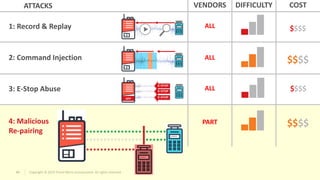
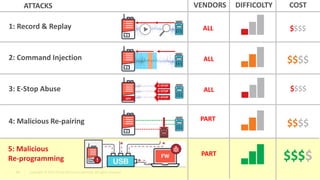
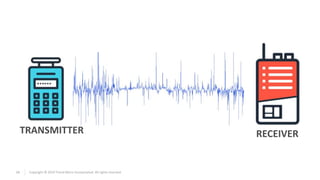
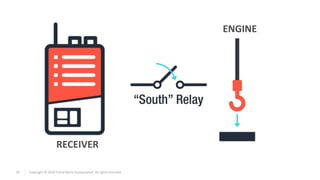
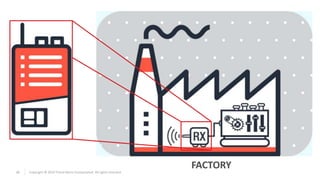
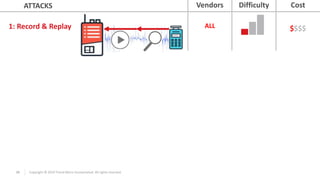
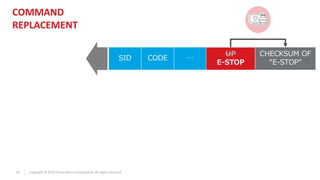
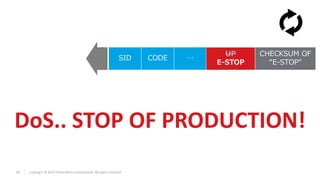
The document discusses vulnerabilities found in industrial remote controllers. It identifies 5 main types of attacks that can exploit vulnerabilities in how the controllers operate and communicate wirelessly. These include record and replay attacks, command injection, abuse of emergency stop functions, malicious device pairing, and malicious reprogramming. The attacks can potentially allow unauthorized control of equipment, disruption of production, or installation of malware. The document calls for vendors and users to improve security of remote controllers through use of encryption, access control, and regular updates.




















![39 Copyright © 2019 Trend Micro Incorporated. All rights reserved.
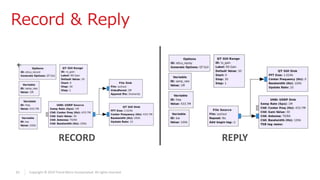
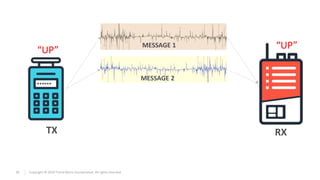
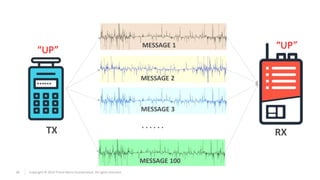
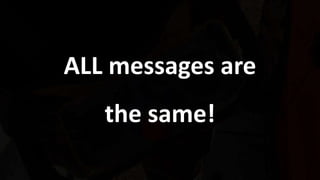
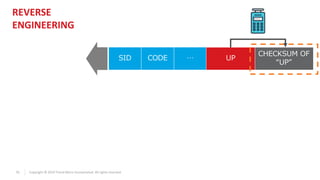
Seq. ID
[SID] [PAIRING_ID(4 bytes)] [SUM1] [0x00] [CMD] [0x000000] [SUM2]
Cryptanalysis
CMD](https://image.slidesharecdn.com/hmi2-190408140202/85/Industrial-Remote-Controllers-Safety-Security-Vulnerabilities-39-320.jpg)