Embed presentation
Download as PDF, PPTX

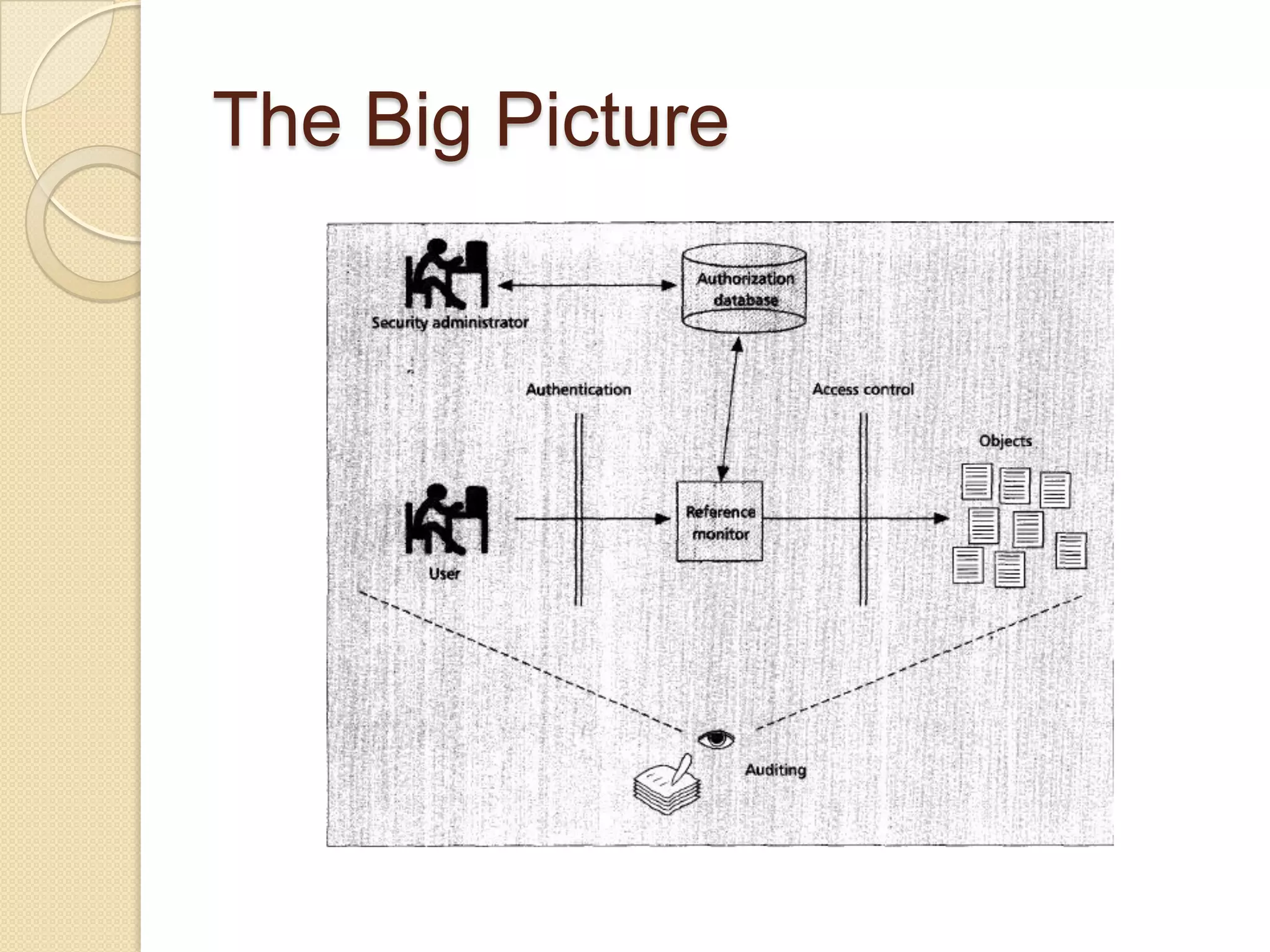




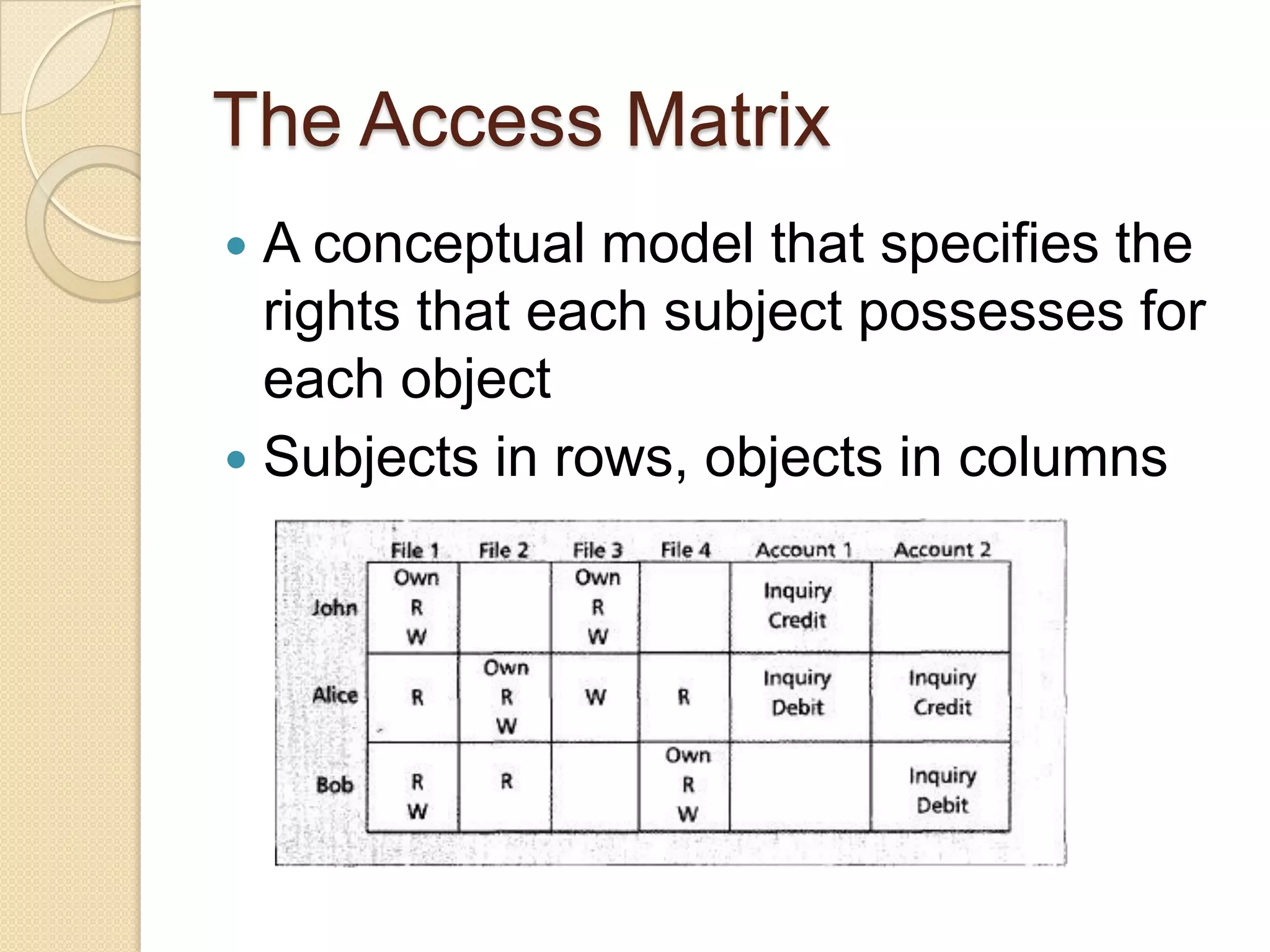


