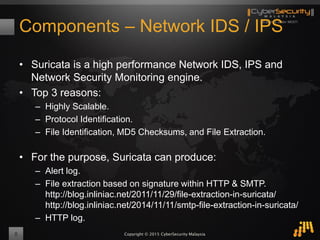
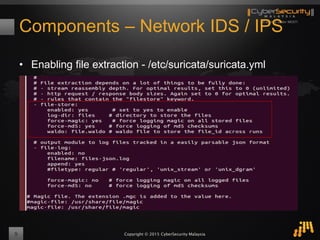
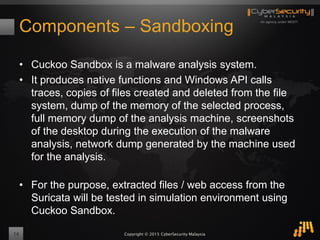
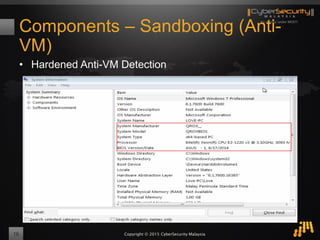
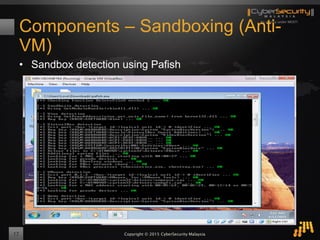
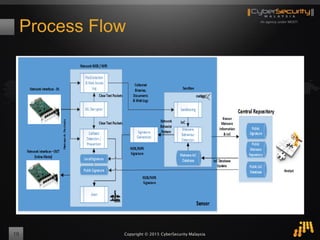
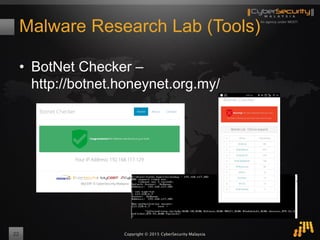
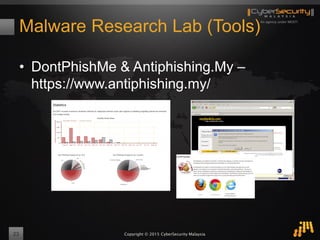
The document outlines a proof of concept for zero-day malware detection and prevention using open-source software by the Cybersecurity Malaysia team. It discusses the need for advanced security measures due to the increasing sophistication of malware-centric cyber attacks, introduces various open-source components and tools, and details the process for capturing and analyzing malicious content in a network environment. Furthermore, it emphasizes the importance of collaboration and continuous improvement in detection and remediation strategies against cyber threats.