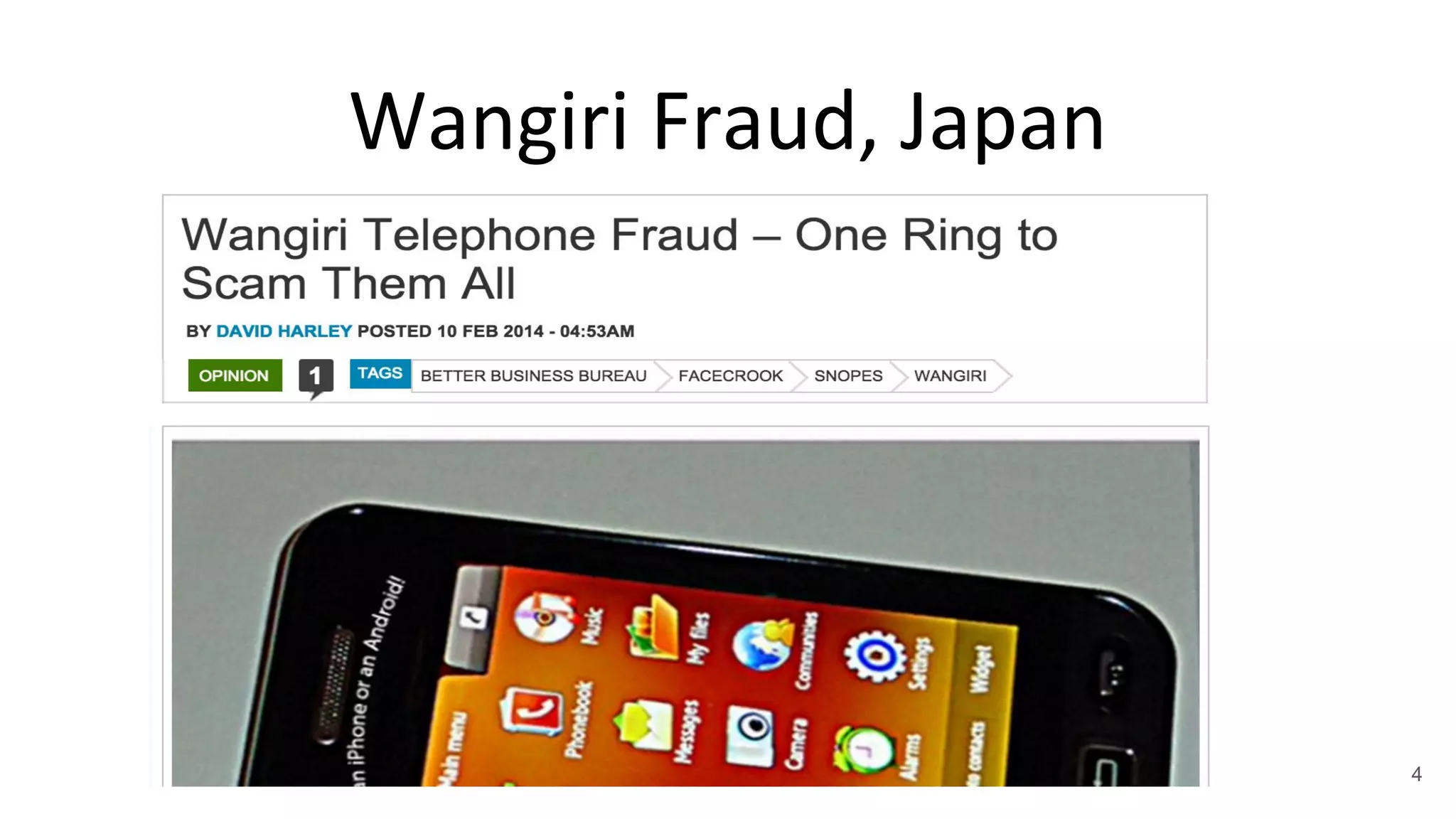
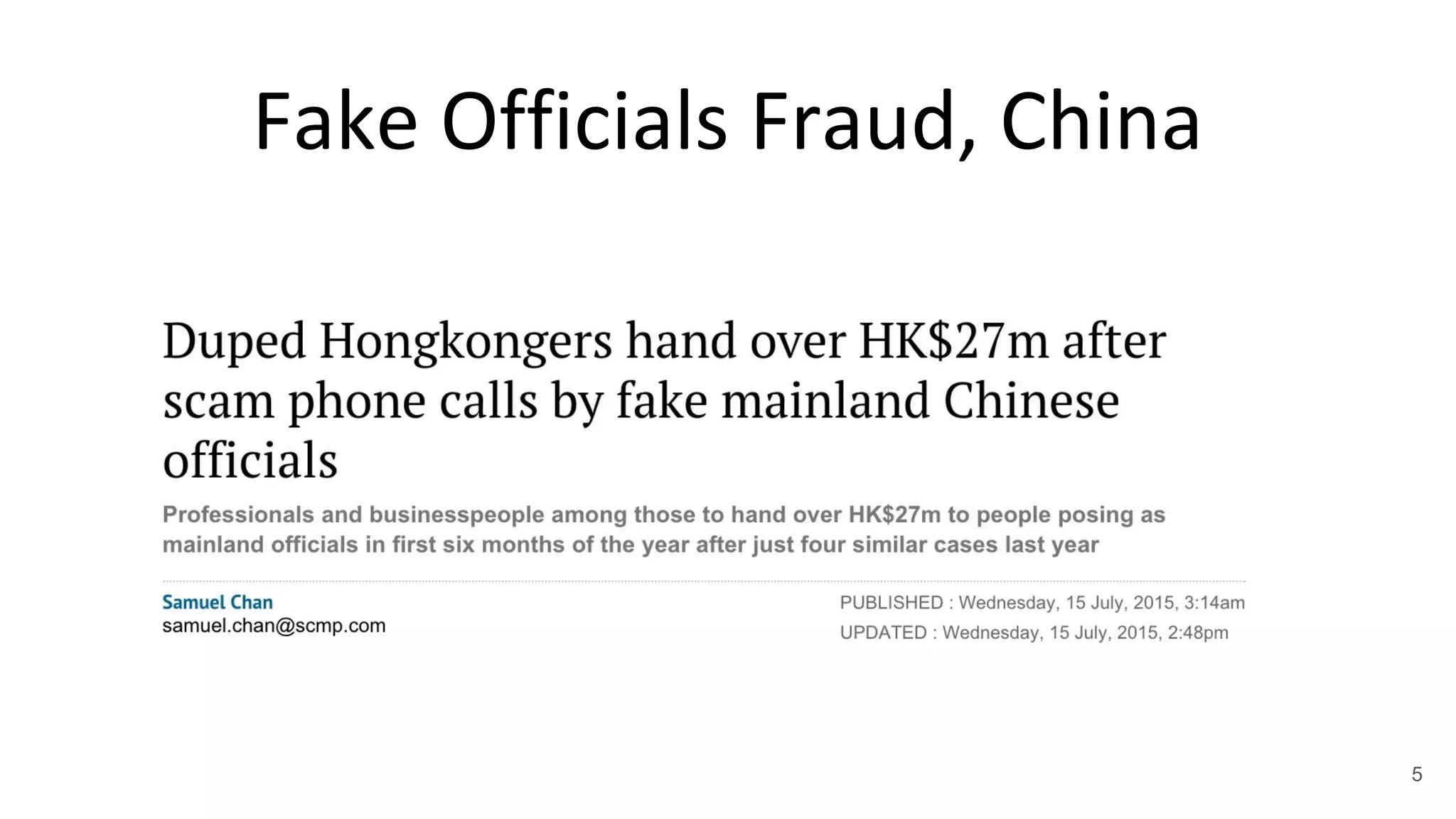
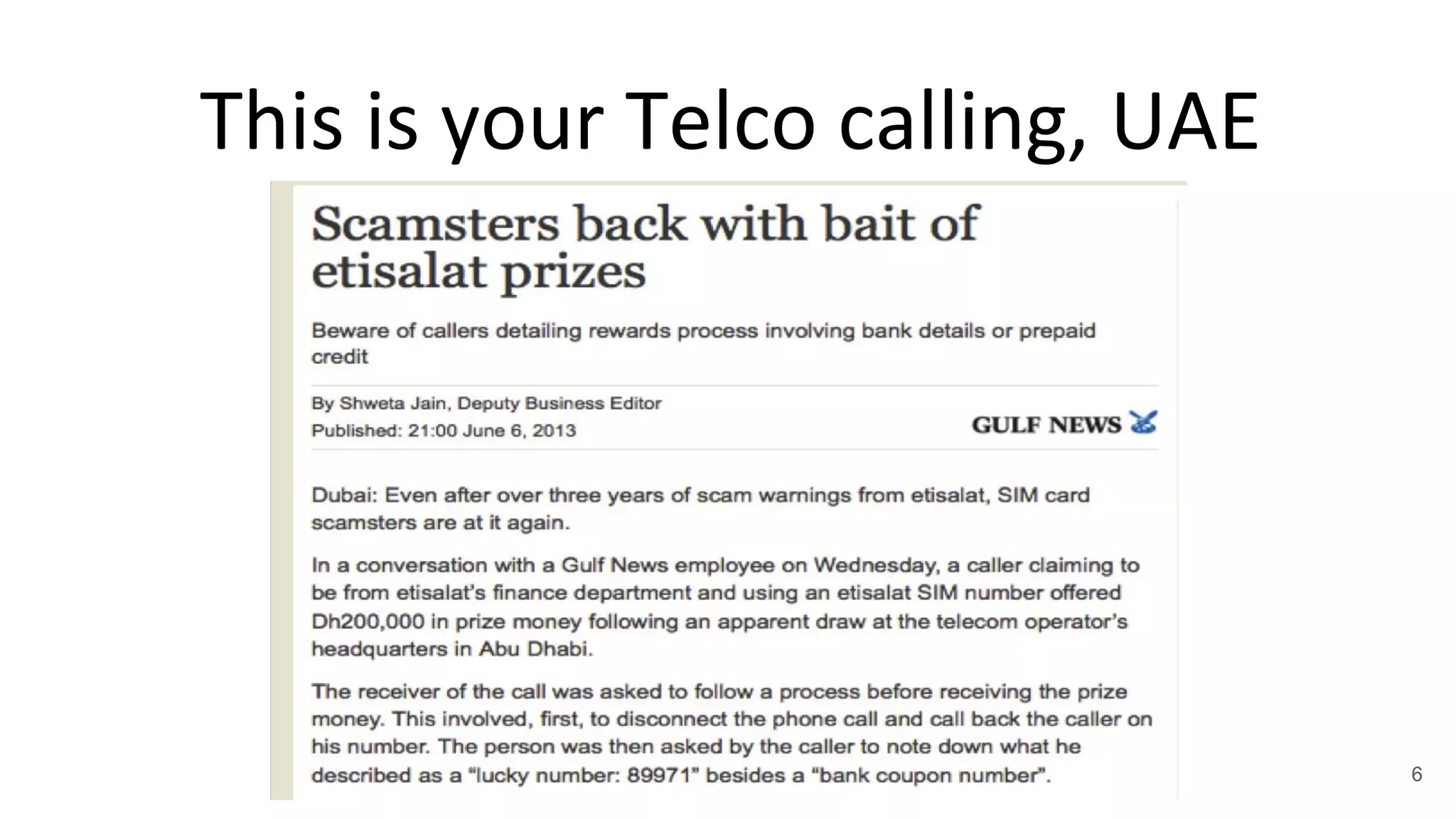
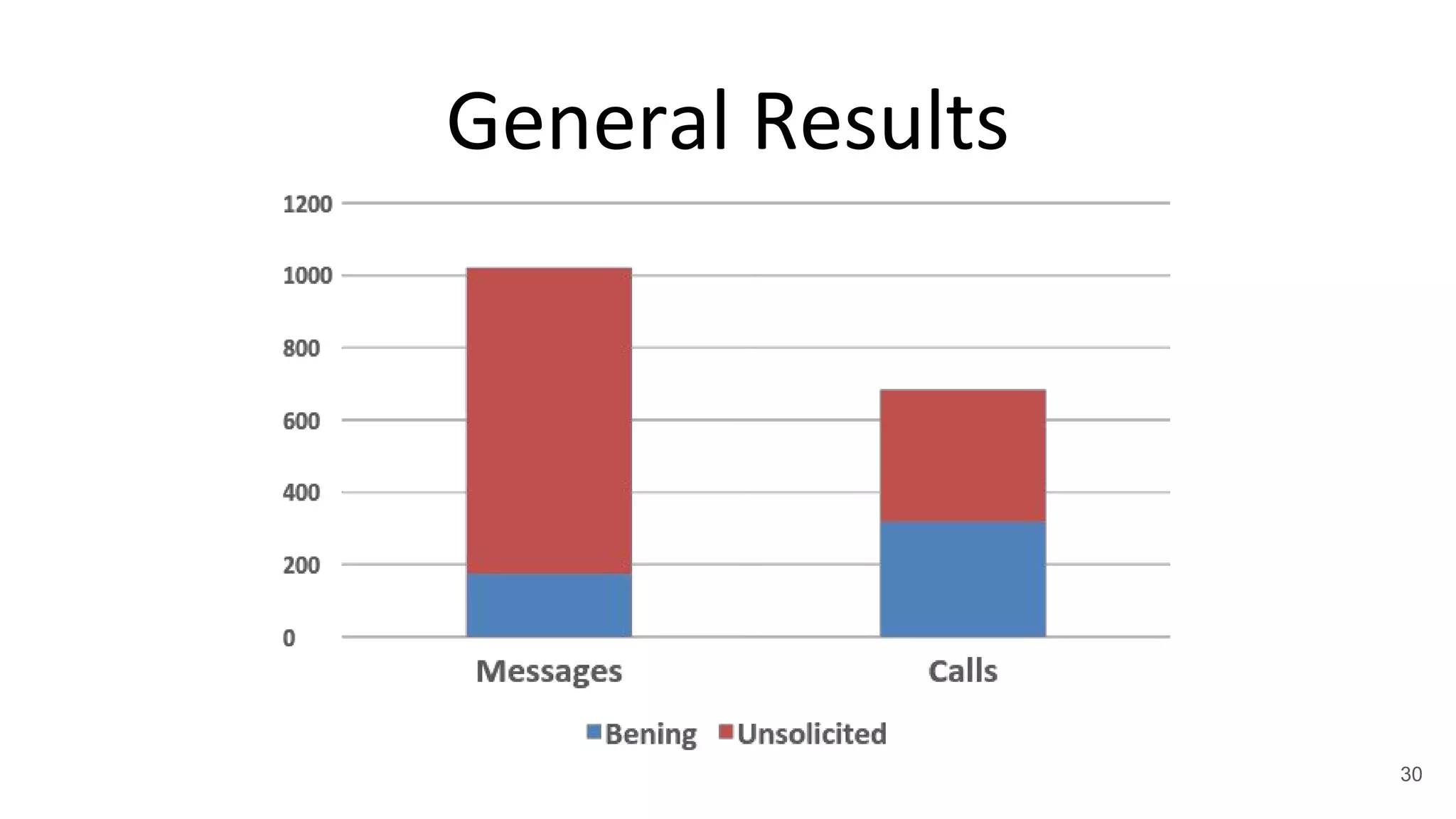
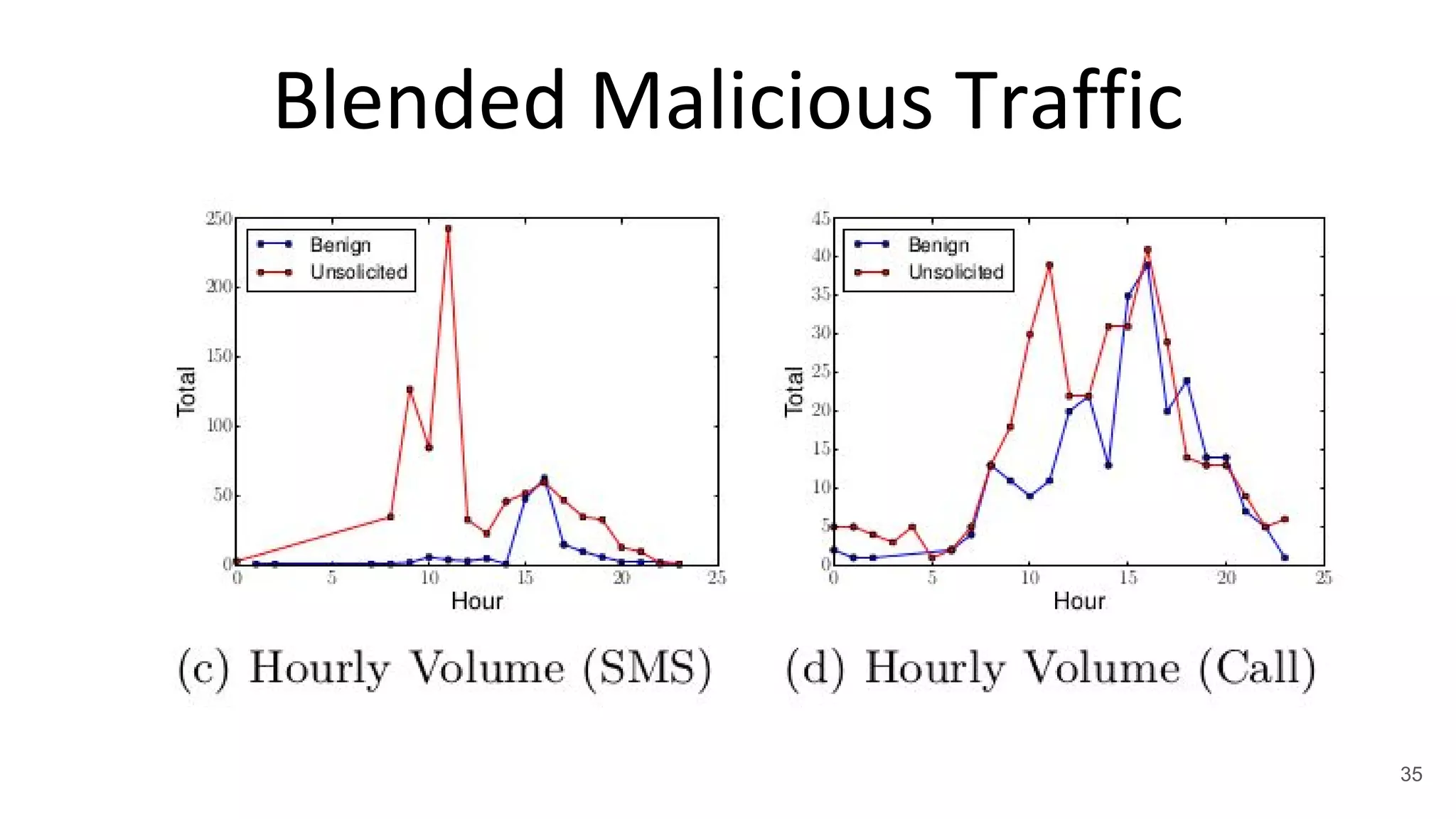
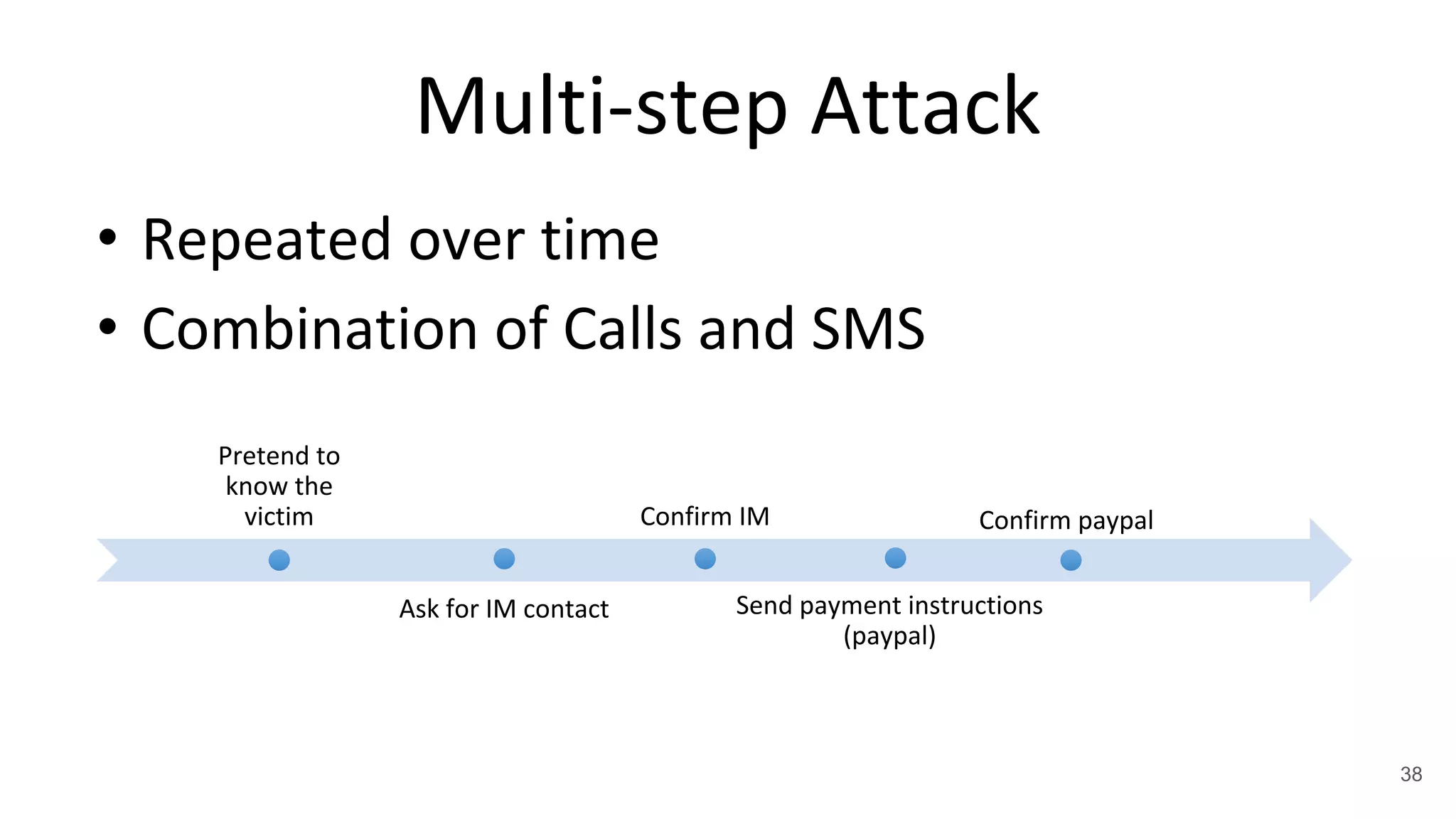
This document summarizes research on mobile telephony fraud in Asia