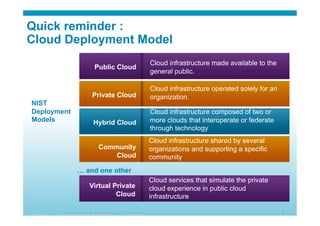
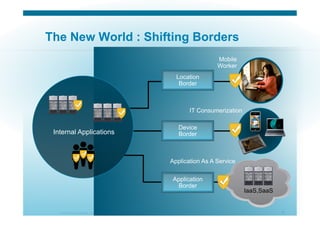
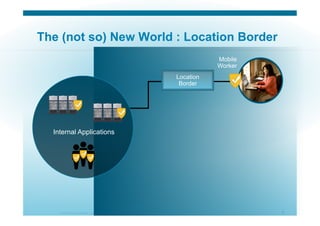
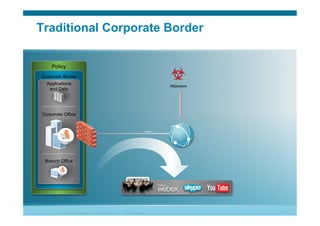
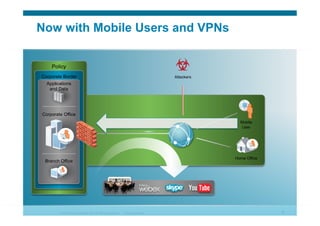
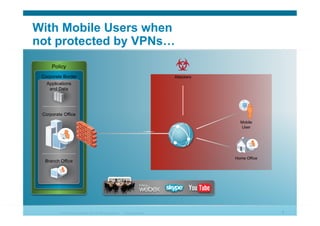
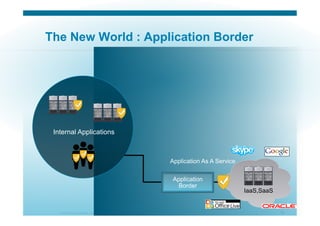
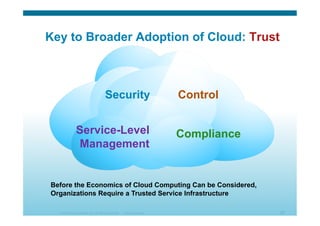
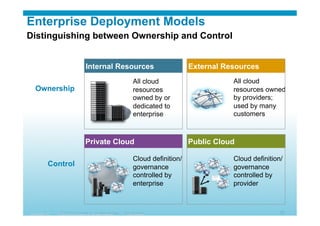
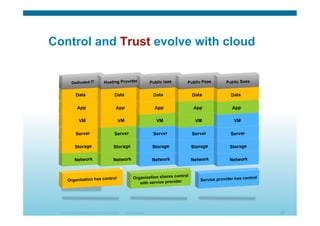
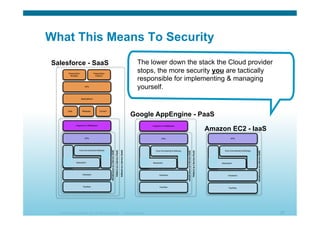
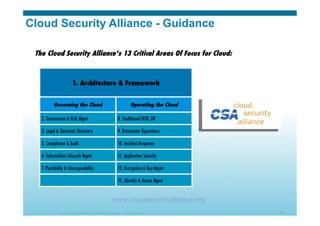
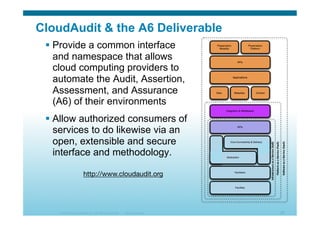
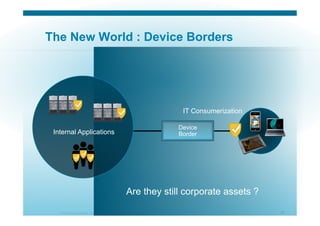
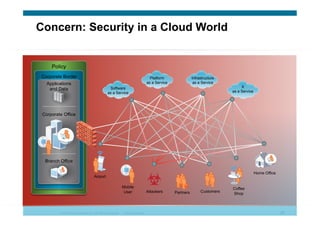
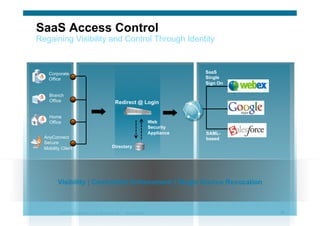
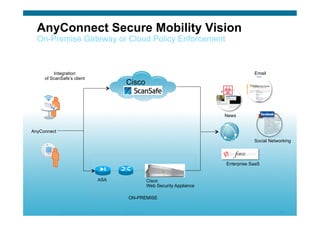
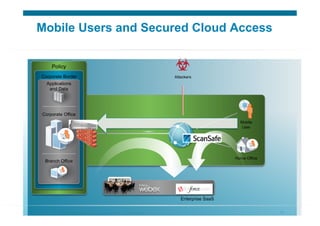
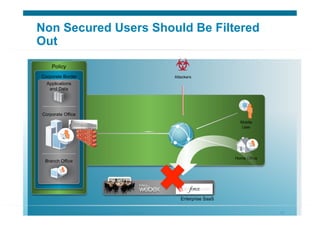
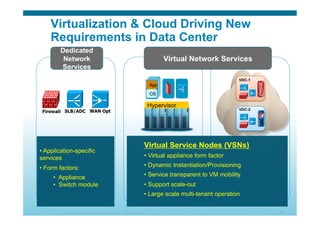
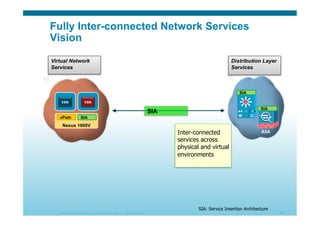
The document discusses various aspects of cloud security, focusing on the differences between public and private cloud models, including their security approaches. It highlights the need for trust, control, and compliance in cloud services, emphasizing that organizations may face risks due to unmanaged cloud services and the outsourcing of critical processes. Furthermore, it outlines key recommendations for improving security and managing risks in cloud environments.