What are Honeypots? and how are they deployed?
•
0 likes•1,183 views
This is a full beginners guide on Honeypots , we will be explaining the types of Honeypots, how are they deployed, who uses them, and so on.
Report
Share
Report
Share
Download to read offline
Recommended
Honeypot a trap to hackers

A presentation on Honeypot technique which are used to track the hacker's movement
HONEYPOTS: Definition, working, advantages, disadvantages

introduction of HONEYPOTS and comparison with some other security techniques
Honeypot2

Honey pots are generally based on a real server, real operating system, and with data that appears to be real. One of the main differences is the location of the machine in relation to the actual servers. The most important activity of a honeypot is to capture the data, the ability to log, alert, and capture everything the bad guy is doing. Most honeypot solutions, such as Honeyd or Specter, have their own logging and alerting capabilities. This gathered information can prove to be quiet critical against the attacker. Honeypots only see activities that interact with them and do not capture attack, directed against other existing systems.
Risk of being compromised: A Honeypot may be used as a platform to launch further attacks.
At the end it would not be wrong to say that honeypots are good resources to track attackers, and its value lies in being attacked. But at the same time due to the listed disadvantages above Honeypots cannot replace any security mechanisms; they can only work to enhance the overall security.
Recommended
Honeypot a trap to hackers

A presentation on Honeypot technique which are used to track the hacker's movement
HONEYPOTS: Definition, working, advantages, disadvantages

introduction of HONEYPOTS and comparison with some other security techniques
Honeypot2

Honey pots are generally based on a real server, real operating system, and with data that appears to be real. One of the main differences is the location of the machine in relation to the actual servers. The most important activity of a honeypot is to capture the data, the ability to log, alert, and capture everything the bad guy is doing. Most honeypot solutions, such as Honeyd or Specter, have their own logging and alerting capabilities. This gathered information can prove to be quiet critical against the attacker. Honeypots only see activities that interact with them and do not capture attack, directed against other existing systems.
Risk of being compromised: A Honeypot may be used as a platform to launch further attacks.
At the end it would not be wrong to say that honeypots are good resources to track attackers, and its value lies in being attacked. But at the same time due to the listed disadvantages above Honeypots cannot replace any security mechanisms; they can only work to enhance the overall security.
Honeypots

It deals with and explores the fascinating world of Honey pots.
It describes a security tool and concept known as a Honey pot and Honeynet.
Honey Pots and Honeynets are digital network bait, and through deception, they are designed to actually attract intruders.
www.presentationslive.blogspot.com
Honeypots

Honeypots are information system resources whose value lie in illicit use of them.In simple words, they are a trap to track the ways in which a hacker can can attack a valuable resource to extract information from it.
Seminar Report on Honeypot

This is a Seminar Report on a computer security mechanism named Honeypot. In this I've included Honeypot Basics, Types, Value, Implementation, Merits & Demerits, Legal issues and Future of Honeypots.
Honey pots

A Honey Pot is an intrusion (unwanted) detection technique used to study hacker movement and interested to help better system defences against later attacks usually made up of a virtual machine that sits on a network or single client.
Honey po tppt

Honeypot is a trap set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems.
Honeynet architecture

Honeynet architecture and attacks on different OS and tracking the attacks using honeymap.
Honeypot Basics

This ppt contains all the basics of honeypots like their types, implementation technologies, position in the network etc.
In the end, it contains a screenshot of a live honeypot processing.
Tushar mandal.honeypot

this honeypot slide teells u everything what is basically honeypot and easily understable to every oney. hope u enjoy this presentation,.
honey pots introduction and its types

presentation includes introduction of honeypot. With evaluation and different types of honeypots including the low interaction and high interaction.
OpenMetadata Community Meeting - 5th June 2024

The OpenMetadata Community Meeting was held on June 5th, 2024. In this meeting, we discussed about the data quality capabilities that are integrated with the Incident Manager, providing a complete solution to handle your data observability needs. Watch the end-to-end demo of the data quality features.
* How to run your own data quality framework
* What is the performance impact of running data quality frameworks
* How to run the test cases in your own ETL pipelines
* How the Incident Manager is integrated
* Get notified with alerts when test cases fail
Watch the meeting recording here - https://www.youtube.com/watch?v=UbNOje0kf6E
Prosigns: Transforming Business with Tailored Technology Solutions

