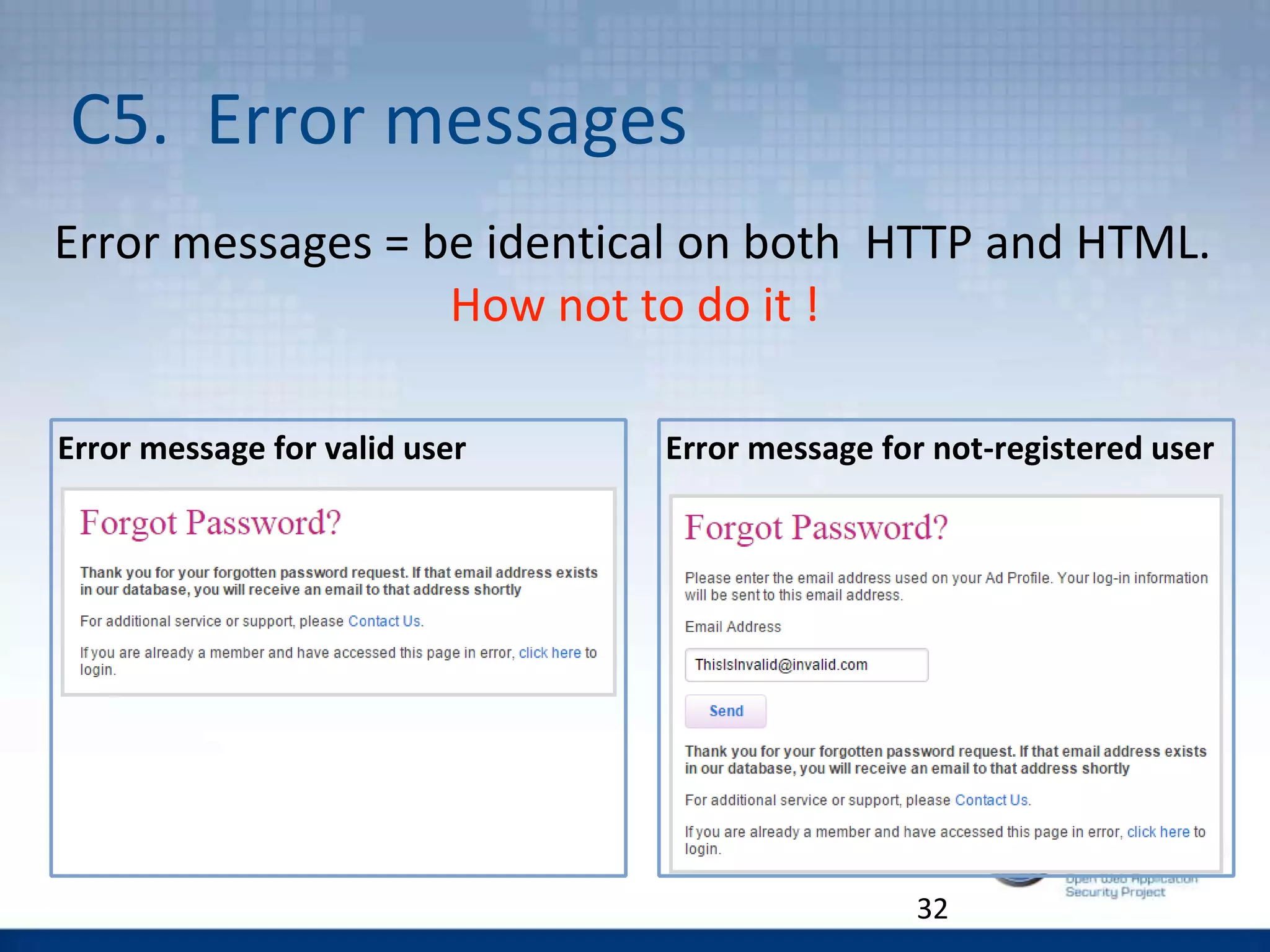
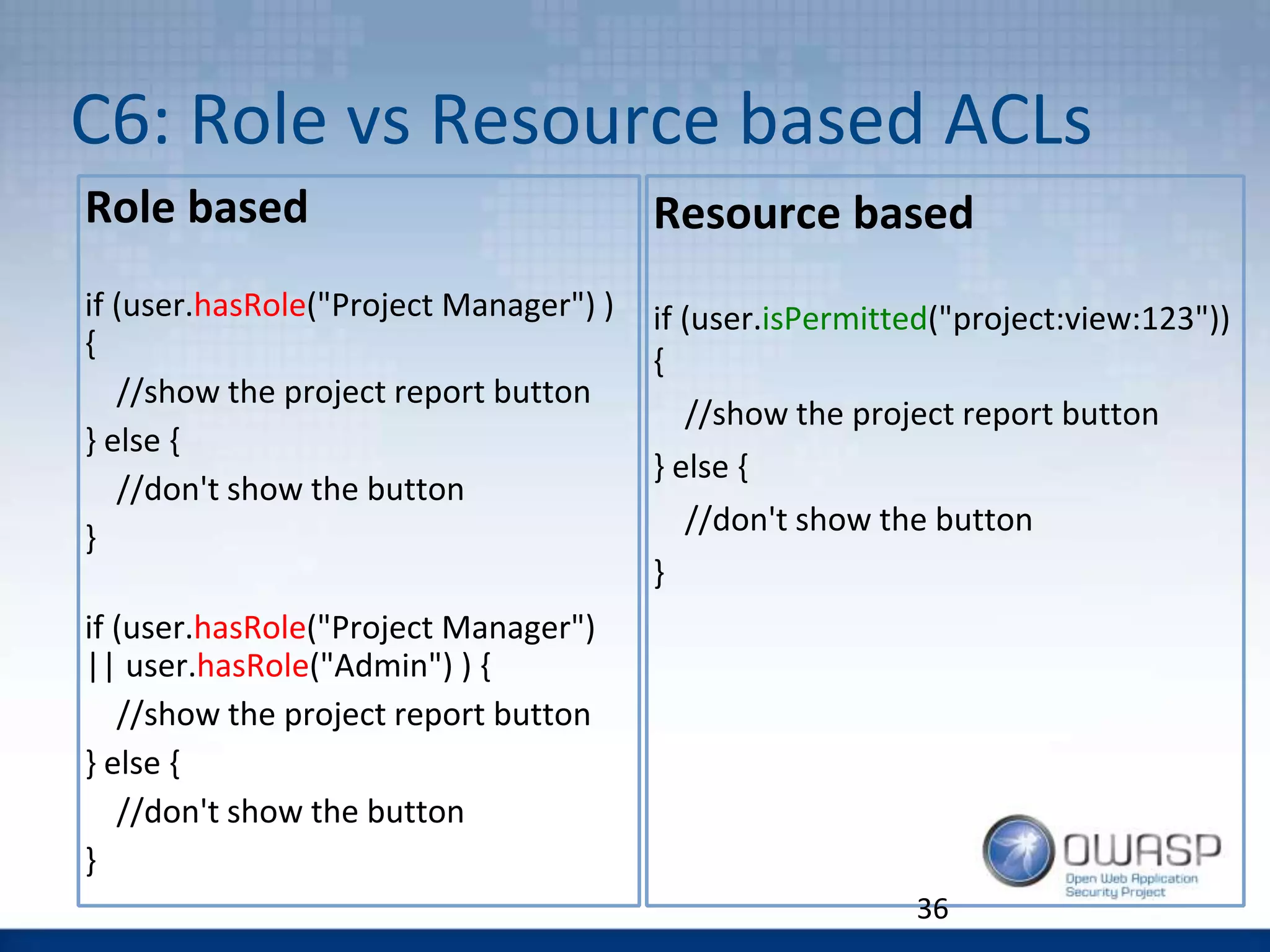
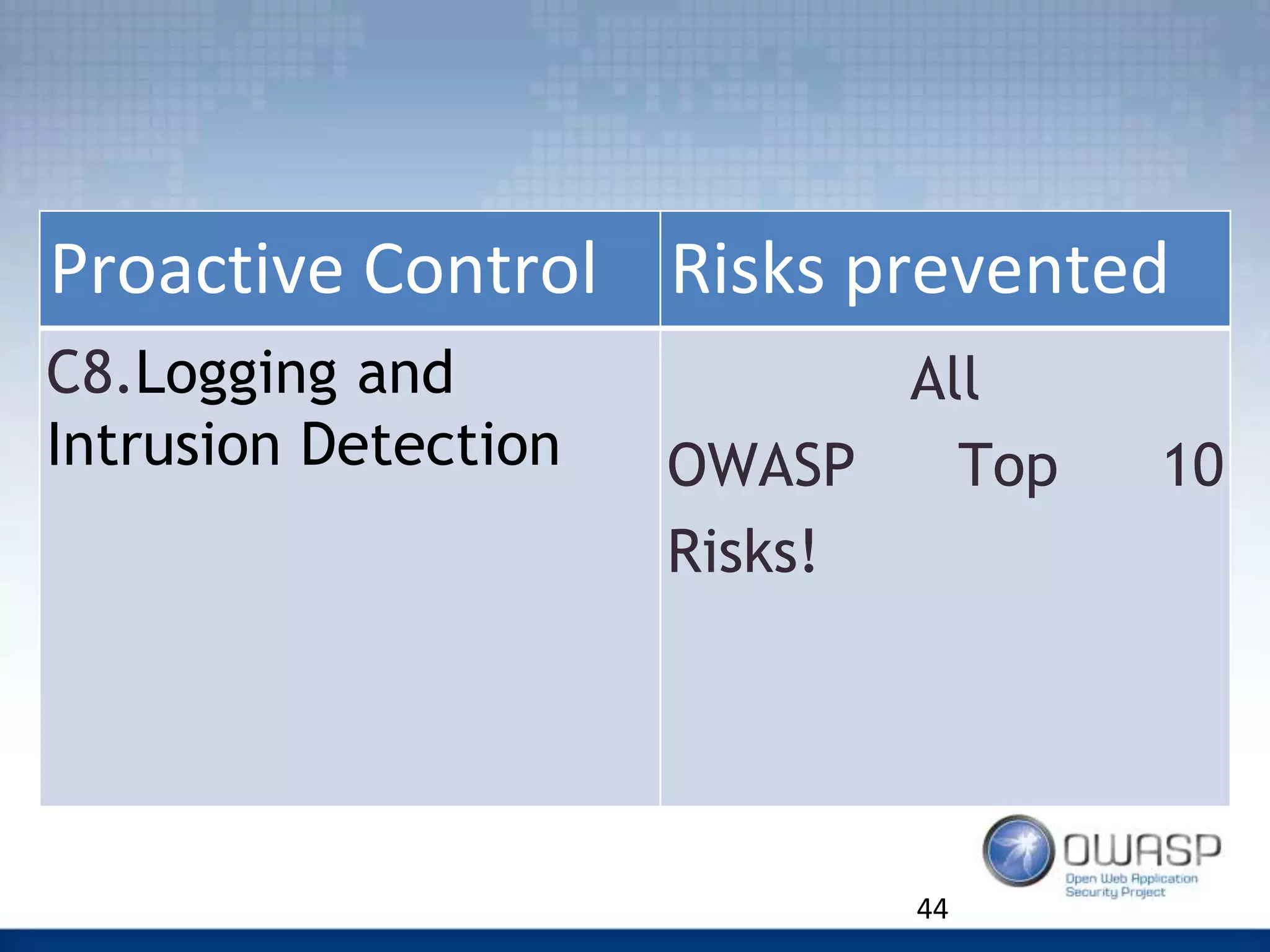
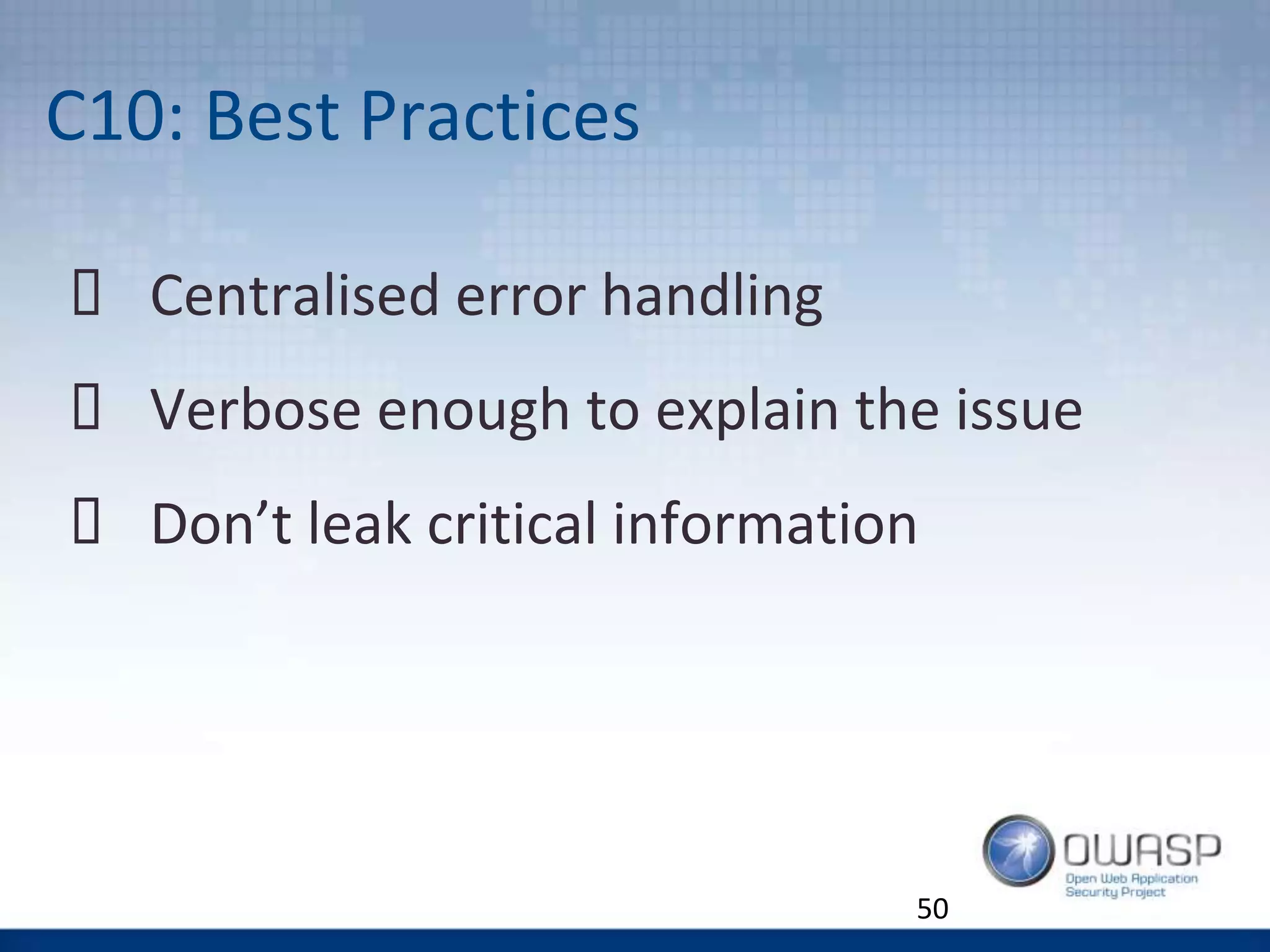
