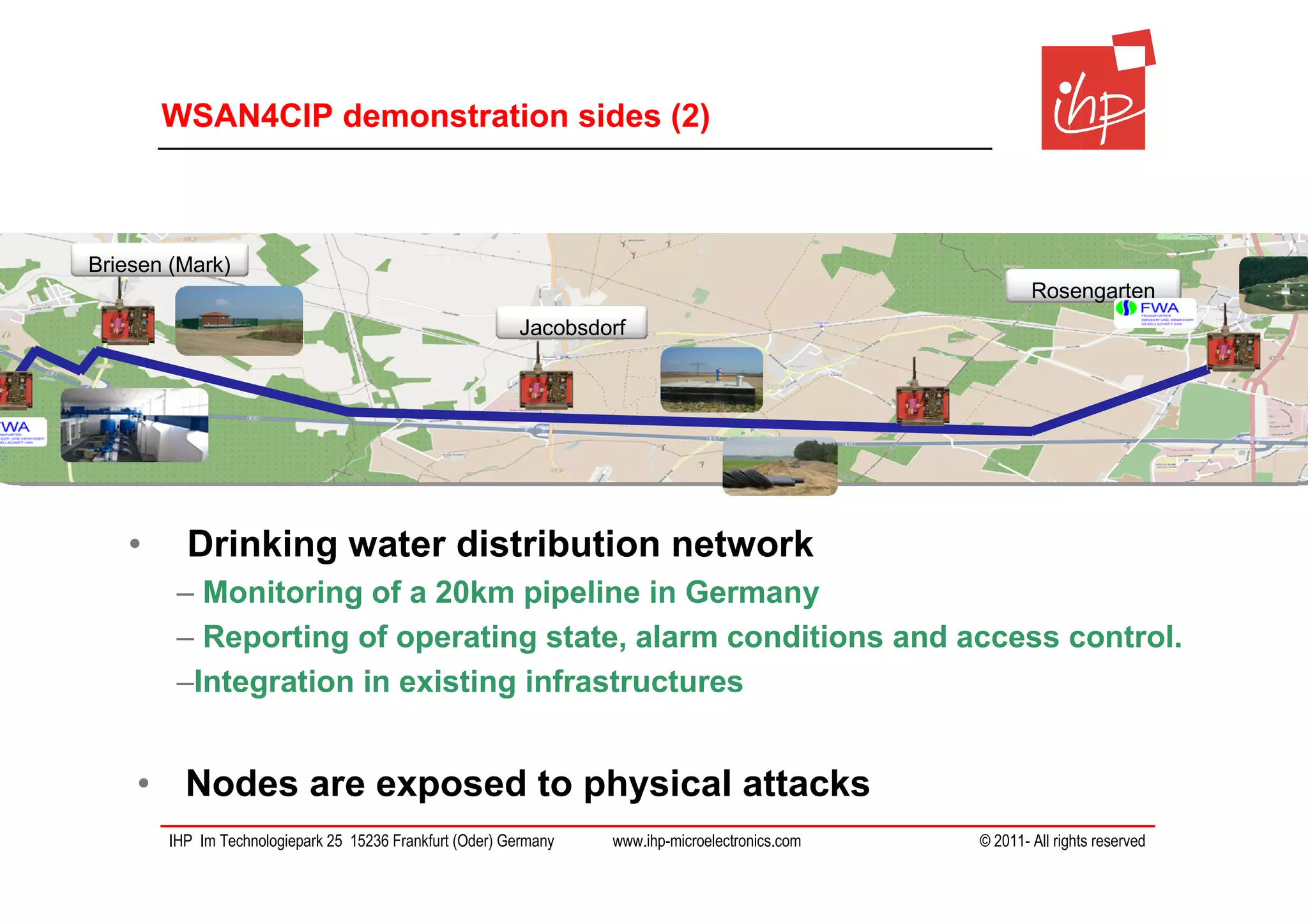
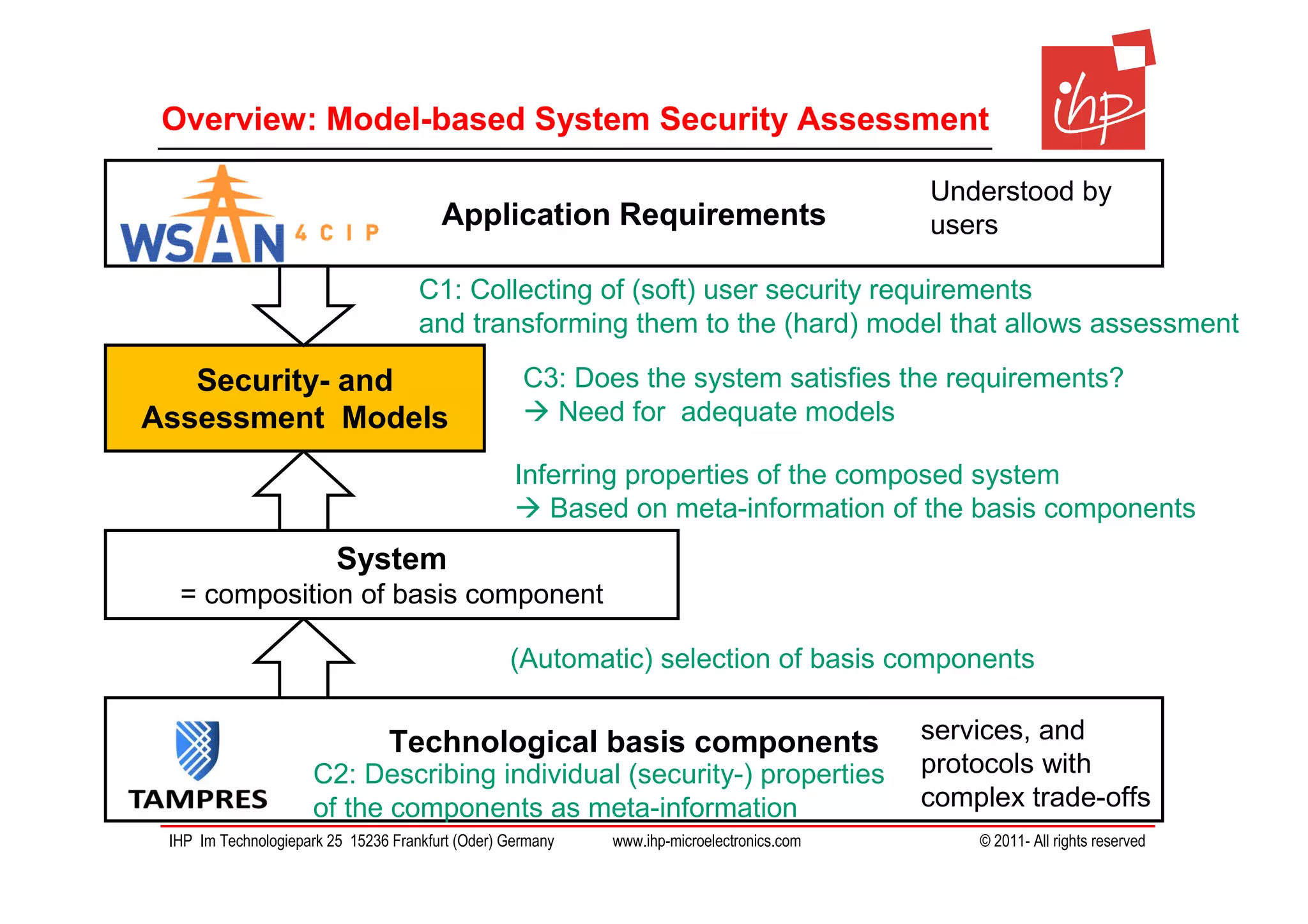
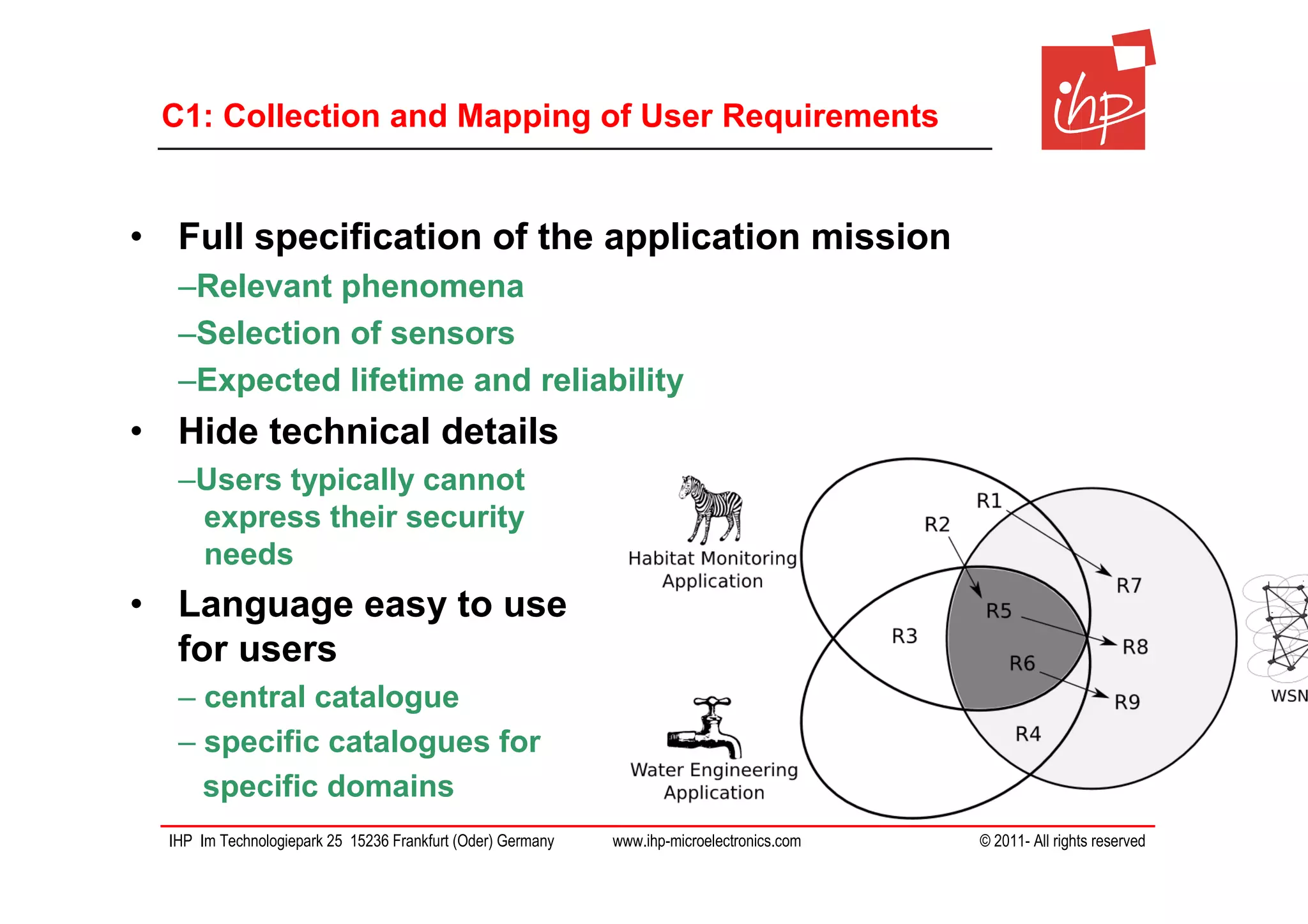