presented at Black Hat Asia 2017. It describes different types of fraud campaigns in countries like Japan, China, UAE, Singapore, and Nigeria. These include wangiri fraud, fake officials fraud, police scams, and bringing back cash scams. The document also discusses strategies used by fraudsters to seed target numbers, techniques like social engineering to target victims, and defensive strategies for individuals and organizations.


![3
Click to play recording [removed]](https://image.slidesharecdn.com/asia-17-balduzzi-mobile-telephony-threats-in-asia-170331201204/75/Mobile-Telephony-Threats-in-Asia-3-2048.jpg)


















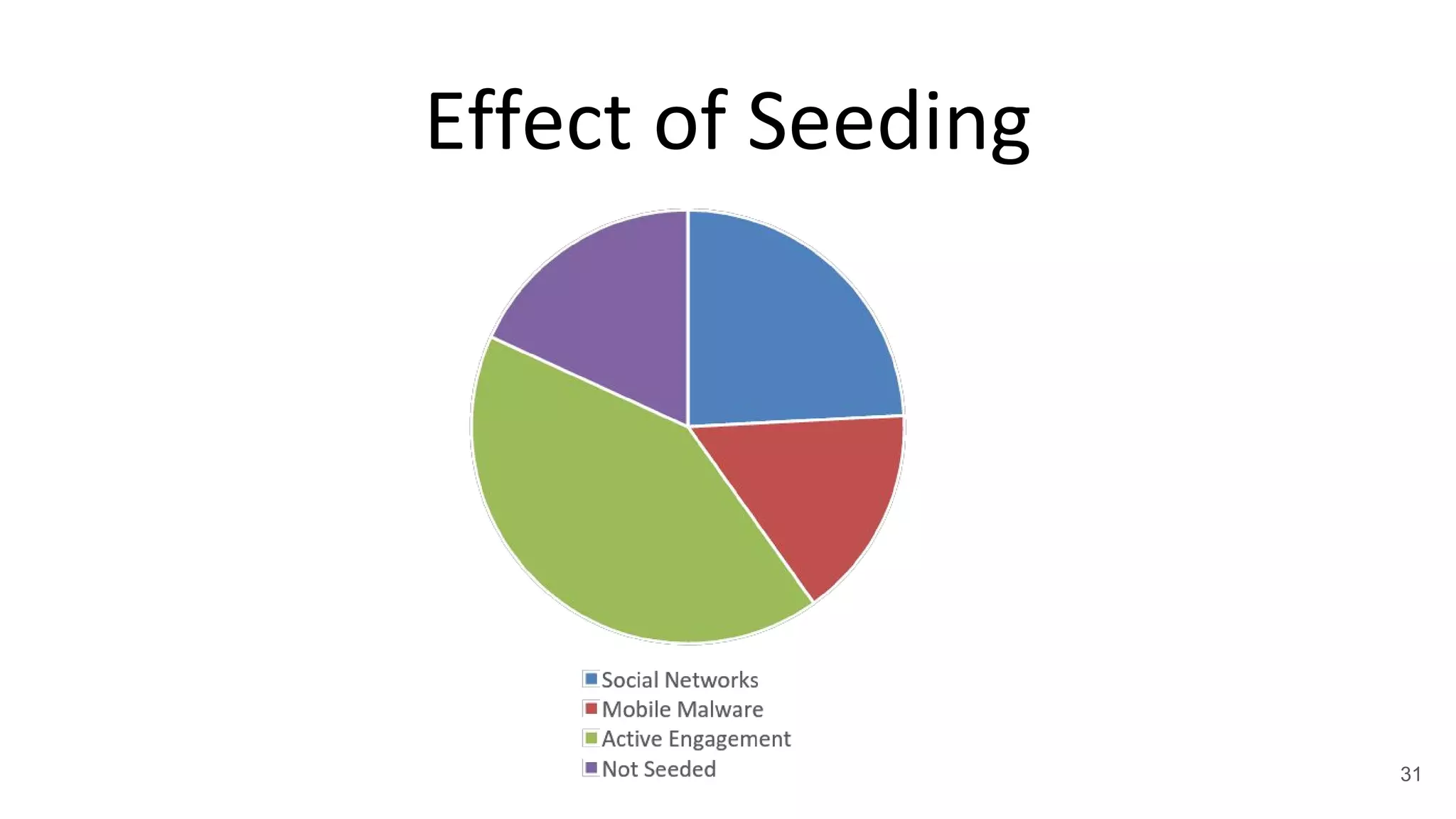
![Social Networks
• Very effective
• Picked up by Xinhua
Quanmei [*]
• Daily news in the form
of spam -> 221
messages
[*] http://www.xhqm.cn/ 32](https://image.slidesharecdn.com/asia-17-balduzzi-mobile-telephony-threats-in-asia-170331201204/75/Mobile-Telephony-Threats-in-Asia-32-2048.jpg)