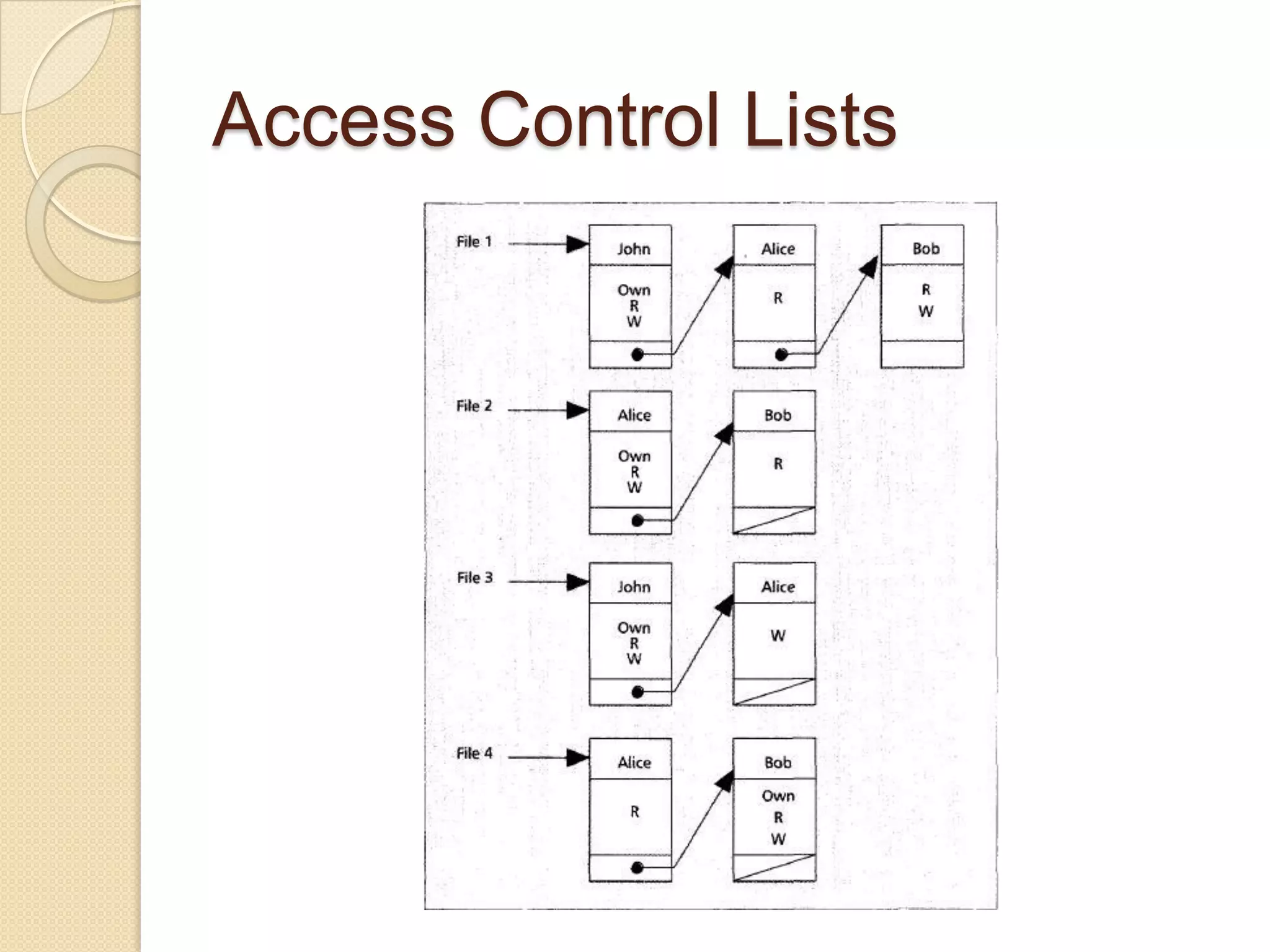


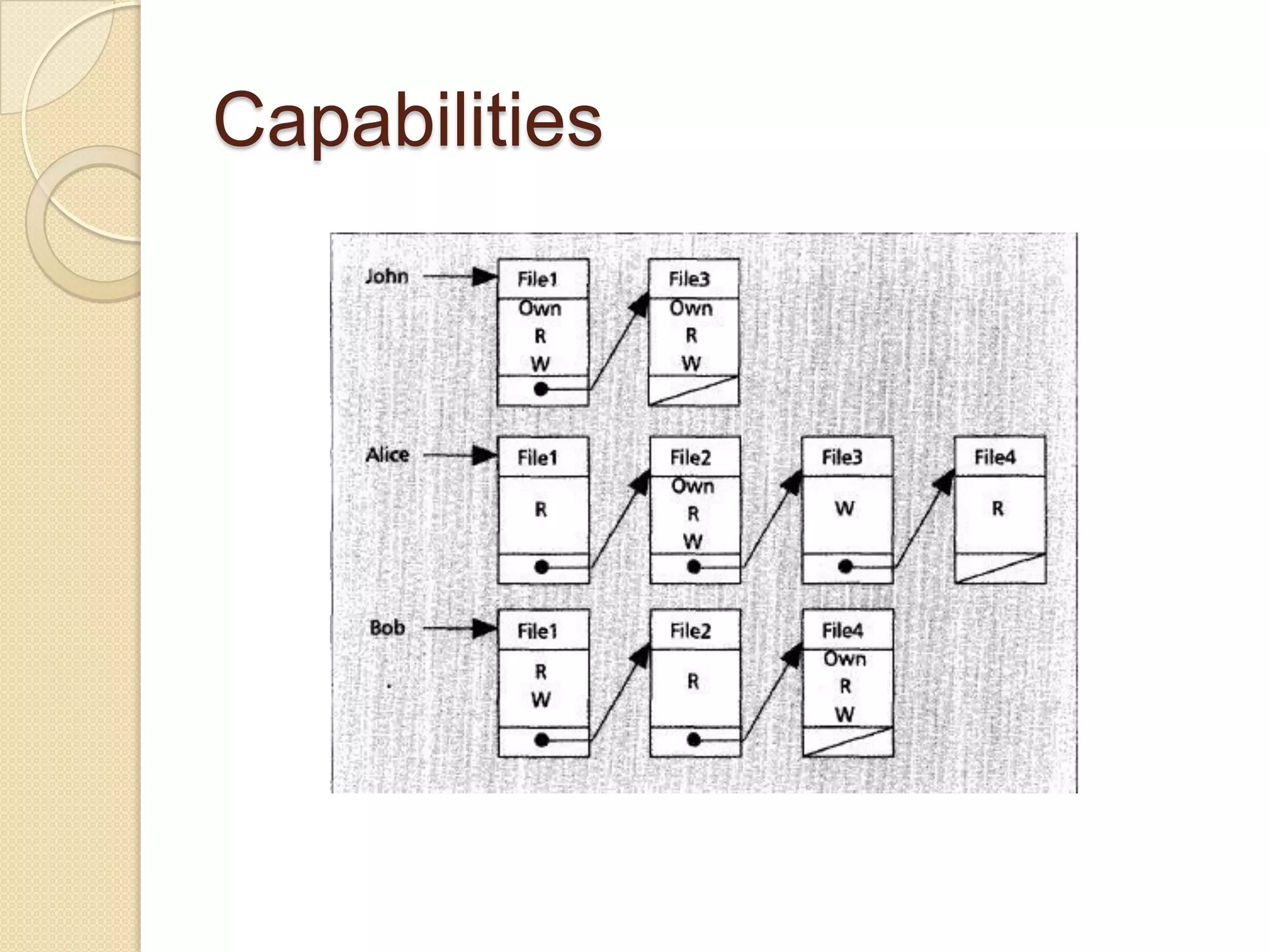