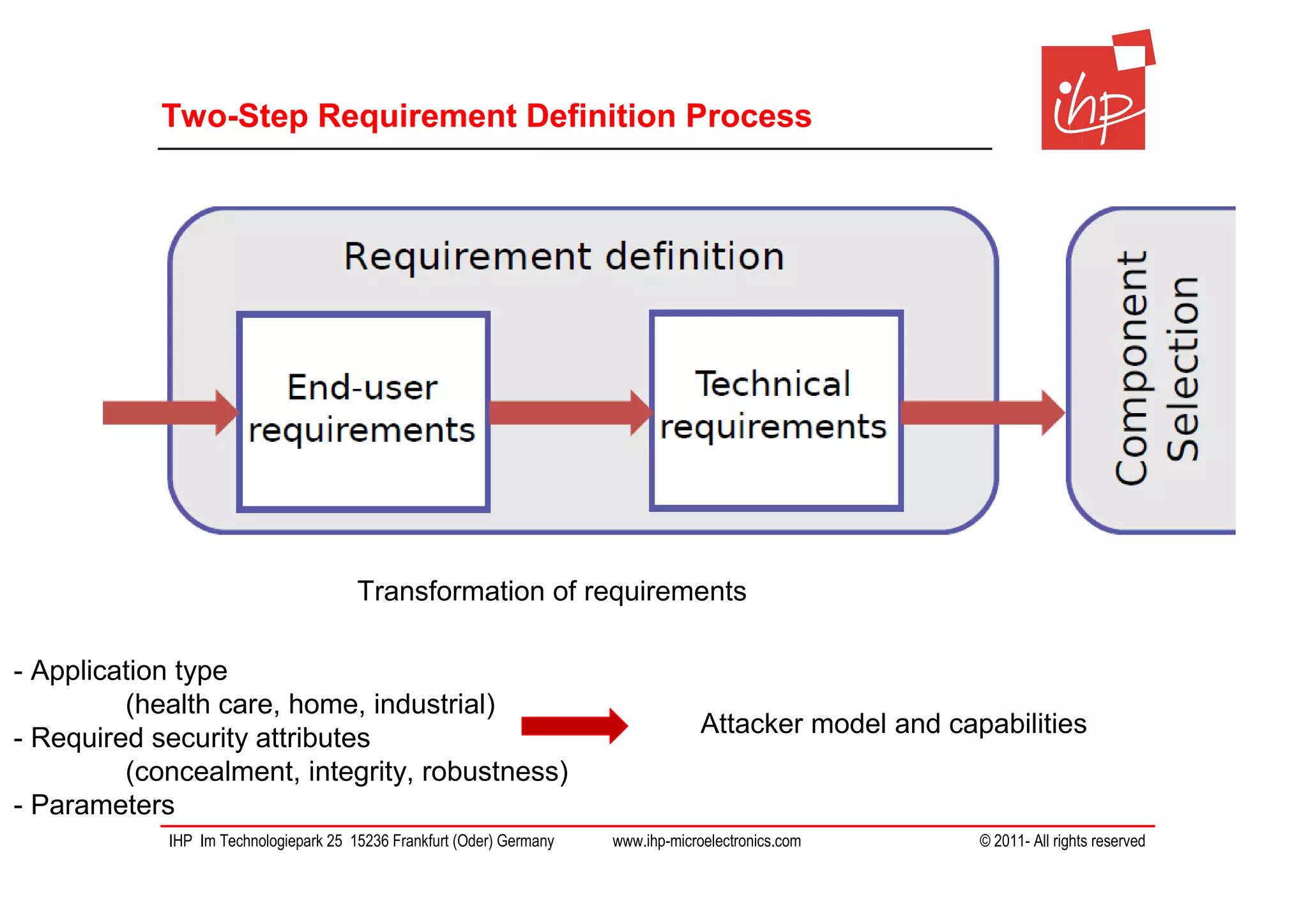
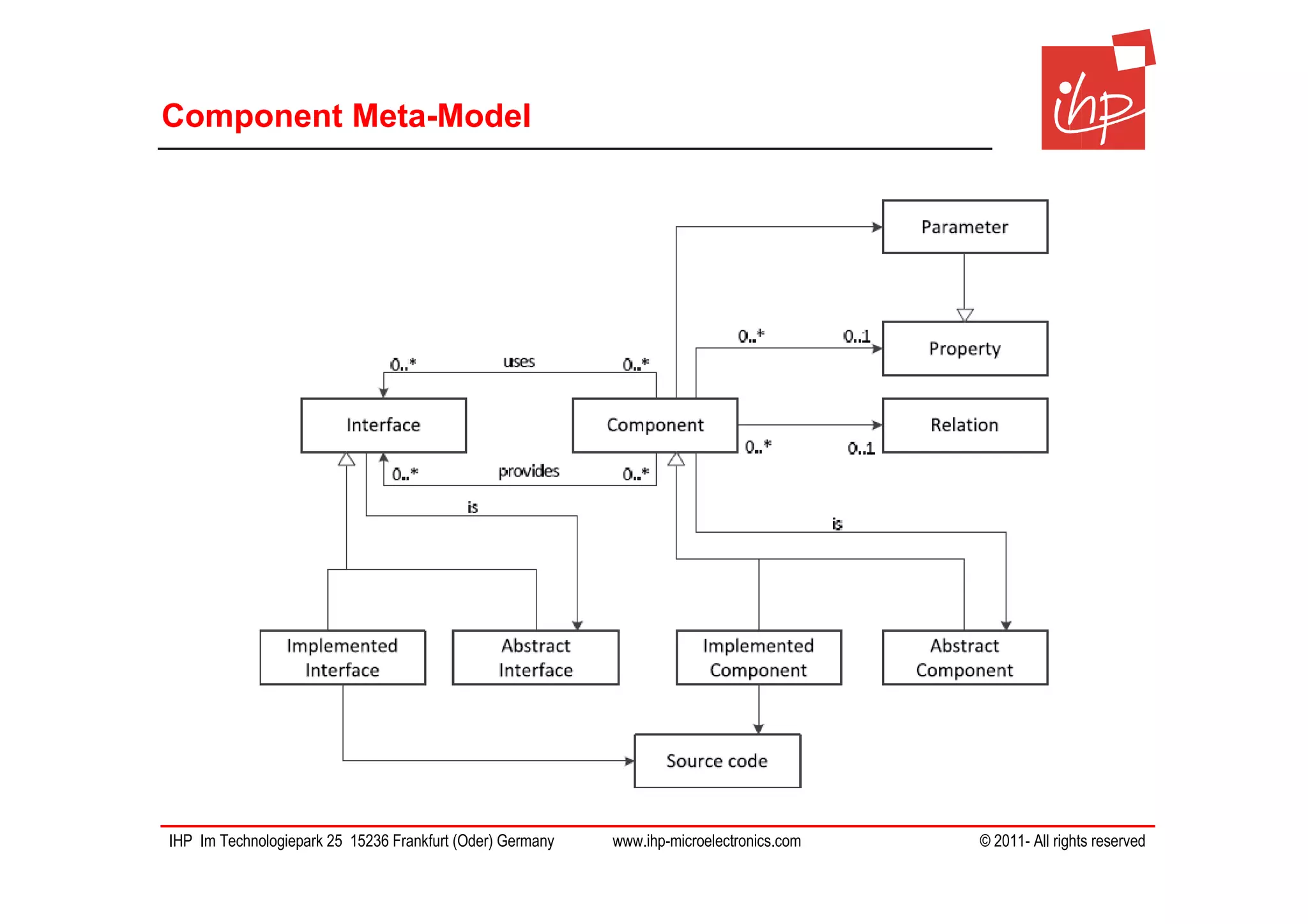
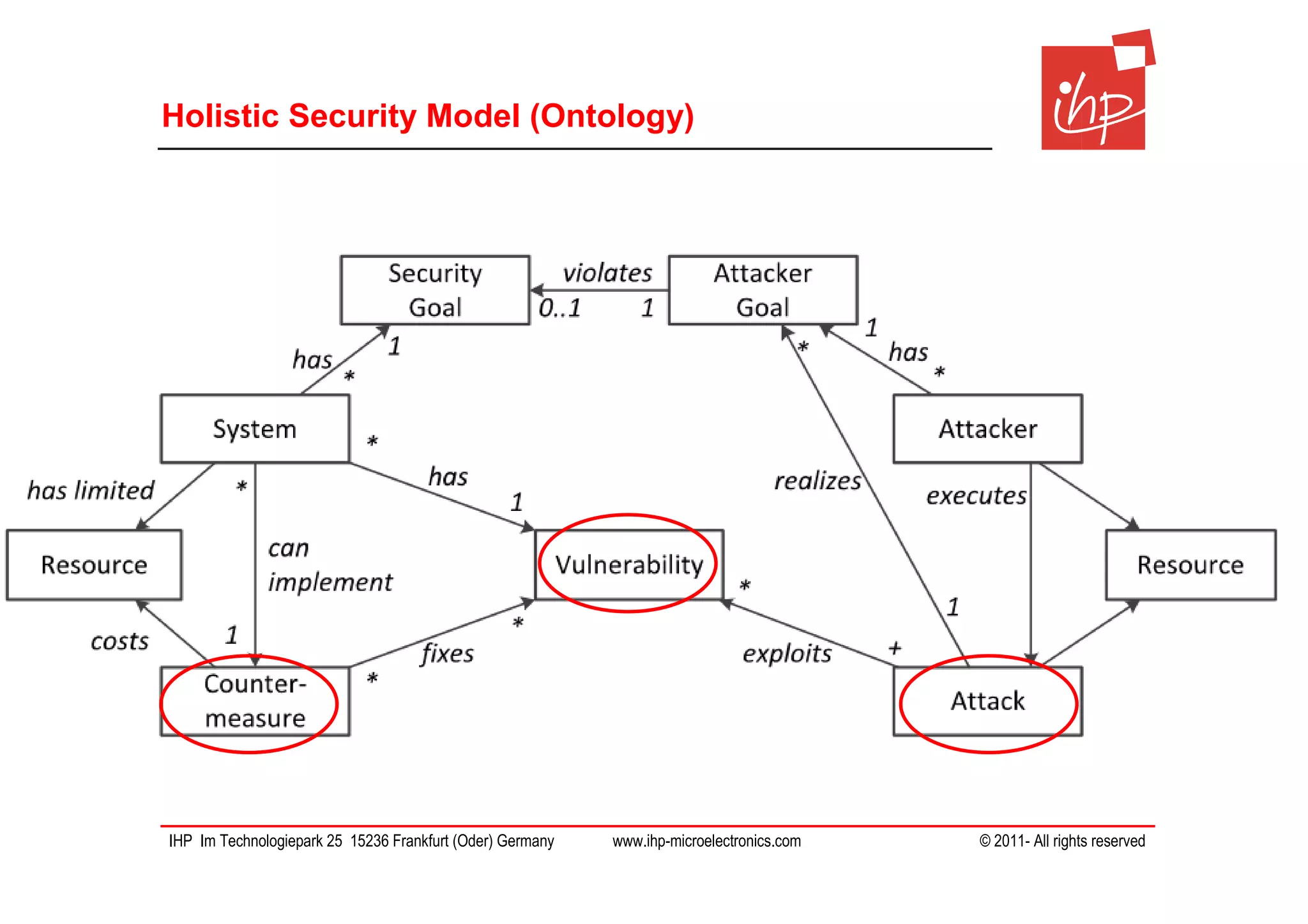
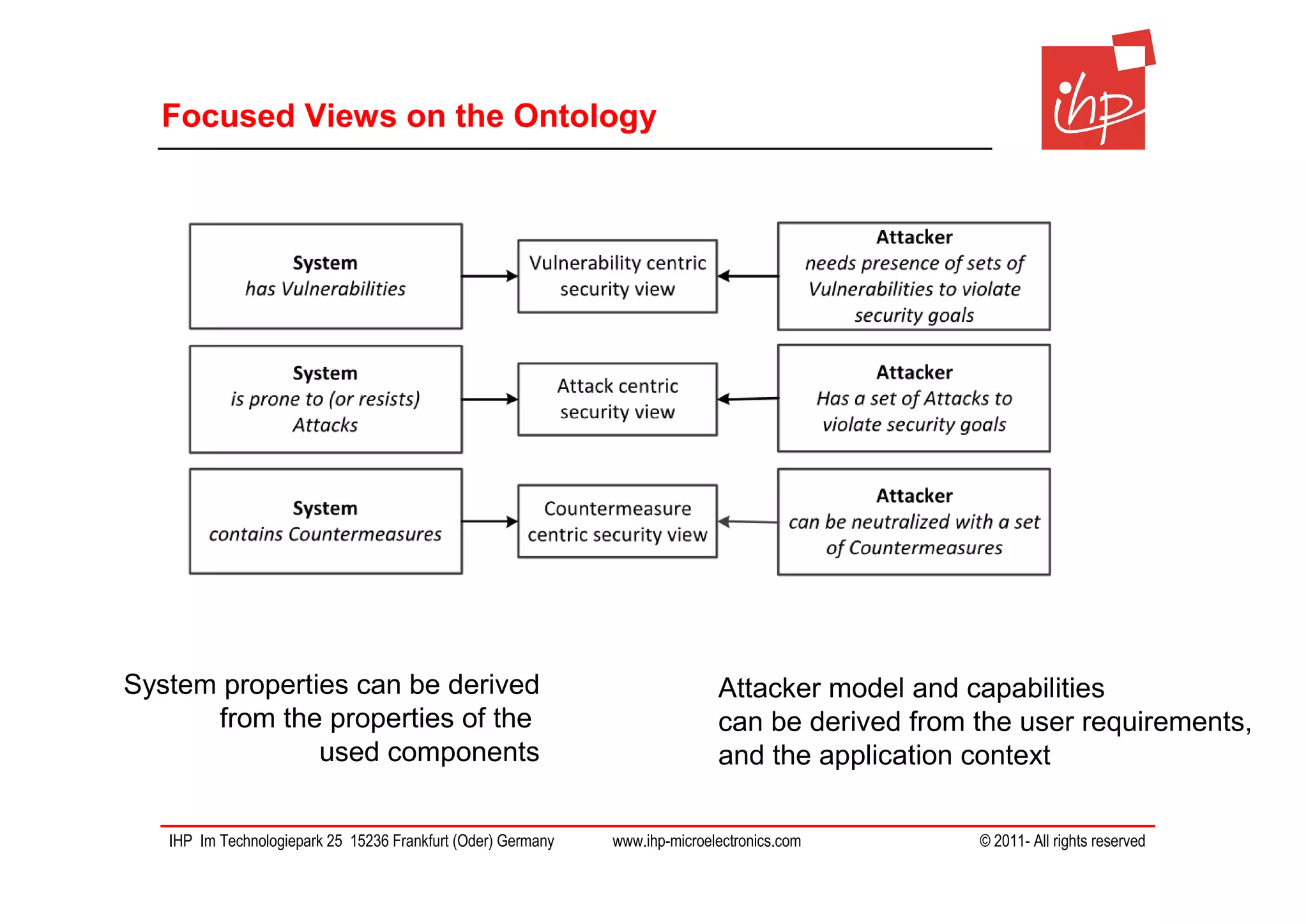