Unlocking Business Potential: Tailored Technology Solutions by Prosigns
Discover how Prosigns, a leading technology solutions provider, partners with businesses to drive innovation and success. Our presentation showcases our comprehensive range of services, including custom software development, web and mobile app development, AI & ML solutions, blockchain integration, DevOps services, and Microsoft Dynamics 365 support.
Custom Software Development: Prosigns specializes in creating bespoke software solutions that cater to your unique business needs. Our team of experts works closely with you to understand your requirements and deliver tailor-made software that enhances efficiency and drives growth.
Web and Mobile App Development: From responsive websites to intuitive mobile applications, Prosigns develops cutting-edge solutions that engage users and deliver seamless experiences across devices.
AI & ML Solutions: Harnessing the power of Artificial Intelligence and Machine Learning, Prosigns provides smart solutions that automate processes, provide valuable insights, and drive informed decision-making.
Blockchain Integration: Prosigns offers comprehensive blockchain solutions, including development, integration, and consulting services, enabling businesses to leverage blockchain technology for enhanced security, transparency, and efficiency.
DevOps Services: Prosigns' DevOps services streamline development and operations processes, ensuring faster and more reliable software delivery through automation and continuous integration.
Microsoft Dynamics 365 Support: Prosigns provides comprehensive support and maintenance services for Microsoft Dynamics 365, ensuring your system is always up-to-date, secure, and running smoothly.
Learn how our collaborative approach and dedication to excellence help businesses achieve their goals and stay ahead in today's digital landscape. From concept to deployment, Prosigns is your trusted partner for transforming ideas into reality and unlocking the full potential of your business.
Join us on a journey of innovation and growth. Let's partner for success with Prosigns.
More Related Content
What's hot
Honeypots

It deals with and explores the fascinating world of Honey pots.
It describes a security tool and concept known as a Honey pot and Honeynet.
Honey Pots and Honeynets are digital network bait, and through deception, they are designed to actually attract intruders.
www.presentationslive.blogspot.com
Honeypots

Honeypots are information system resources whose value lie in illicit use of them.In simple words, they are a trap to track the ways in which a hacker can can attack a valuable resource to extract information from it.
Seminar Report on Honeypot

This is a Seminar Report on a computer security mechanism named Honeypot. In this I've included Honeypot Basics, Types, Value, Implementation, Merits & Demerits, Legal issues and Future of Honeypots.
Honey pots

A Honey Pot is an intrusion (unwanted) detection technique used to study hacker movement and interested to help better system defences against later attacks usually made up of a virtual machine that sits on a network or single client.
Honey po tppt

Honeypot is a trap set to detect, deflect, or, in some manner, counteract attempts at unauthorized use of information systems.
Honeynet architecture

Honeynet architecture and attacks on different OS and tracking the attacks using honeymap.
Honeypot Basics

This ppt contains all the basics of honeypots like their types, implementation technologies, position in the network etc.
In the end, it contains a screenshot of a live honeypot processing.
Tushar mandal.honeypot

this honeypot slide teells u everything what is basically honeypot and easily understable to every oney. hope u enjoy this presentation,.
honey pots introduction and its types

presentation includes introduction of honeypot. With evaluation and different types of honeypots including the low interaction and high interaction.
What's hot (20)
Recently uploaded
OpenMetadata Community Meeting - 5th June 2024

The OpenMetadata Community Meeting was held on June 5th, 2024. In this meeting, we discussed about the data quality capabilities that are integrated with the Incident Manager, providing a complete solution to handle your data observability needs. Watch the end-to-end demo of the data quality features.
* How to run your own data quality framework
* What is the performance impact of running data quality frameworks
* How to run the test cases in your own ETL pipelines
* How the Incident Manager is integrated
* Get notified with alerts when test cases fail
Watch the meeting recording here - https://www.youtube.com/watch?v=UbNOje0kf6E
Prosigns: Transforming Business with Tailored Technology Solutions

