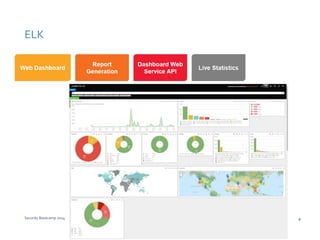
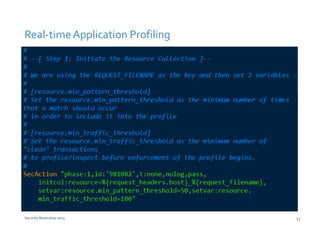
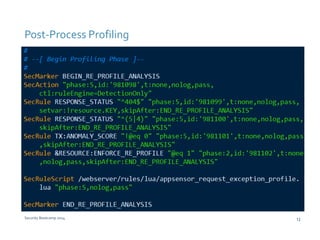
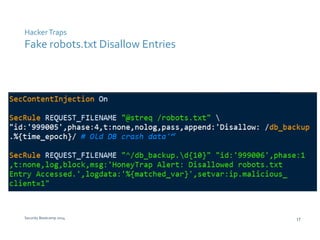
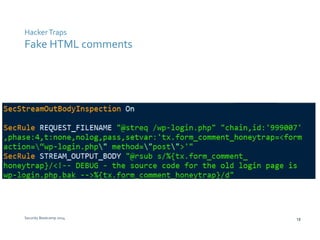
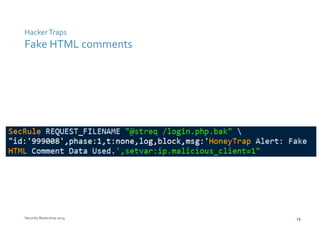
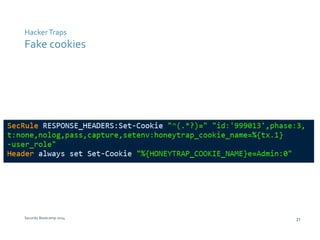
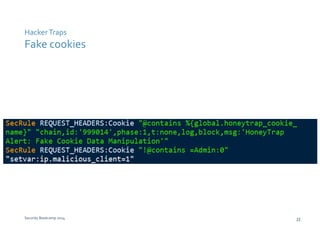
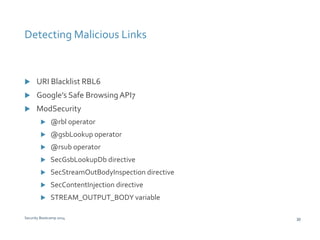
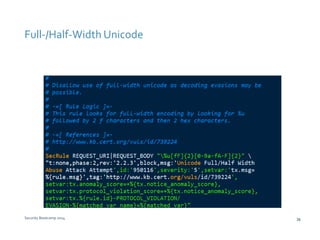
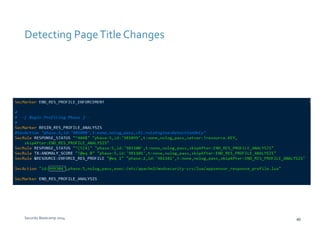
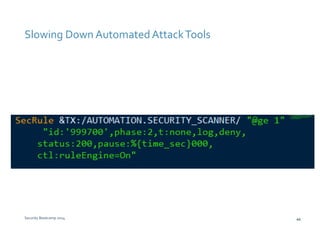
The document discusses various techniques for web application security and traffic analysis using ModSecurity, including real-time application profiling, hacker traps, anomaly scoring, correlation of inbound and outbound events, detecting malicious links, unicode normalization, abnormal header ordering, detecting page title changes, device fingerprinting, and slowing down automated attacks. It also mentions using ELK (Elasticsearch, Logstash, Kibana) for real-time analysis of streaming log data.