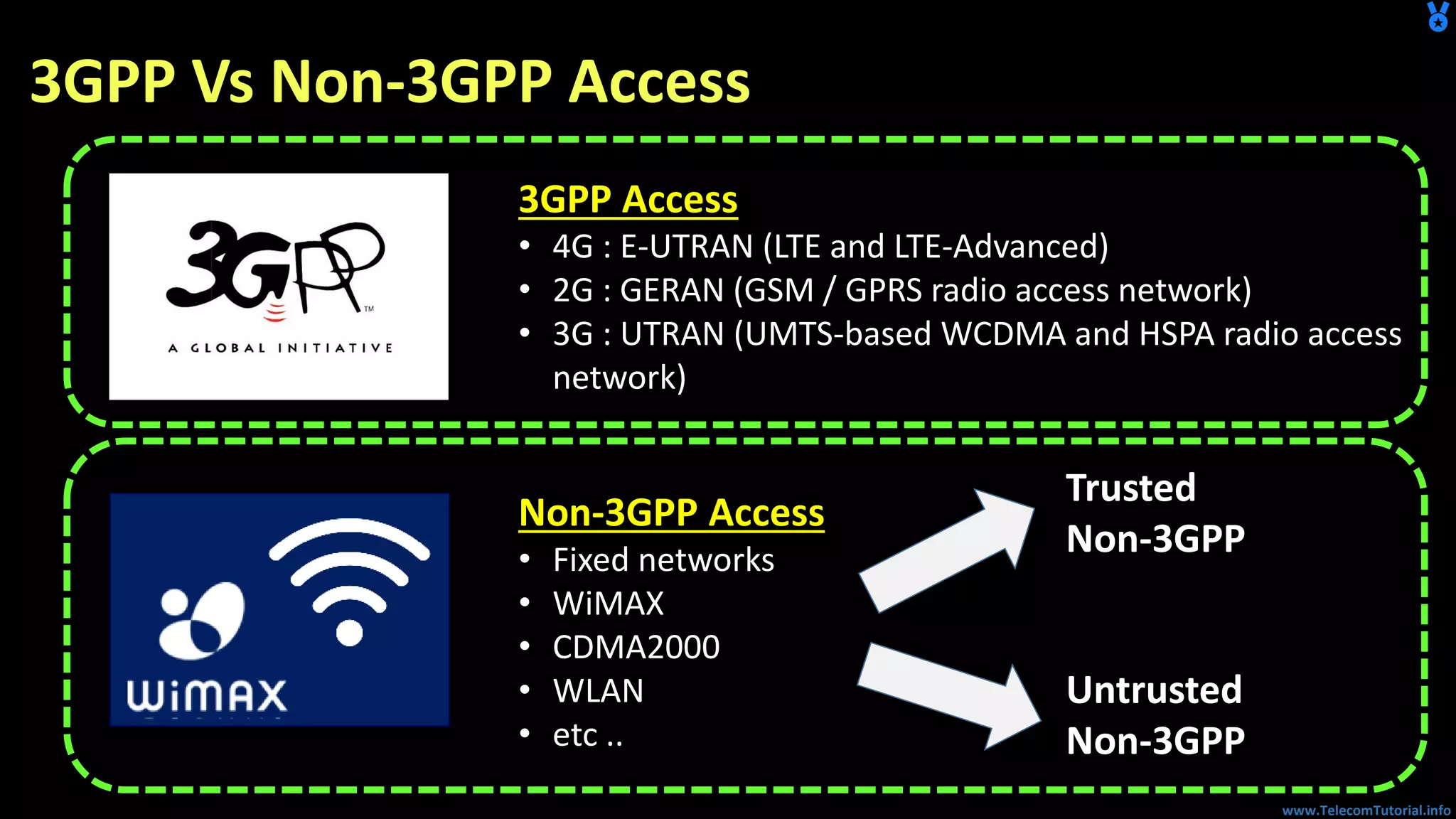
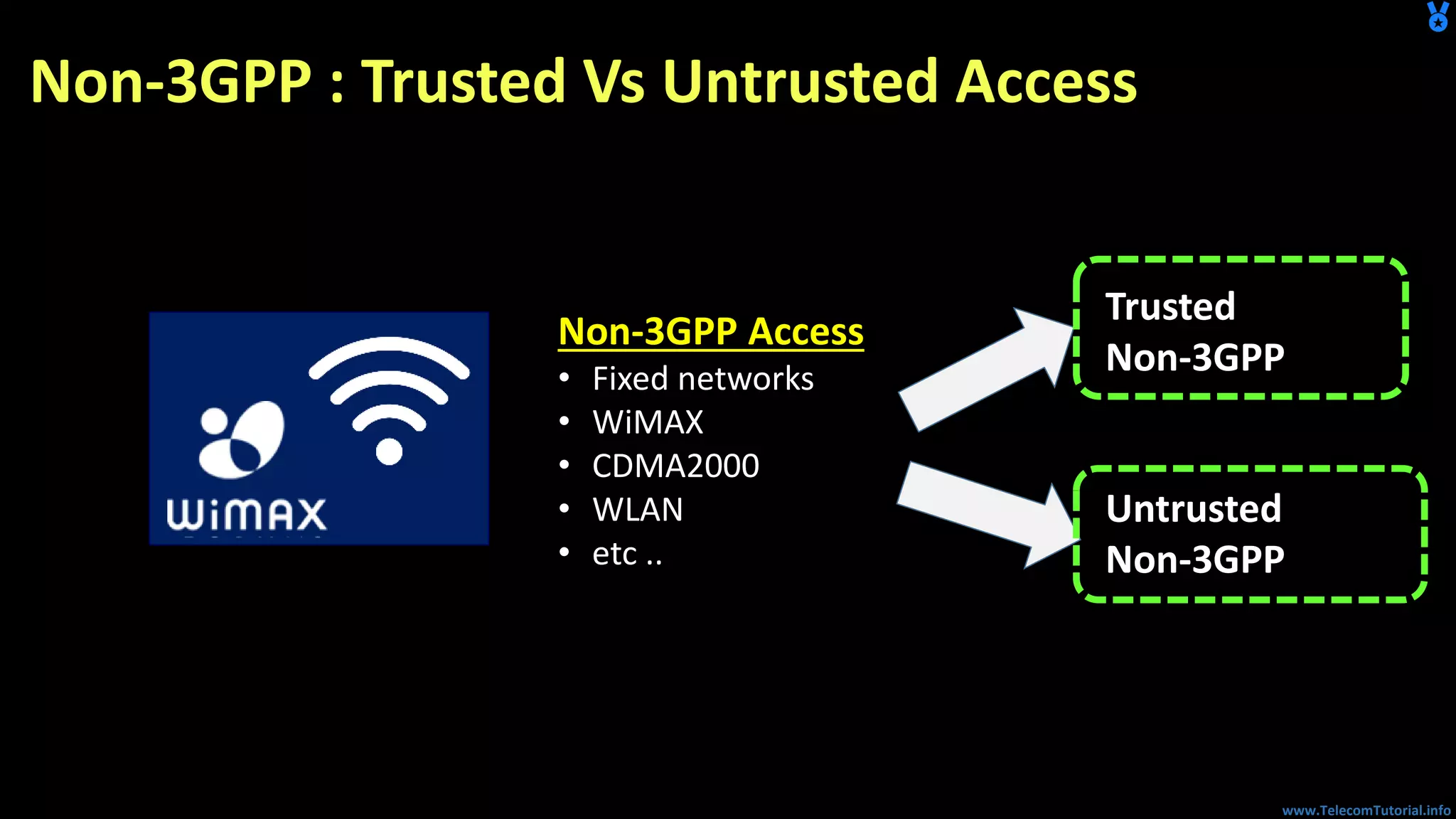
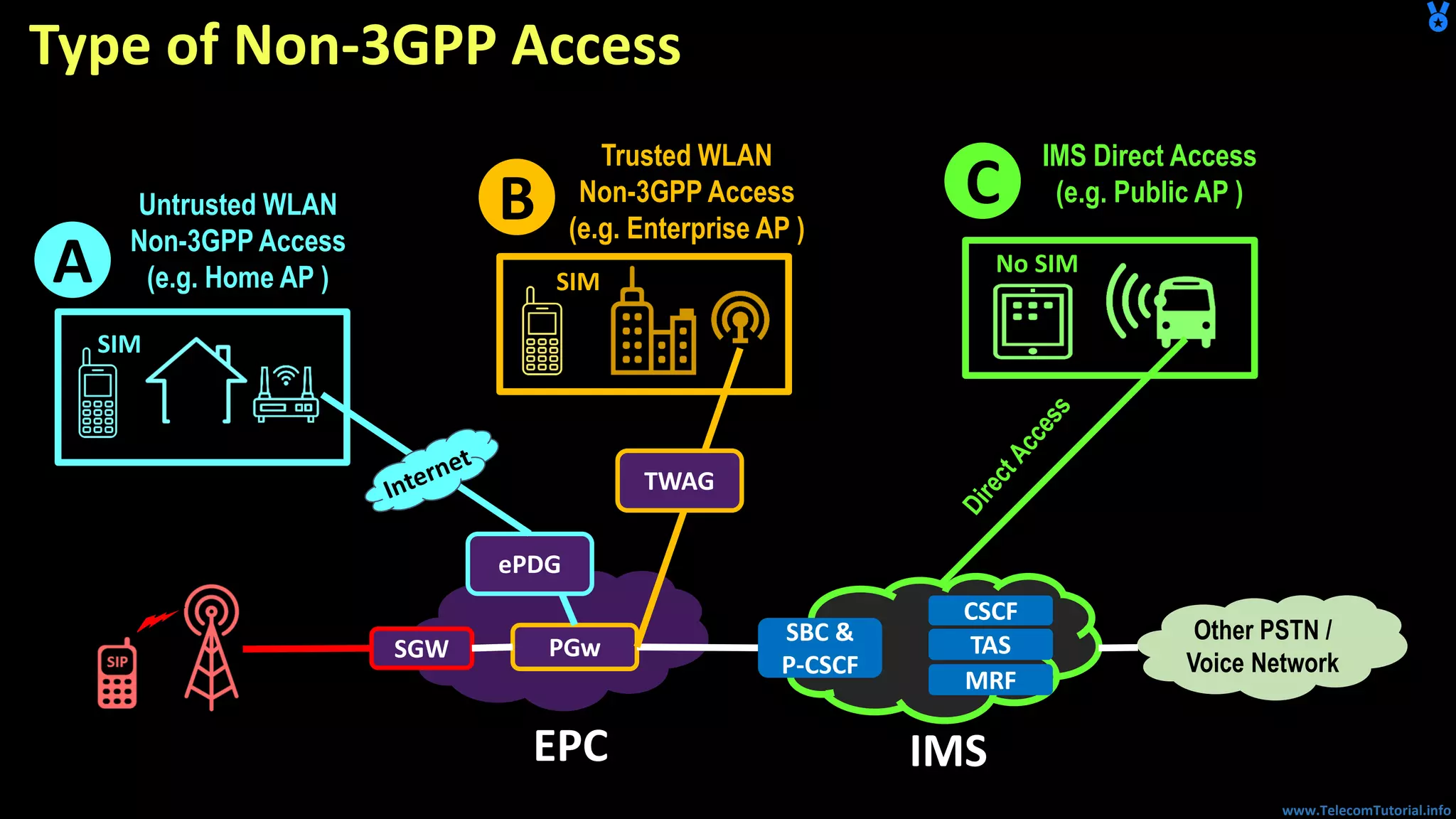