Unlocking Business Potential: Tailored Technology Solutions by Prosigns
Discover how Prosigns, a leading technology solutions provider, partners with businesses to drive innovation and success. Our presentation showcases our comprehensive range of services, including custom software development, web and mobile app development, AI & ML solutions, blockchain integration, DevOps services, and Microsoft Dynamics 365 support.
Custom Software Development: Prosigns specializes in creating bespoke software solutions that cater to your unique business needs. Our team of experts works closely with you to understand your requirements and deliver tailor-made software that enhances efficiency and drives growth.
Web and Mobile App Development: From responsive websites to intuitive mobile applications, Prosigns develops cutting-edge solutions that engage users and deliver seamless experiences across devices.
AI & ML Solutions: Harnessing the power of Artificial Intelligence and Machine Learning, Prosigns provides smart solutions that automate processes, provide valuable insights, and drive informed decision-making.
Blockchain Integration: Prosigns offers comprehensive blockchain solutions, including development, integration, and consulting services, enabling businesses to leverage blockchain technology for enhanced security, transparency, and efficiency.
DevOps Services: Prosigns' DevOps services streamline development and operations processes, ensuring faster and more reliable software delivery through automation and continuous integration.
Microsoft Dynamics 365 Support: Prosigns provides comprehensive support and maintenance services for Microsoft Dynamics 365, ensuring your system is always up-to-date, secure, and running smoothly.
Learn how our collaborative approach and dedication to excellence help businesses achieve their goals and stay ahead in today's digital landscape. From concept to deployment, Prosigns is your trusted partner for transforming ideas into reality and unlocking the full potential of your business.
Join us on a journey of innovation and growth. Let's partner for success with Prosigns.
Climate Science Flows: Enabling Petabyte-Scale Climate Analysis with the Eart...

The Earth System Grid Federation (ESGF) is a global network of data servers that archives and distributes the planet’s largest collection of Earth system model output for thousands of climate and environmental scientists worldwide. Many of these petabyte-scale data archives are located in proximity to large high-performance computing (HPC) or cloud computing resources, but the primary workflow for data users consists of transferring data, and applying computations on a different system. As a part of the ESGF 2.0 US project (funded by the United States Department of Energy Office of Science), we developed pre-defined data workflows, which can be run on-demand, capable of applying many data reduction and data analysis to the large ESGF data archives, transferring only the resultant analysis (ex. visualizations, smaller data files). In this talk, we will showcase a few of these workflows, highlighting how Globus Flows can be used for petabyte-scale climate analysis.
A Sighting of filterA in Typelevel Rite of Passage

Slide deck home: https://fpilluminated.com/deck/220
Automated software refactoring with OpenRewrite and Generative AI.pptx.pdf

https://2024.springio.net/sessions/automated-software-refactoring-with-openrewrite-and-generative-ai/
Globus Connect Server Deep Dive - GlobusWorld 2024

We explore the Globus Connect Server (GCS) architecture and experiment with advanced configuration options and use cases. This content is targeted at system administrators who are familiar with GCS and currently operate—or are planning to operate—broader deployments at their institution.
Enhancing Research Orchestration Capabilities at ORNL.pdf

Cross-facility research orchestration comes with ever-changing constraints regarding the availability and suitability of various compute and data resources. In short, a flexible data and processing fabric is needed to enable the dynamic redirection of data and compute tasks throughout the lifecycle of an experiment. In this talk, we illustrate how we easily leveraged Globus services to instrument the ACE research testbed at the Oak Ridge Leadership Computing Facility with flexible data and task orchestration capabilities.
Gamify Your Mind; The Secret Sauce to Delivering Success, Continuously Improv...

Games are powerful teaching tools, fostering hands-on engagement and fun. But they require careful consideration to succeed. Join me to explore factors in running and selecting games, ensuring they serve as effective teaching tools. Learn to maintain focus on learning objectives while playing, and how to measure the ROI of gaming in education. Discover strategies for pitching gaming to leadership. This session offers insights, tips, and examples for coaches, team leads, and enterprise leaders seeking to teach from simple to complex concepts.
Atelier - Innover avec l’IA Générative et les graphes de connaissances

Atelier - Innover avec l’IA Générative et les graphes de connaissances
Allez au-delà du battage médiatique autour de l’IA et découvrez des techniques pratiques pour utiliser l’IA de manière responsable à travers les données de votre organisation. Explorez comment utiliser les graphes de connaissances pour augmenter la précision, la transparence et la capacité d’explication dans les systèmes d’IA générative. Vous partirez avec une expérience pratique combinant les relations entre les données et les LLM pour apporter du contexte spécifique à votre domaine et améliorer votre raisonnement.
Amenez votre ordinateur portable et nous vous guiderons sur la mise en place de votre propre pile d’IA générative, en vous fournissant des exemples pratiques et codés pour démarrer en quelques minutes.
Lecture 1 Introduction to games development

