Embed presentation





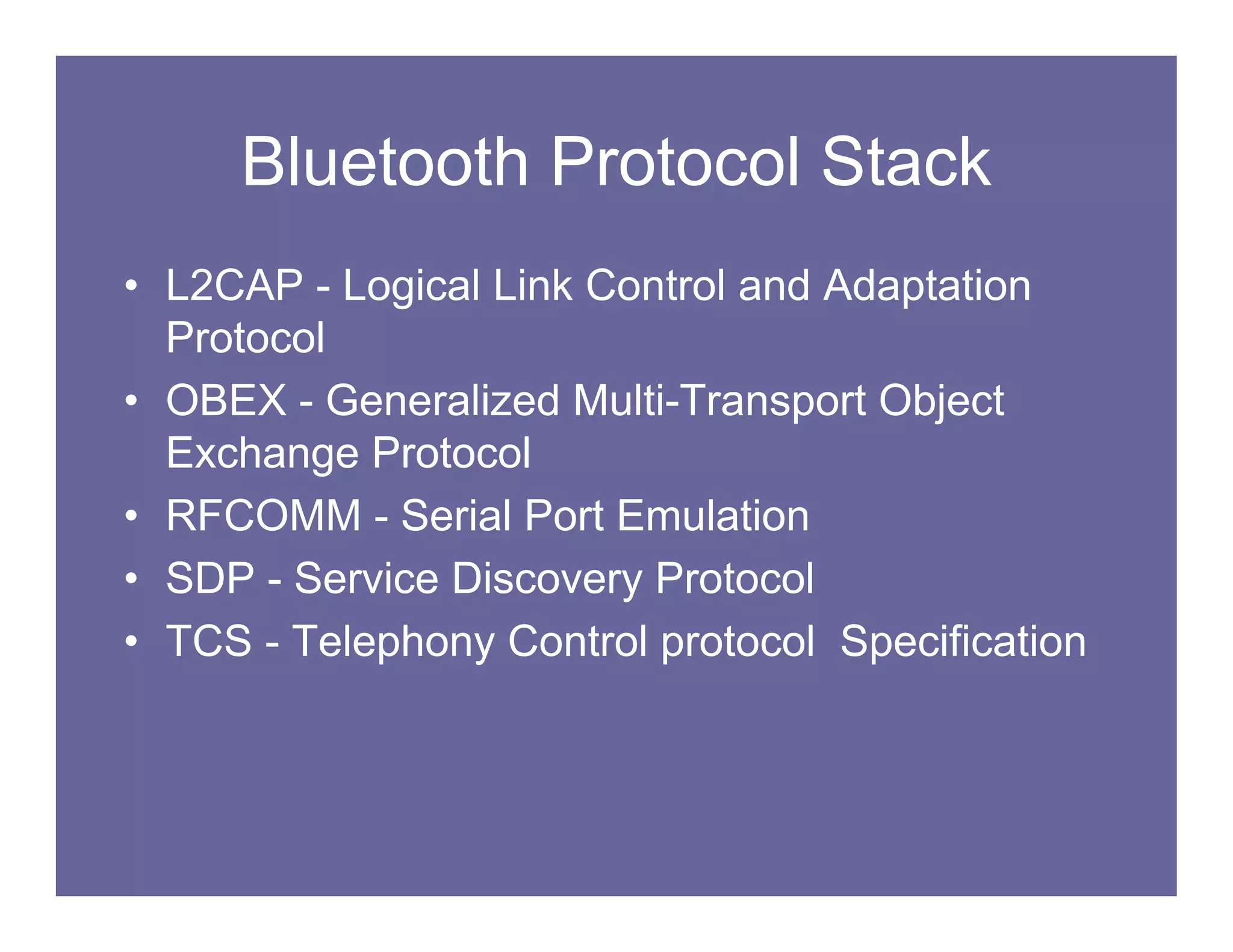



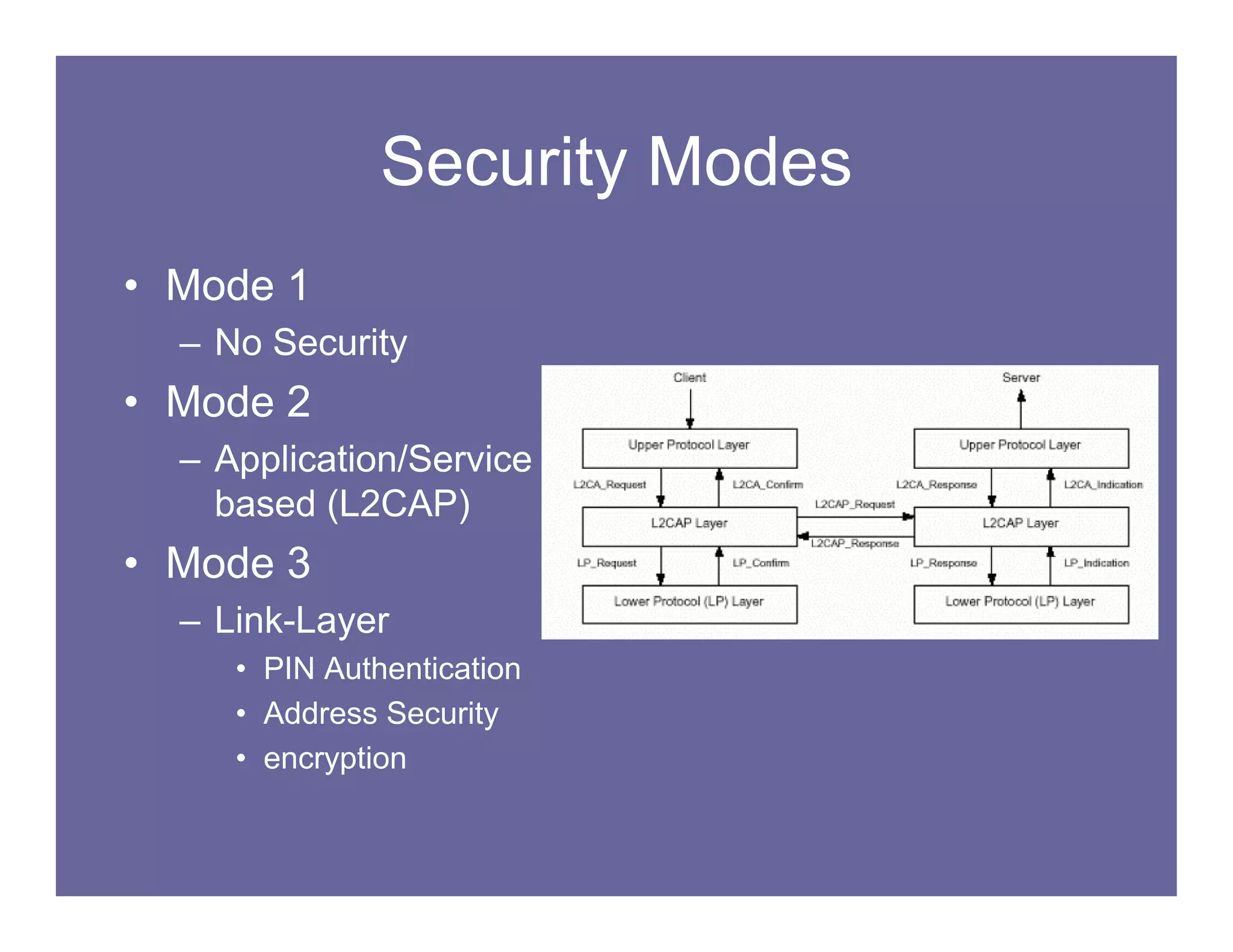










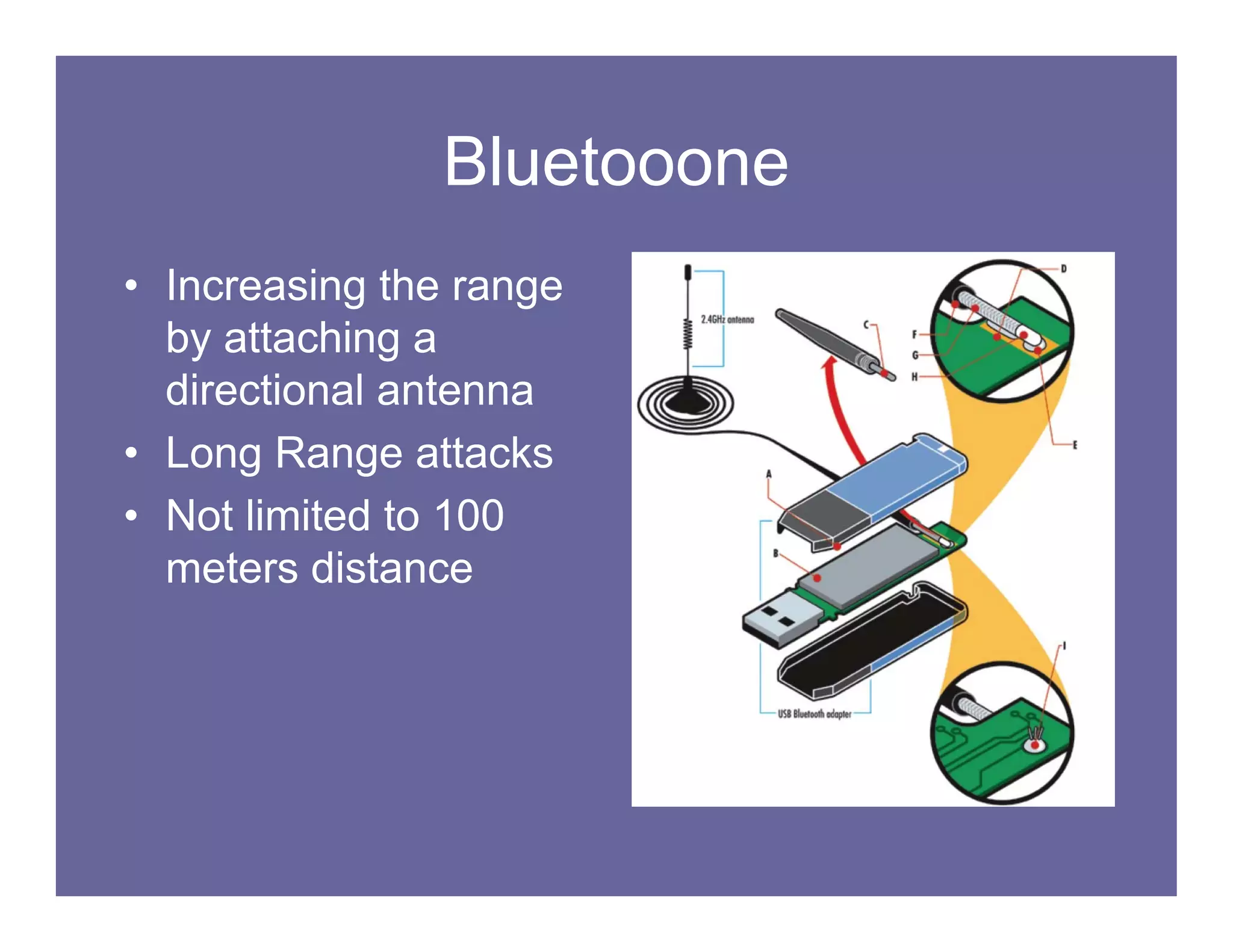




This document summarizes vulnerabilities in Bluetooth technology, including eavesdropping, impersonation, and cipher vulnerabilities. It describes "bluejacking", "bluesnarfing", and other attacks that exploit flaws in Bluetooth functionality and permissions. The document recommends turning off Bluetooth when not in use, setting devices to non-discoverable, using random PINs, and avoiding transmitting sensitive data over Bluetooth to help protect against these vulnerabilities and attacks.


