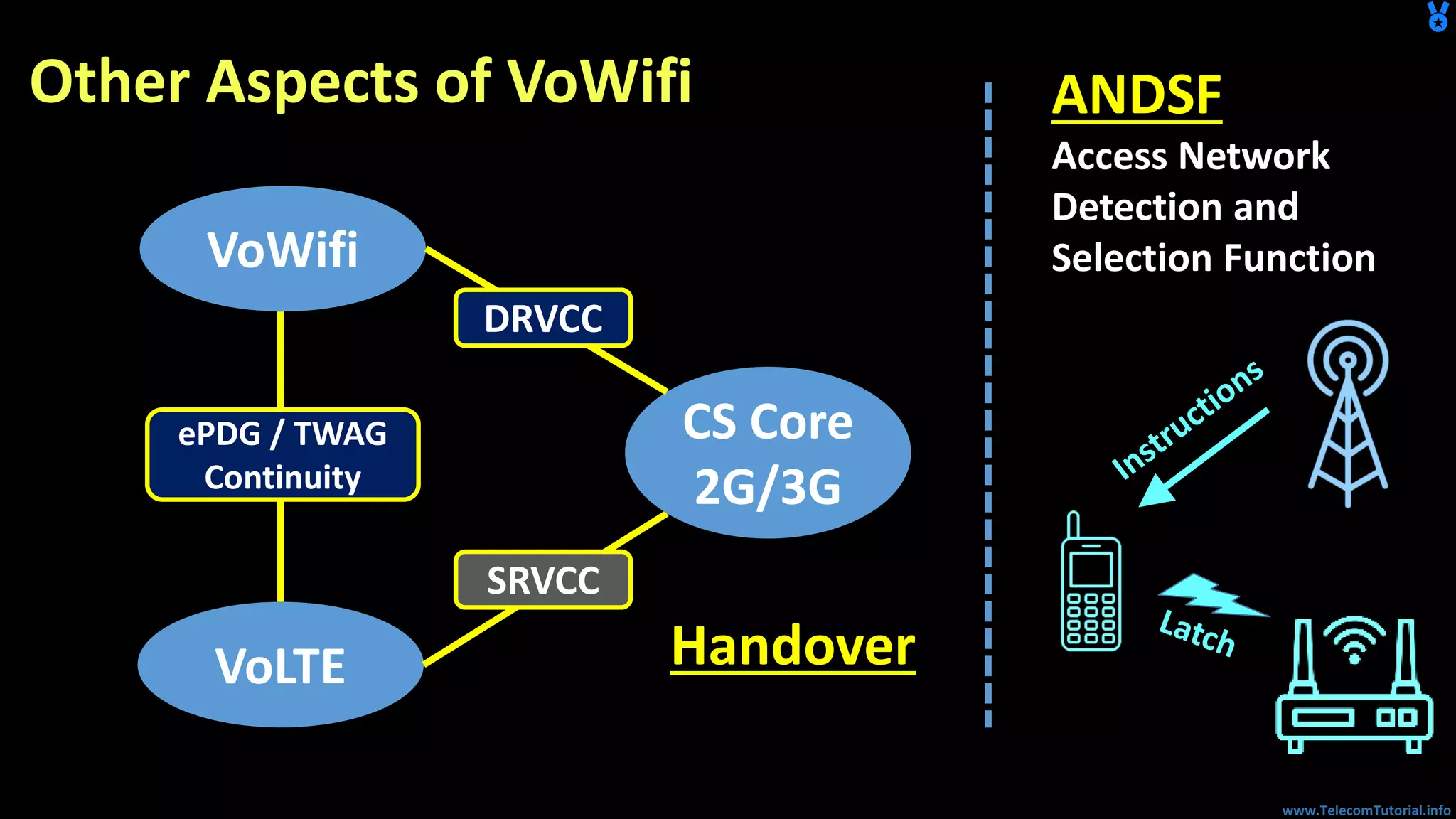
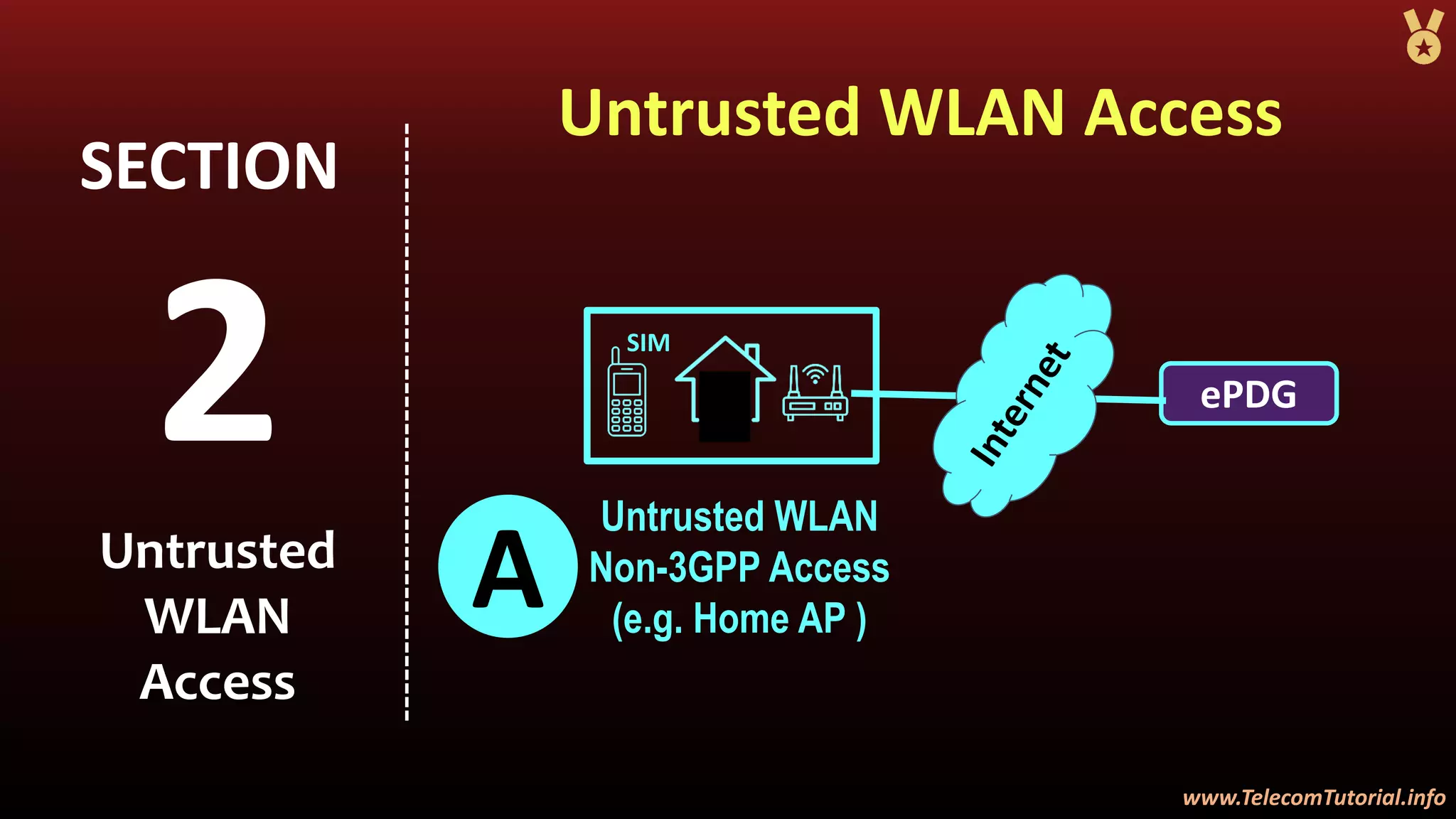