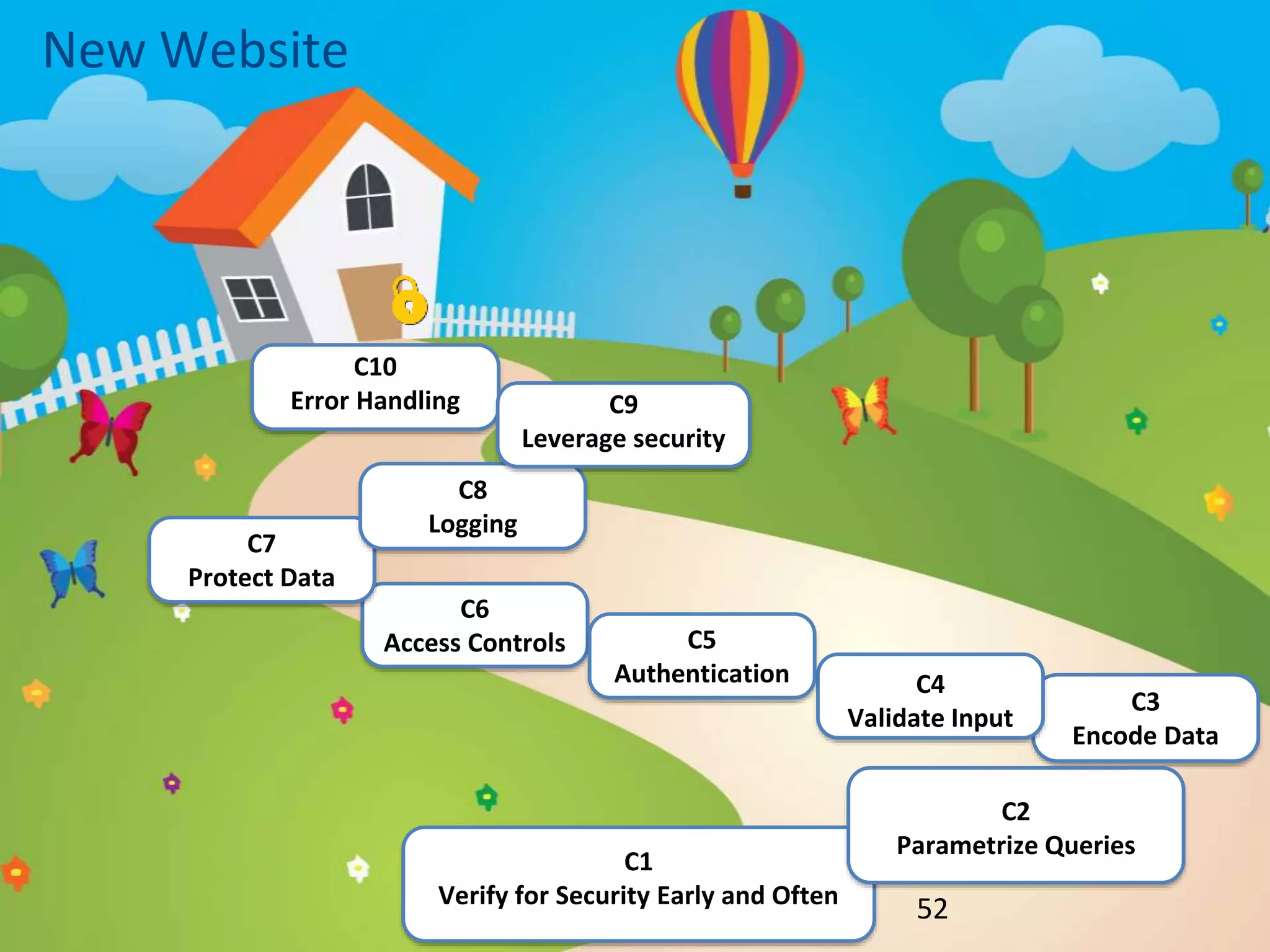
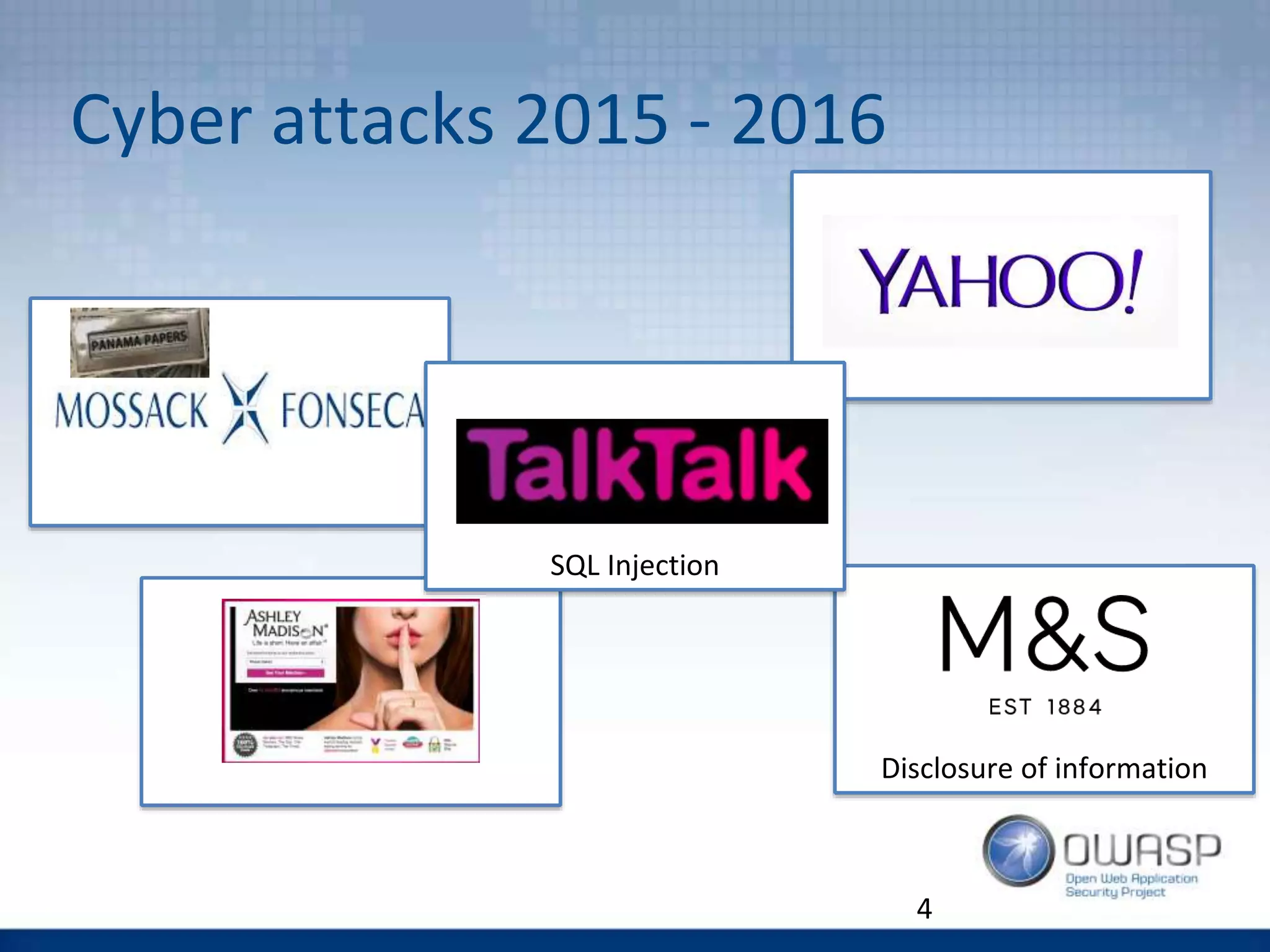
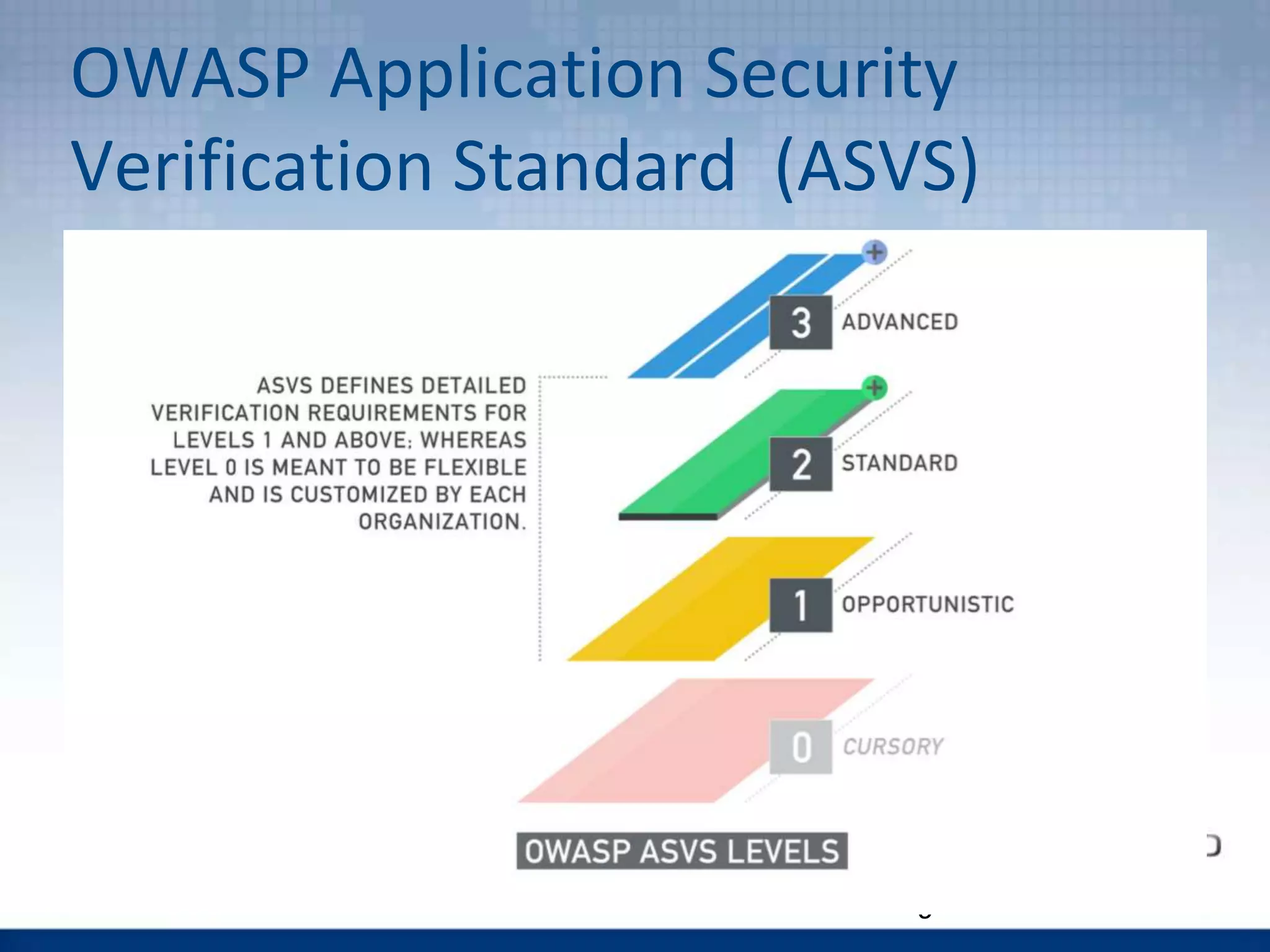
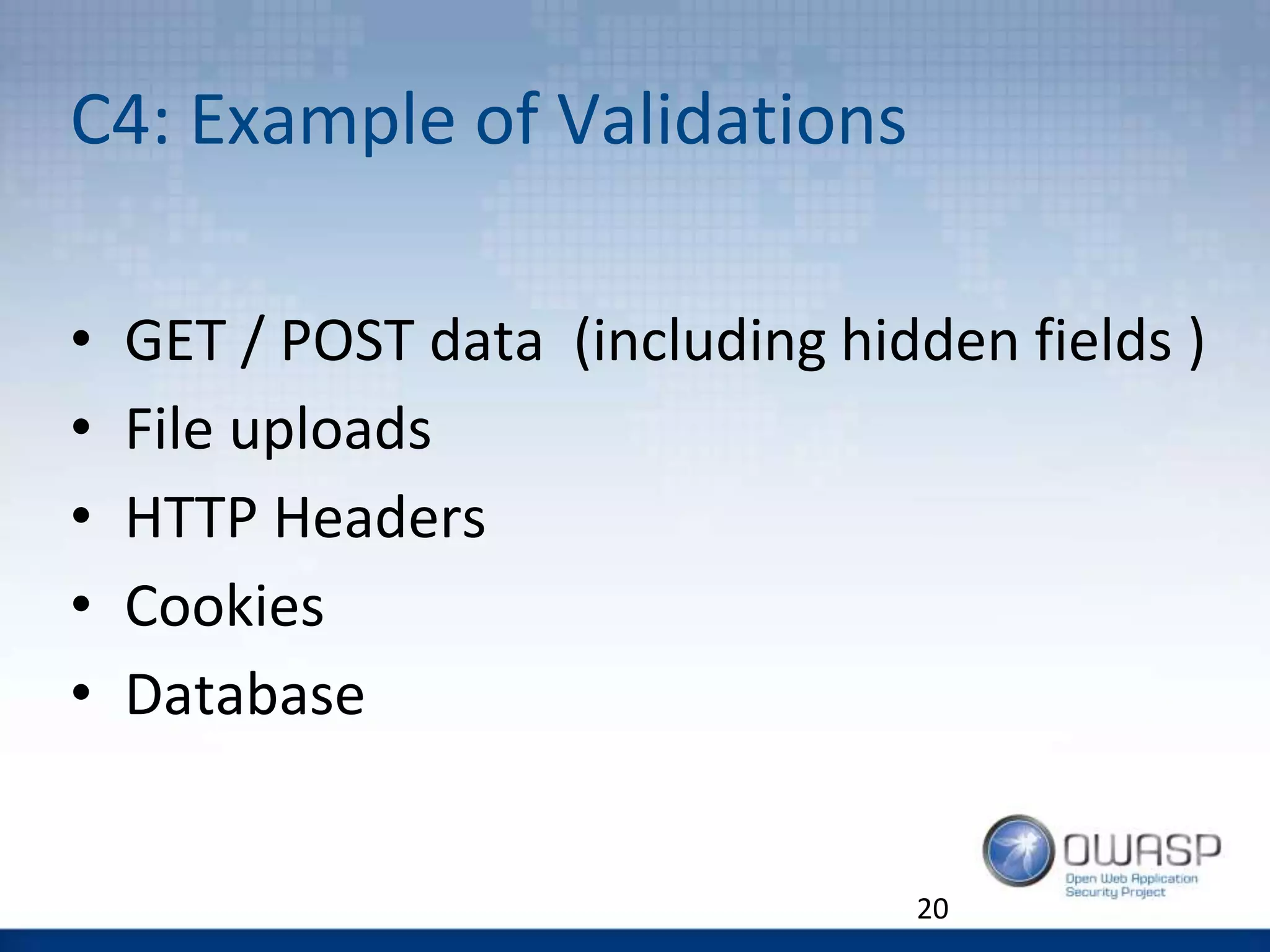
