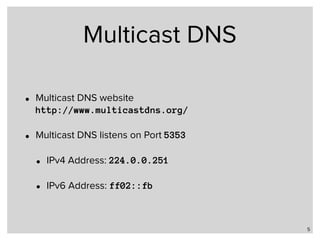
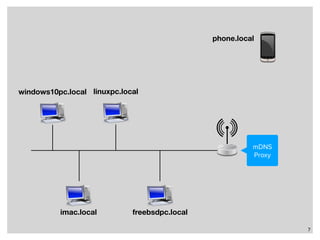
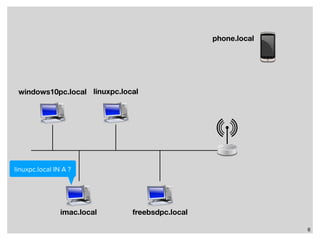
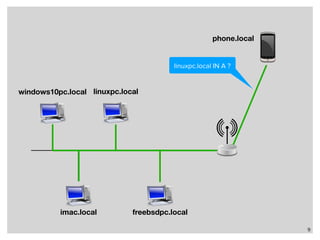
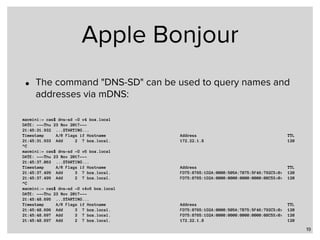
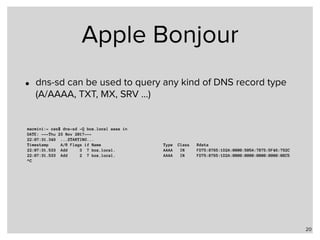
The webinar discusses local name resolution systems like Multicast DNS (mDNS) and its implementation across various operating systems including Unix and Windows. It highlights Apple's Bonjour service, which utilizes mDNS, and the Avahi implementation for Linux, along with a focus on systemd-resolved for modern Linux networking. The session explains how these technologies facilitate name resolution in heterogeneous network environments.













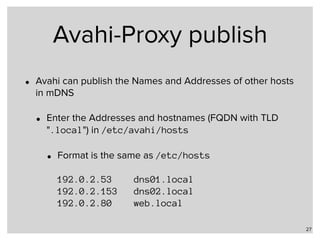
![Avahi
26
[server]
host-name=box
use-ipv4=yes
use-ipv6=yes
enable-dbus=yes
ratelimit-interval-usec=1000000
ratelimit-burst=1000
[wide-area]
enable-wide-area=yes
[publish]
publish-hinfo=yes
publish-workstation=yes
publish-dns-servers=192.0.2.53 192.0.2.153
• Example configuration file for avahi-daemon in
/etc/avahi/avahi-daemon.conf
Name to be
published
Publish HINFO-
Record and
Workstation
Service](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-26-320.jpg)







![Resolved configuration
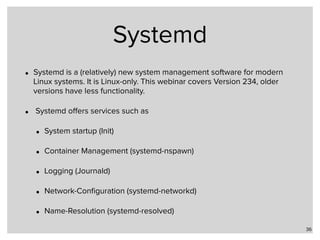
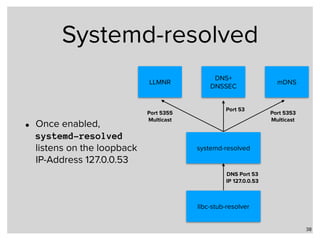
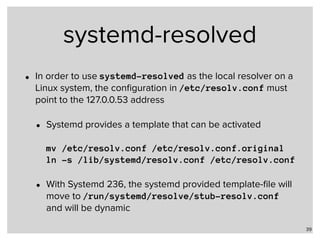
• systemd-resolved is configured via a configuration file in
/etc/systemd/resolved.conf:
41
[Resolve]
DNSStubListener=udp
FallbackDNS=172.22.1.1 172.42.1.105
Domains=example.com home.example.de
MulticastDNS=yes
LLMNR=yes
DNSSEC=yes
Cache=yes
Enables systemd-resolved to
listen on 127.0.0.53](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-41-320.jpg)
![Resolved configuration
• systemd-resolved is configured via a configuration file in
/etc/systemd/resolved.conf:
42
[Resolve]
DNSStubListener=udp
FallbackDNS=9.9.9.9
Domains=example.com home.example.de
MulticastDNS=yes
LLMNR=yes
DNSSEC=yes
Cache=yes
If no DNS resolver are
received via DHCP or IPv6-
RDNSD, use these
If no Fallback-DNS
servers are
configured, the
Google-Public-DNS-
Servers are used](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-42-320.jpg)
![Resolved configuration
• systemd-resolved is configured via a configuration file in
/etc/systemd/resolved.conf:
43
[Resolve]
DNSStubListener=udp
FallbackDNS=9.9.9.9
Domains=example.com home.example.de
MulticastDNS=yes
LLMNR=yes
DNSSEC=yes
Cache=yes
"Search" domains for single
label names in queries](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-43-320.jpg)
![Resolved configuration
• systemd-resolved is configured via a configuration file in
/etc/systemd/resolved.conf:
44
[Resolve]
DNSStubListener=udp
FallbackDNS=9.9.9.9
Domains=example.com home.example.de
MulticastDNS=yes
LLMNR=yes
DNSSEC=yes
Cache=yes
Enable mDNS resolution and
publication](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-44-320.jpg)
![Resolved configuration
• systemd-resolved is configured via a configuration file in
/etc/systemd/resolved.conf:
45
[Resolve]
DNSStubListener=udp
FallbackDNS=9.9.9.9
Domains=example.com home.example.de