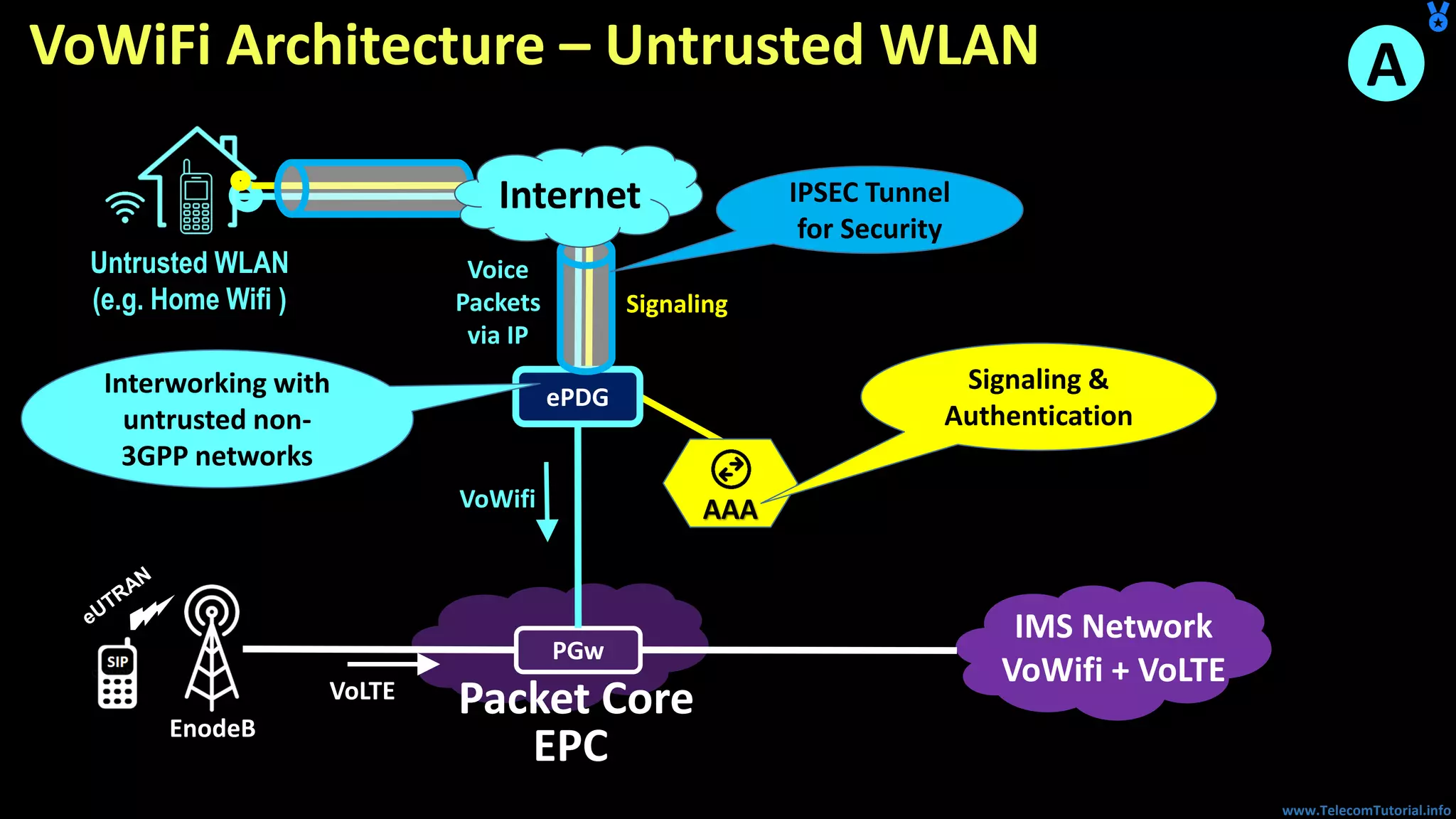
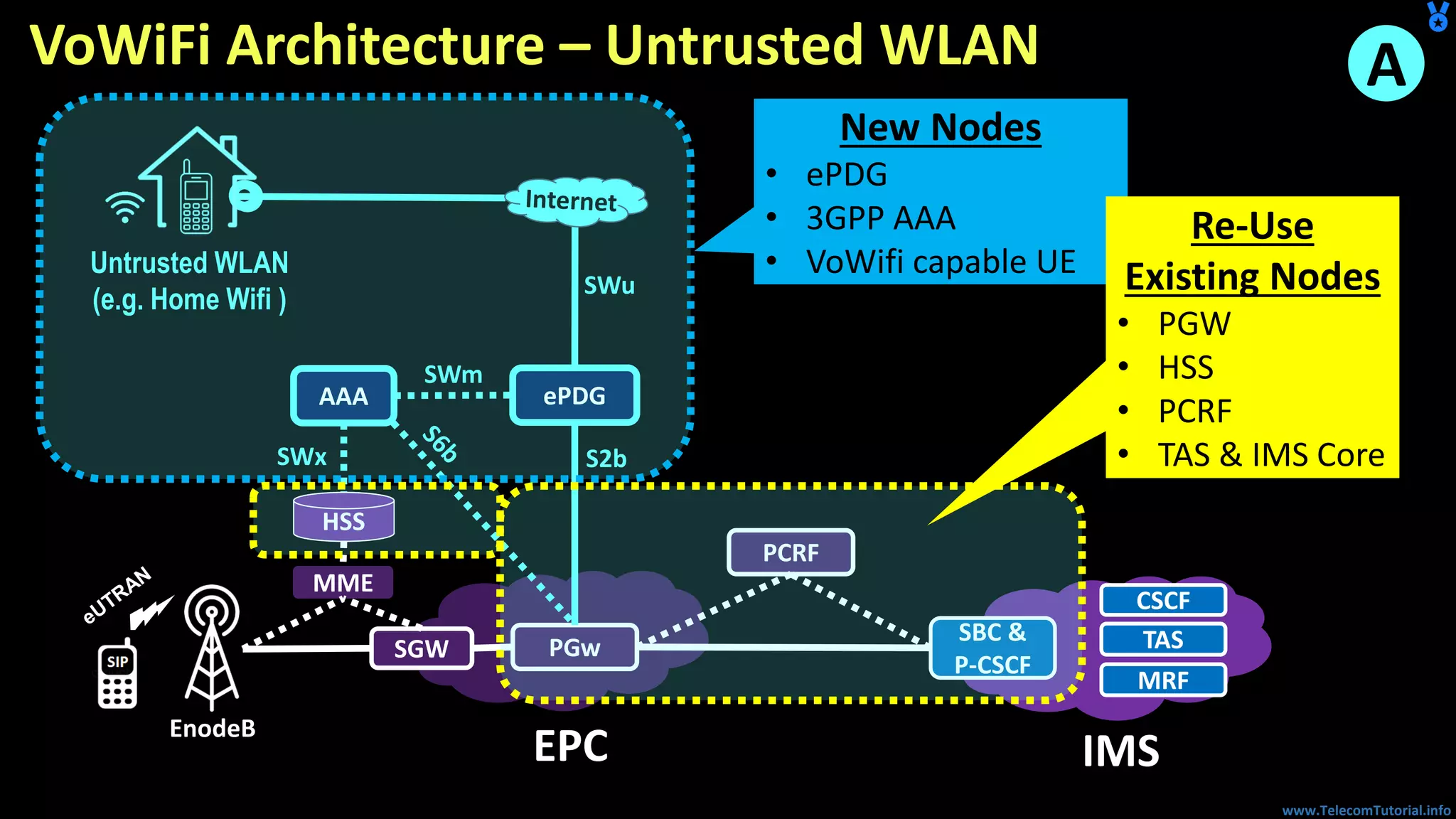
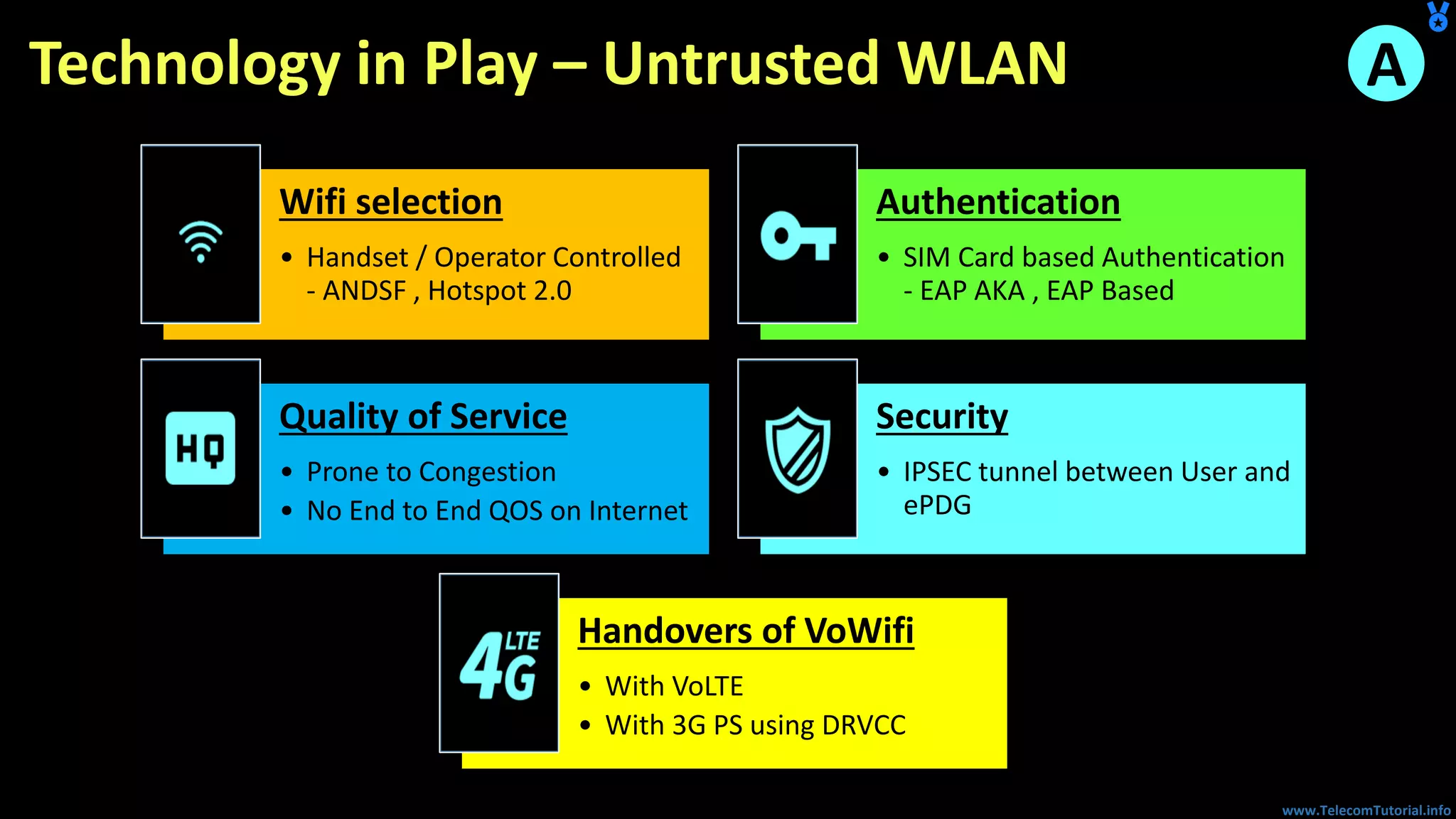
