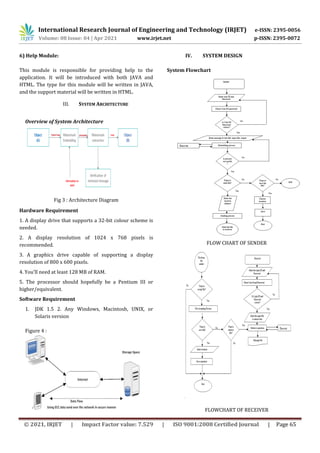
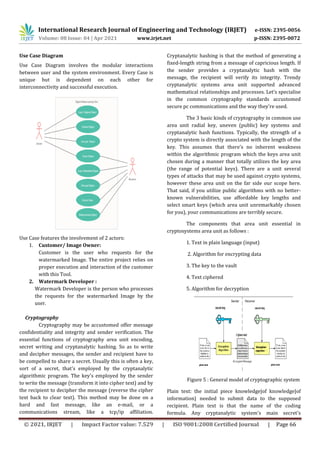
This document discusses security techniques for data transmission in ad-hoc networks, specifically encrypted data transmission and steganography. It proposes a system that enables encrypted data transmission between nodes and uses steganography to hide encrypted data in cover files like images, audio, and video during transmission for additional security. The system architecture includes modules for user interface, embedding secret data in cover files, extracting secret data, sending files between nodes, and receiving files. It aims to securely transmit data in ad-hoc networks using both encryption and steganography to protect confidentiality and integrity of transmitted data.




![International Research Journal of Engineering and Technology (IRJET) e-ISSN: 2395-0056
Volume: 08 Issue: 04 | Apr 2021 www.irjet.net p-ISSN: 2395-0072
© 2021, IRJET | Impact Factor value: 7.529 | ISO 9001:2008 Certified Journal | Page 69
RSA, ECC seems to own a far better future than RSA. ECC
may be used for coding and coding in today's tiny
computing devices as a result of it wants smaller key sizes
and has less computing complexness than RSA. As a result,
ECC is a superb possibility for compact, mobile, and low-
power applications, still as cloud integration. The time
taken by the 2 algorithms for key generation and coding is
compared during this paper. The importance of this
analysis is that it demonstrates the utilization of the ECC
algorithmic rule in cloud storage, which provides
improved protection. This analysis may be dilated to
equate ECC with different algorithms for digital signatures,
key exchanges, and information integrity.
VII. REFERENCES
[1] Study on Watermarking Techniques in Digital
Images Purnima Pal1 M.Tech1(Communication
Engineering) KNIT Sultanpur purnima22pal@gmail.com1
Harsh Vikram Singh2 Associate Prof.2(Electronics
Department) KNIT Sultanpur harshvikram@gmail.com2
Sarvesh Kumar Verma3 M.Tech3(Communication
Engineering) KNIT Sultanpur sarvesh24816@gmail.com3
[2] A Robust Double-Blind Secure High Capacity
Watermarking and Information Hiding Scheme For
Authentication and Tampering Recovery Via the Wavelet
and Arnold Transforms
S. Swapnil and D. B. Megherbi - Center for Computer
Man/Human Intelligence Networking and Distributed
Systems (CMINDS),Department of Electrical and
Computer Engineering, University of Massachusetts,
Lowell, MA
[3] An Invisible Watermarking Technique For Image
Verification.
Minewa M. Yeung and Fred Mintzer - IBM T.J. Watson
Research Center, Yorktown Heights, NY 10598.
{yeung,mintzer} @ watson.ibm.com
[4] Elliptic curve cryptography,
https://en.wikipedia.org/wiki/Elliptic_curve_cryptogra
phy
[5] RSA (algorithm),
http://en.wikipedia.org/wiki/RSA_(algorithm)
[6] JavaTM Cryptography Extension (JCE), Reference
Guide.
http://docs.oracle.com/javase/1.5.0/docs/guide/secur
ity/jce/JCE
RefGuide.html](https://image.slidesharecdn.com/irjet-v8i412-220105102328/85/IRJET-Security-in-Ad-Hoc-Network-using-Encrypted-Data-Transmission-and-Steganography-7-320.jpg)