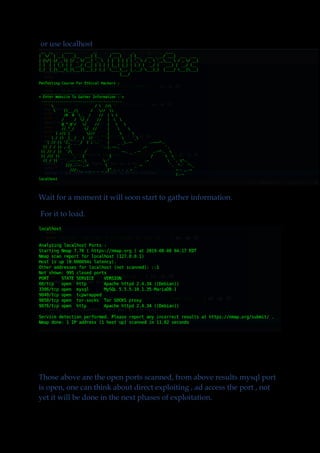
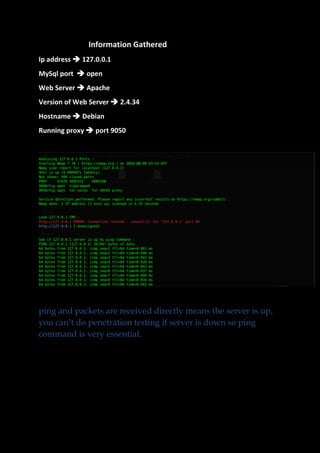
This document introduces a security short course aimed at system administrators, university students, and individuals interested in computer security, focusing on ethical hacking and safeguarding systems against black hackers. It emphasizes the importance of knowledge in current hacking methodologies and includes practical information gathering techniques, tools like infogather.sh, and resources for vulnerability assessment. The course provides relevant knowledge and skills to enhance cybersecurity competence in today’s technology landscape.