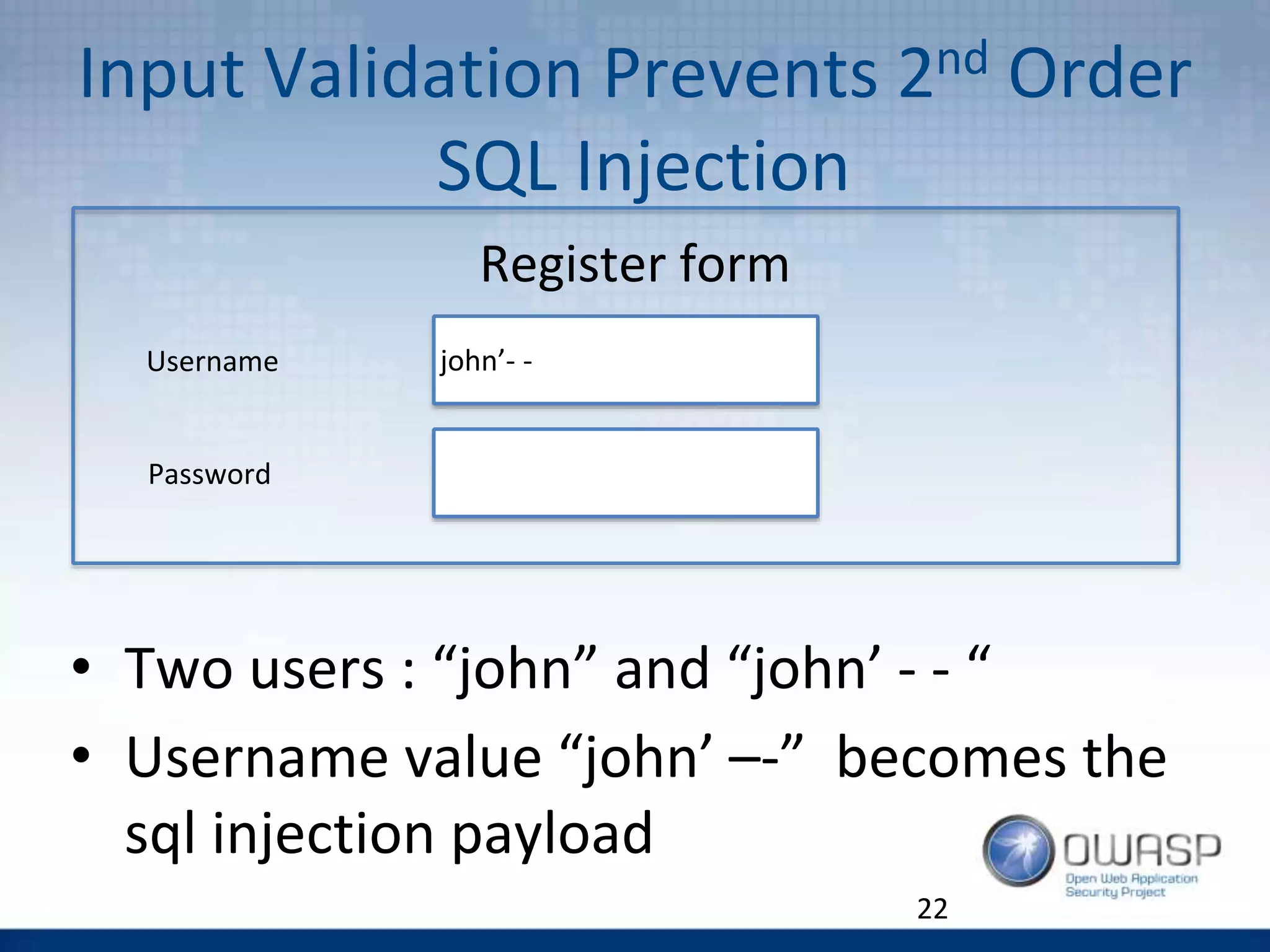
The document discusses the OWASP Top 10 Proactive Controls aimed at mitigating common web application security risks such as injection, broken authentication, and sensitive data exposure. It emphasizes best practices such as verifying security early, parameterizing queries, and implementing strong authentication and access controls. Each control is elaborated with examples and methods to prevent specific vulnerabilities, highlighting the importance of security in application development.







