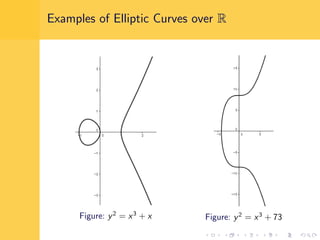
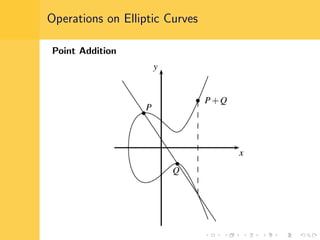
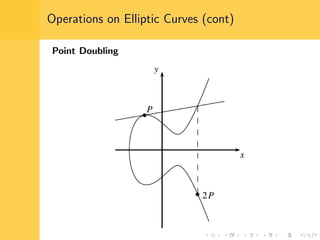
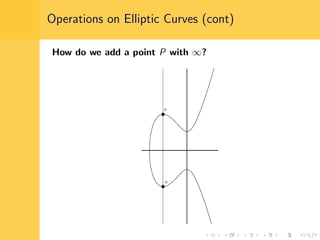
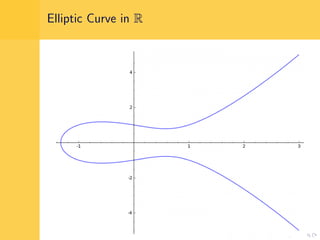
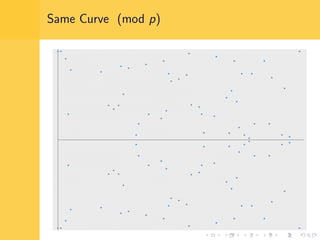
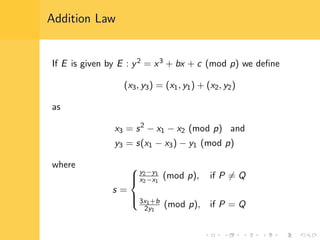
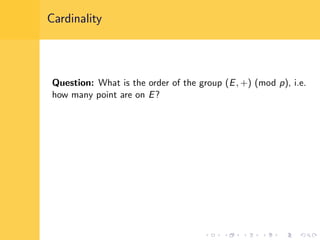
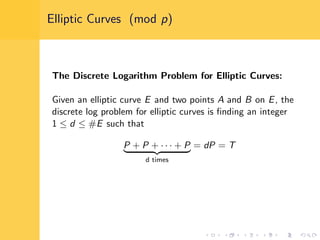
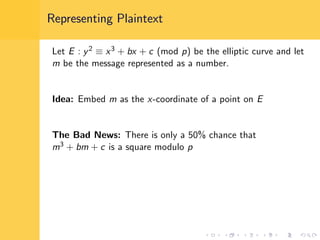
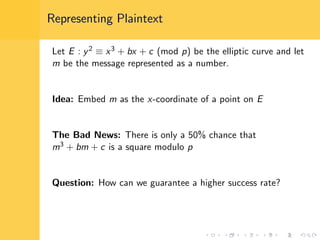
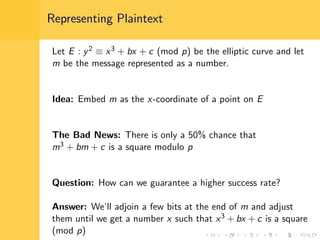
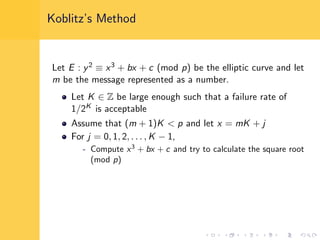
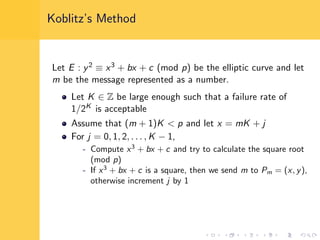
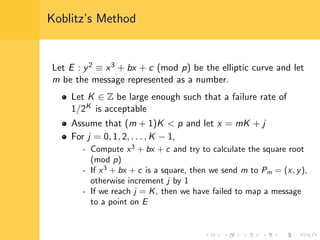
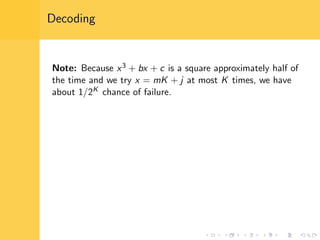
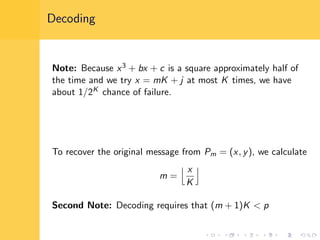
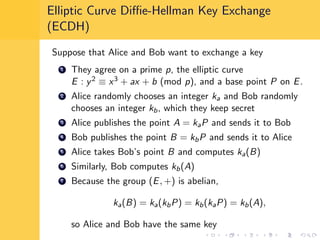
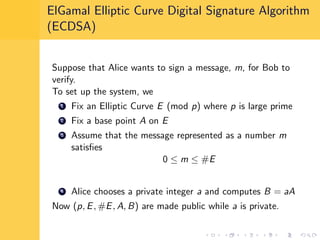
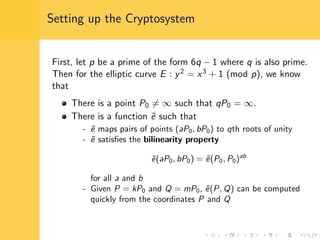
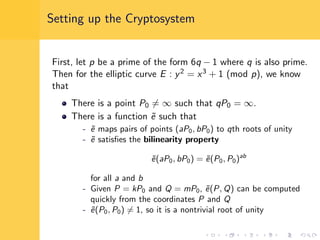
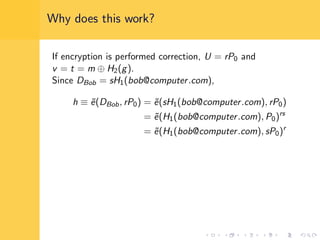
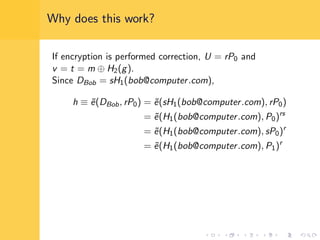
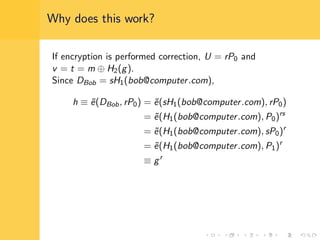
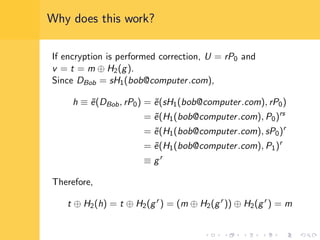
Elliptic curve cryptography (ECC) uses elliptic curves over finite fields for encryption, digital signatures, and key exchange. It provides the same security as RSA or discrete logarithm schemes but with smaller key sizes (e.g. 256-bit ECC vs. 3072-bit RSA). ECC algorithms are also faster and use less energy than other schemes. While ECC offers advantages, security relies on using cryptographically strong elliptic curves and there is no deterministic method to encode messages as curve points.