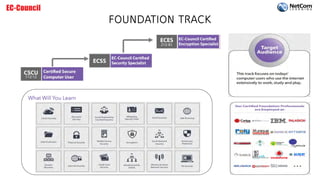
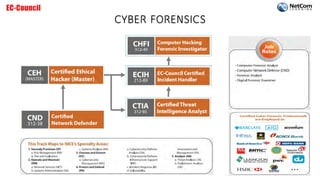
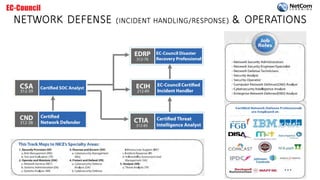
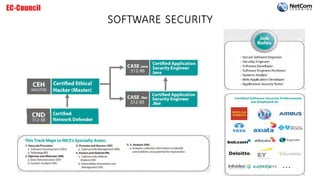
The document outlines the EC-Council certification roadmap and course catalog provided by NetCom Learning, highlighting various cybersecurity training tracks, including ethical hacking, network defense, and cyber forensics. It offers details on multiple certifications such as Certified Ethical Hacker (CEH) and Certified Network Defender (CND), including their schedules and associated costs. NetCom Learning is portrayed as an accredited training partner that ensures quality instruction in essential cybersecurity skills, endorsed by prominent government agencies.