![PHP:
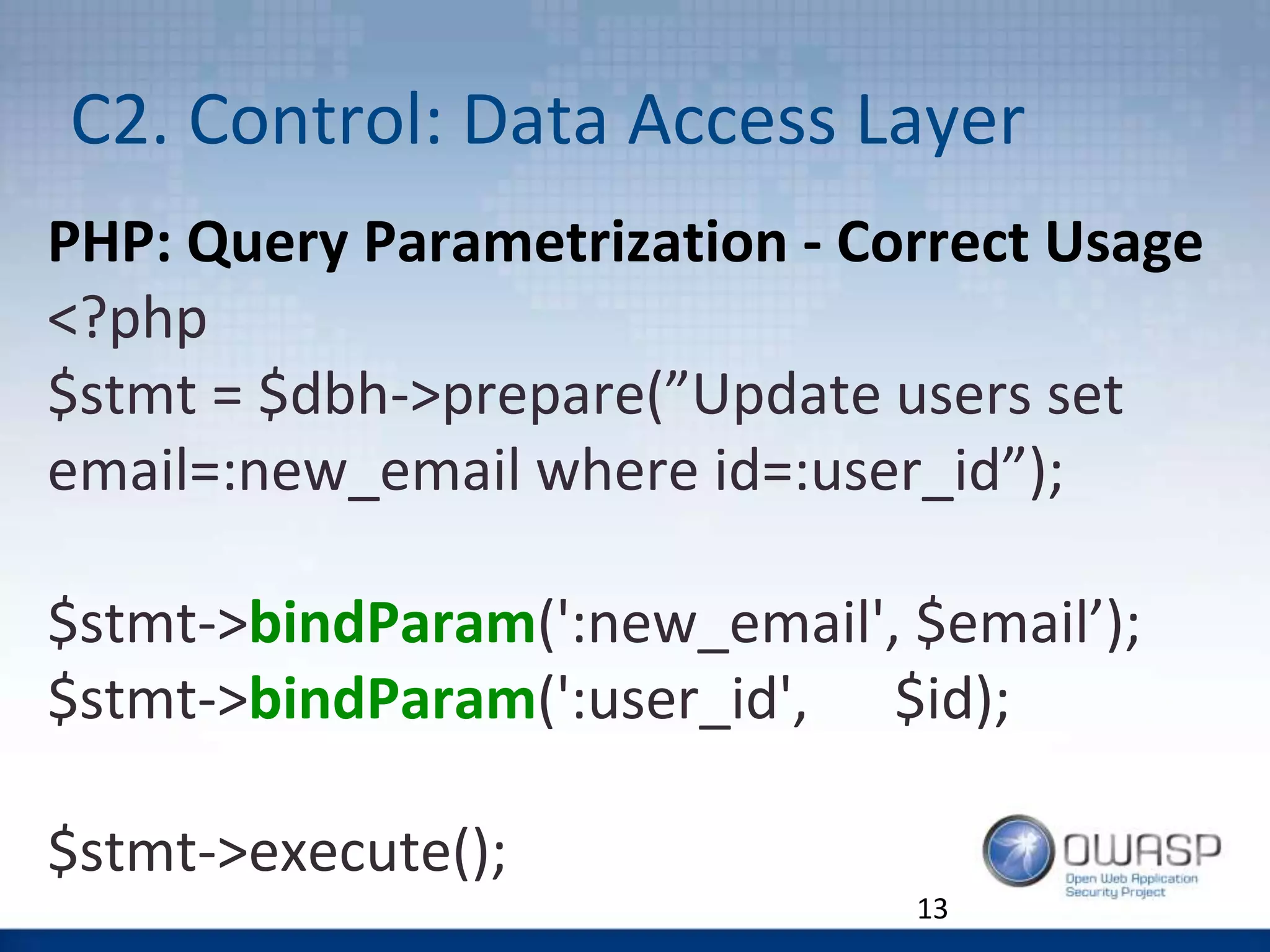
<?php
$stmt = $dbh->prepare(”Update users set
email = $_GET[‘email’] where id=$id”);
$stmt->execute();
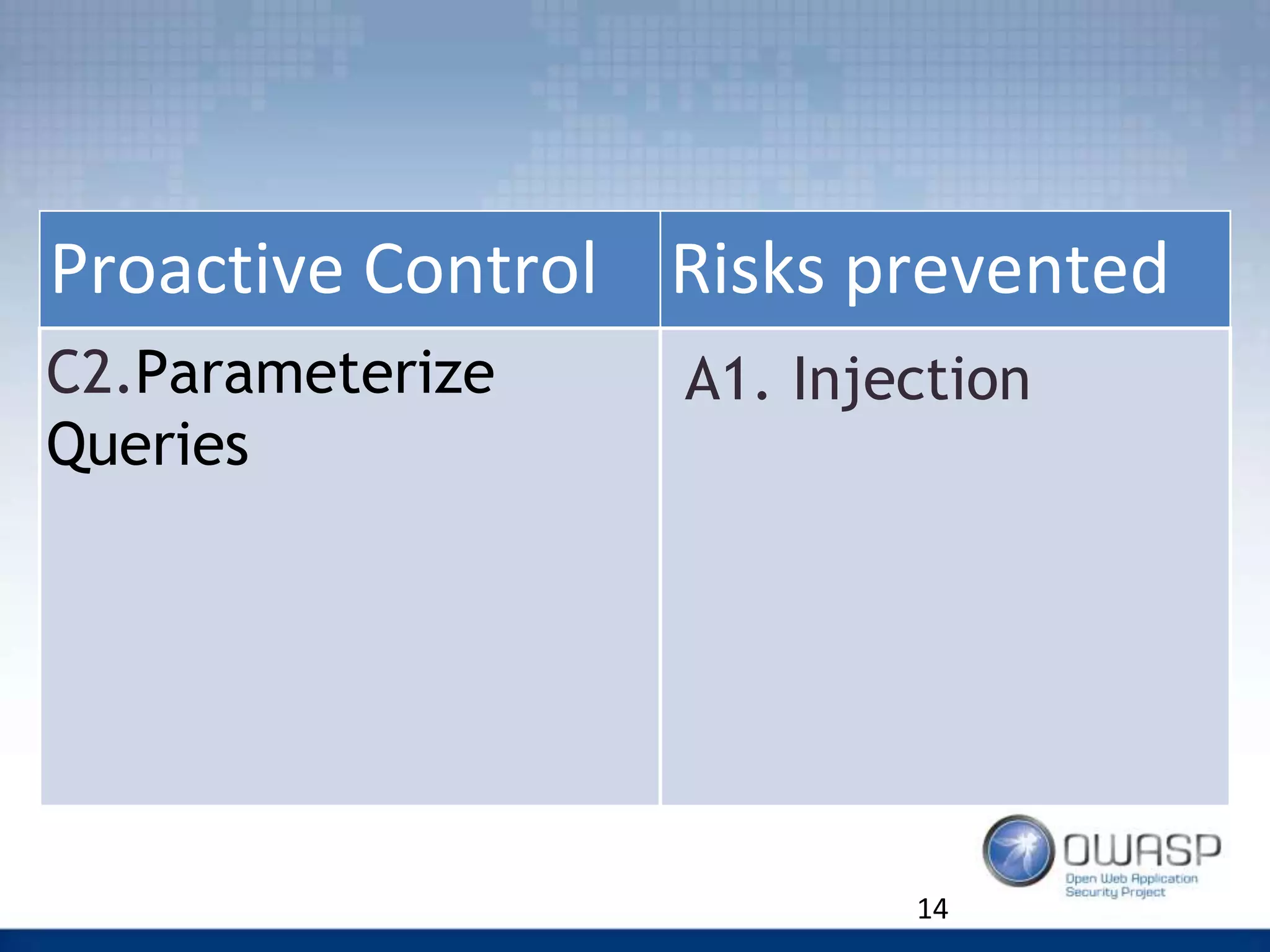
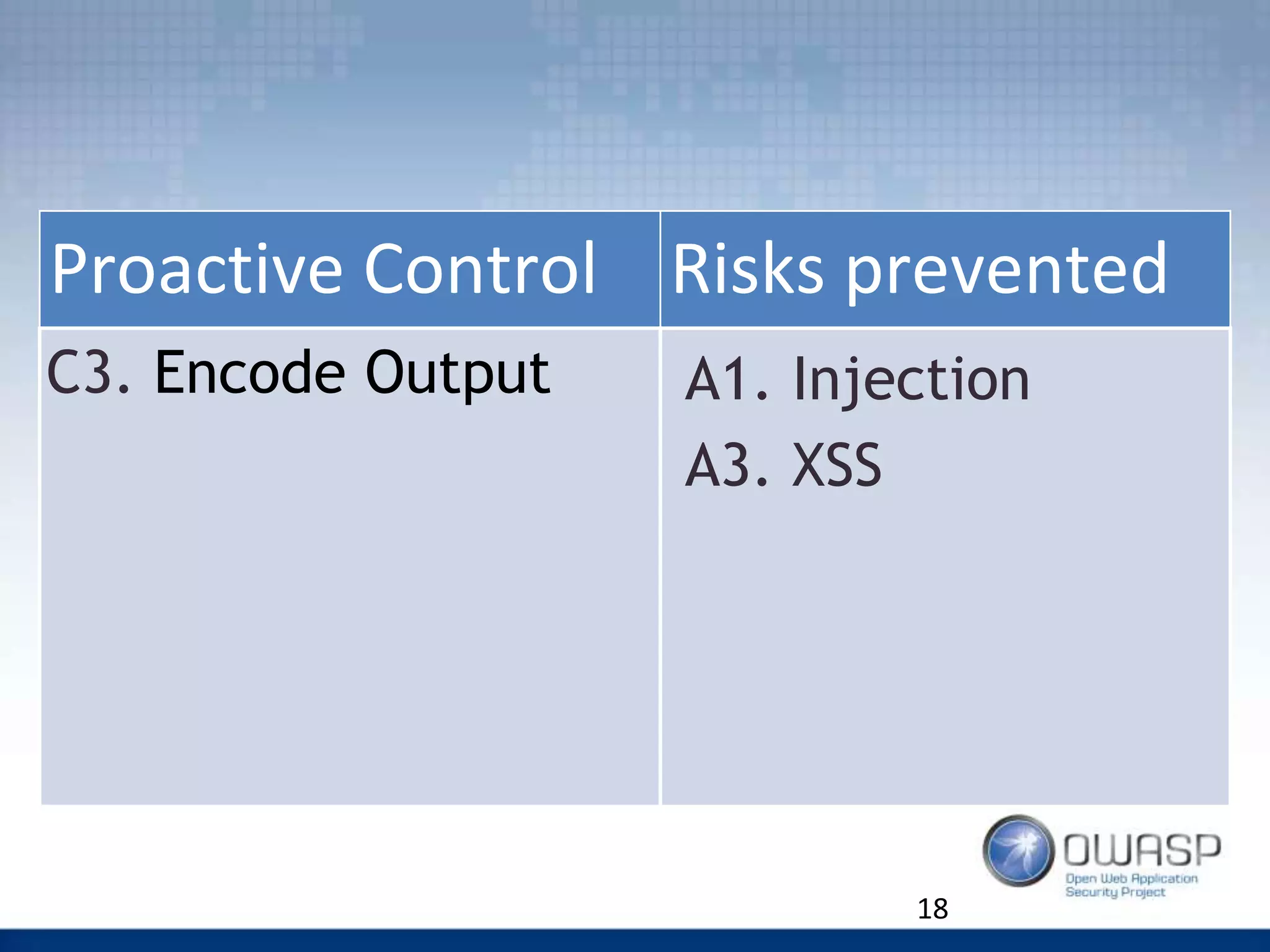
Example of Query Parametrisation
C2. Control: Data Access Layer
11