Software engineering
Game Development
unity Game Development
Top 7 Unique WhatsApp API Benefits | Saudi Arabia

Discover the transformative power of the WhatsApp API in our latest SlideShare presentation, "Top 7 Unique WhatsApp API Benefits." In today's fast-paced digital era, effective communication is crucial for both personal and professional success. Whether you're a small business looking to enhance customer interactions or an individual seeking seamless communication with loved ones, the WhatsApp API offers robust capabilities that can significantly elevate your experience.
In this presentation, we delve into the top 7 distinctive benefits of the WhatsApp API, provided by the leading WhatsApp API service provider in Saudi Arabia. Learn how to streamline customer support, automate notifications, leverage rich media messaging, run scalable marketing campaigns, integrate secure payments, synchronize with CRM systems, and ensure enhanced security and privacy.
openEuler Case Study - The Journey to Supply Chain Security

openEuler Case Study - The Journey to Supply Chain Security
Webinar: Salesforce Document Management 2.0 - Smarter, Faster, Better

Check out the webinar slides to learn more about how XfilesPro transforms Salesforce document management by leveraging its world-class applications. For more details, please connect with sales@xfilespro.com
If you want to watch the on-demand webinar, please click here: https://www.xfilespro.com/webinars/salesforce-document-management-2-0-smarter-faster-better/
Understanding Globus Data Transfers with NetSage

NetSage is an open privacy-aware network measurement, analysis, and visualization service designed to help end-users visualize and reason about large data transfers. NetSage traditionally has used a combination of passive measurements, including SNMP and flow data, as well as active measurements, mainly perfSONAR, to provide longitudinal network performance data visualization. It has been deployed by dozens of networks world wide, and is supported domestically by the Engagement and Performance Operations Center (EPOC), NSF #2328479. We have recently expanded the NetSage data sources to include logs for Globus data transfers, following the same privacy-preserving approach as for Flow data. Using the logs for the Texas Advanced Computing Center (TACC) as an example, this talk will walk through several different example use cases that NetSage can answer, including: Who is using Globus to share data with my institution, and what kind of performance are they able to achieve? How many transfers has Globus supported for us? Which sites are we sharing the most data with, and how is that changing over time? How is my site using Globus to move data internally, and what kind of performance do we see for those transfers? What percentage of data transfers at my institution used Globus, and how did the overall data transfer performance compare to the Globus users?
May Marketo Masterclass, London MUG May 22 2024.pdf

Can't make Adobe Summit in Vegas? No sweat because the EMEA Marketo Engage Champions are coming to London to share their Summit sessions, insights and more!
This is a MUG with a twist you don't want to miss.
Vitthal Shirke Java Microservices Resume.pdf

Software Engineering, Software Consulting, Tech Lead, Spring Boot, Spring Cloud, Spring Core, Spring JDBC, Spring Transaction, Spring MVC, OpenShift Cloud Platform, Kafka, REST, SOAP, LLD & HLD.
Cracking the code review at SpringIO 2024

Code reviews are vital for ensuring good code quality. They serve as one of our last lines of defense against bugs and subpar code reaching production.
Yet, they often turn into annoying tasks riddled with frustration, hostility, unclear feedback and lack of standards. How can we improve this crucial process?
In this session we will cover:
- The Art of Effective Code Reviews
- Streamlining the Review Process
- Elevating Reviews with Automated Tools
By the end of this presentation, you'll have the knowledge on how to organize and improve your code review proces
Quarkus Hidden and Forbidden Extensions

Quarkus has a vast extension ecosystem and is known for its subsonic and subatomic feature set. Some of these features are not as well known, and some extensions are less talked about, but that does not make them less interesting - quite the opposite.
Come join this talk to see some tips and tricks for using Quarkus and some of the lesser known features, extensions and development techniques.
2024 RoOUG Security model for the cloud.pptx

How we've evolved the MySQL server security model from a single DBA to the cloud.
Large Language Models and the End of Programming

Talk by Matt Welsh at Craft Conference 2024 on the impact that Large Language Models will have on the future of software development. In this talk, I discuss the ways in which LLMs will impact the software industry, from replacing human software developers with AI, to replacing conventional software with models that perform reasoning, computation, and problem-solving.
Recently uploaded (20)
Prosigns: Transforming Business with Tailored Technology Solutions

Prosigns: Transforming Business with Tailored Technology Solutions
Climate Science Flows: Enabling Petabyte-Scale Climate Analysis with the Eart...