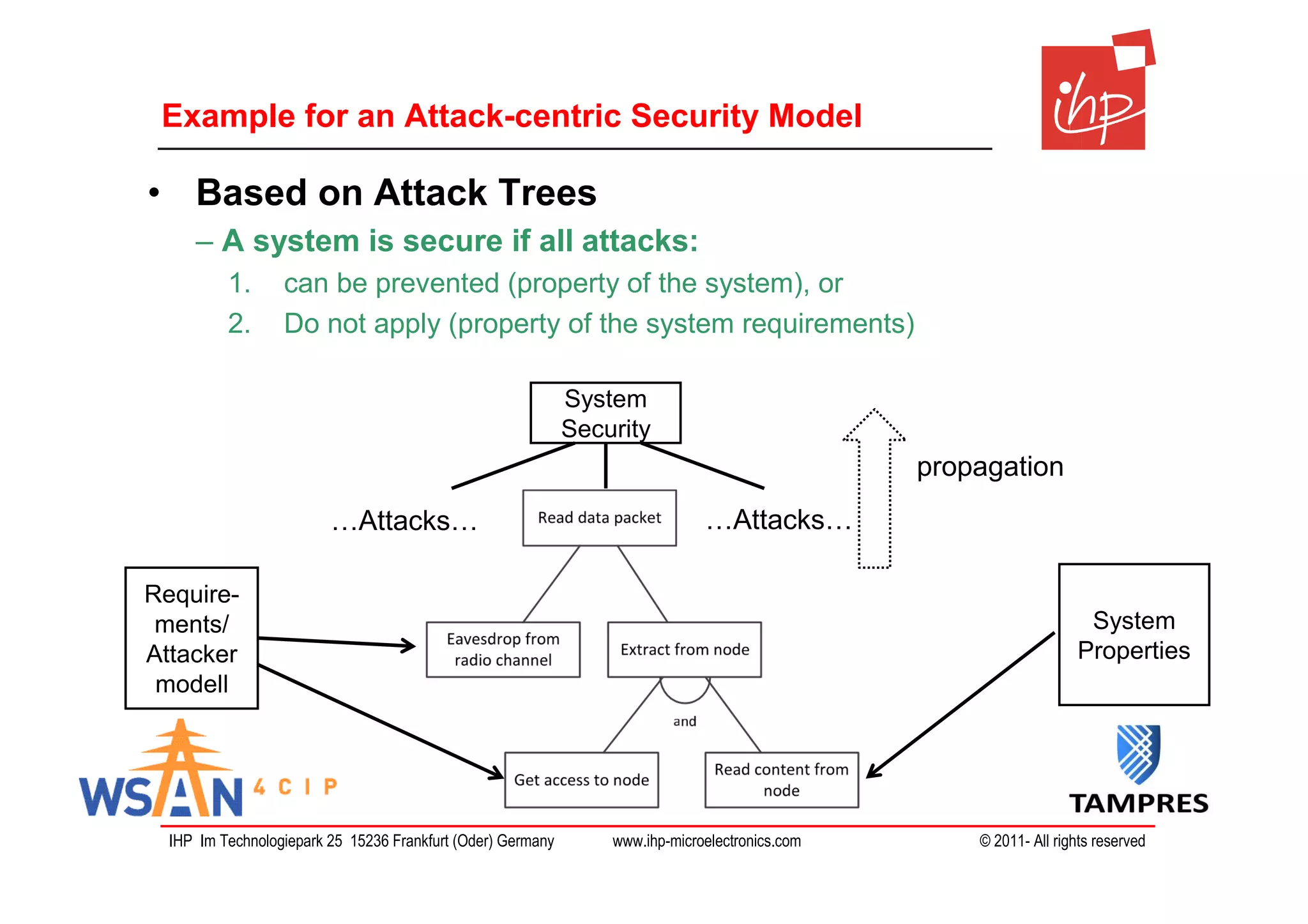
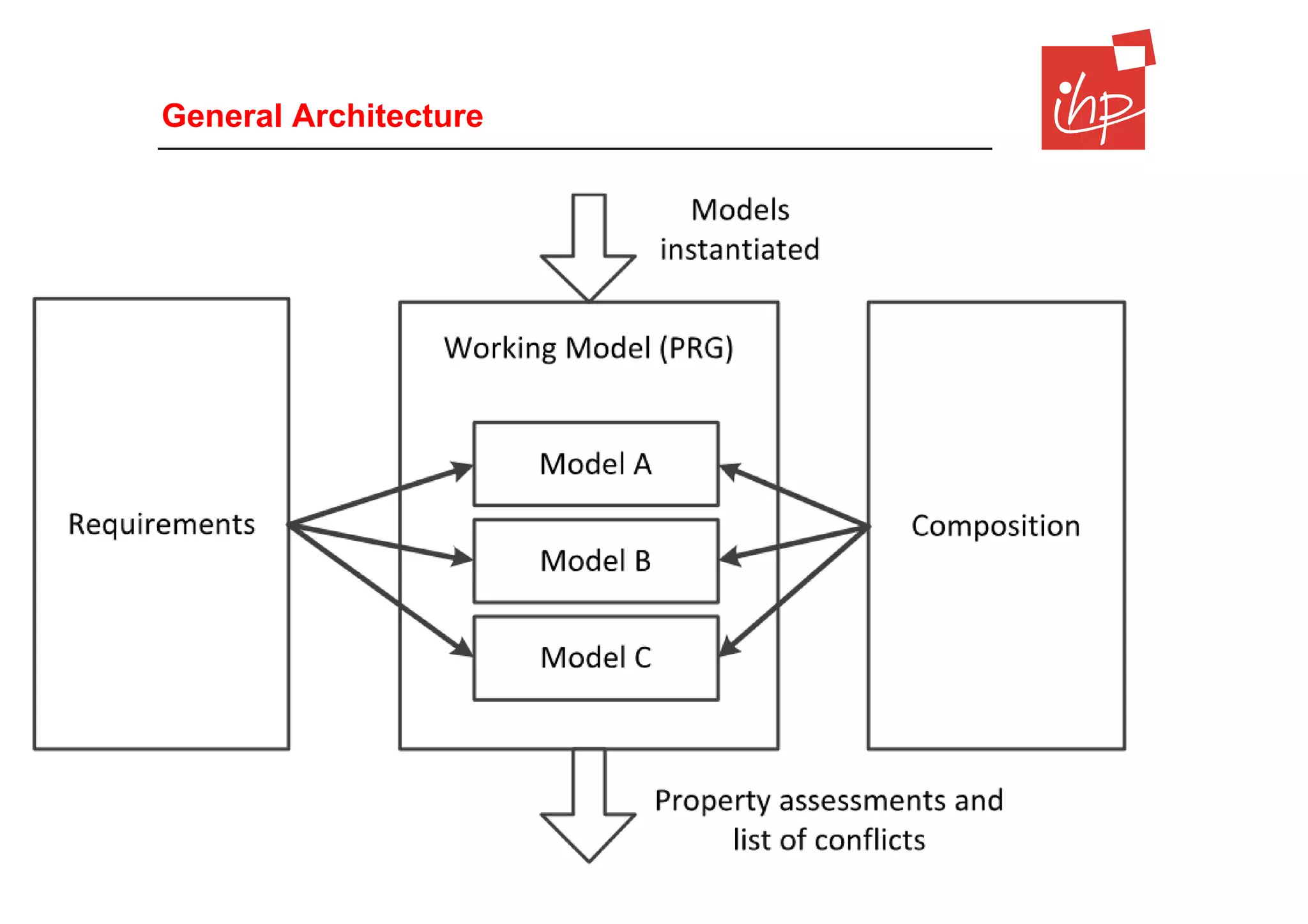
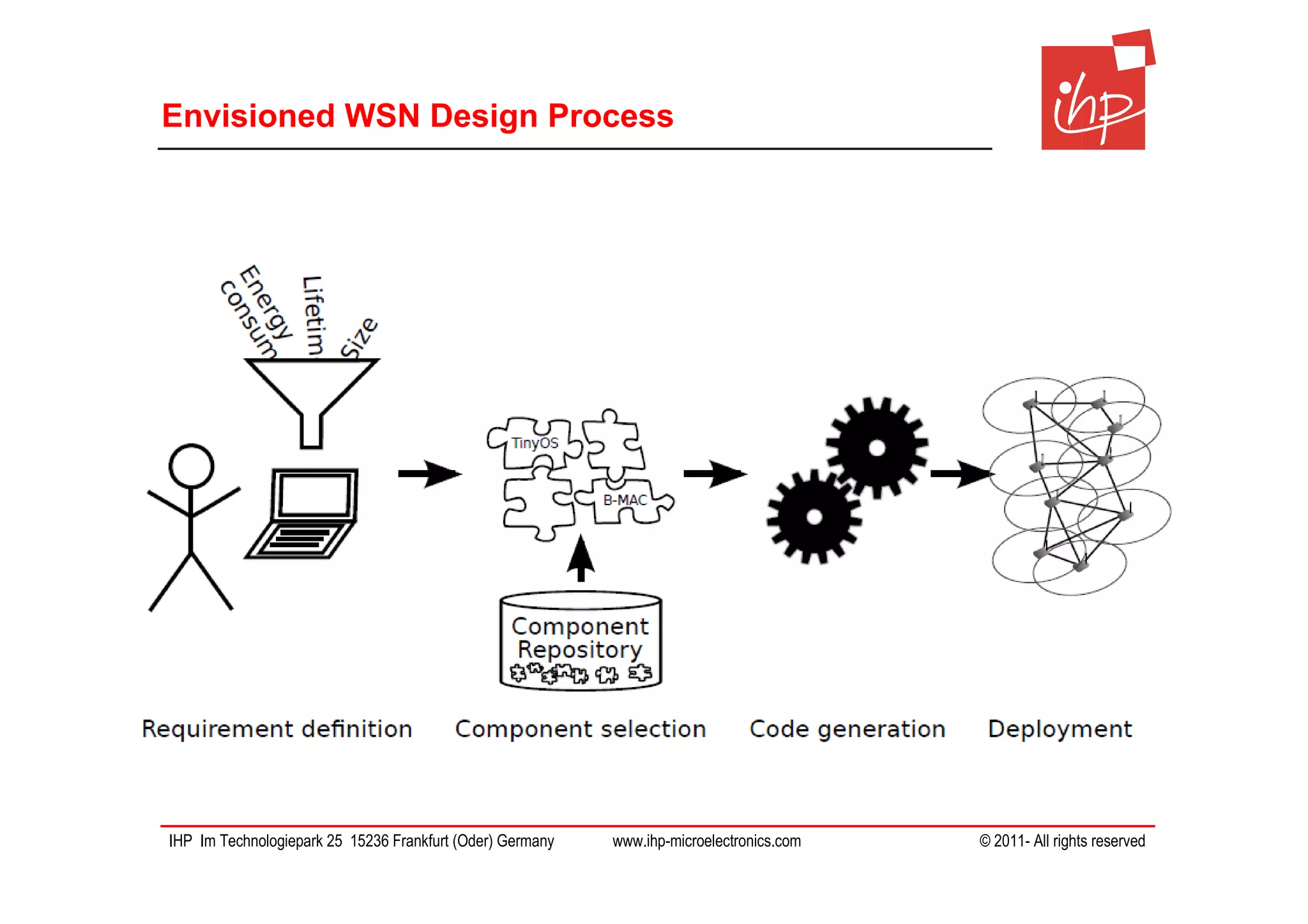
