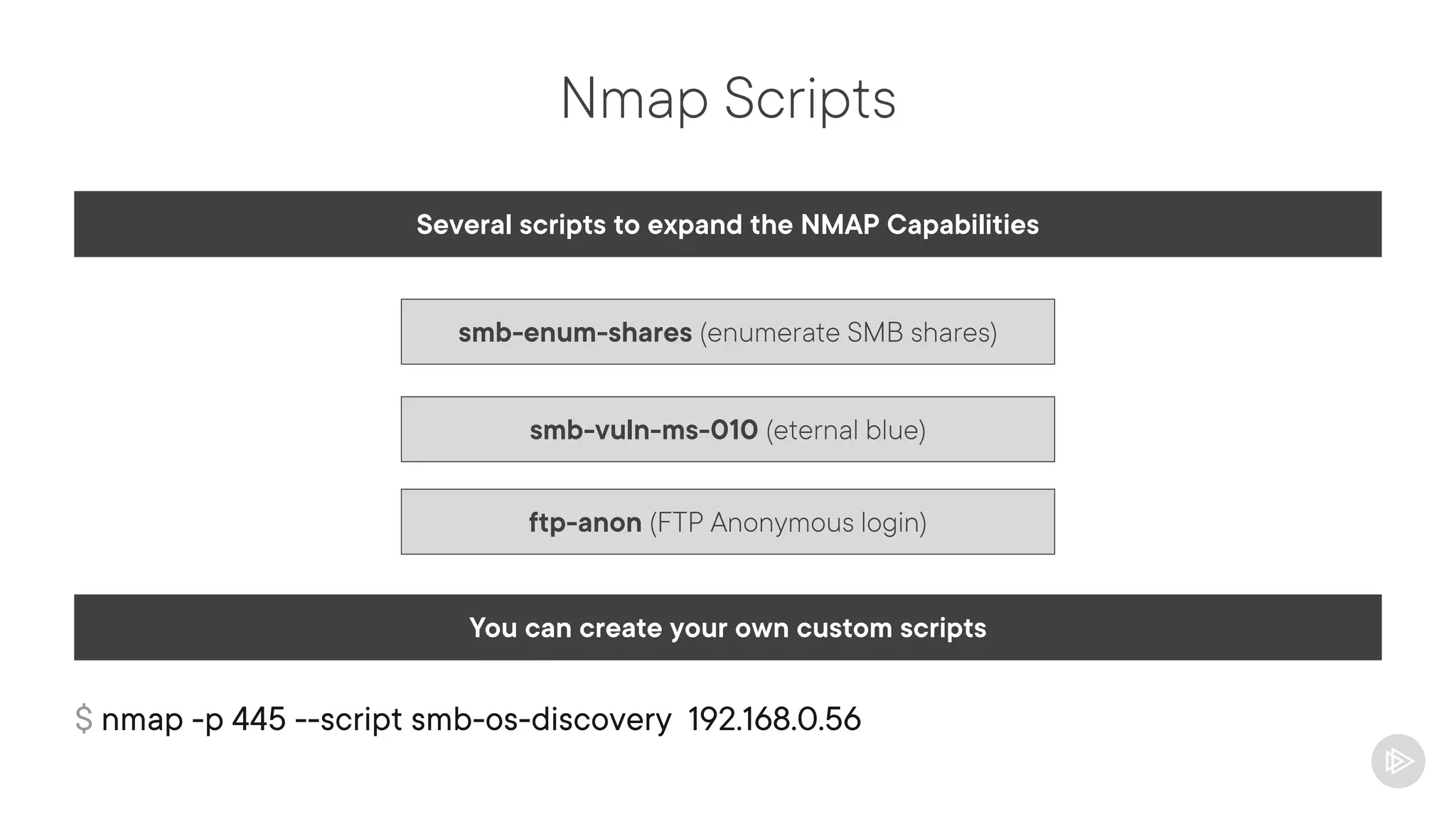
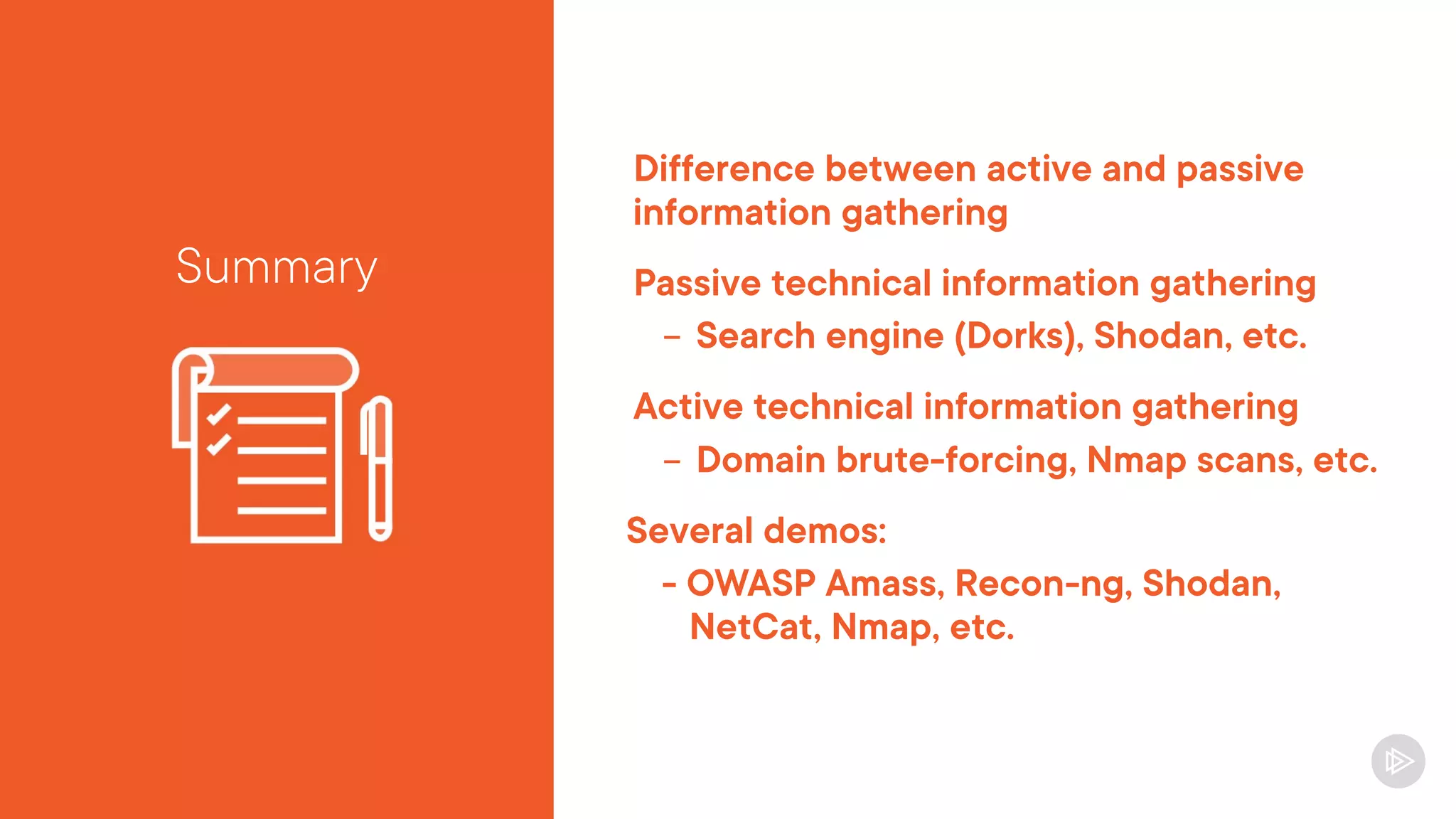
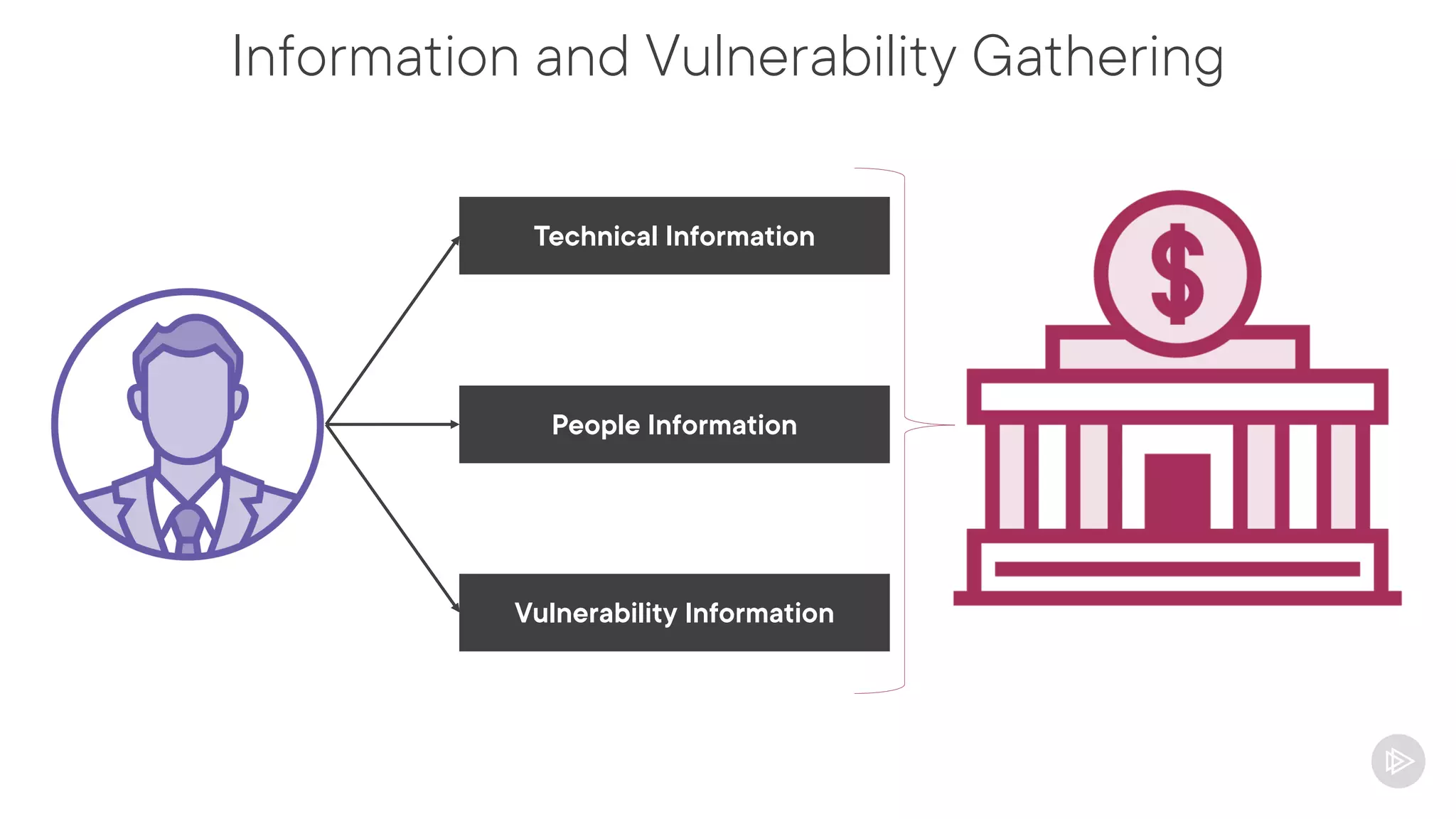
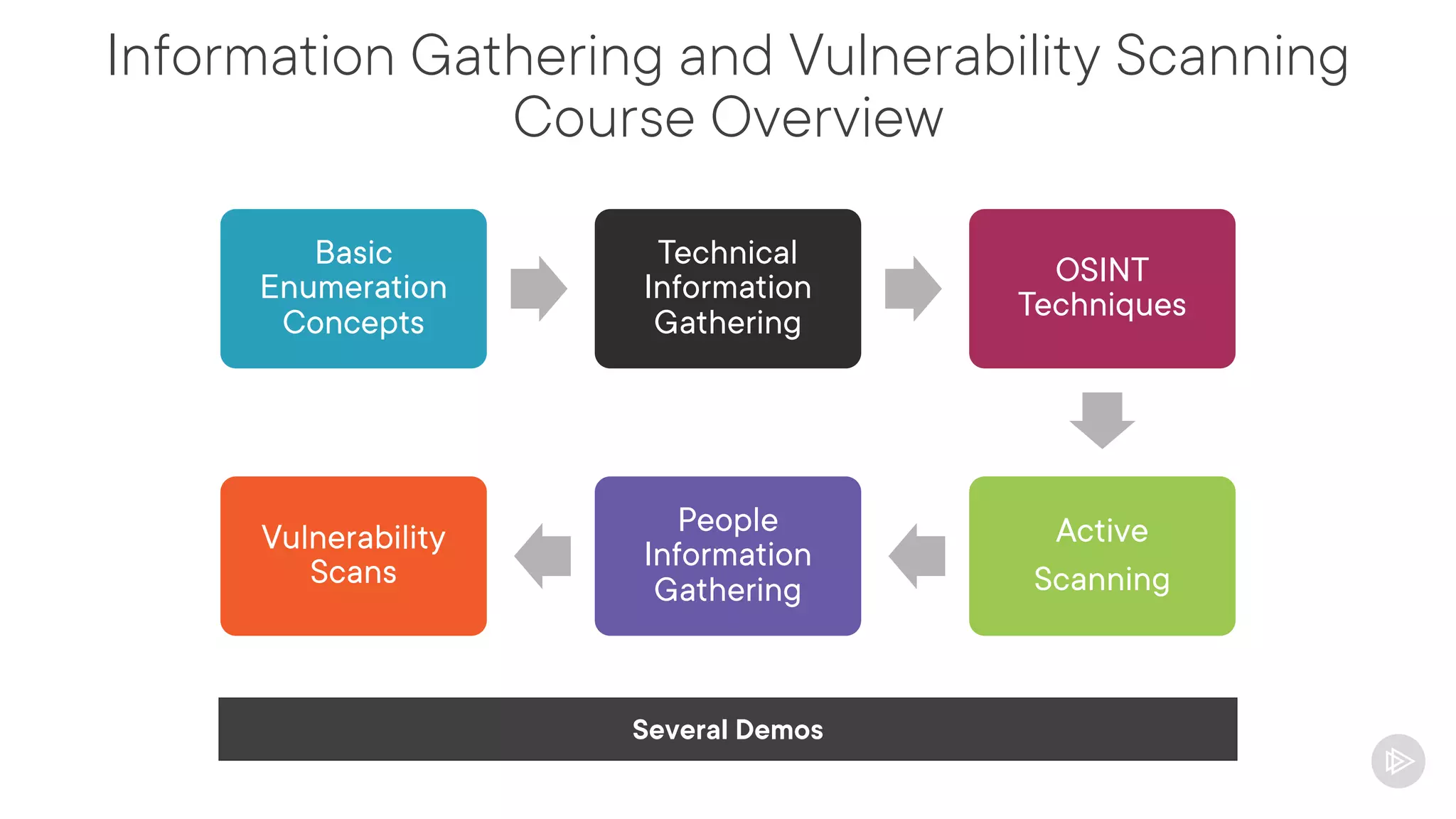
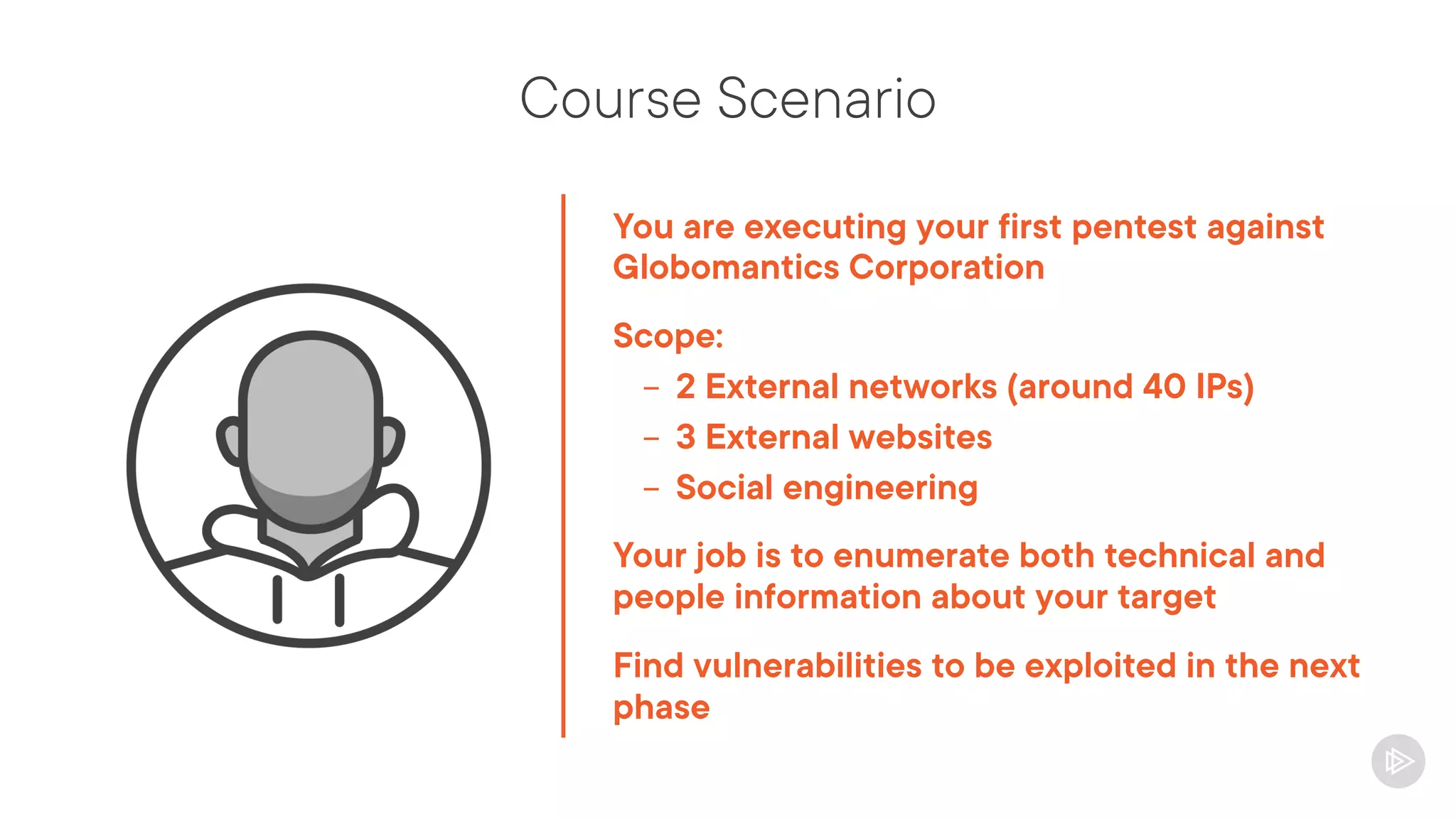
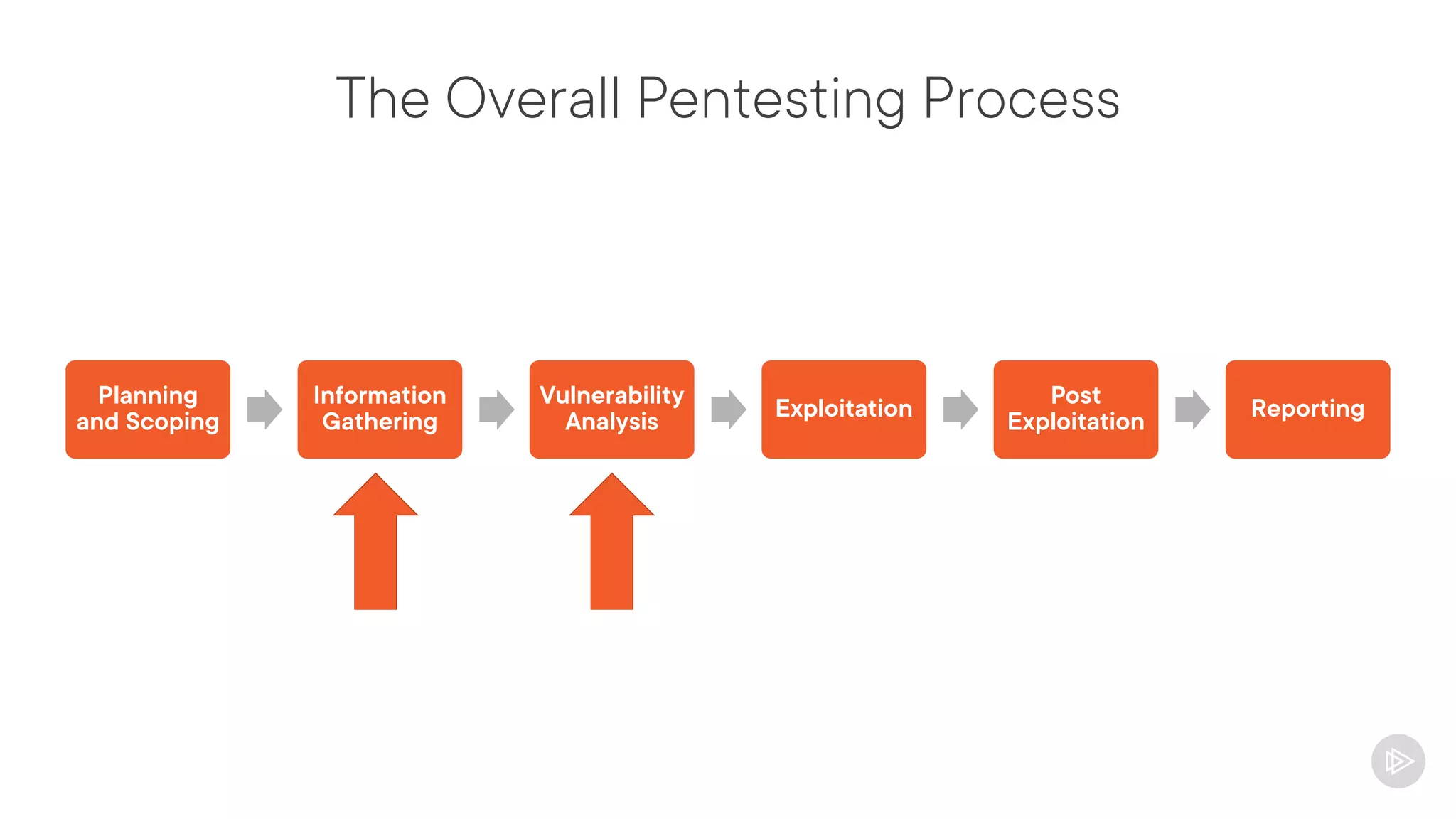
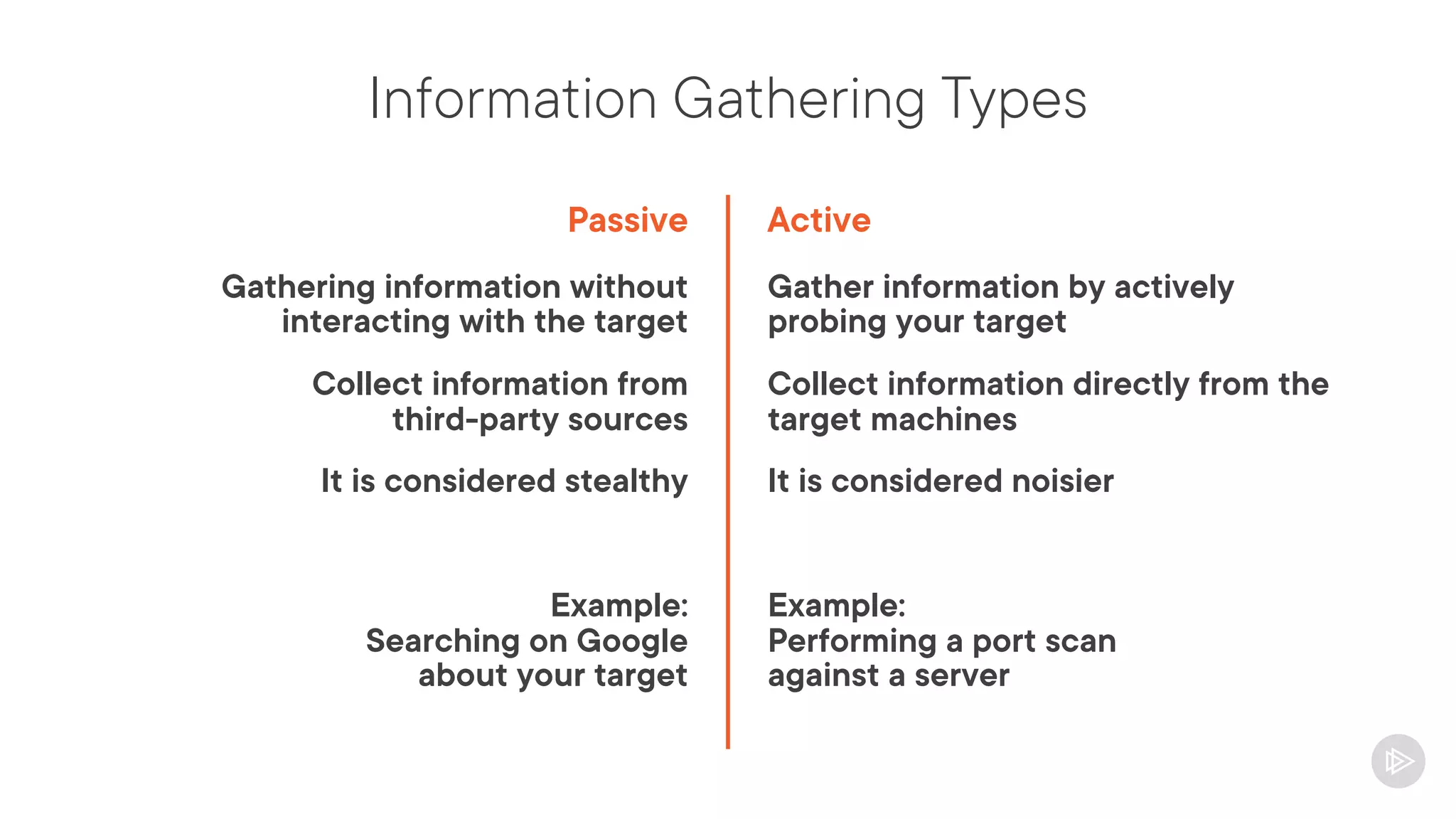
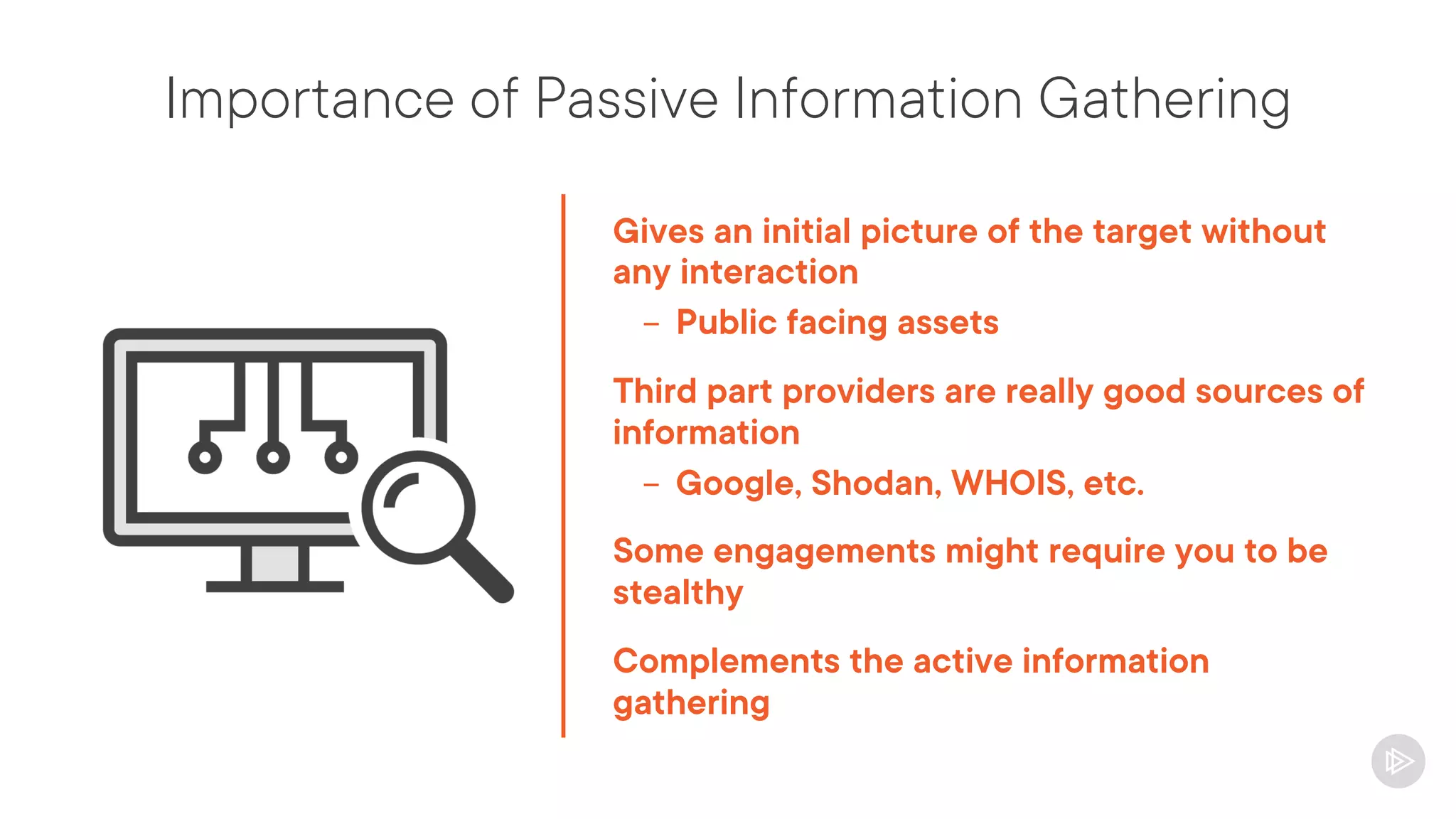
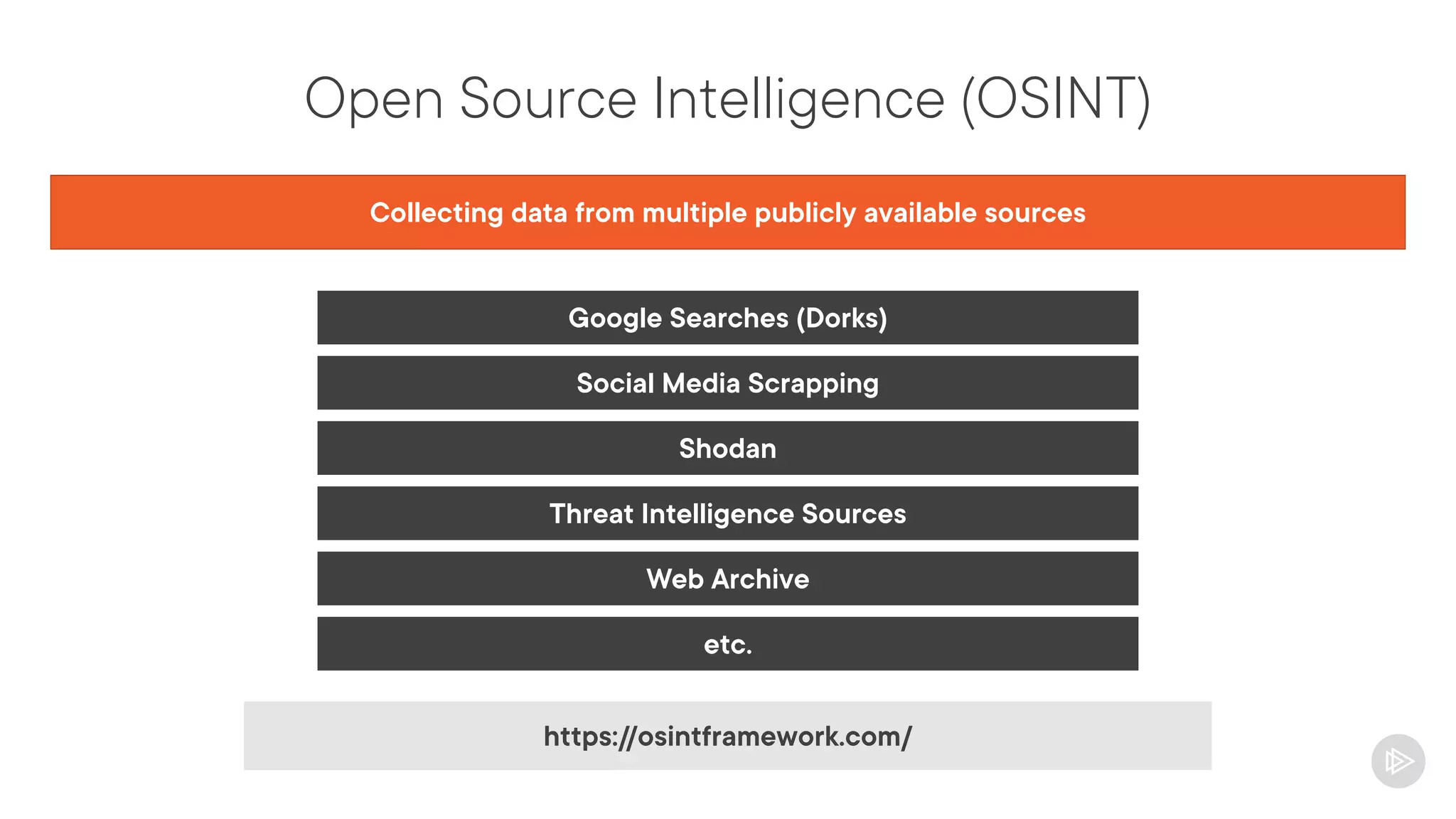