Climate Science Flows: Enabling Petabyte-Scale Climate Analysis with the Eart...
A Sighting of filterA in Typelevel Rite of Passage

A Sighting of filterA in Typelevel Rite of Passage
Automated software refactoring with OpenRewrite and Generative AI.pptx.pdf

Automated software refactoring with OpenRewrite and Generative AI.pptx.pdf
Globus Connect Server Deep Dive - GlobusWorld 2024

Globus Connect Server Deep Dive - GlobusWorld 2024
Enhancing Research Orchestration Capabilities at ORNL.pdf

Enhancing Research Orchestration Capabilities at ORNL.pdf
Gamify Your Mind; The Secret Sauce to Delivering Success, Continuously Improv...

Gamify Your Mind; The Secret Sauce to Delivering Success, Continuously Improv...
Atelier - Innover avec l’IA Générative et les graphes de connaissances

Atelier - Innover avec l’IA Générative et les graphes de connaissances
openEuler Case Study - The Journey to Supply Chain Security

openEuler Case Study - The Journey to Supply Chain Security
Webinar: Salesforce Document Management 2.0 - Smarter, Faster, Better

Webinar: Salesforce Document Management 2.0 - Smarter, Faster, Better
May Marketo Masterclass, London MUG May 22 2024.pdf

May Marketo Masterclass, London MUG May 22 2024.pdf
What are Honeypots? and how are they deployed?
- 1. Honey Pots Hussein Muhaisen AKA System Exploited 1 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 2. What are honey pots? •Honey pots are basically decoy ( fake ) systems deployed by people , organizations and other entities to log user activity and the way they approach the system to hack it or do any other activity on it. 2 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
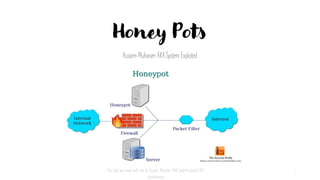
- 3. Honey pot illustration 3 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 4. why are honey pots deployed? •The simple answer is that honey pots are deployed for people/orgs to study how an attacker behaves , examine his moves, and sometimes they are deployed for other uses like confusing the attacker. 4 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 5. A basic working of a honeypot •Logs users' IP address. •Keystrokes submitted by the user. •The resources the user has accessed, modified, and deleted. •and a lot of other things! Really , you can configure your honeypot to act based on your needs 5 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 6. Types of honeypots •Low-interaction honeypots. •Medium-interaction honeypots. •High-interaction honeypots. •Pure honeypots. 6 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 7. Low-Interaction Honeypots •These types of honeypots run on limited services , and have restricted permissions, they can be used to track UDP,TCP,IICMP and other protocols/services . 7 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 8. Medium-Interaction Honeypots •These types of honeypots are based on real-time functioning operating systems they have the same services as the real application, the purpose of this honey pot is to collect more information on the attack, and so the organization can take extra time when mitigating the attack. 8 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 9. High-Interaction Honeypots •These types of honeypots are real applications but they are vulnerable, these are hard to maintain but the success rates are high. 9 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 10. Pure Honeypots •These honeypots are deployed on real working environments ! Yes real ones, so once the attacker sees it he will directly spend time enumerating and epxloiting it once he does the organization will be alerted, and like that they knew the attackers ways of attacking the machine, and they will prevent future attacks like this. 10 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 11. Honey pots deployments Honey pots have different types and these types are: Email Honeypots --> Inactive emails waiting for the malicious actor to send an email, then later analyze the malicious email sent by the attacker. Malware Honeypots --> used to trap malware in the network, then later analyzed by the ORG. Database Honeypots --> these honeypots act as a vulnerable database which lures attackers into thinking the database is vulnerable and it has credit cards for example. Spider Honeypots --> these Honeypots are used to stop web crawlers that crawl the internet for a certain malicious purpose. 11 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 12. How to setup honeypots • By the timeyou see this I Will have a video uploaded on my channel on how to do it youtube.com/SystemExploited So these are honeypots you can download: - DigitalOcean offers a honeypot service - Cowrie - HoneyPy - Honeynet - Honeytrap -Specter -KFsensor This is a curated list of honeypots https://github.com/paralax/awesome-honeypots 12 This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein
- 13. This slide was made with love by Hussein Muhaisen AKA SystemExploited AKA atoncehussein 13