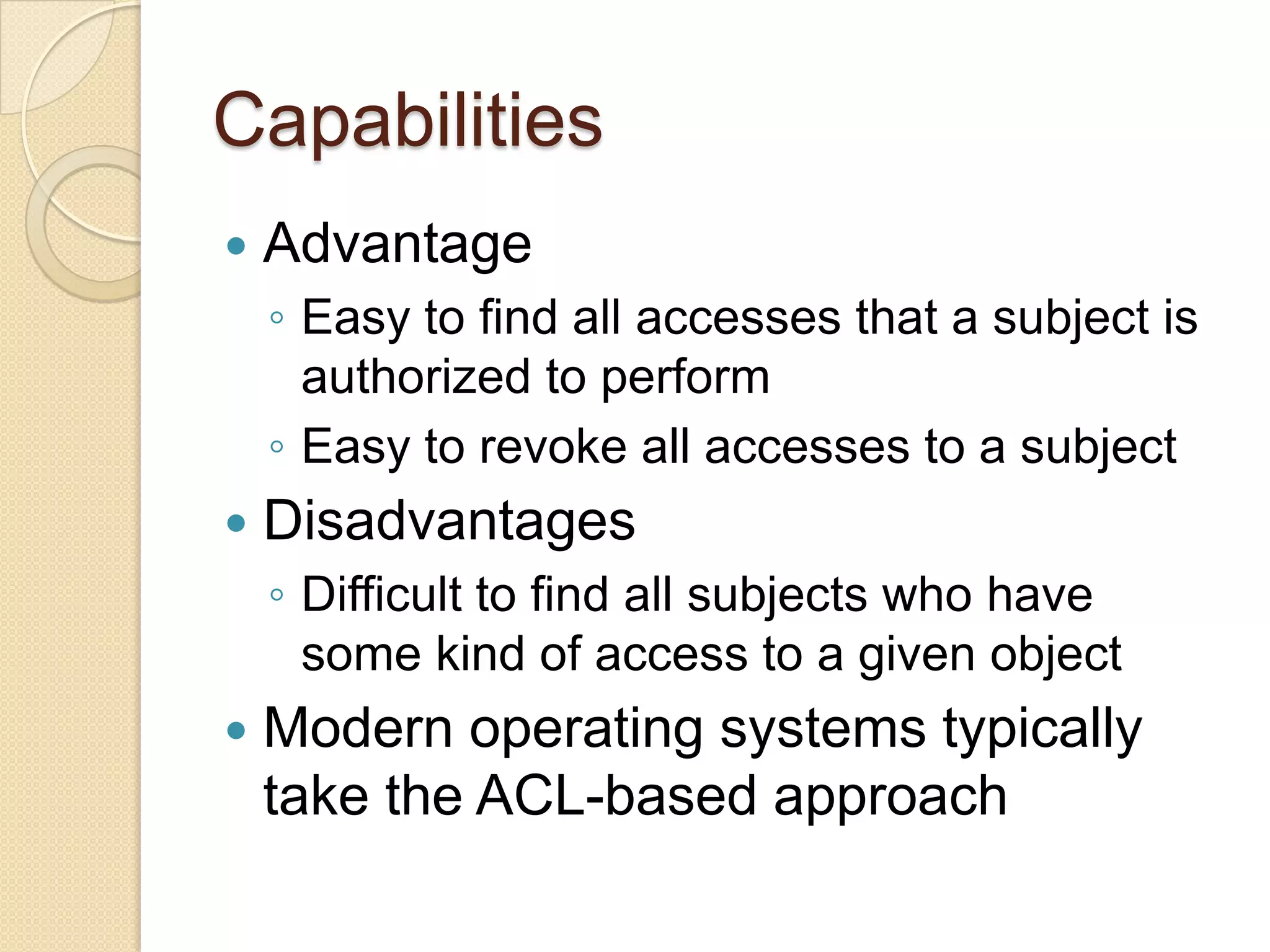

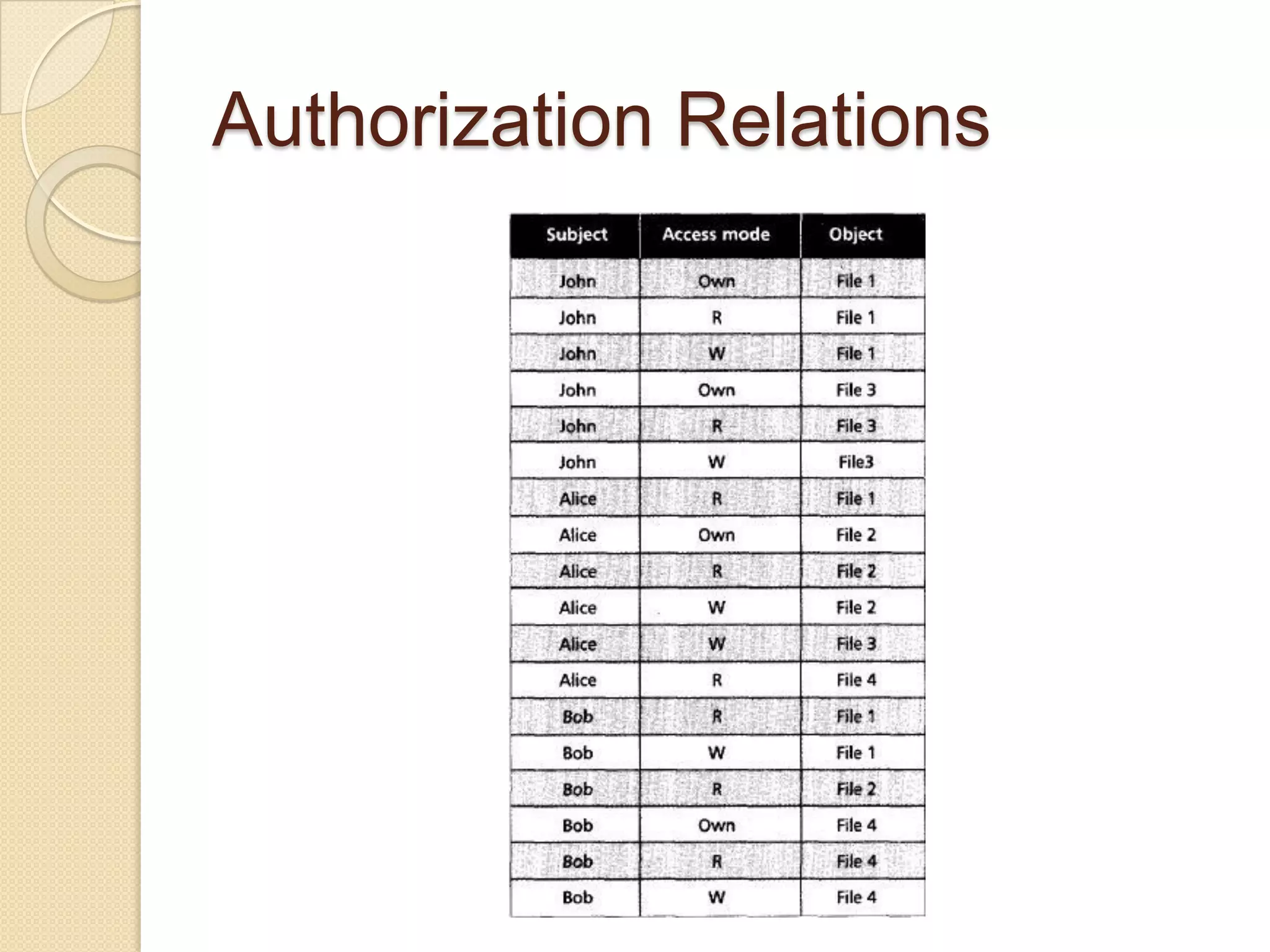

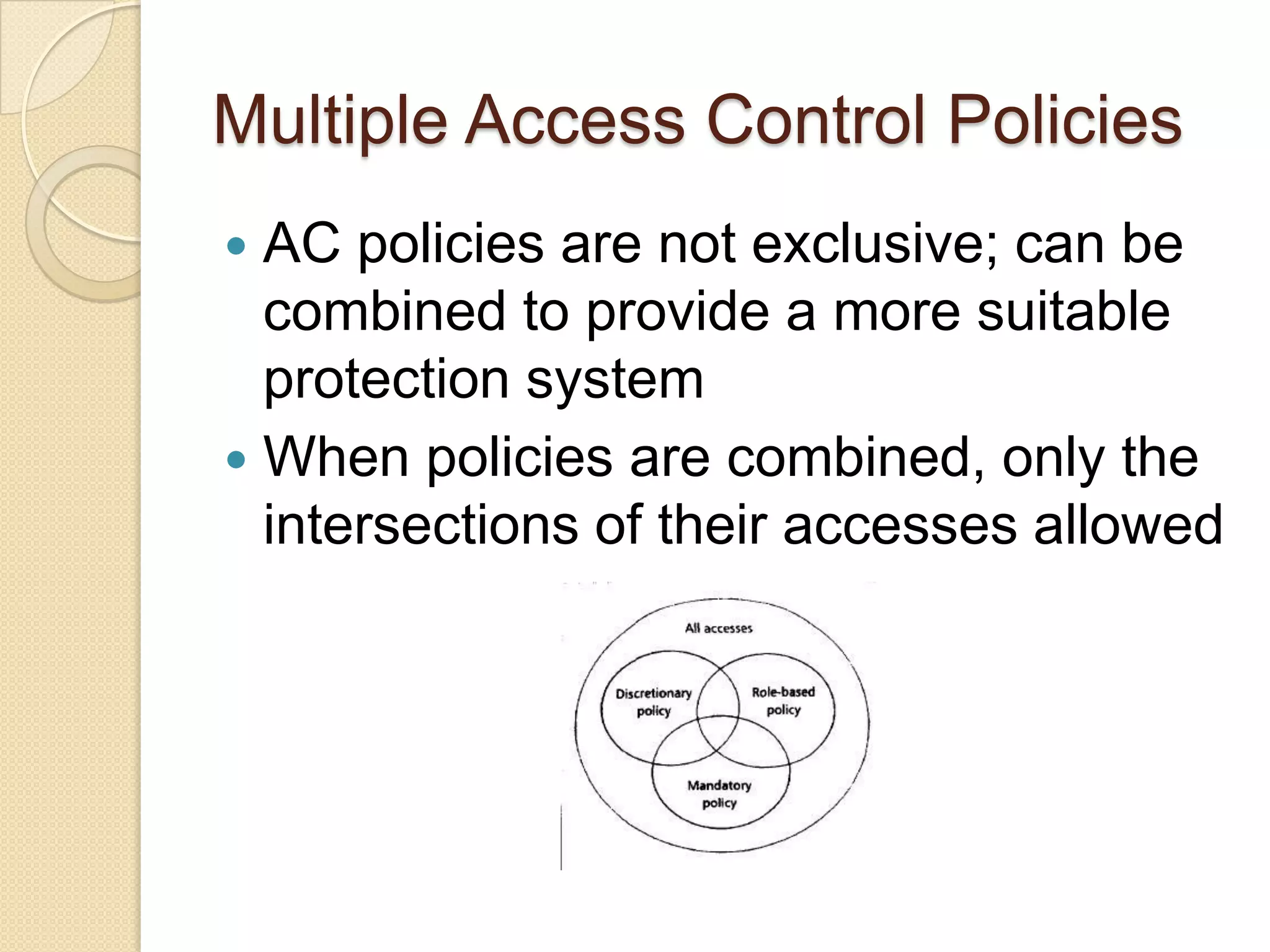






