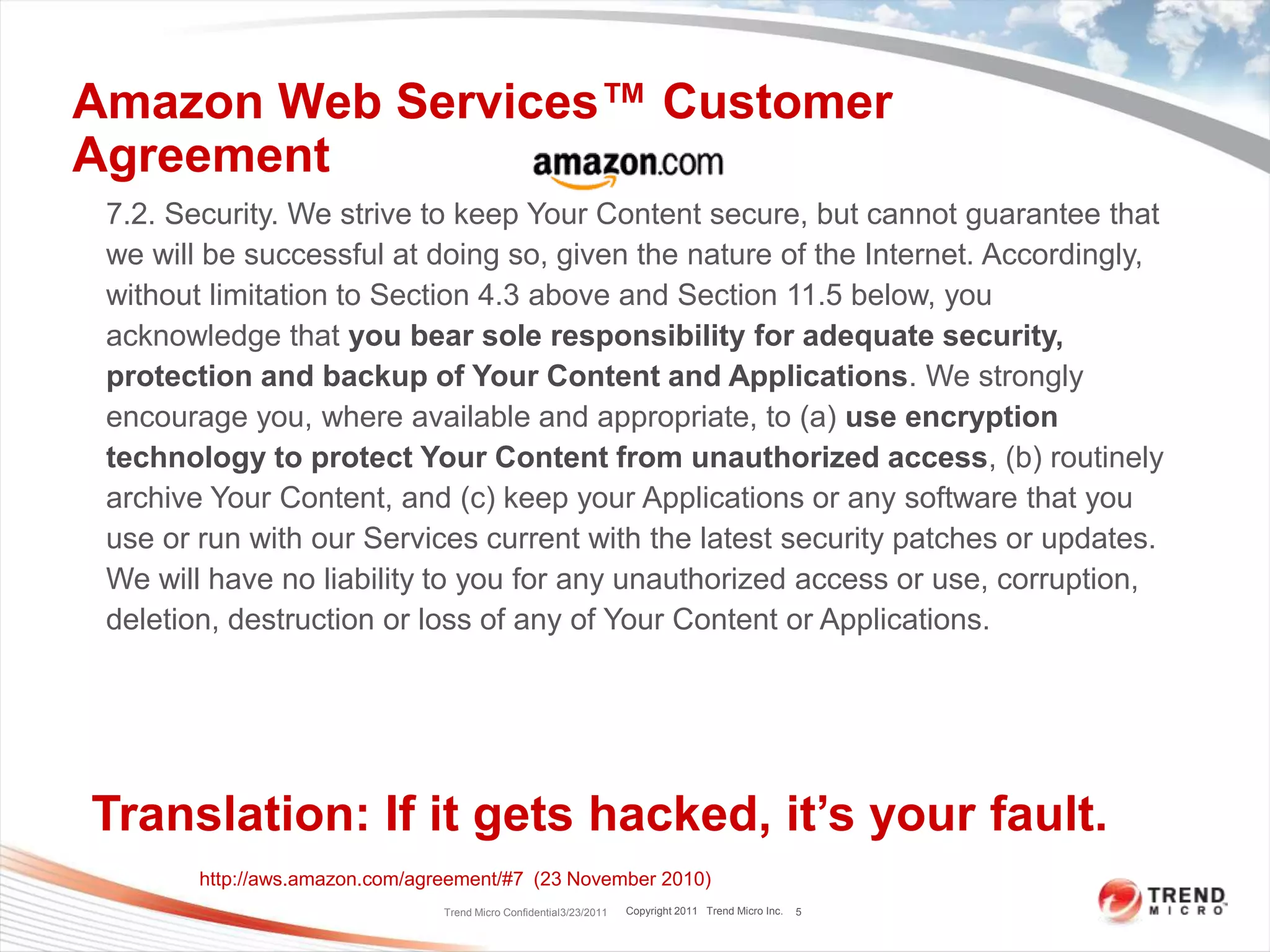
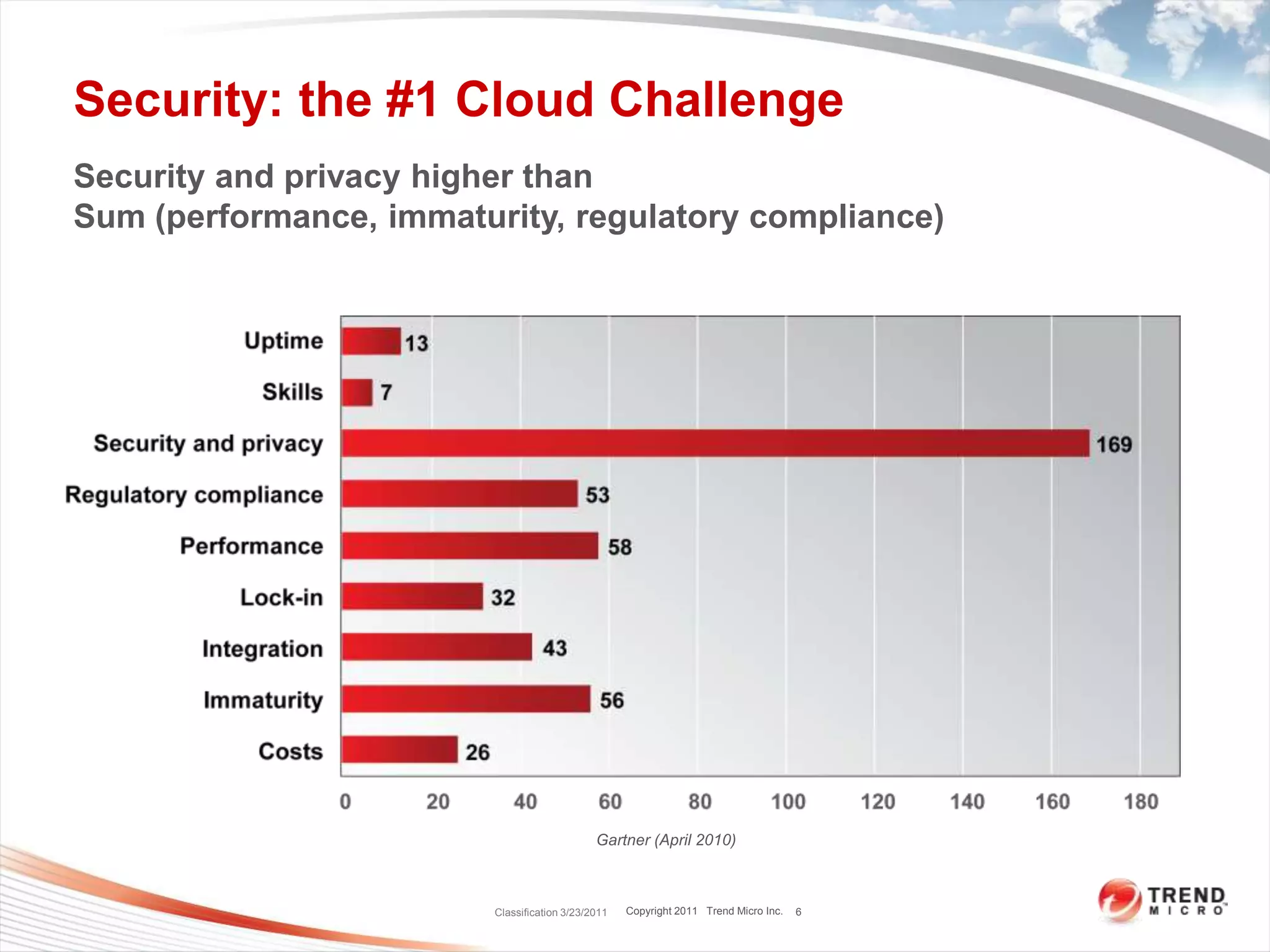
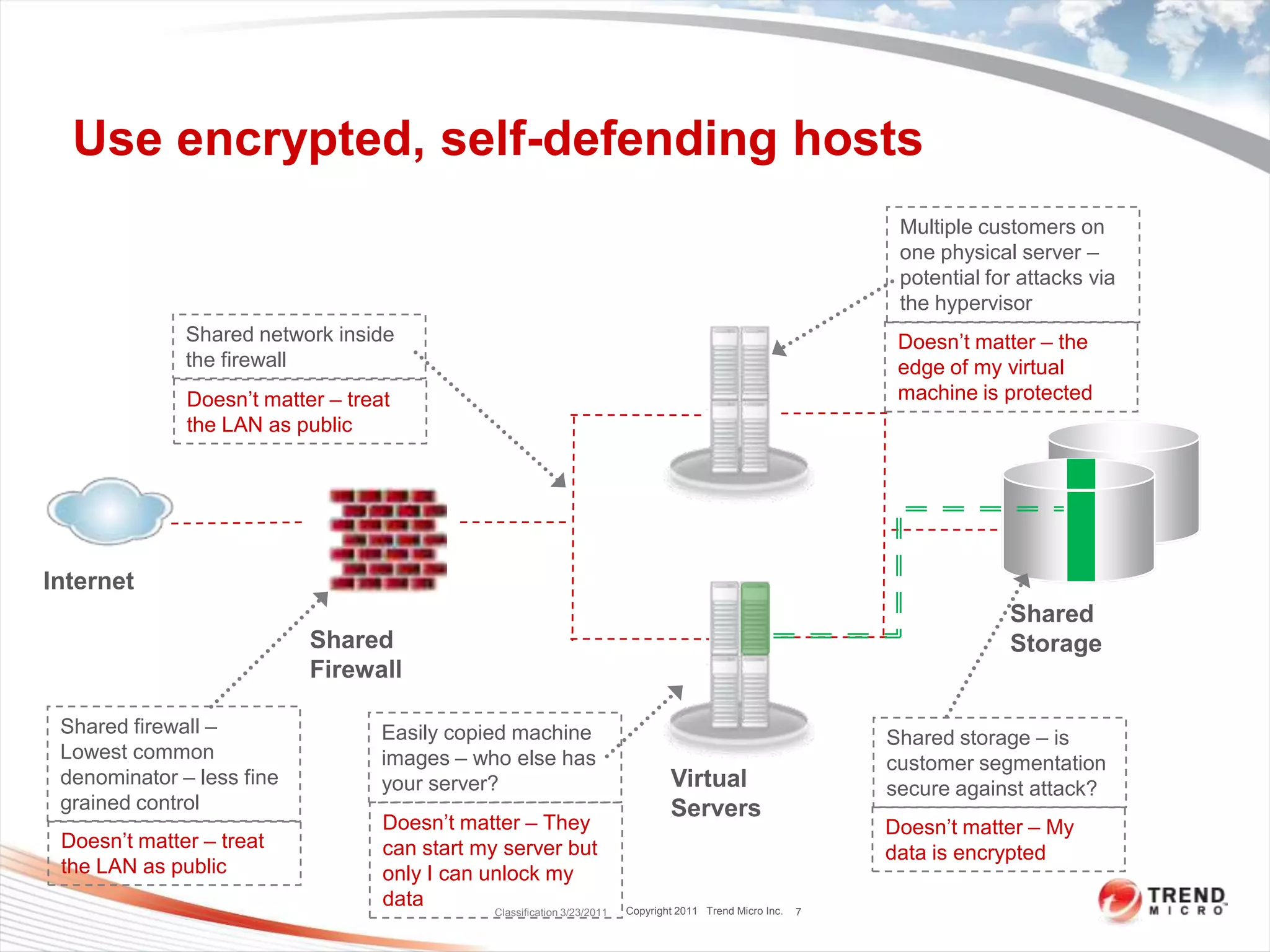
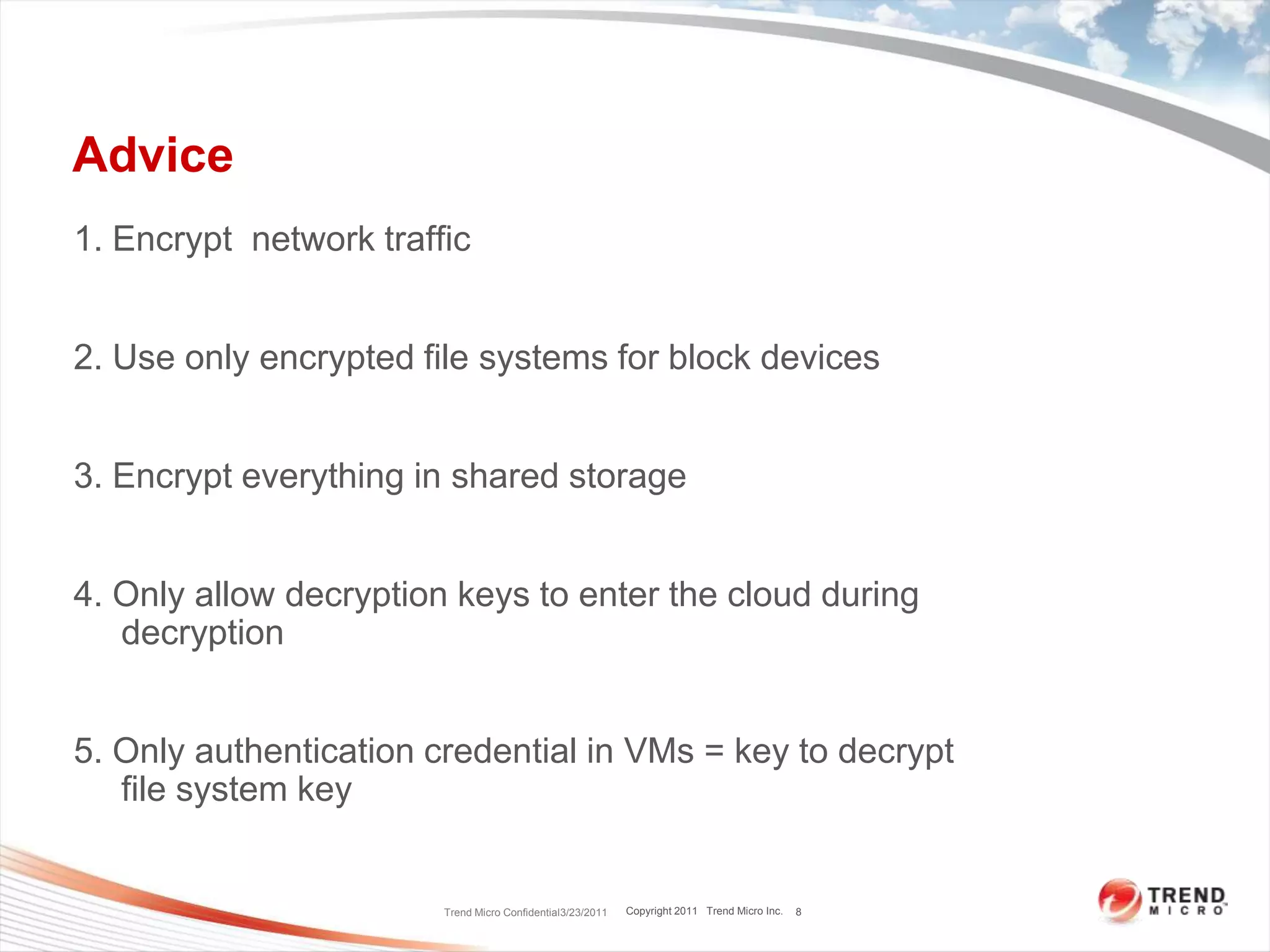
Dave Asprey, VP of Cloud Security at Trend Micro, presented on encryption techniques for securing data and applications in public clouds. He outlined 16 pieces of advice, including encrypting network traffic, files systems, and data in shared storage. Only allow decryption keys to enter the cloud during decryption. Minimize the number of services per virtual machine instance and only open necessary ports. Use host-based intrusion detection and system hardening tools.