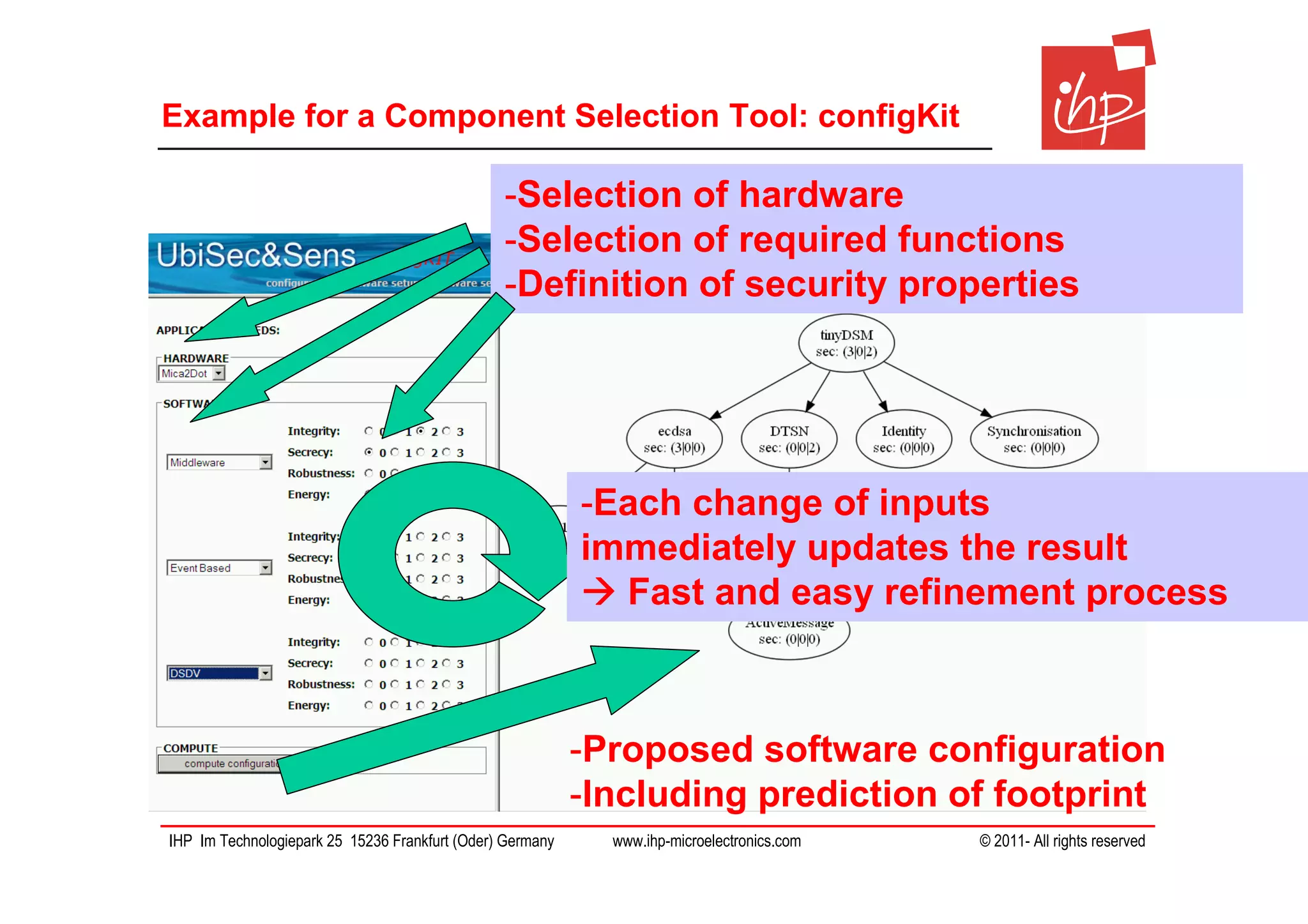
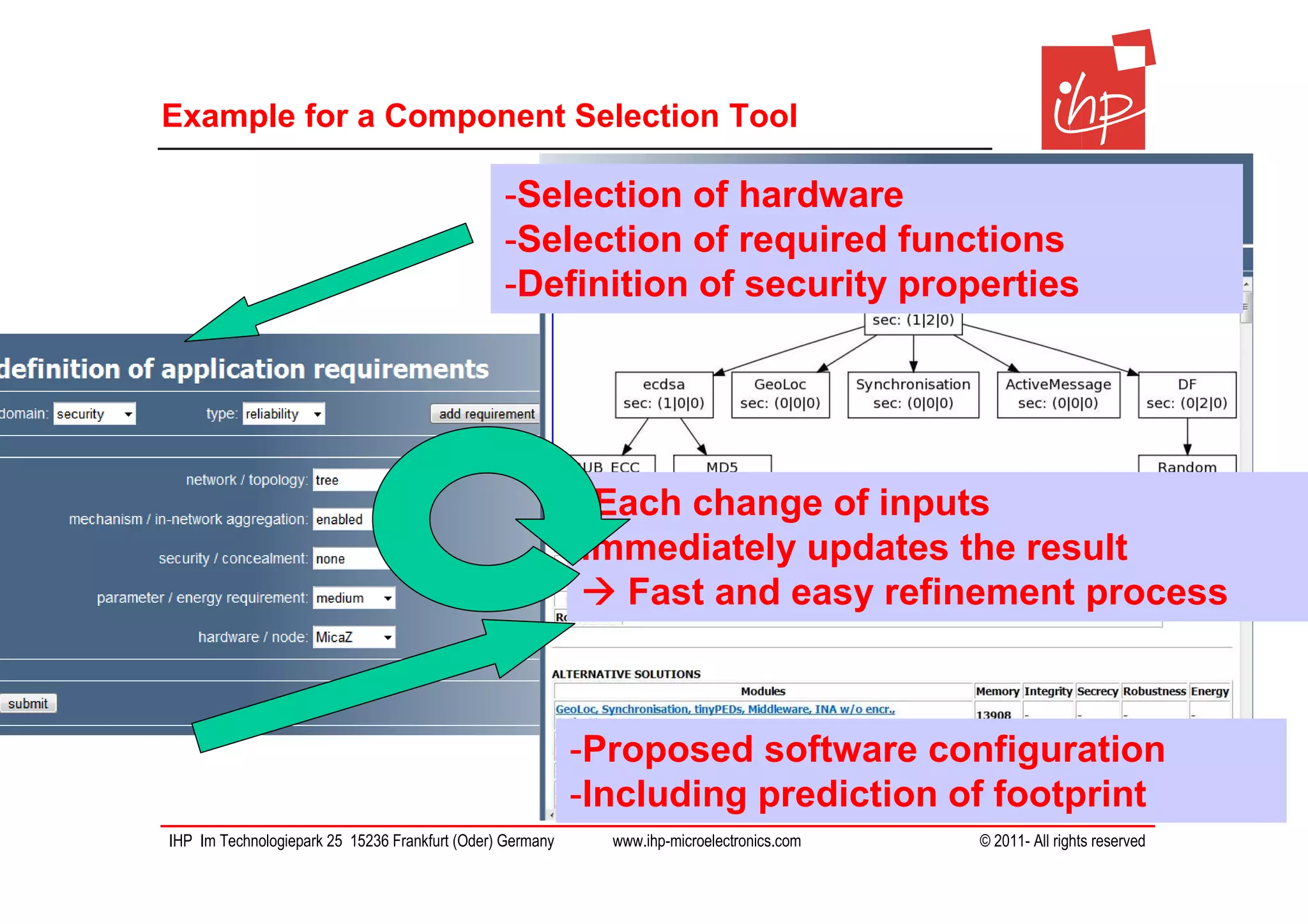
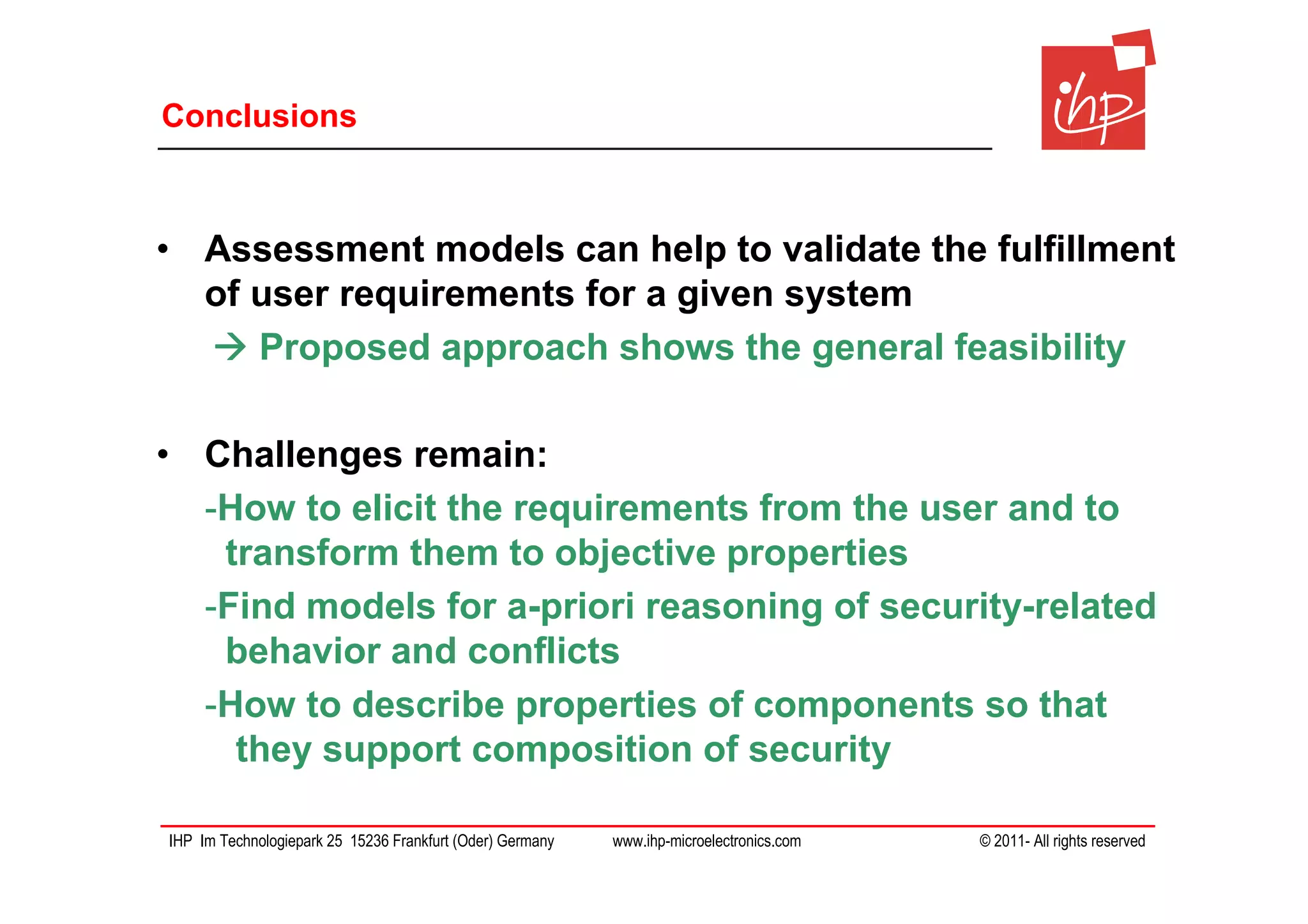
The document discusses using assessment models to improve the usability and security of wireless sensor networks (WSNs). It proposes a model-based approach involving (1) collecting and mapping user security requirements, (2) describing component properties and how they compose, and (3) defining security models to assess whether requirements are satisfied. The approach aims to bridge the gap between users and technical implementation. An example security model uses attack trees to evaluate if attacks can be prevented or don't apply given the system and requirements.