MulticastDNS=yes
LLMNR=yes
DNSSEC=yes
Cache=yes
Enable LLMNR resolution and
publication](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-45-320.jpg)
![Resolved configuration
• systemd-resolved is configured via a configuration file in
/etc/systemd/resolved.conf:
46
[Resolve]
DNSStubListener=udp
FallbackDNS=9.9.9.9
Domains=example.com home.example.de
MulticastDNS=yes
LLMNR=yes
DNSSEC=yes
Cache=yes
Validate DNSSEC signatures
against the trust-anchor](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-46-320.jpg)
![Resolved configuration
• systemd-resolved is configured via a configuration file in
/etc/systemd/resolved.conf:
47
[Resolve]
DNSStubListener=udp
FallbackDNS=9.9.9.9
Domains=example.com home.example.de
MulticastDNS=yes
LLMNR=yes
DNSSEC=yes
Cache=yes
Enable a local DNS/mDNS/
LLMNR cache](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-47-320.jpg)
![systemd-resolved
48
[user@box]~% sudo systemctl status systemd-resolved
● systemd-resolved.service - Network Name Resolution
Loaded: loaded (/usr/lib/systemd/system/systemd-resolved.service; enabled; vendor preset: disable
Active: active (running) since Thu 2017-11-23 11:59:24 CET; 9s ago
Docs: man:systemd-resolved.service(8)
https://www.freedesktop.org/wiki/Software/systemd/resolved
https://www.freedesktop.org/wiki/Software/systemd/writing-network-configuration-managers
https://www.freedesktop.org/wiki/Software/systemd/writing-resolver-clients
Main PID: 7017 (systemd-resolve)
Status: "Processing requests..."
Tasks: 1 (limit: 4915)
CGroup: /system.slice/systemd-resolved.service
└─7017 /usr/lib/systemd/systemd-resolved
Nov 23 11:59:24 csmobile4.home.strotmann.de systemd[1]: Starting Network Name Resolution...
Nov 23 11:59:24 csmobile4.home.strotmann.de systemd-resolved[7017]: Positive Trust Anchors:
Nov 23 11:59:24 csmobile4.home.strotmann.de systemd-resolved[7017]: . IN DS 19036 8 2 49aac11d7b6f64
Nov 23 11:59:24 csmobile4.home.strotmann.de systemd-resolved[7017]: . IN DS 20326 8 2 e06d44b80b8f1d
Nov 23 11:59:24 csmobile4.home.strotmann.de systemd-resolved[7017]: Negative trust anchors: 10.in-ad…
Nov 23 11:59:24 csmobile4.home.strotmann.de systemd-resolved[7017]: Using system hostname 'box.example.com'
Nov 23 11:59:24 csmobile4.home.strotmann.de systemd[1]: Started Network Name Resolution.](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-48-320.jpg)
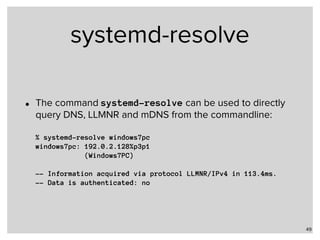
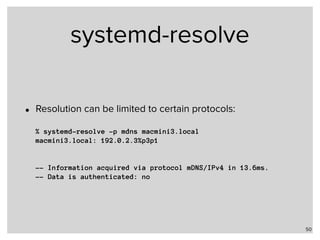
![systemd-resolve
• Status of the systemd-resolver:
% systemd-resolve —status
Global
DNS Servers: 172.42.1.105
DNSSEC NTA: 10.in-addr.arpa
16.172.in-addr.arpa
[…]
168.192.in-addr.arpa
31.172.in-addr.arpa
corp
d.f.ip6.arpa
home
internal
intranet
lan
local
private
test
Link 2 (eno1)
Current Scopes: DNS LLMNR/IPv4 LLMNR/IPv6
LLMNR setting: yes
MulticastDNS setting: no
DNSSEC setting: yes
DNSSEC supported: yes
DNS Servers: 192.0.2.1
192.0.2.53
fd75:8765:1d2a::1
DNS Domain: home.example.com
51](https://image.slidesharecdn.com/part3alternative-name-resolution-in-unix-networks-171205135505/85/Part-3-Local-Name-Resolution-in-Linux-FreeBSD-and-macOS-iOS-51-320.jpg)