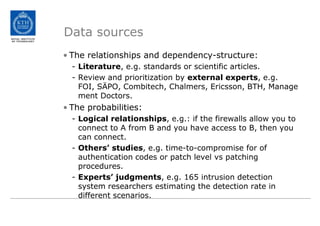
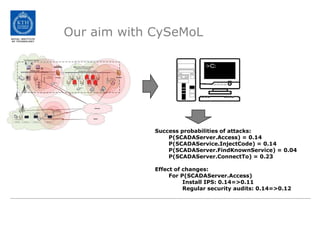
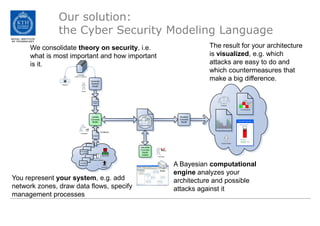
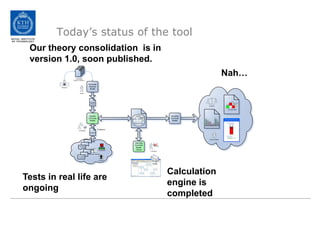
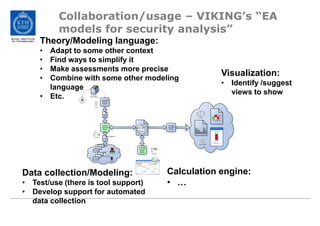
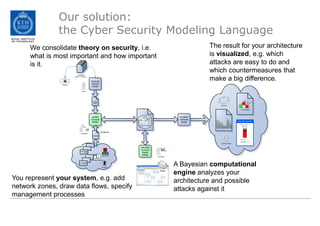
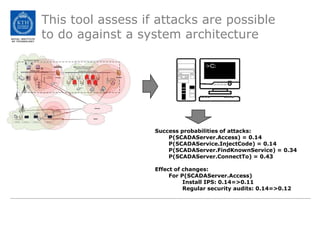
The document discusses the Cyber Security Modeling Language (CySeMoL) tool developed by the VIKING project. The tool allows users to model their system architecture, visualize potential attacks, and calculate success probabilities of attacks. It consolidates security theory to identify the most important factors that influence attack success. The tool is currently being tested in real-life cases and the developers are seeking collaboration to improve the modeling language, calculation engine, and data collection capabilities.




![[Qualitative theory]The metamodelAttribute dependenciesFor example:The probability that Remote Arbitrary Code Exploits on a Service can be performed depend on:If you can connect to the ServiceIf it has a high-severity vulnerabilityThe attacker can authenticate itself as a legitimate userIf its OS uses ASLR or NX memory protectionIf there is Deep Packet Inspection Firewall between the attacker and Service](https://image.slidesharecdn.com/2-viking-sommestad-110802044231-phpapp02/85/VIKING-cluster-meeting-1-9-320.jpg)
![[Quantitative theory]Example:Remote Arbitrary Code Exploits on a Service](https://image.slidesharecdn.com/2-viking-sommestad-110802044231-phpapp02/85/VIKING-cluster-meeting-1-10-320.jpg)
![Say that your architecture and our “rules” produces these dependencies[Quantitative theory]Canthis attack be done by professional penetration tester?](https://image.slidesharecdn.com/2-viking-sommestad-110802044231-phpapp02/85/VIKING-cluster-meeting-1-11-320.jpg)
![Our tool would answer:[Quantitative theory]1.00*0.24*1.00*0.51*1.00=0.1224=12.24% chance of success100%100%100%24%51%](https://image.slidesharecdn.com/2-viking-sommestad-110802044231-phpapp02/85/VIKING-cluster-meeting-1-12-320.jpg)
![What if analysis:Execute arbitrary code[Quantitative theory]Install a deep-packet-inspection firewall (IPS)As is.Remove Address Space Layout Randomization (ASLR)15 % probabilitythat the attacker canexecute his/hercode…24 % probabilitythat the attacker canexecute his/hercode…27 % probabilitythat the attacker canexecutehis/hercode……8 % for the attack scenario……12 % for the attack scenario……14% for the attack scenario…](https://image.slidesharecdn.com/2-viking-sommestad-110802044231-phpapp02/85/VIKING-cluster-meeting-1-13-320.jpg)