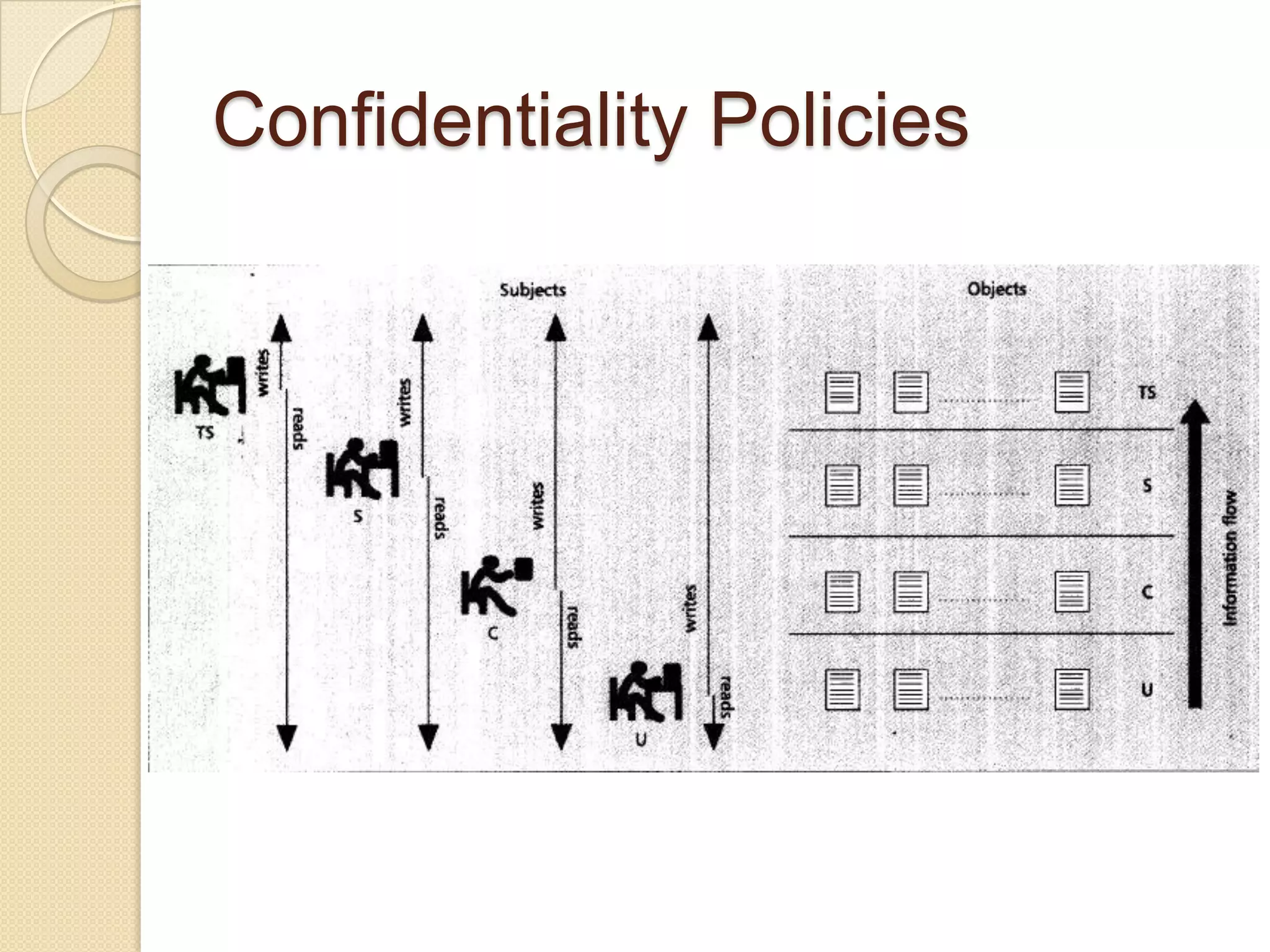










The document outlines the principles and practices of access control, emphasizing its role in managing user operations to maintain security in computer systems. It covers the models of access control, such as access matrices, access control lists (ACLs), capabilities, and various policy frameworks including discretionary, mandatory, and role-based policies. Additionally, it discusses the importance of auditing in identifying violations and ensuring accountability within access control systems.






