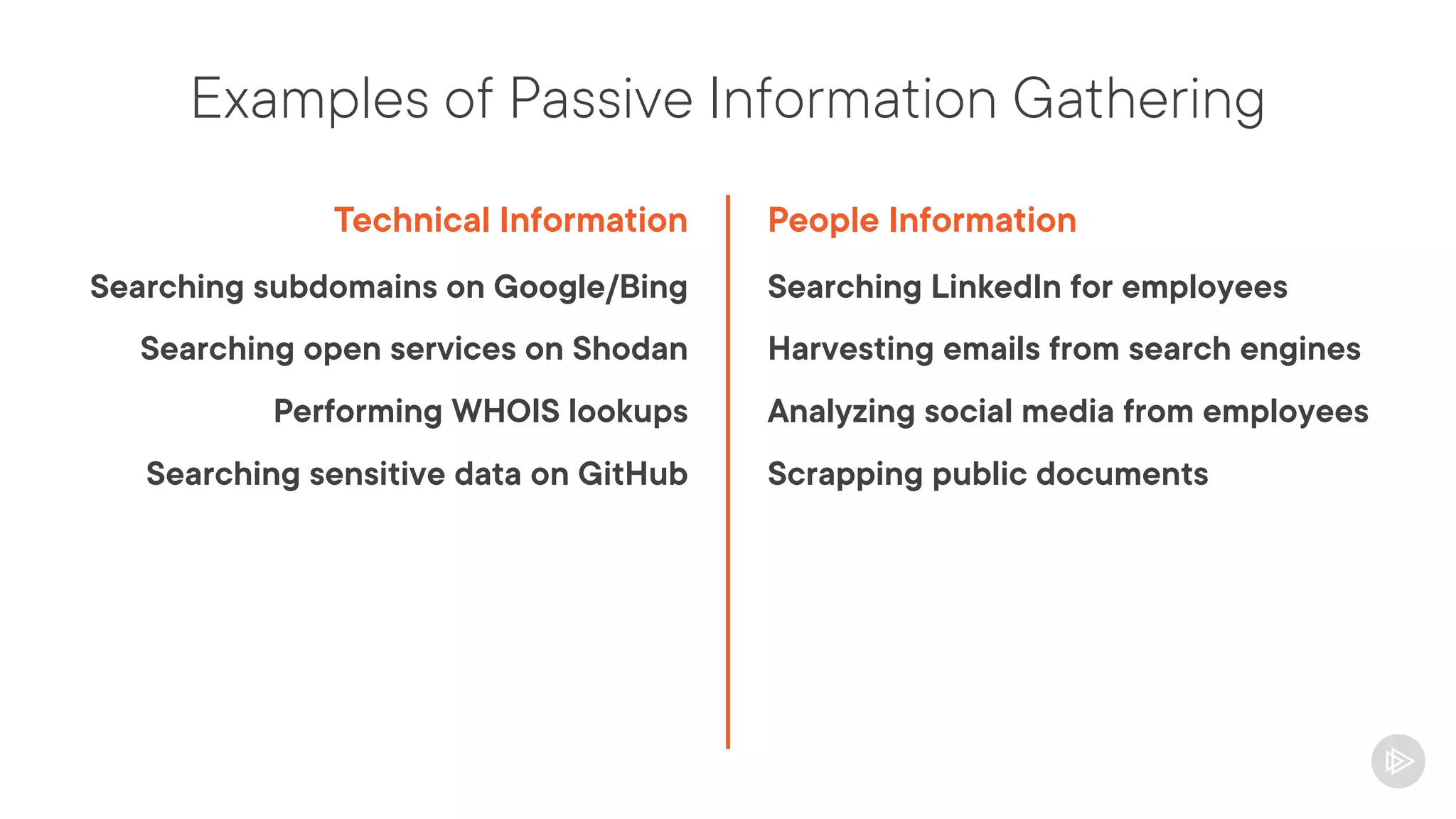
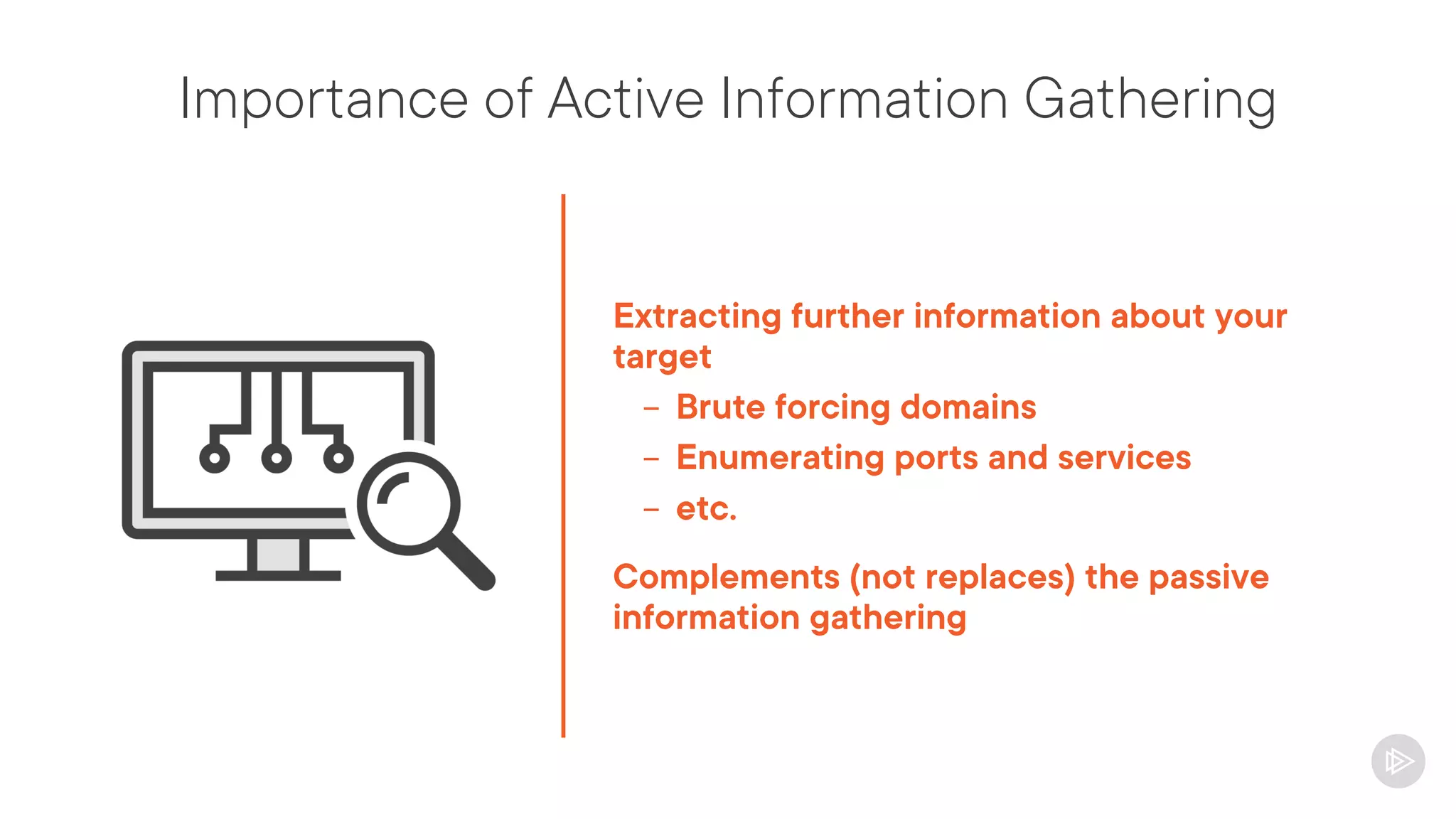
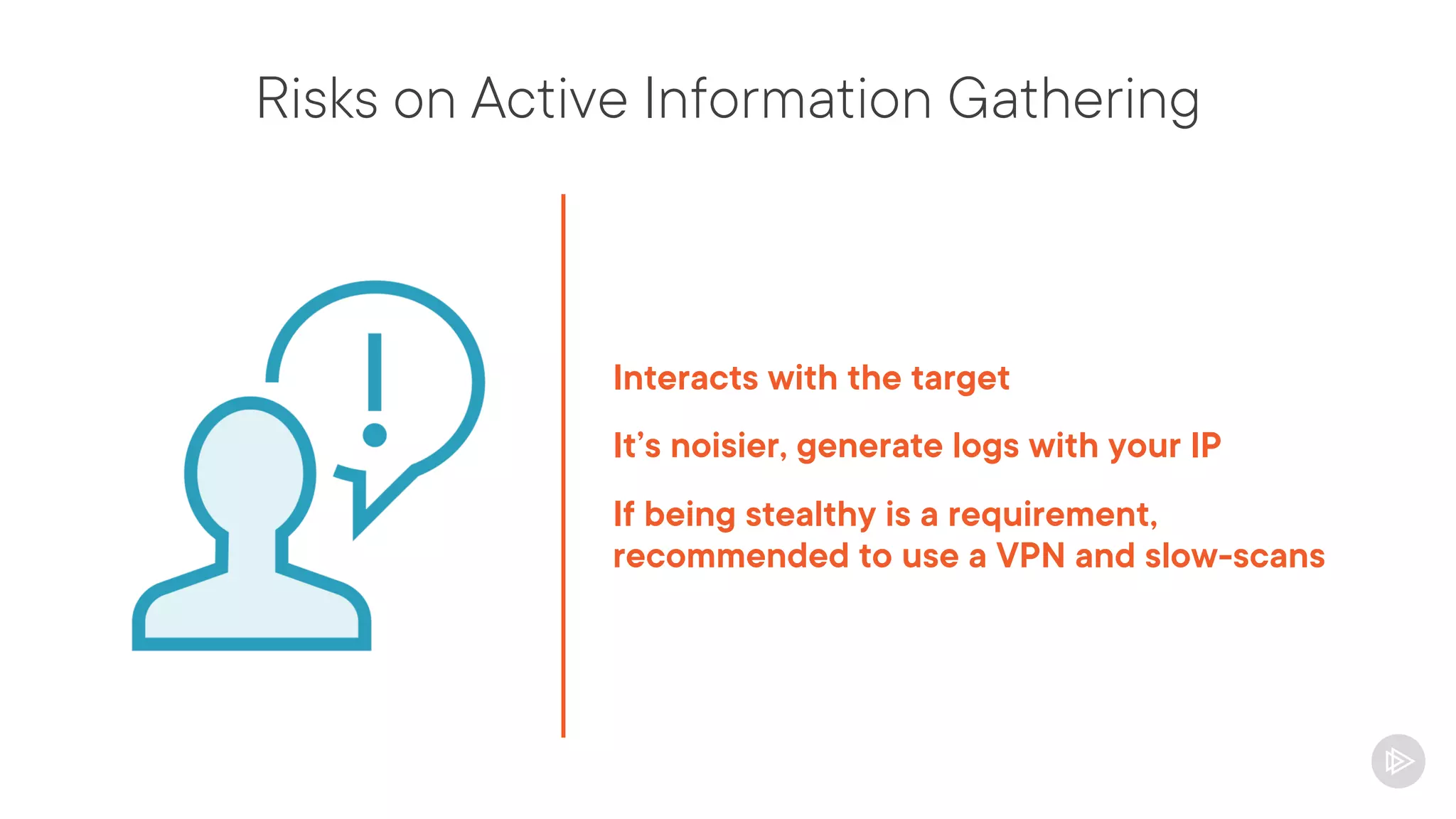
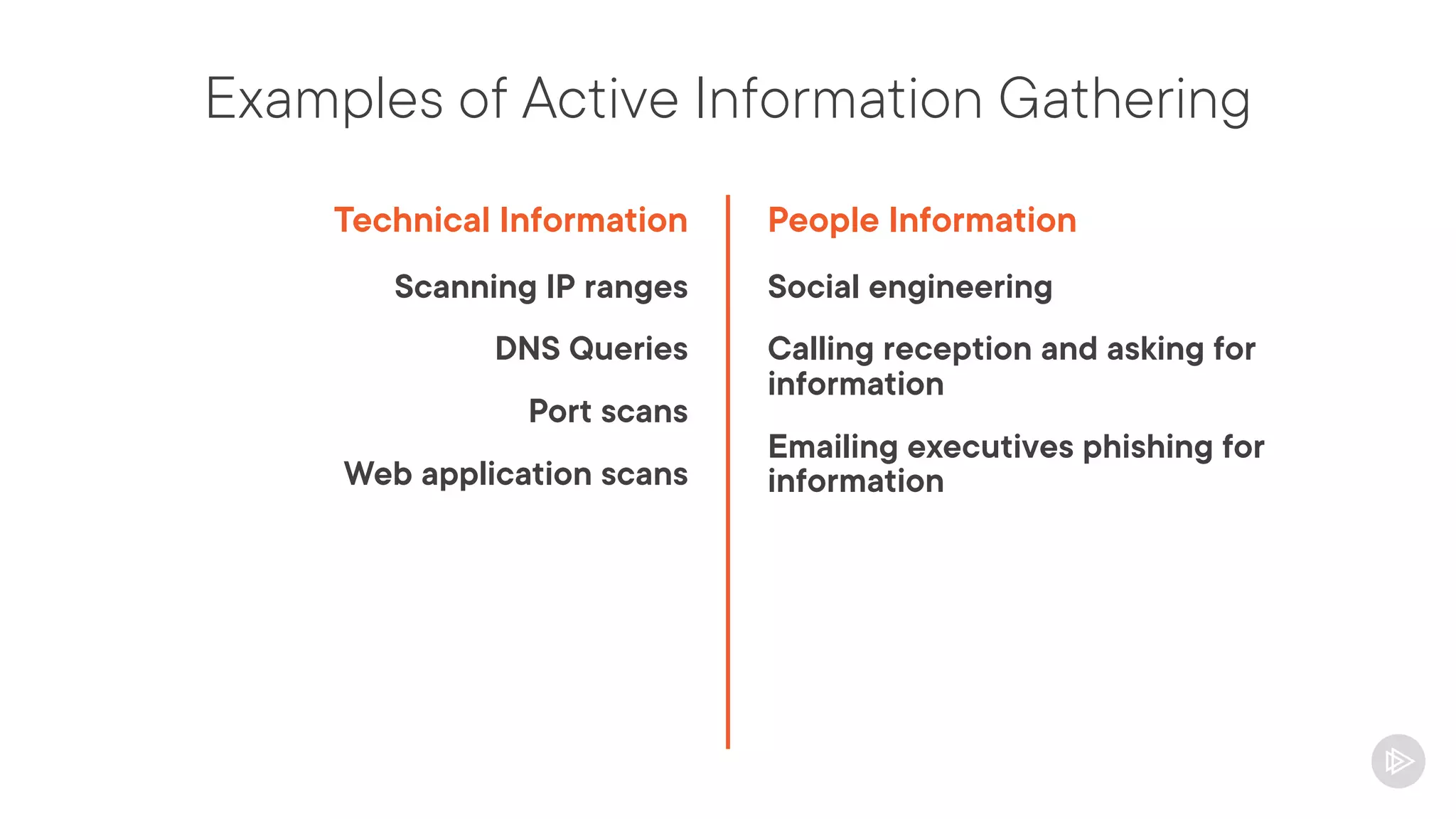
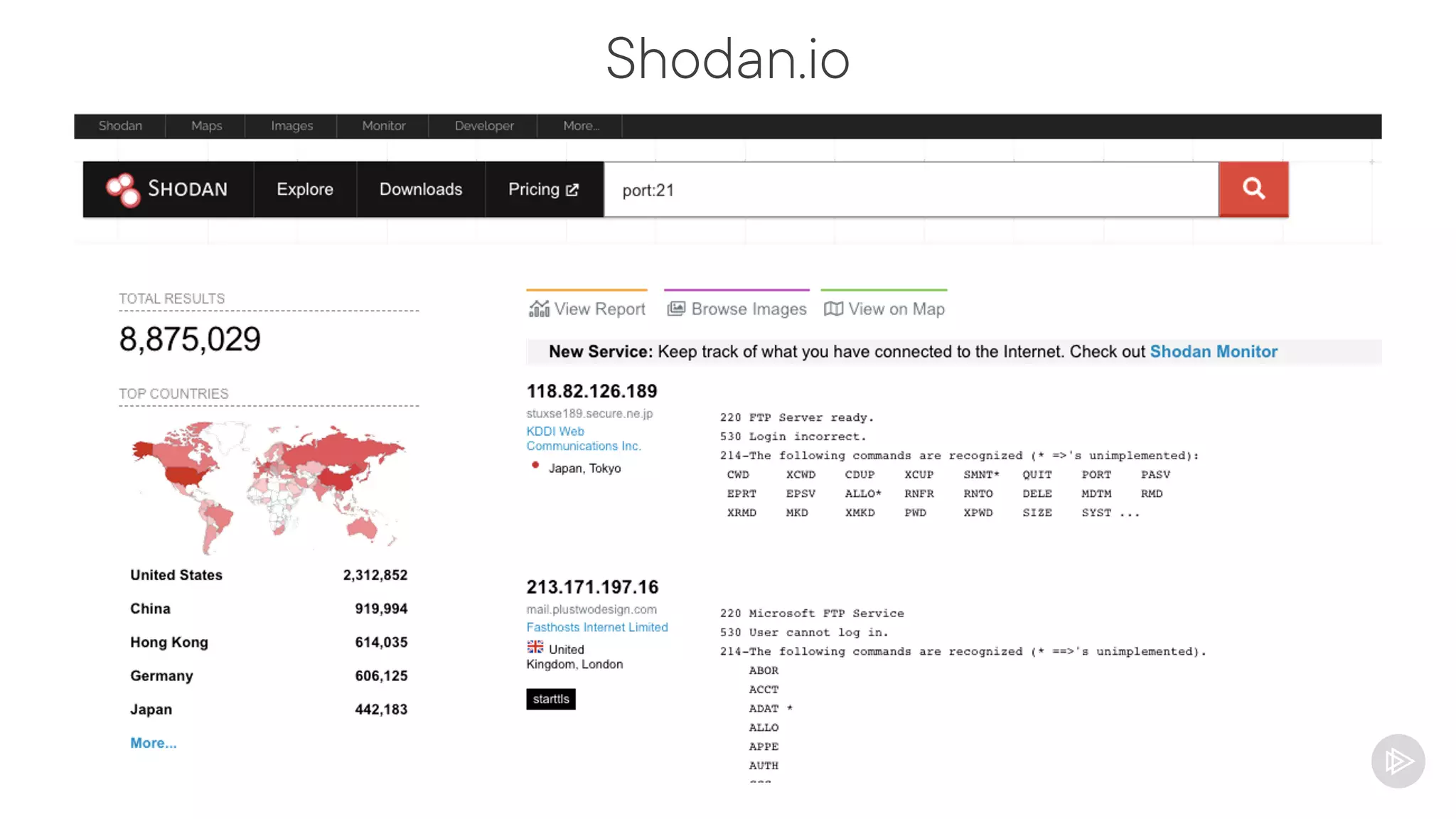
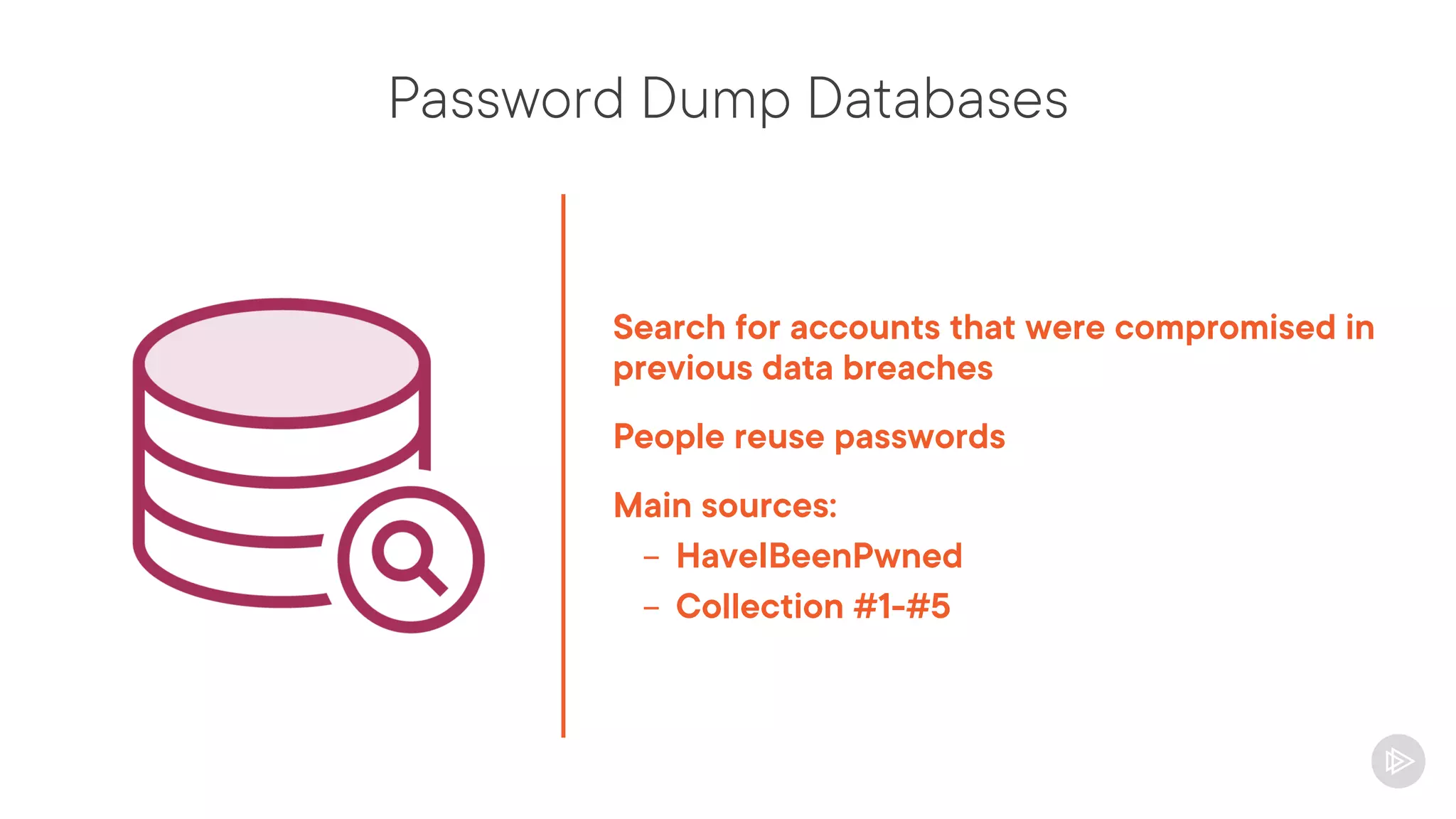
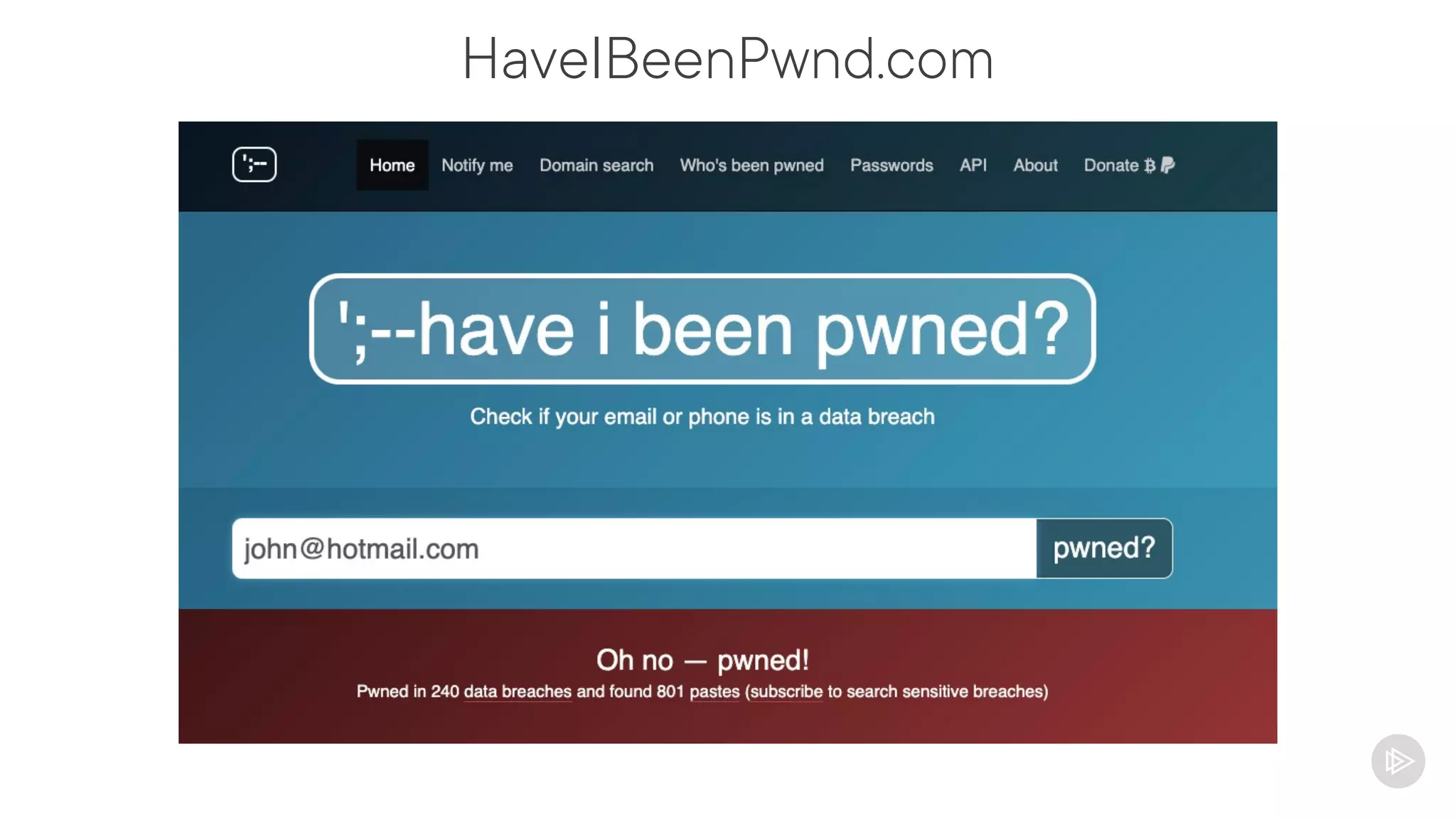
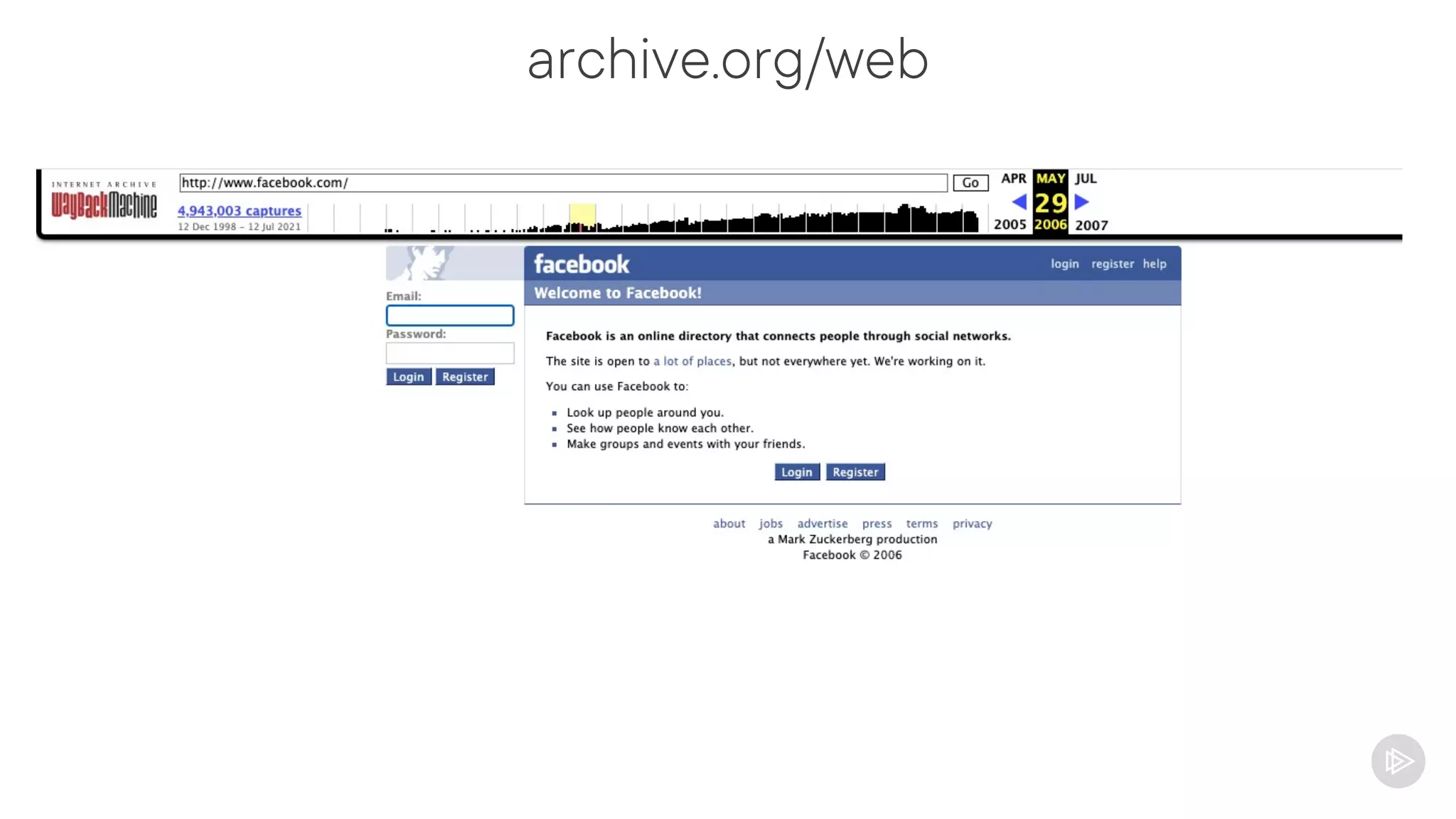