How not to do it !](https://image.slidesharecdn.com/phpnorthwest2016katyanton-161003201031/75/OWASP-Top-10-Proactive-Controls-11-2048.jpg)
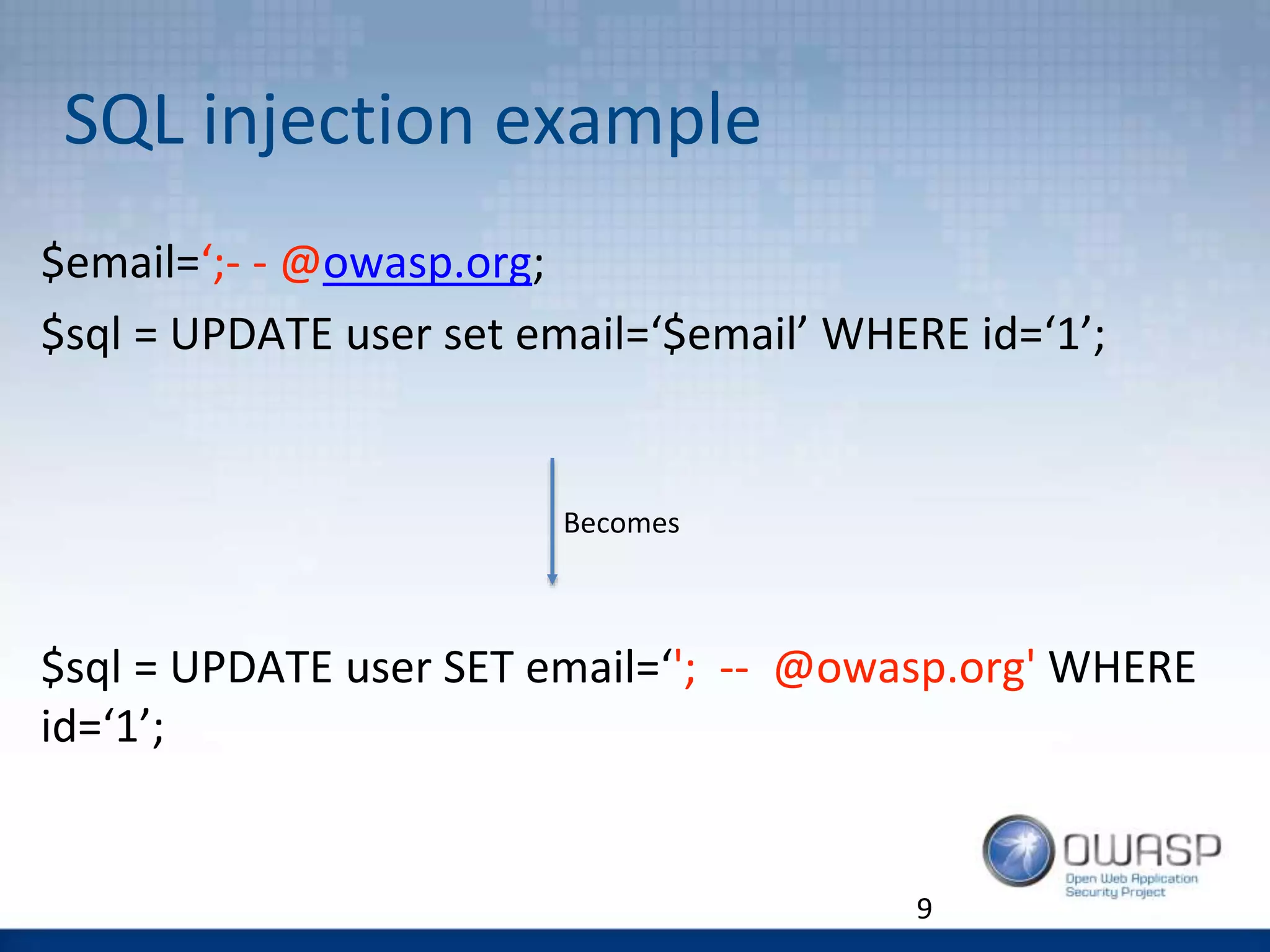
![C2: How NOT to
$sql = ”Update users set email=$_GET[‘email’] where
id=$id”
This one string combines both the code and the input.
SQL parser cannot differentiate between code
and user input.
