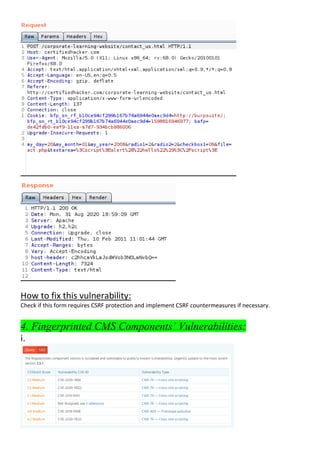
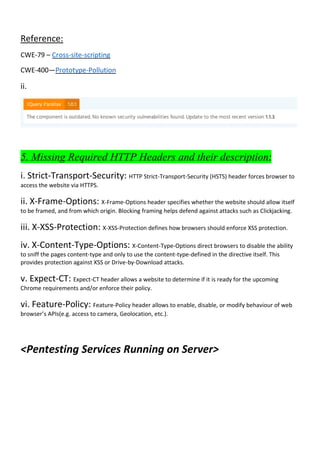
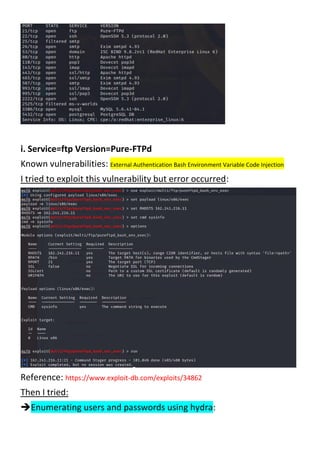
The document details a penetration testing assessment of the website certifiedhacker.com, revealing various vulnerabilities including Cross-Site Scripting (XSS) and HTML forms lacking CSRF protection, which could lead to unauthorized actions by attackers. It highlights the server's infrastructure, the operational technologies in use, and notes that despite some minor vulnerabilities, the overall website security appears to be fairly robust. Additionally, the testing uncovered a directory listing and recommended implementing strict security measures for embedded external content and missing HTTP headers.


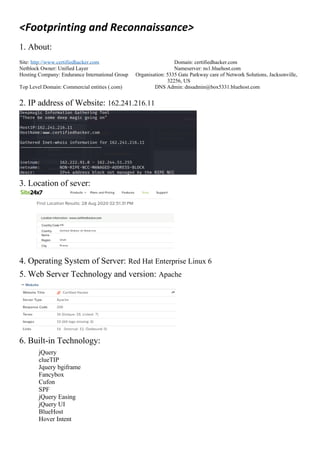


![Content-Encoding: gzip
host-header: c2hhcmVkLmJsdWVob3N0LmNvbQ==
Content-Range: bytes 0-274/275
Content-Length: 275
Keep-Alive: timeout=5, max=54
Connection: Keep-Alive
Content-Type: text/html; charset=UTF-8
<!-- PHP Wrapper - 500 Server Error -->
<html><head><title>500 Server Error</title></head>
<body bgcolor=white>
<h1>500 Server Error</h1>
A misconfiguration on the server caused a hiccup.
Check the server logs, fix the problem, then try again.
<hr>
URL: http://certifiedhacker.com/P-folio/images/500.php/.htaccess.aspx-->">'>'"<sfi000317v352289><br>
</body></html>
=== END OF DATA ===
Possible remediations or prevention methods:
Avoiding client side document rewriting, redirection, or other sensitive actions, using client side data.
Analysing and hardening the client side (Javascript) code.
Reference: https://www.a2hosting.in/kb/developer-corner/php/500-internal-server-error-while-running-php
https://owasp.org/www-community/attacks/xss/
2. External content embedded on a page
Vulnerability Description:
External content embedded on a page means something isn't right with the site – wrong – yet some way or
another we appear to continue building sites that do. This can prompt issues, for example identity theft. The
content is usually sent through email and directs users to an http site instead of https.
Affected Items:
→Higher Risk:-
http://certifiedhacker.com/Online%20Booking/
Memo:
http://www.google.com/jsapi?autoload={'modules':[{name:'maps',version:3,other_params:'sensor=false'}]}
→Lower Risk:-
http://certifiedhacker.com/Turbo%20Max/js/jquery.prettyPhoto.js
Memo: http://www.youtube.com/v/'+grab_param('v',images[setPosition])+'](https://image.slidesharecdn.com/pentest-project-cert-merged-220123154228/85/Penetration-Testing-Report-7-320.jpg)