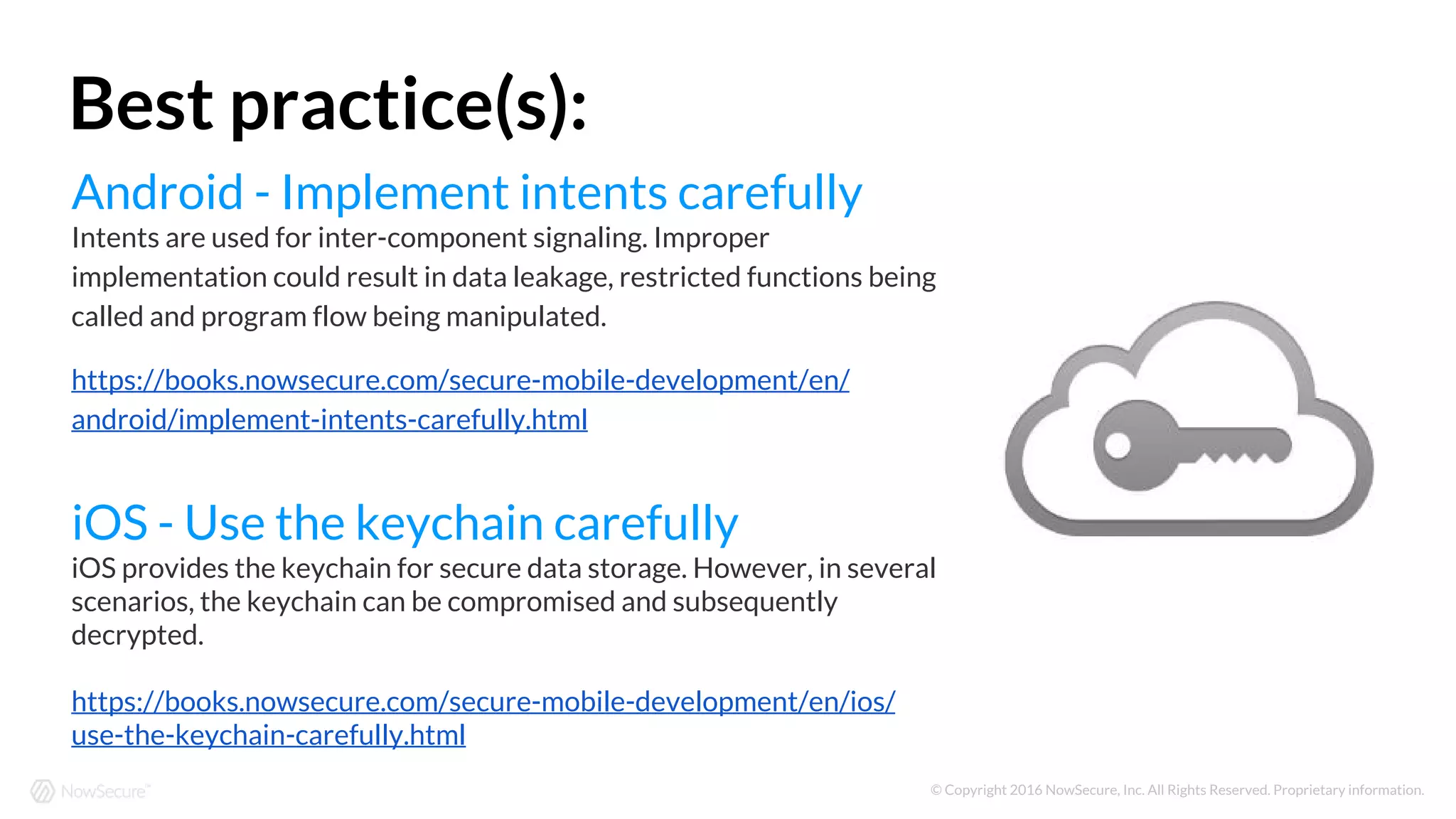
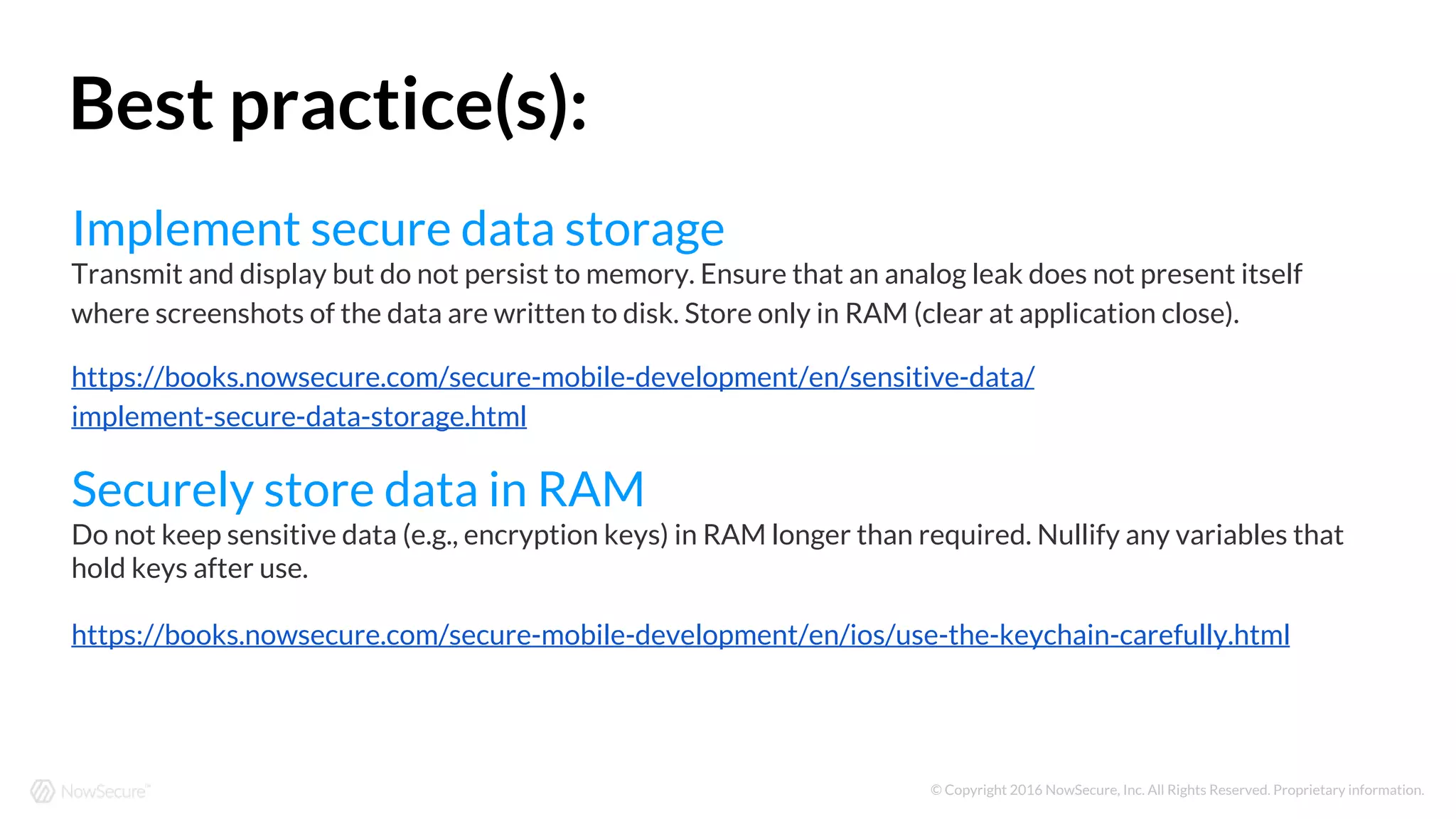
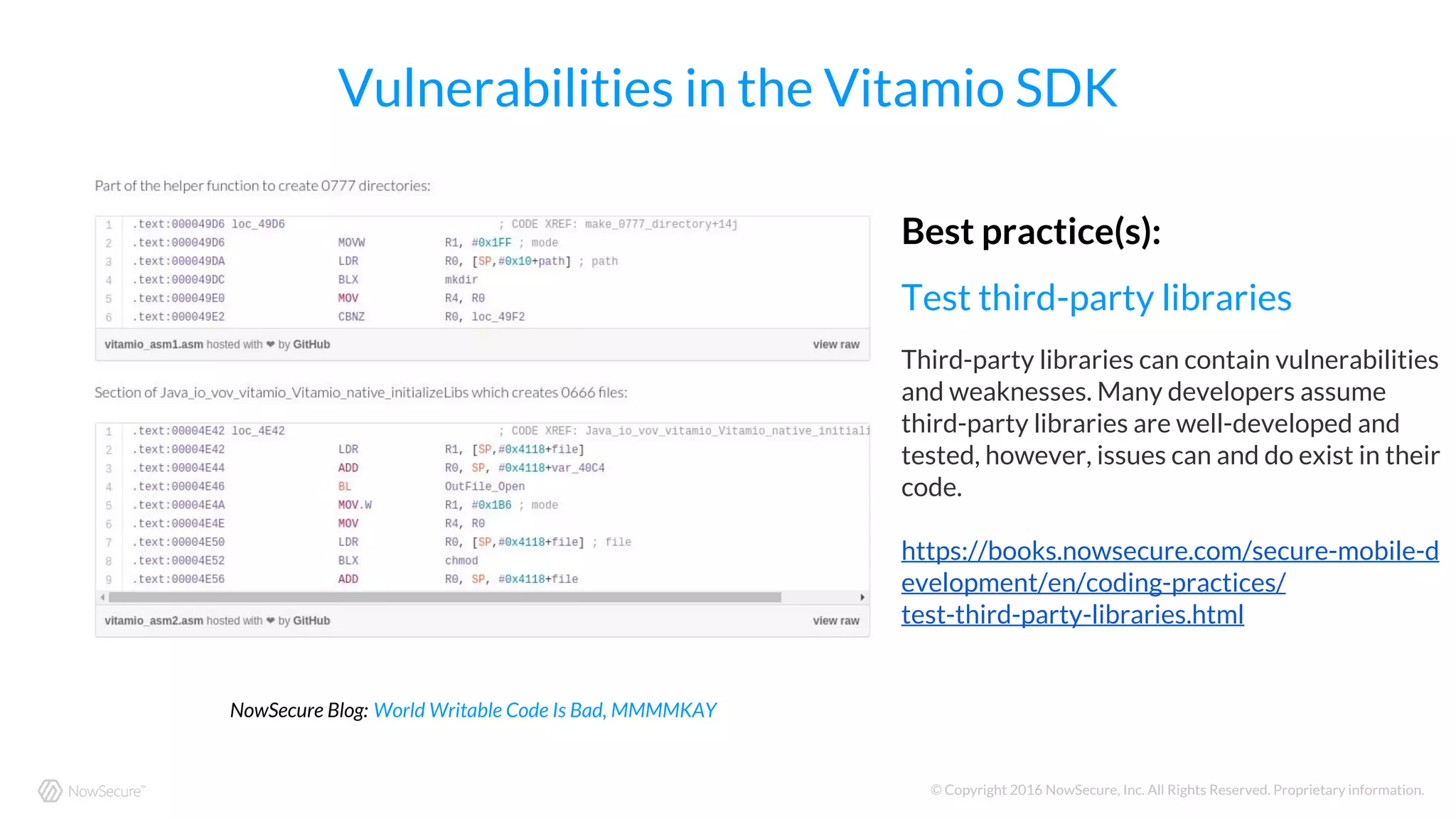
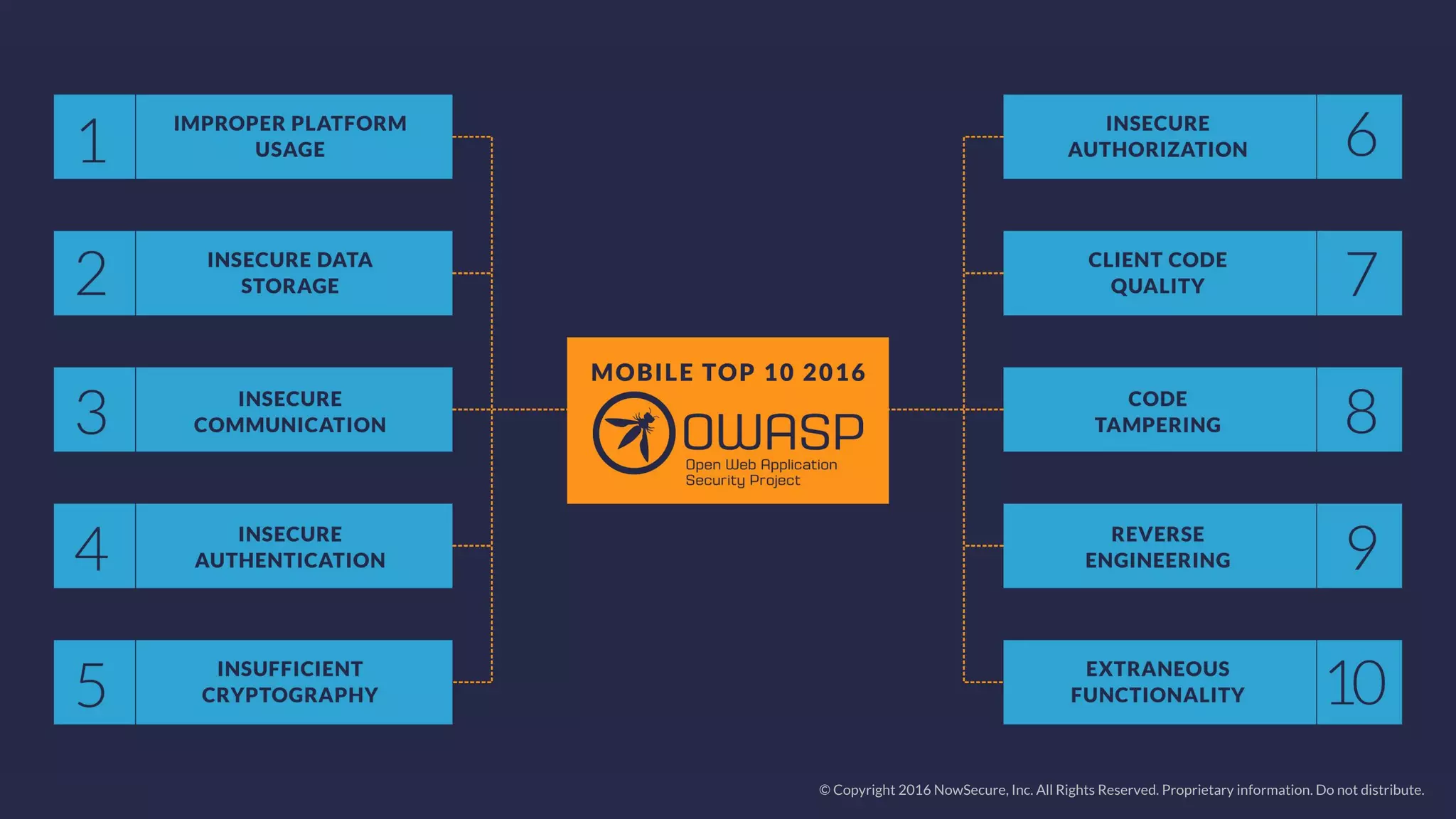
The document outlines the OWASP Top 10 mobile risks and best practices for secure mobile development as identified by NowSecure. Key risks include improper platform usage, insecure data storage, insecure communication, and insufficient cryptography, each with recommended mitigations to enhance app security. It emphasizes the importance of secure coding practices and managing risks associated with third-party libraries, authentication, and app functionality.