12](https://image.slidesharecdn.com/phpnorthwest2016katyanton-161003201031/75/OWASP-Top-10-Proactive-Controls-12-2048.jpg)





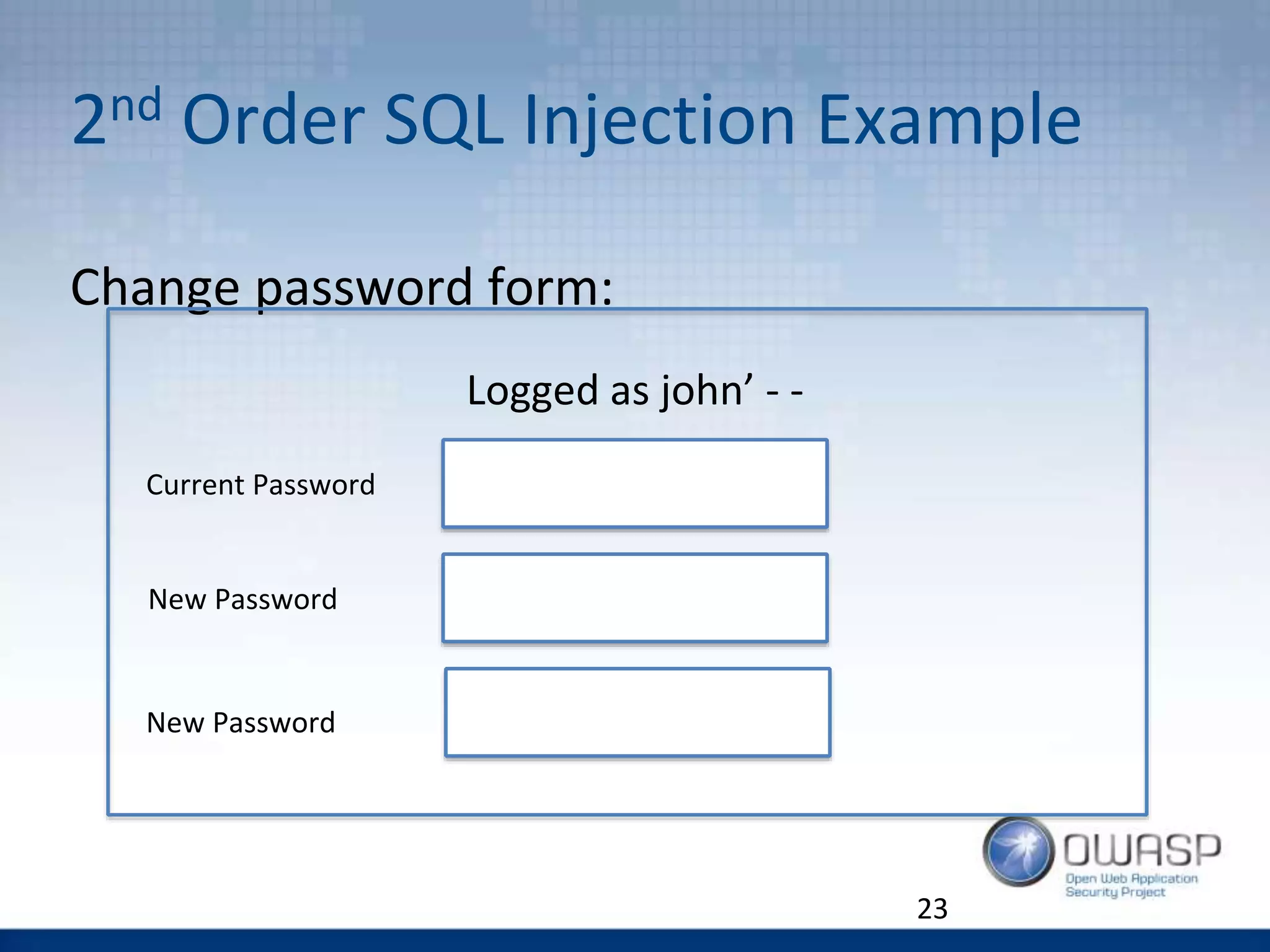
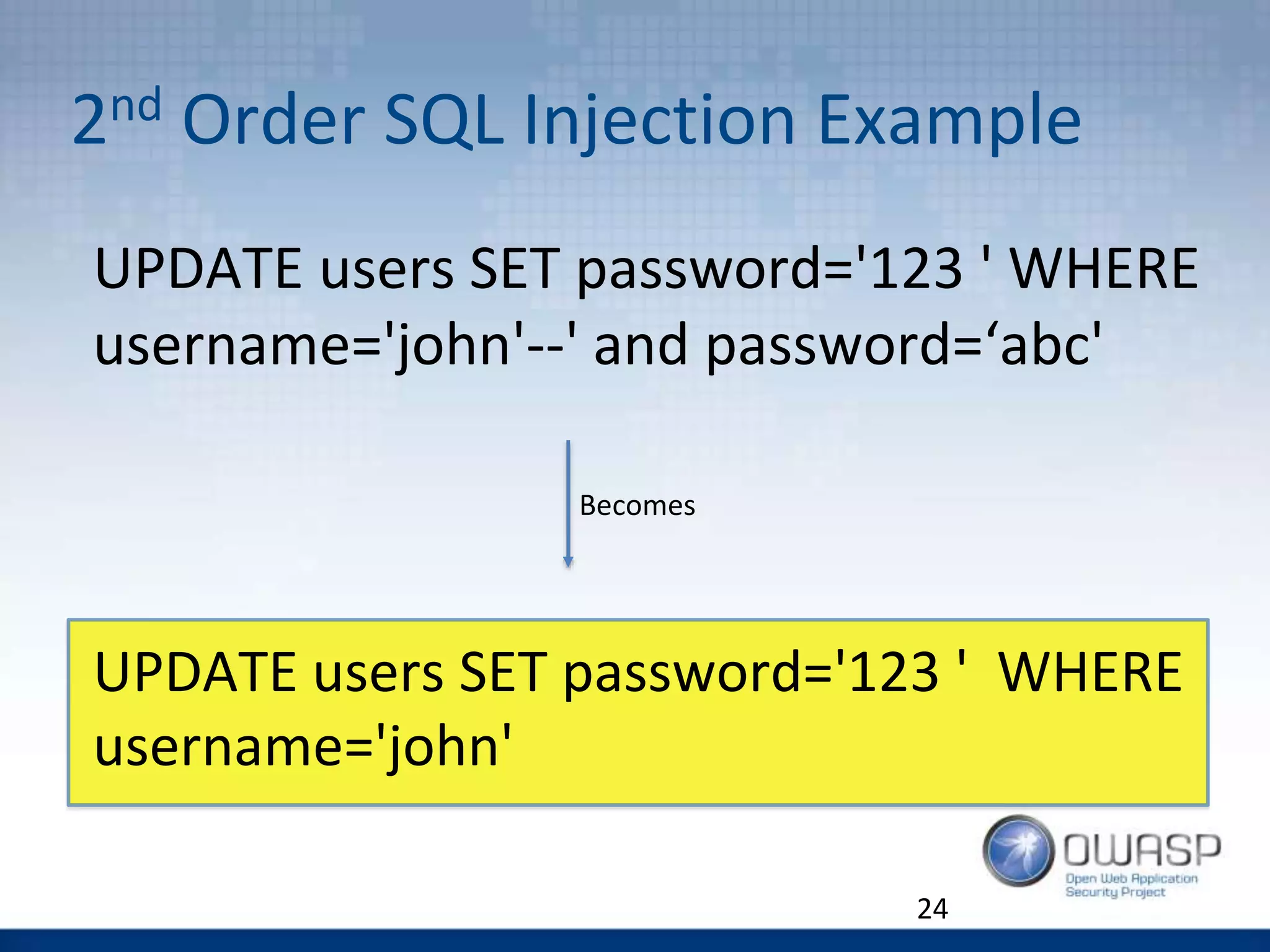




![C5. Password storage – How Not To
$password=bcrypt([salt] + [password],
work_factor);
$loginkey =md5(lc([username]).”::”.lc([password]))
Be consistent when storing sensitive data!
30](https://image.slidesharecdn.com/phpnorthwest2016katyanton-161003201031/75/OWASP-Top-10-Proactive-Controls-30-2048.jpg)