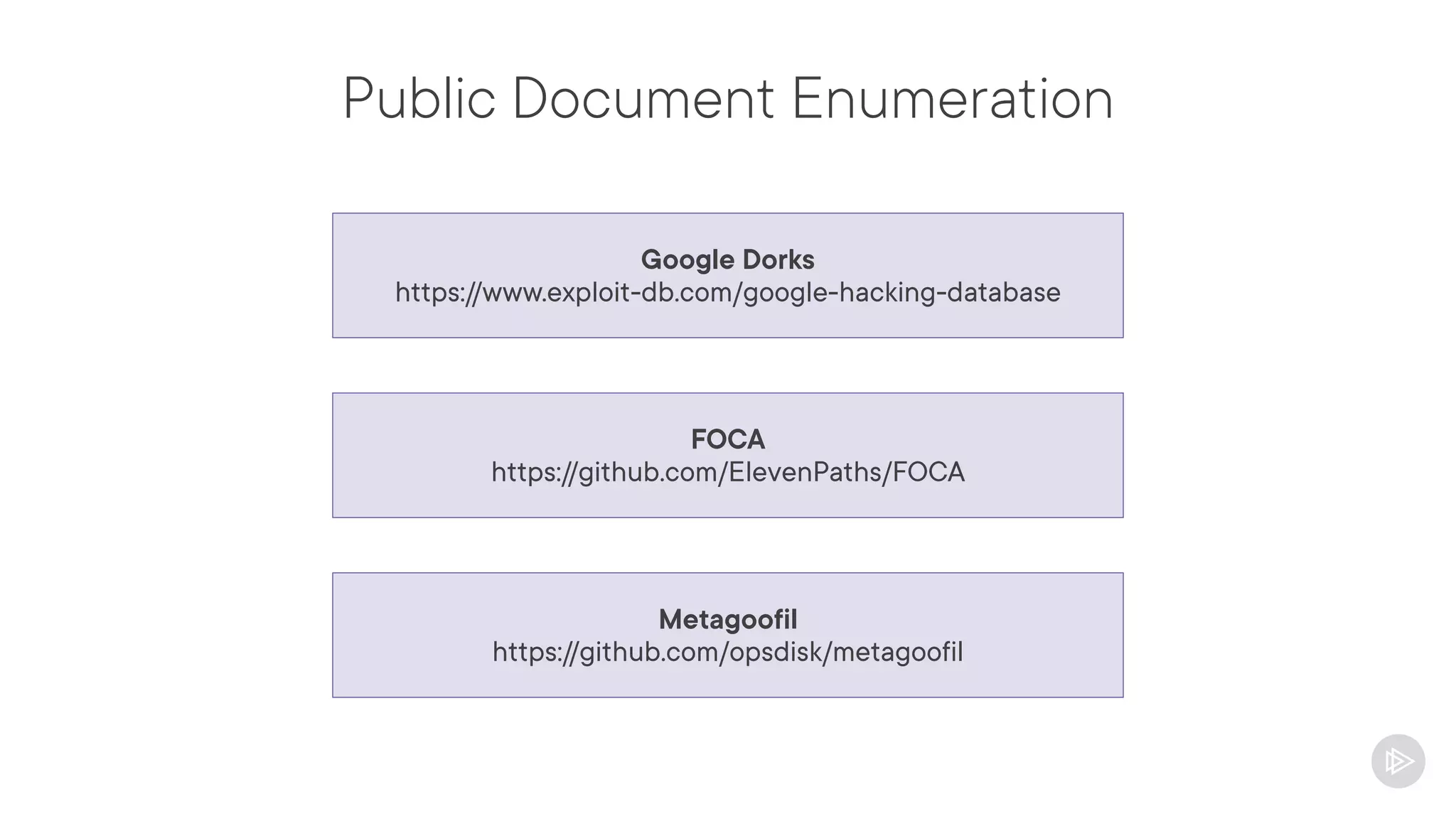
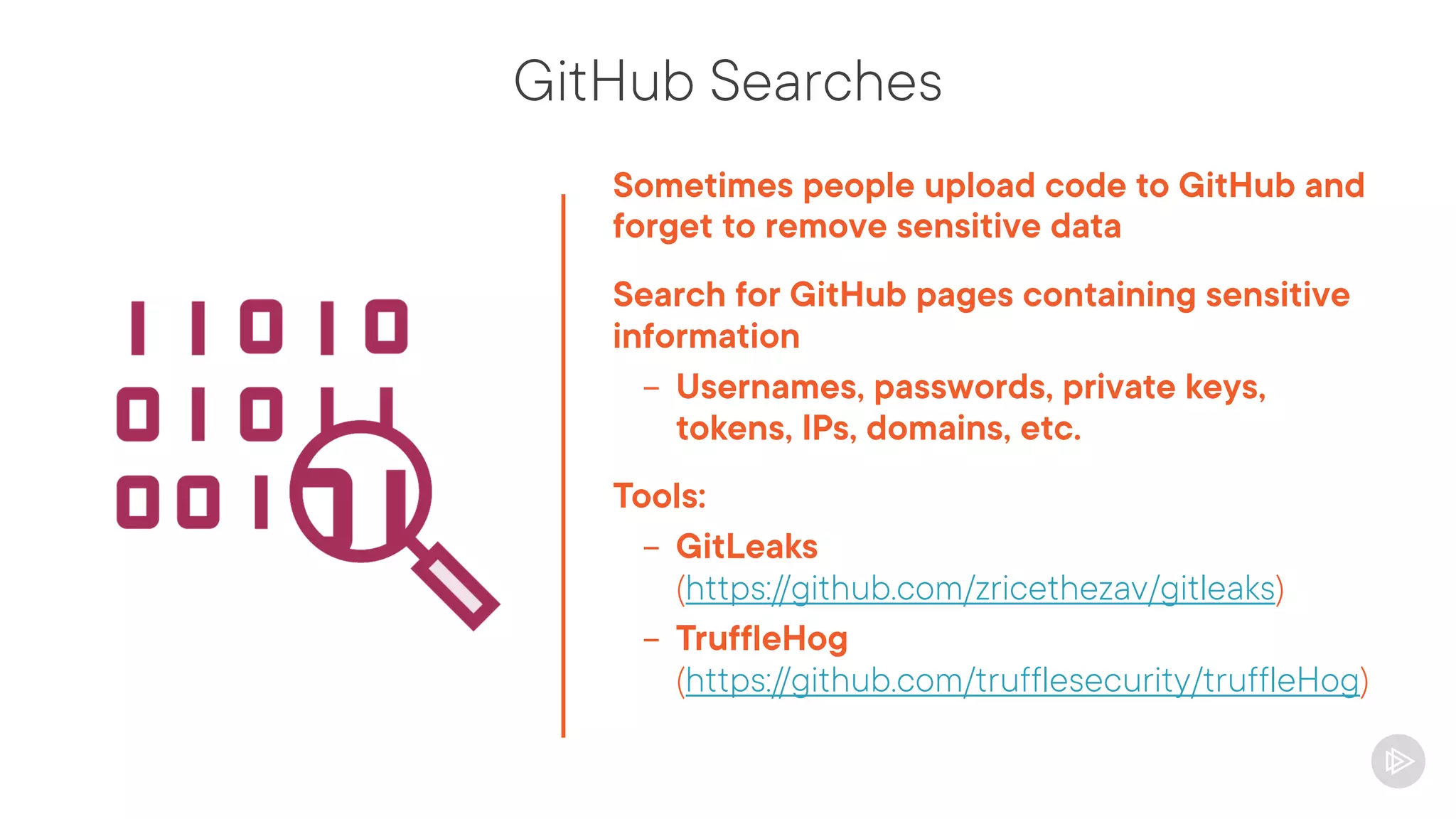
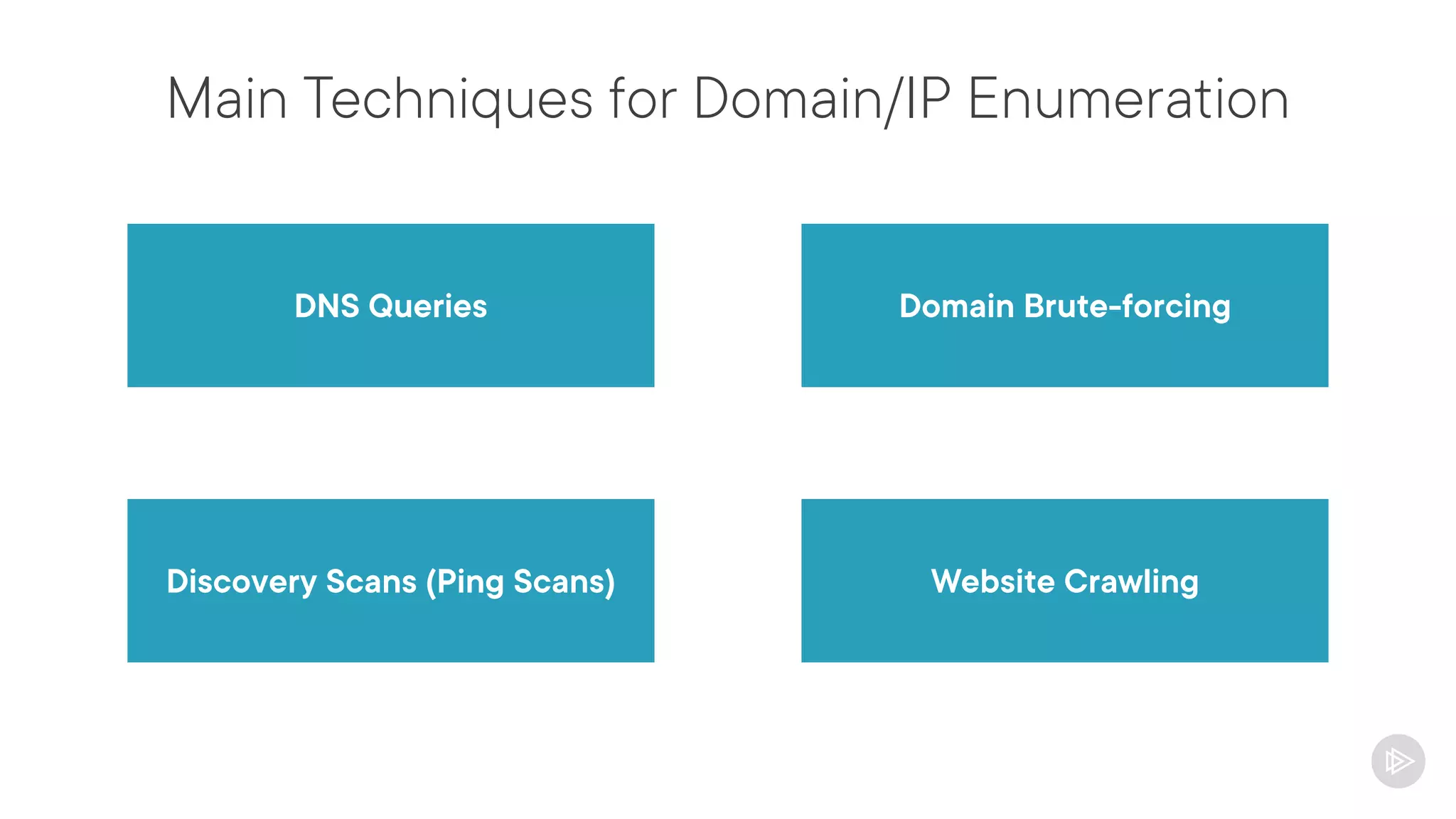
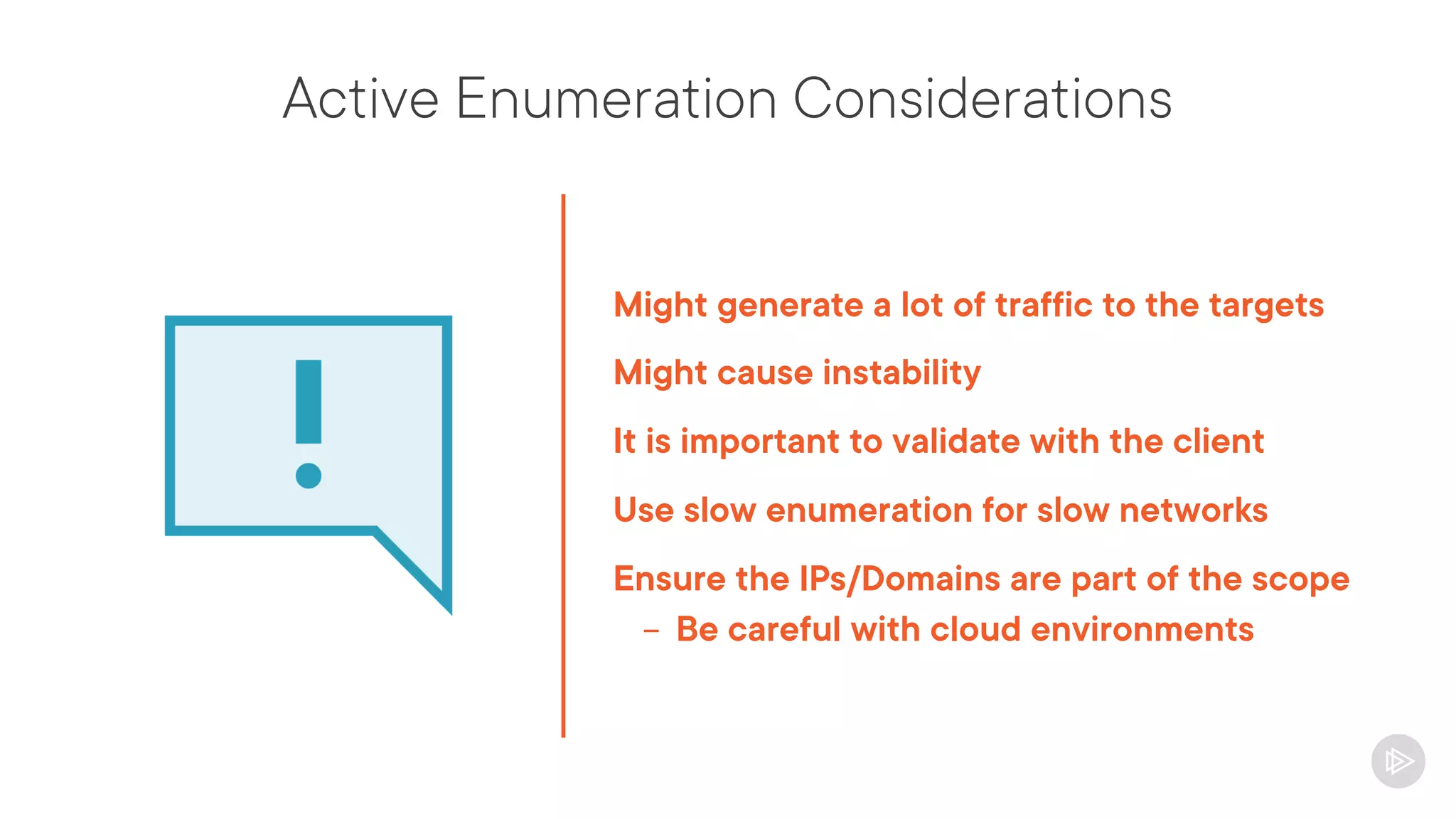
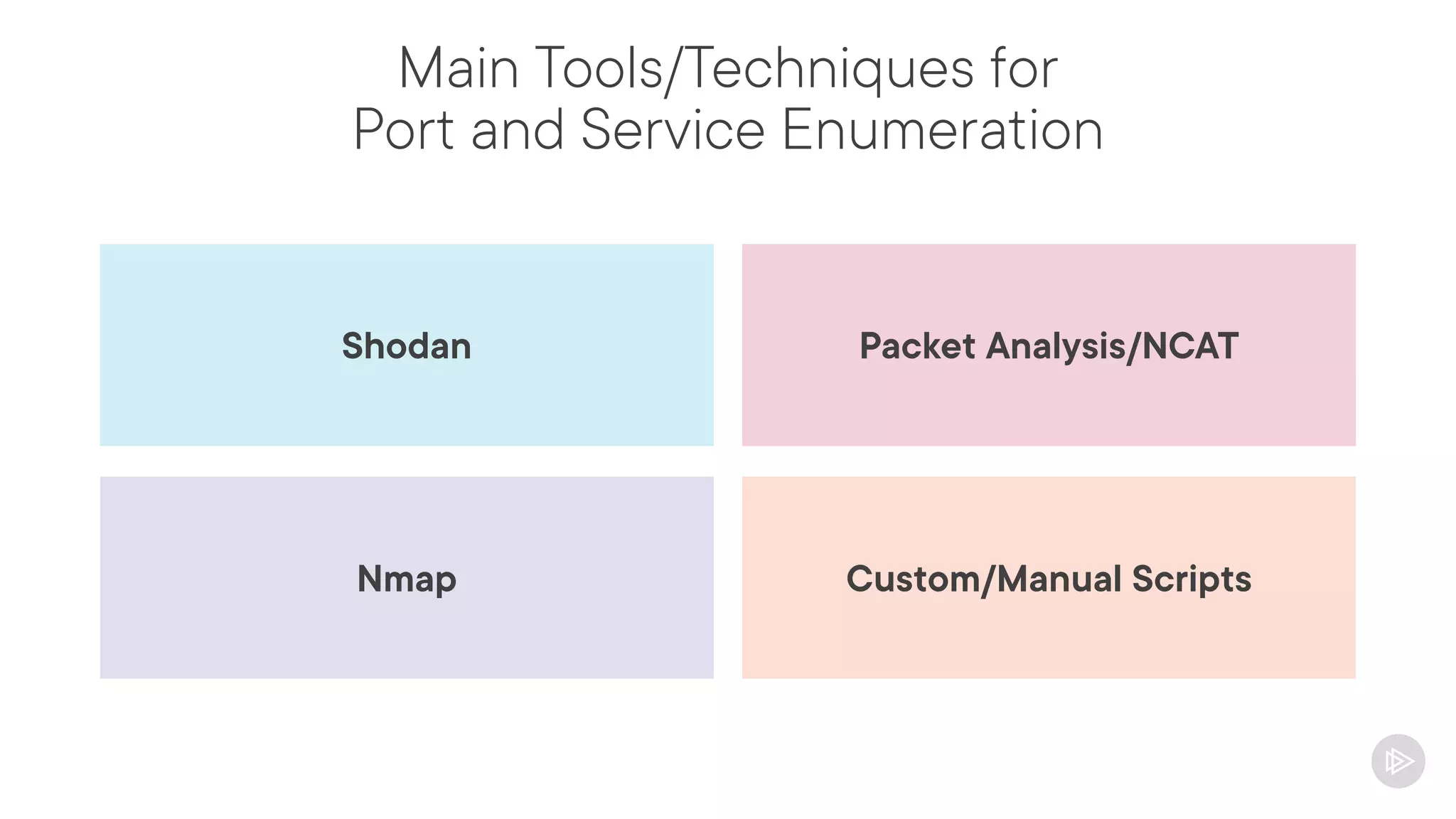
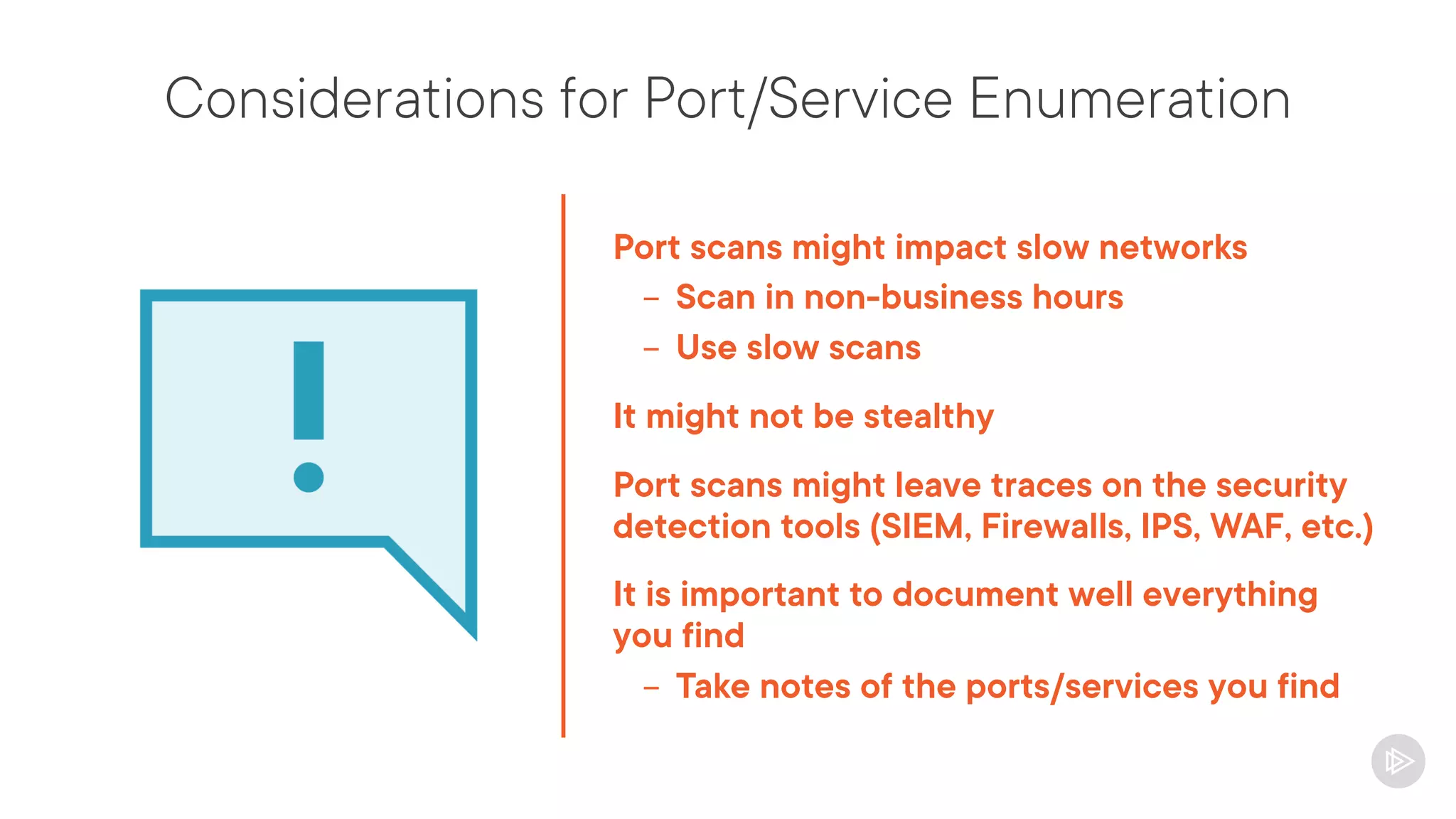
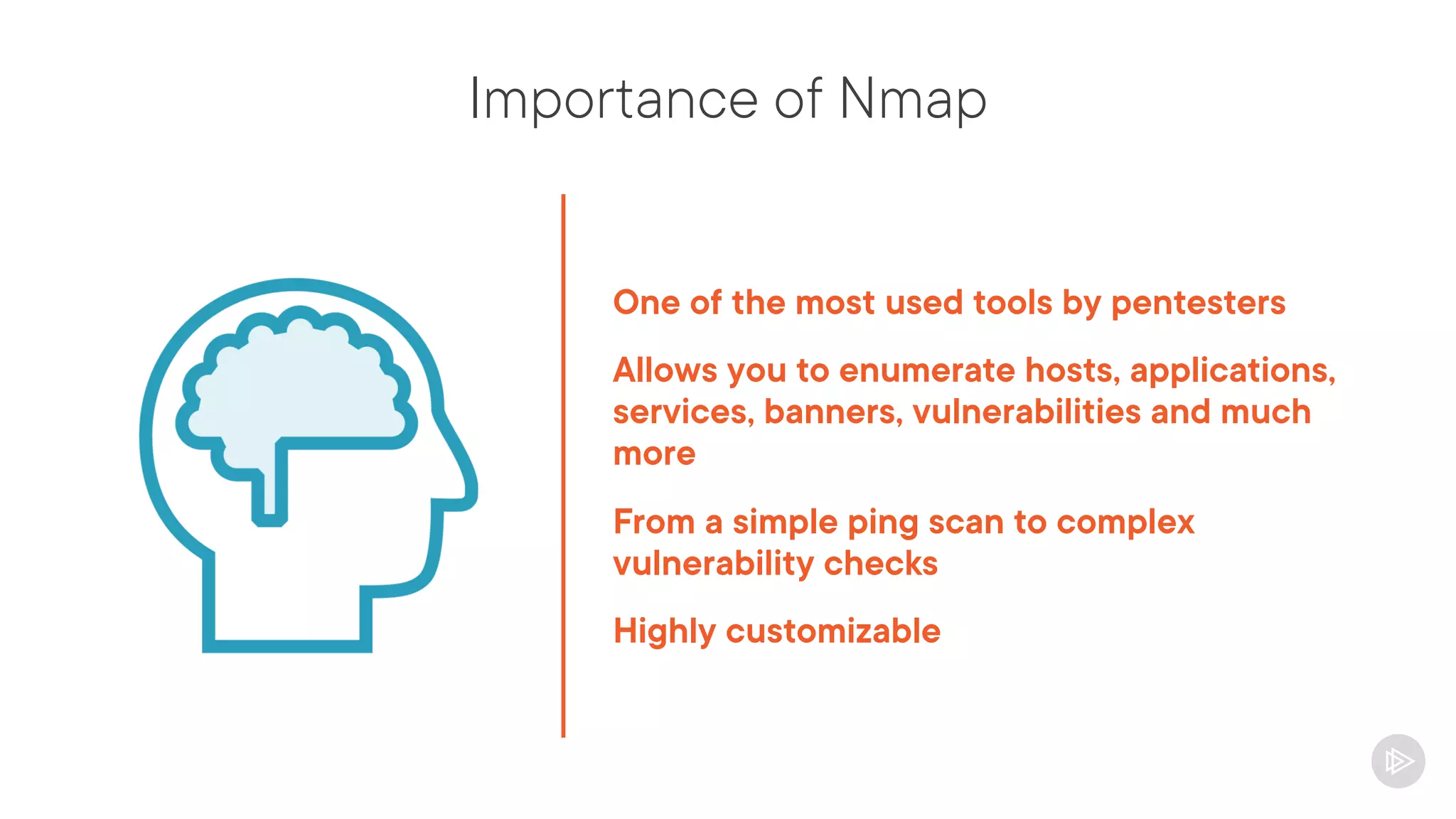
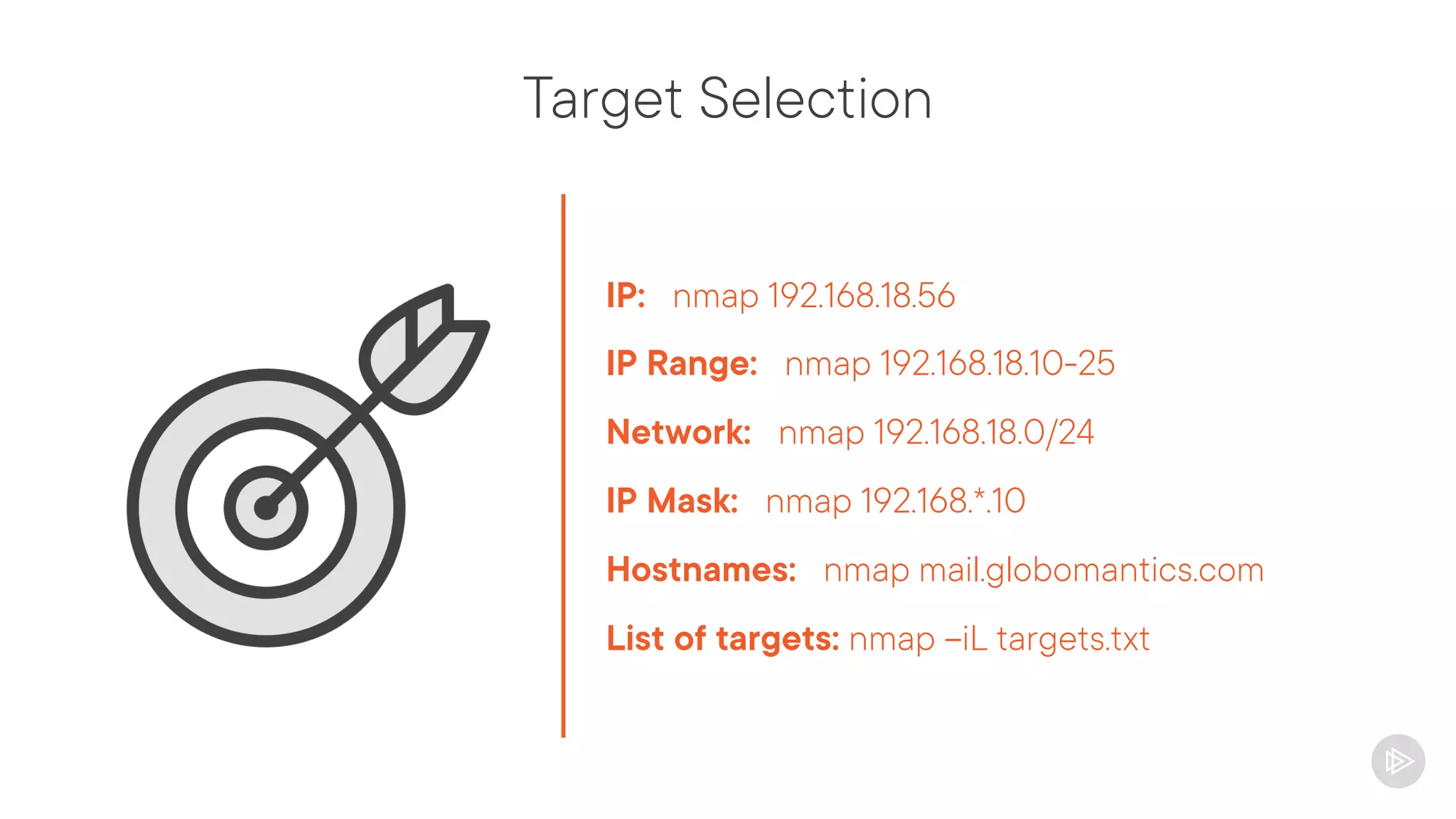
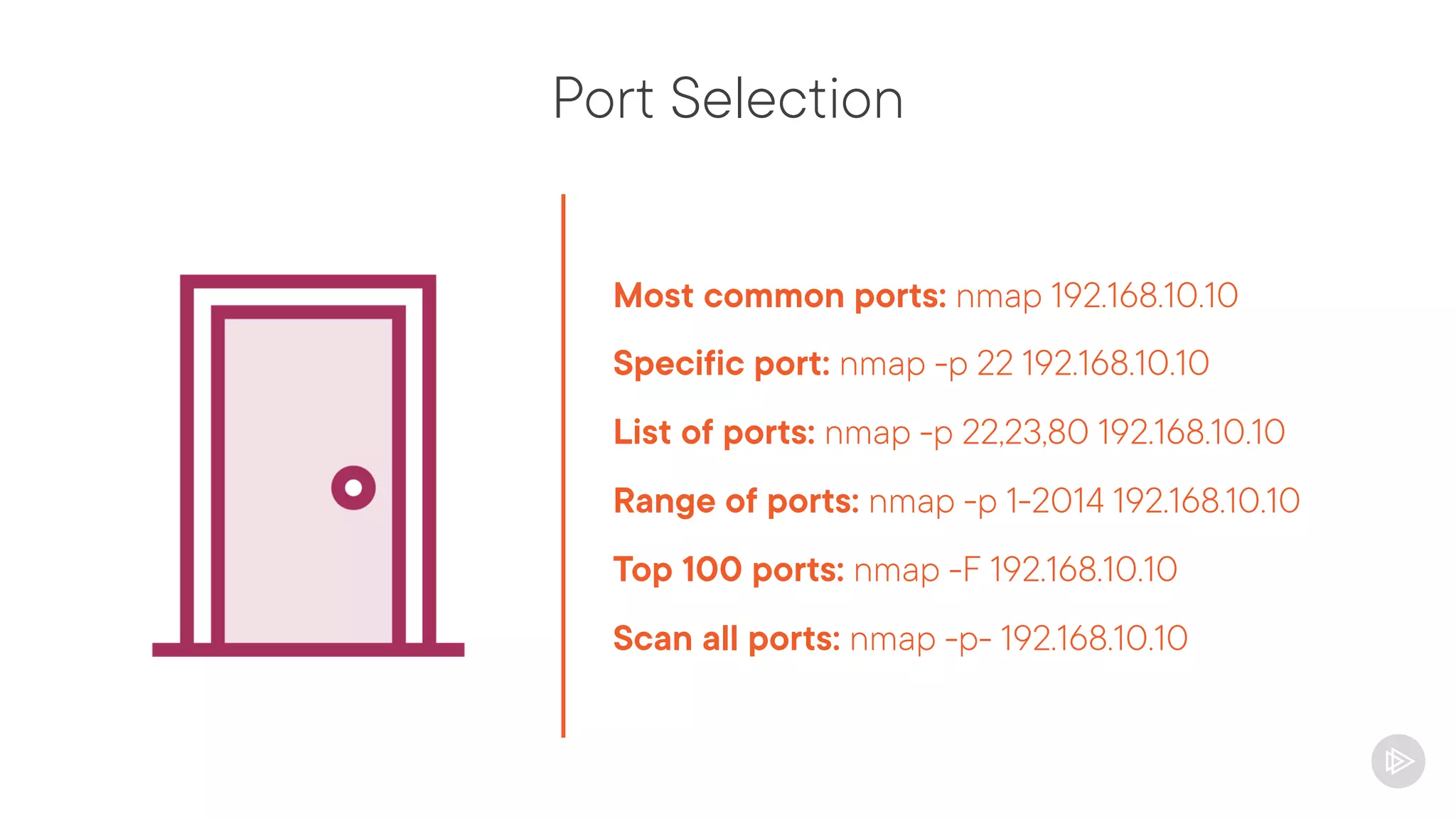