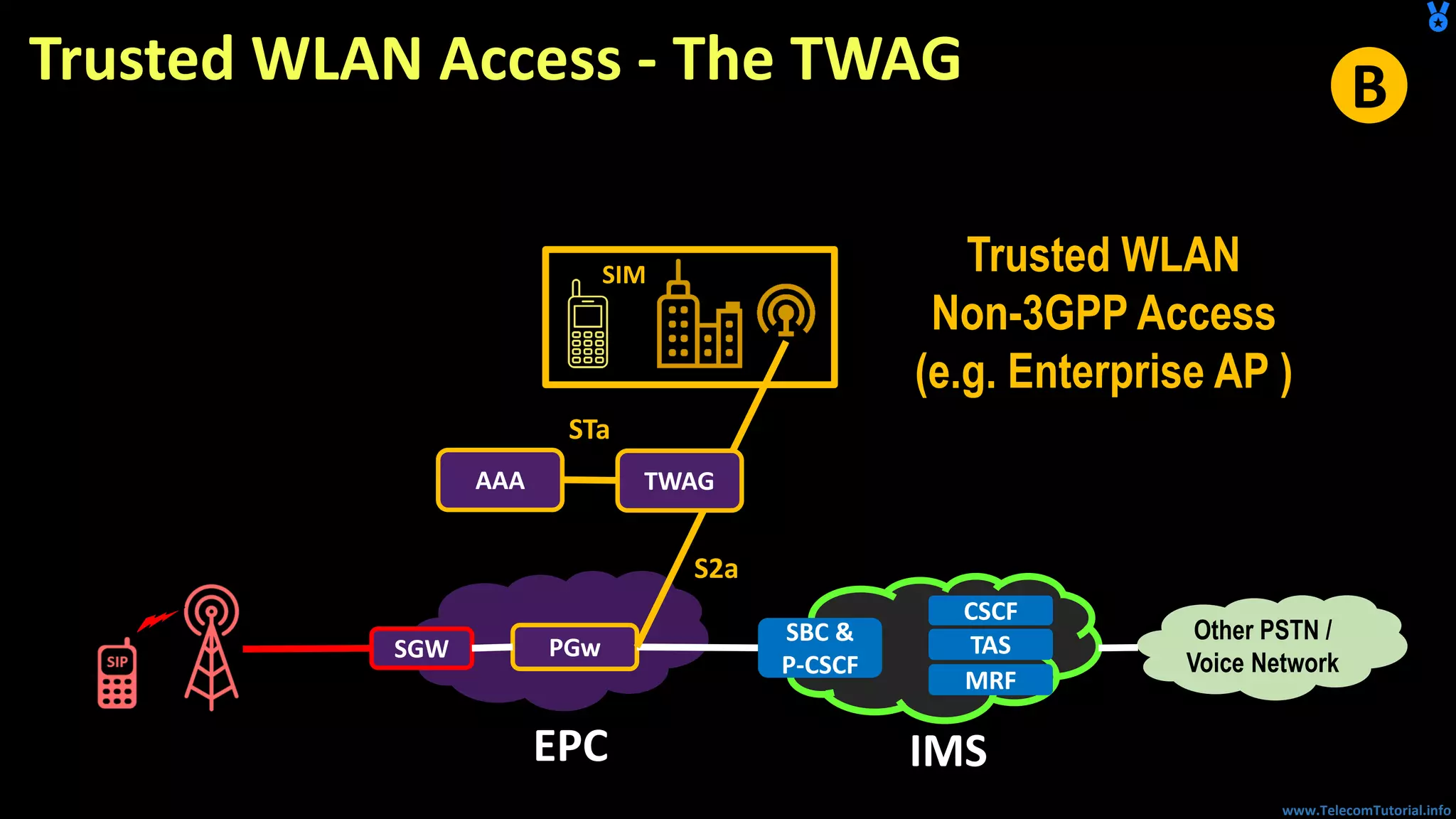
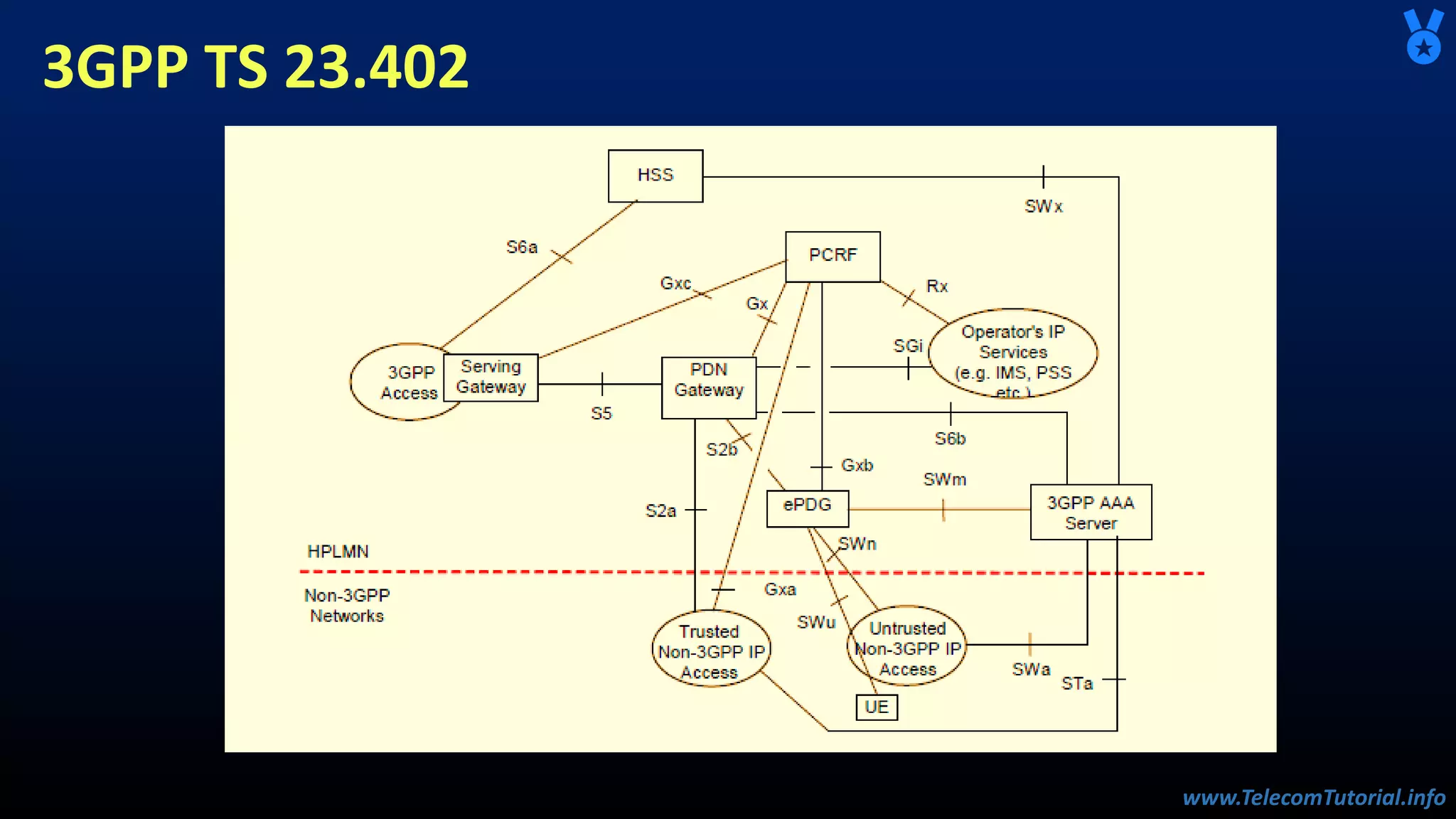
The document provides a detailed overview of Voice over Wi-Fi (VoWiFi) architecture, including various access types such as trusted and untrusted WLAN. It discusses the integration of VoWiFi with existing telecom infrastructures, emphasizing the seamless handover capabilities between LTE and Wi-Fi. Additionally, it covers key technical specifications and options for addressing security and authentication in VoWiFi implementations.