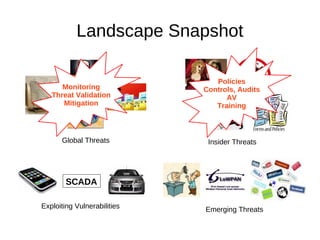
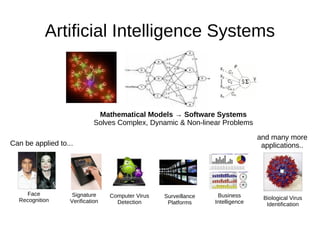
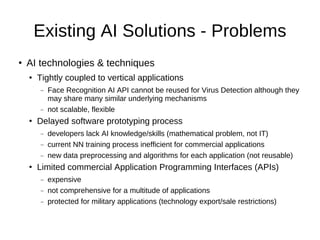
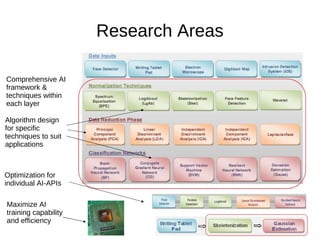
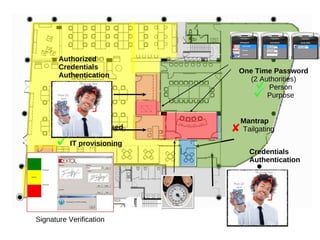
This document discusses Extol Corp, an information and communications technology security solutions provider in Malaysia. It provides details on Extol's 25 years in business, growth from general IT trading to a leading security provider, and research and development successes creating antivirus and authentication software. The document also outlines Extol's human capital and certifications, as well as selected security products. It then provides snapshots of the information security landscape, including policies, threats, and trends, before discussing general trends in attacks becoming cheaper and more proactive while defenses become more expensive and reactive. Potential research areas are outlined around developing a comprehensive artificial intelligence framework and optimizing individual AI APIs.