This document provides an overview of information gathering and vulnerability scanning techniques for the CompTIA Pentest+ certification. It discusses the importance of gathering both technical and people information about the target. It covers passive information gathering techniques like searching public databases and active techniques like port scanning and website crawling. The document demonstrates tools for discovering domains, IP addresses, ports, services and technical details through techniques like DNS queries, Nmap scanning, and using search engines and Shodan. It emphasizes using both passive and active approaches to fully map the target environment.













![Nmap Command Structure
$ nmap <OPTIONS> [TARGET]
$ nmap 10.10.56.18
$ nmap -p 21,22,80,443 10.10.56.0/24](https://image.slidesharecdn.com/technical-information-gathering-slides-221003141717-3873285f/75/technical-information-gathering-slides-pdf-48-2048.jpg)
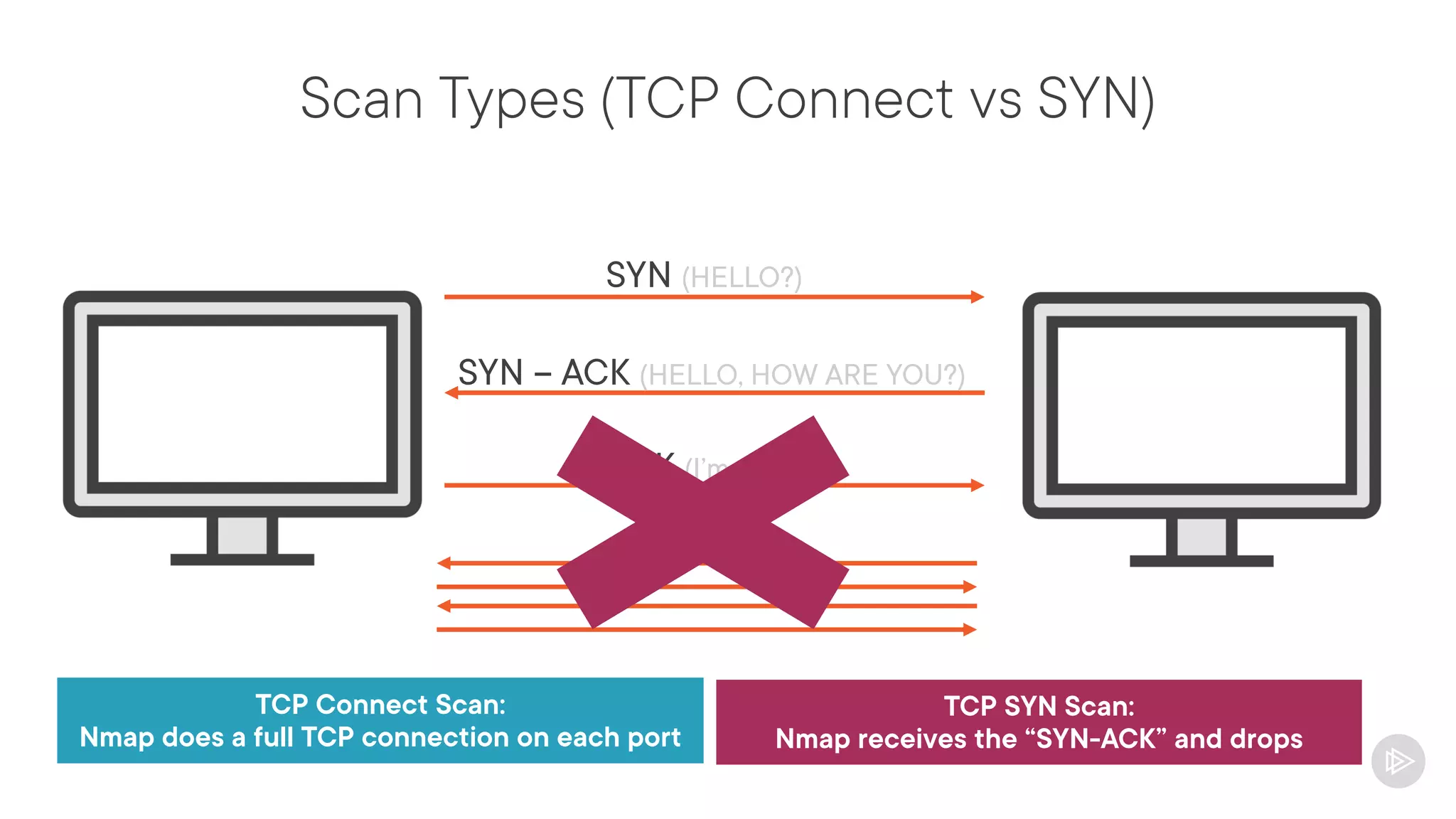
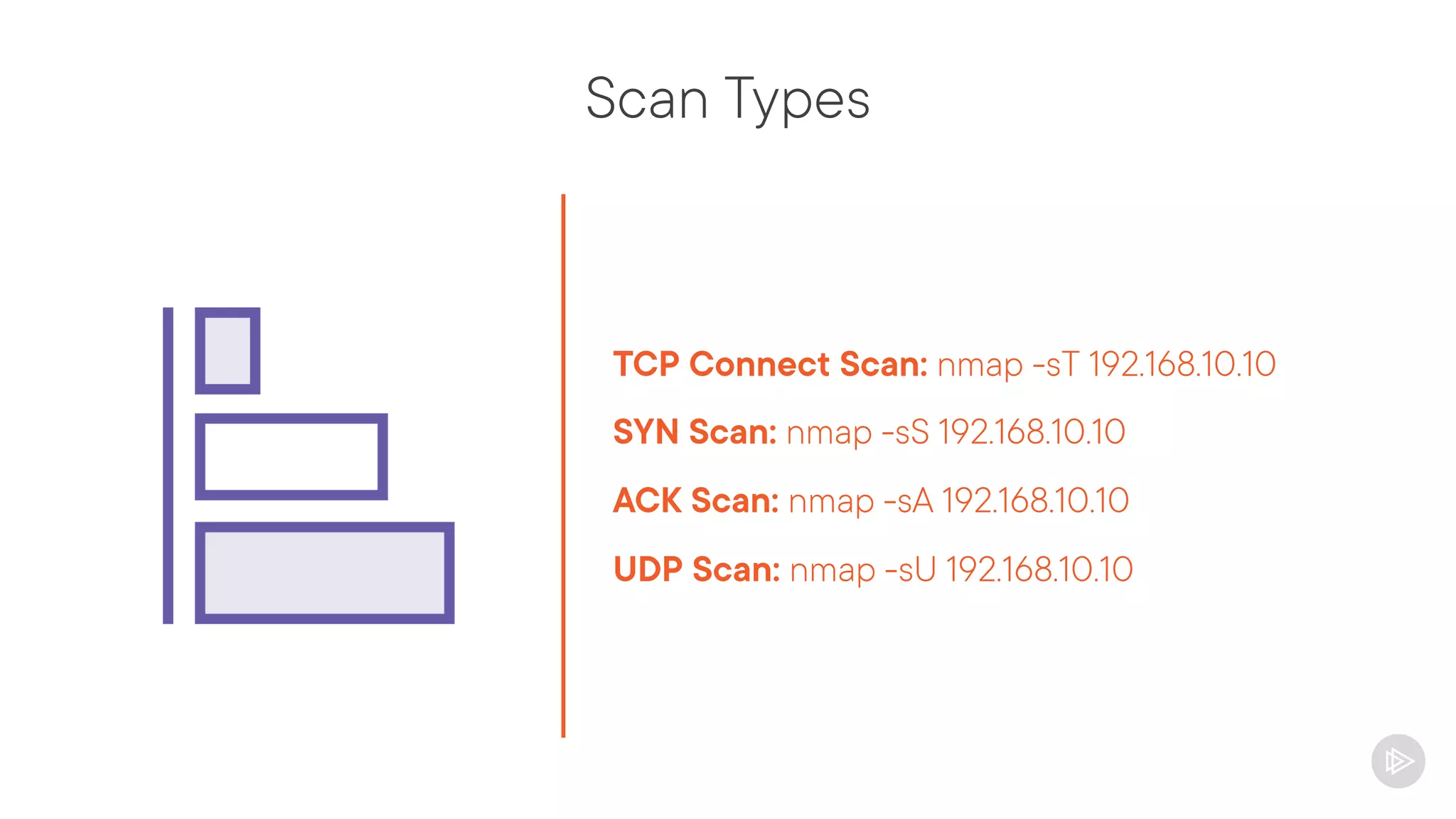
![Output Formats
Normal output:
nmap 192.168.10.10 -oN result.nmap
XML output:
nmap 192.168.10.10 -oX result.xml
Grepable output:
nmap 192.168.10.10 -oG | grep [string]
Output all types:
nmap 192.168.10.10 -oA result
[result.nmap, result.xml and result.gnmap]](https://image.slidesharecdn.com/technical-information-gathering-slides-221003141717-3873285f/75/technical-information-gathering-slides-pdf-53-2048.jpg)
![Timing Options
Setting scan speed:
nmap –T [0-5] 192.168.10.10
Slow:0, Fast 5, Default: 3
Delay between probes:
nmap --scan-delay 5 192.168.10.10](https://image.slidesharecdn.com/technical-information-gathering-slides-221003141717-3873285f/75/technical-information-gathering-slides-pdf-54-2048.jpg)