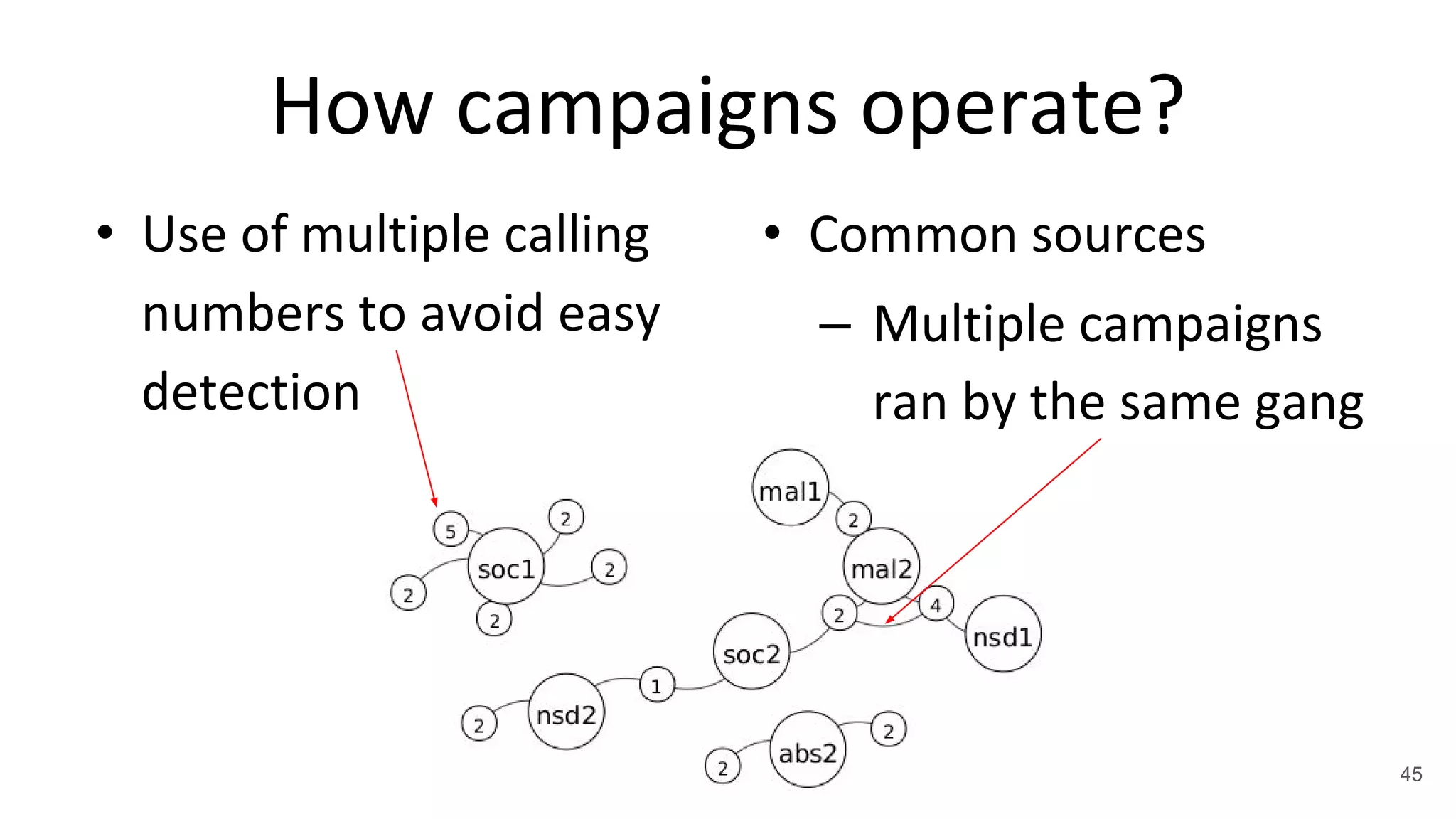
![Malicious Apps
• 79 ADs from 106588302
• Self-promoting app [*]
– 0690123590110 (mal1)
1065502004955590110
(mal2) are spoofed
[*] http://wap.guanxi.me 33](https://image.slidesharecdn.com/asia-17-balduzzi-mobile-telephony-threats-in-asia-170331201204/75/Mobile-Telephony-Threats-in-Asia-33-2048.jpg)




![Google Business Listing
• List your business online
on Google
• Click here for recording
[removed].
40](https://image.slidesharecdn.com/asia-17-balduzzi-mobile-telephony-threats-in-asia-170331201204/75/Mobile-Telephony-Threats-in-Asia-40-2048.jpg)
![Can you hear me?
• Subscribe you to
services when you say
‘YES’
• Click here for recording.
[removed]
41](https://image.slidesharecdn.com/asia-17-balduzzi-mobile-telephony-threats-in-asia-170331201204/75/Mobile-Telephony-Threats-in-Asia-41-2048.jpg)



![Authentication Bypass
• Reuse of previously-terminated numbers
• Circumvent 2-factor auth!
[Tencent] Verification code 658339. Use it
to change the password of the QQ number
64******5. Leaking the verification code
has a risk. The QQ Security Center.
46](https://image.slidesharecdn.com/asia-17-balduzzi-mobile-telephony-threats-in-asia-170331201204/75/Mobile-Telephony-Threats-in-Asia-46-2048.jpg)

